
🐧 Introduction to Digital Forensics
⭕ Definition
Digital forensics, also known as computer forensics or cyber forensics, is the branch of forensic science that deals with the identification, preservation, collection, analysis, and presentation of digital evidence in legal and investigative contexts.
The scope of digital forensics encompasses a wide range of areas, including:
Cybersecurity Incidents: Digital forensics plays a crucial role in investigating and mitigating cybersecurity incidents such as data breaches, network intrusions, malware attacks, and unauthorized access. It helps identify the source of an attack, the methods employed, and the extent of the damage.
Criminal Investigations: Law enforcement agencies rely on digital forensics to collect and analyze digital evidence related to criminal activities. This can involve examining computers, mobile devices, storage media, or network logs to uncover evidence of fraud, cybercrimes, intellectual property theft, or child exploitation.
Civil Litigation: In legal disputes, digital forensics can be used to gather evidence for civil litigation cases. This may involve examining digital communications, analyzing data on electronic devices, or reconstructing digital events to support legal claims or defenses.
Corporate Investigations: Organizations conduct internal investigations to uncover unauthorized activities, such as data breaches, intellectual property theft, employee misconduct, or policy violations. Digital forensics assists in collecting and analyzing evidence to determine the extent of the incident and take appropriate actions.
⭕ Importance of Digital Forensics in Cybersecurity
- Identifying and Investigating Cybersecurity Incidents: It helps uncover the nature of attacks, the extent of compromise, and the tactics used by threat actors, aiding in incident response and containment.
- Gathering Evidence for Prosecution: Digital forensics provides reliable evidence to support criminal investigations and prosecutions, ensuring cybercriminals are held accountable.
- Incident Response and Recovery: It assists in understanding the root cause of incidents, eradicating threats, and recovering systems, minimizing the impact on operations.
- Enhancing Cybersecurity Posture: Findings from digital forensics guide improvements in security controls, incident response plans, and personnel training, strengthening overall defenses.
⭕ Key Principles of Digital Forensics
⚔ Locard’s Exchange Principle
Locard’s Exchange Principle, formulated by forensic scientist Dr. Edmond Locard, states that “every contact leaves a trace.”
This principle underpins the entire field of digital forensics, emphasizing that when a digital system is accessed, modified, or interacted with, there will be evidence of these actions.
Investigators use this principle to identify, collect, and analyze digital evidence, understanding that digital artifacts and traces are left behind as a result of user activities.
⚔ Preservation Of Evidence
This principle requires investigators to use proper forensic techniques to acquire and preserve digital evidence without altering or contaminating it.
⚔Chain Of Custody
The principle of chain of custody emphasizes the need to maintain a documented record of the custody, control, and handling of digital evidence.
⚔Accuracy and Validity
Validated methods and tools are used to ensure accurate and reliable results in digital forensic investigations.
⚔Completeness and Thoroughness:
A comprehensive examination of digital sources uncovers all relevant evidence, leaving no gaps in the investigation.
⚔Objectivity and Impartiality
Investigations are conducted objectively, basing conclusions on evidence rather than personal bias or assumptions.
Types of Digital Forensics Investigations
1. Cybercrime Investigations: Involve identifying and prosecuting individuals involved in cybercrimes.
Data Breach Investigations: Analyze incidents where unauthorized access to sensitive data occurs.
Employee Misconduct Investigations: Examine digital evidence to uncover policy violations or intellectual property theft by employees.
Mobile Device Forensics: Analyze digital evidence stored on smartphones and other mobile devices.
👩🏭 Digital Forensics Process
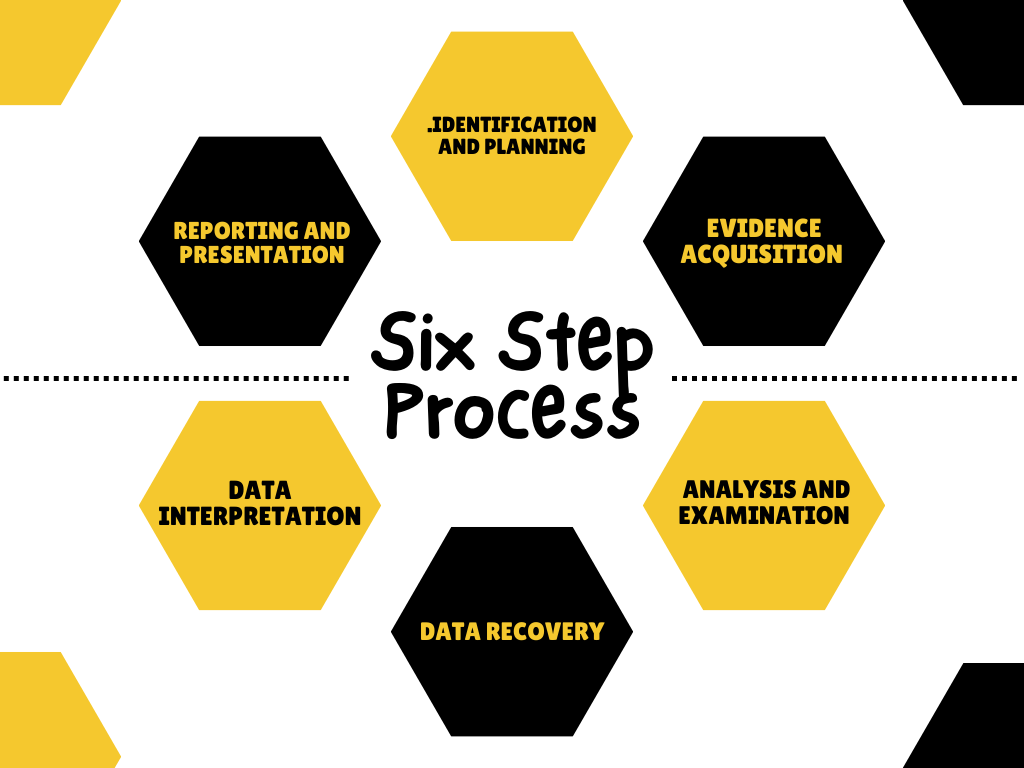
Identification and Planning: Here investigators identify the type of incident, the systems or devices involved, and the potential sources of digital evidence.
Evidence Acquisition: investigators use forensically sound methods to collect and preserve digital evidence. This involves creating forensic copies or images of storage media, such as hard drives or mobile devices
Analysis and Examination: Investigators analyze the acquired digital evidence to extract relevant information. They use various forensic tools and techniques to examine the data, recover deleted files, uncover hidden information, and interpret the findings.
Data Recovery: Data recovery focuses on retrieving data that may have been deleted, damaged, or encrypted.
Data Interpretation : Once the analysis is complete, investigators interpret the findings to form a coherent narrative of events. They correlate different pieces of evidence, establish timelines, and identify patterns or connections.
Reporting and Presentation : Investigators prepare a detailed report summarizing their findings, methodologies, and conclusions.
🐧Forensic Imaging and Data Acquisition
Forensic imaging and data acquisition are essential steps in digital forensics investigations. They involve creating forensic copies or images of storage media to preserve and analyze digital evidence.
A forensic image (forensic copy) is a bit-by-bit, sector-by-sector direct copy of a physical , These files include all the files visible to the operating system(OS), as well as deleted files and pieces of files left in the free space.
Linux Provides us a variety to create Forensic Images and acquire data. Some of them are :
📌 Using dd
We have mentioned the use of dd command before in the storage management part of the blog. We use dd for disk cloning , as it being able to just clone a disk that makes it a great utility for Digital Forensics Guys to use.
In short : DD is a command-line tool commonly used for creating bit-by-bit copies or images of social media.
dd if=/dev/sda of=image.dd bs=512 conv=noerror,sync
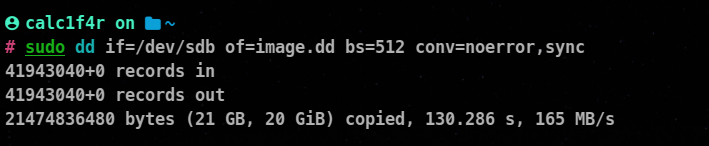
if : Input file
of : Output file
bs : block size
conv : specifies any conversions to be applied during the copy.
📌 Using dcfldd
dcflddis a powerful command-line tool used for forensics and data recovery purposes. It is an enhanced version of the dd command and provides additional features and capabilities.
Syntax :
dcfldd [options] if=<input_file> of=<output_file>
dcflddprovides several options to customize its behavior. Some commonly used options include:
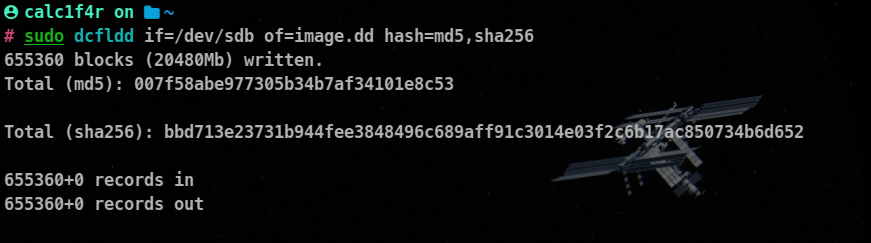
bs=<block_size>: Sets the block size for reading and writing data (e.g., bs=4k).hash=md5, sha1, sha256: Enables hashing while copying, generating checksums for data integrity verification.count=<num_blocks>: Sets the number of blocks to copy.statusinterval=<interval>: Specifies the time interval for updating the status.iflag=<input_flags>: Sets input flags, such as sync, noerror, direct, etc.oflag=<output_flags>: Sets output flags, similar to iflag.
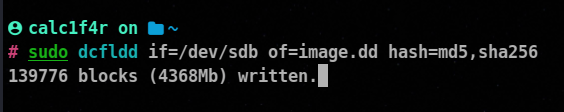
hash specifies the hash algorithms to be used for calculating hash values,
📌 Using dc3dd
DC3DD (Digital Crime Scene Data Disk Duplicator) is a command-line tool used for creating and verifying bit-for-bit forensic disk images. It is an advanced version of the dd command, specifically designed for digital forensics. Here’s a general overview of how to use the dc3dd command:
Installation
sudo apt install dc3dd
Syntax
dc3dd if=<input_file> of=<output_file>
Additional Features
hash=md5, sha1, sha256: Enables hashing while copying, generating checksums for data integrity verification.hashlog=<output_file>: Specifies the file where the hash values will be logged.log=<output_file>: Specifies the log file to record the progress and information about the imaging process.pattern=<hex_pattern>: Writes the specified hex pattern instead of reading from the input file.verify: Performs a verification after the imaging process to ensure the accuracy of the copy.
Example:
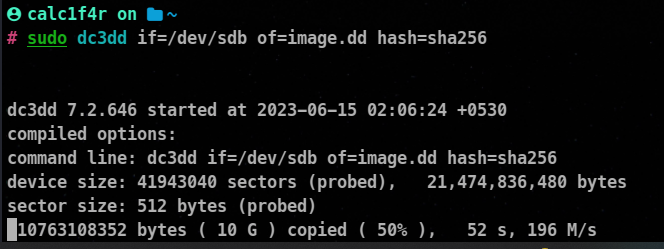
🐧File System Analysis and Recovery
File system analysis and recovery are critical aspects of digital forensics investigations. They involve examining file systems, analyzing their structures, and recovering deleted or damaged files and data.
Understanding file systems and utilizing appropriate tools can greatly assist investigators in retrieving valuable evidence
📌 Using testdisk
TestDisk is a powerful command-line tool primarily used for partition recovery and file system repair. It supports various file system formats and can recover deleted partitions, fix boot sectors, and rebuild file system structures.
Syntax
sudo testdisk /dev/sdb
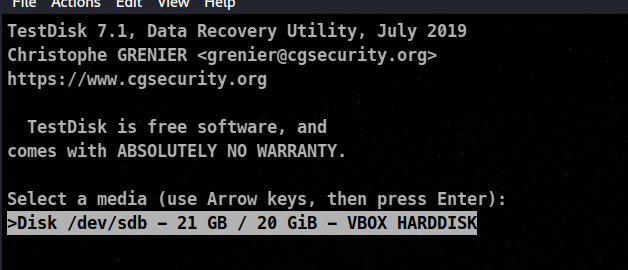
After pressing enter we reach
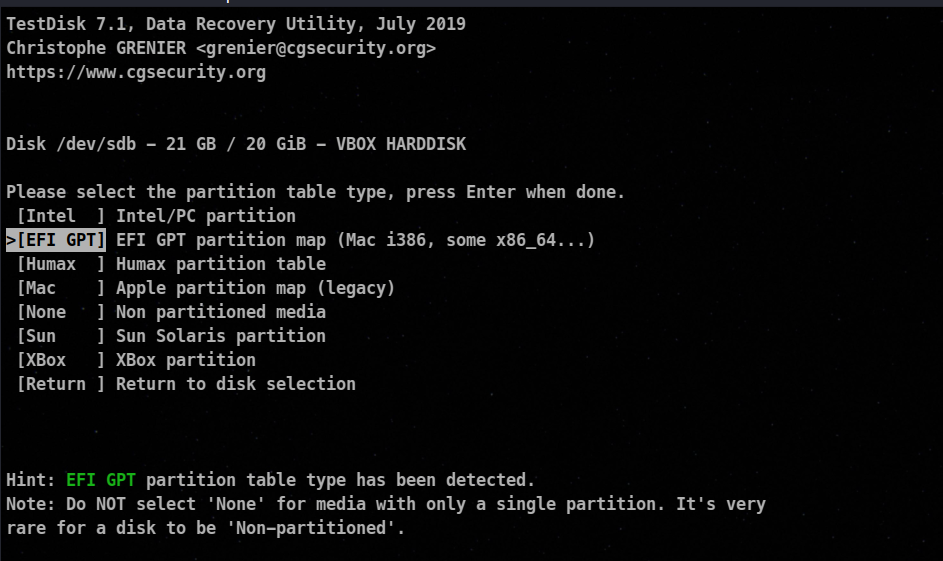
After pressing enter again
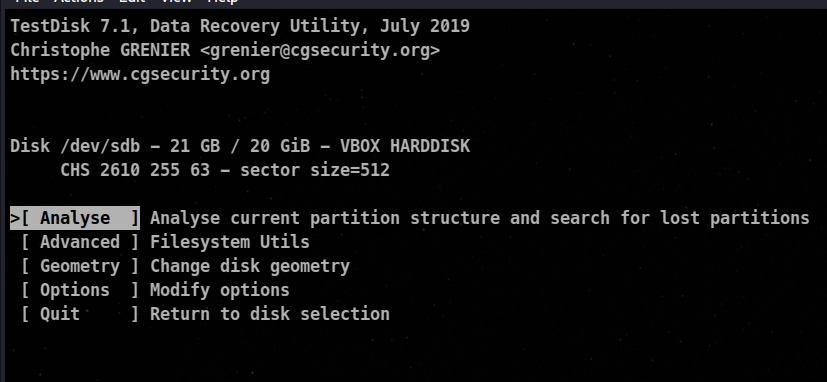
here we can see we are greated with various options , we will go with option 1
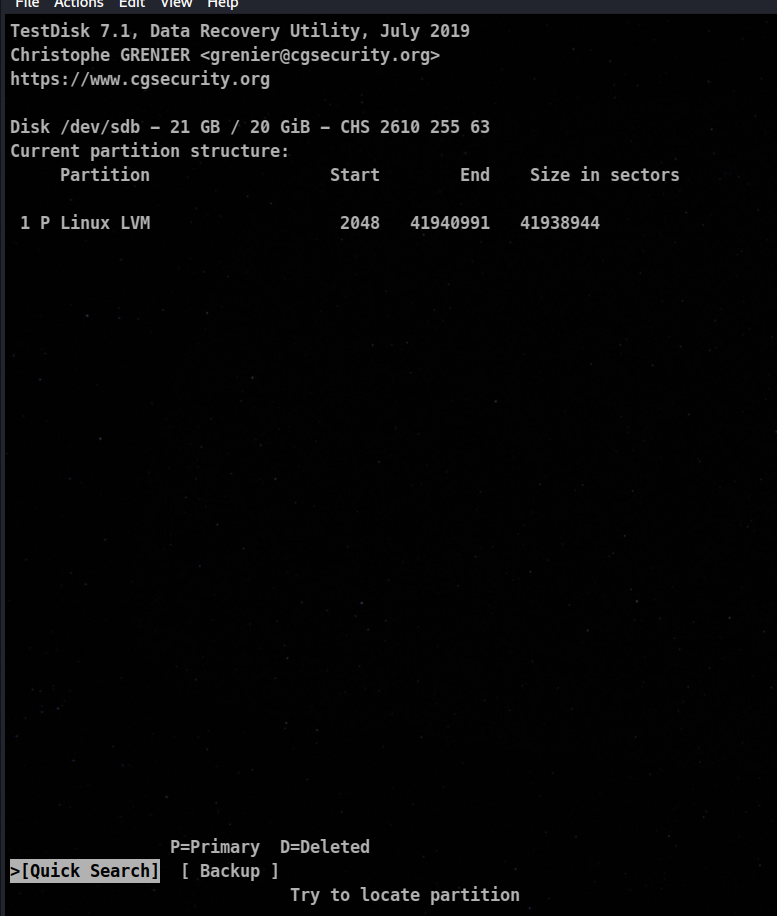
So here we know that we don’t have any deleted partition and we only have one partition number 1.
Using Scalel
Scalpel is a command-line file carving tool used for recovering deleted or damaged files from disk images or devices. It is designed to extract specific file types based on predefined headers and footers, known as “carving signatures.”
Installation
sudo apt install scalpel
Configuration
- Locate the configuration file for Scalpel, typically named “scalpel.conf”.
- Open the configuration file in a text editor to define the file types you want Scalpel to extract.
- Uncomment (remove the ‘#’ symbol) or add entries for the file types you wish to recover. Each entry consists of a file signature and a file extension.
- Customize any other settings in the configuration file, such as output directory, carving method, or header/footer constraints, if needed.
Syntax
scalpel -c scalpel.conf -o output_directory input_file
- Replace “scalpel.conf” with the name of your configuration file.
- Replace “output_directory” with the directory where you want the recovered files to be saved.
- Replace “input_file” with the path to the disk image or raw data file you want to process.
In kali Config file is located at /etc/scalpel/scalpel.conf
🐧 Memory Forensics
Memory forensics involves the analysis and examination of a computer’s volatile memory (RAM) to extract valuable information and evidence. Memory analysis can provide insights into running processes, network connections, opened files, and even encrypted data.
📌 Using Volatility
Volatility is a popular open-source memory forensics framework that allows investigators to extract and analyze information from memory dumps. It supports multiple operating systems and provides a wide range of plugins to identify and examine various artifacts.
It is the number tool being used for memory Forensics
Installation
git clone https://github.com/volatilityfoundation/volatility3.git
cd volatility3
pip3 install -r requirements.txt
python3 setup.py build
python3 setup.py install
In this example I will use not create a memory dump but will use a pre made windows XP memory dump file which can be downloaded from here.
Volatility3 has various plugins to retrieve various information about what was going through the system at that time.
Plugins available for windows machine:
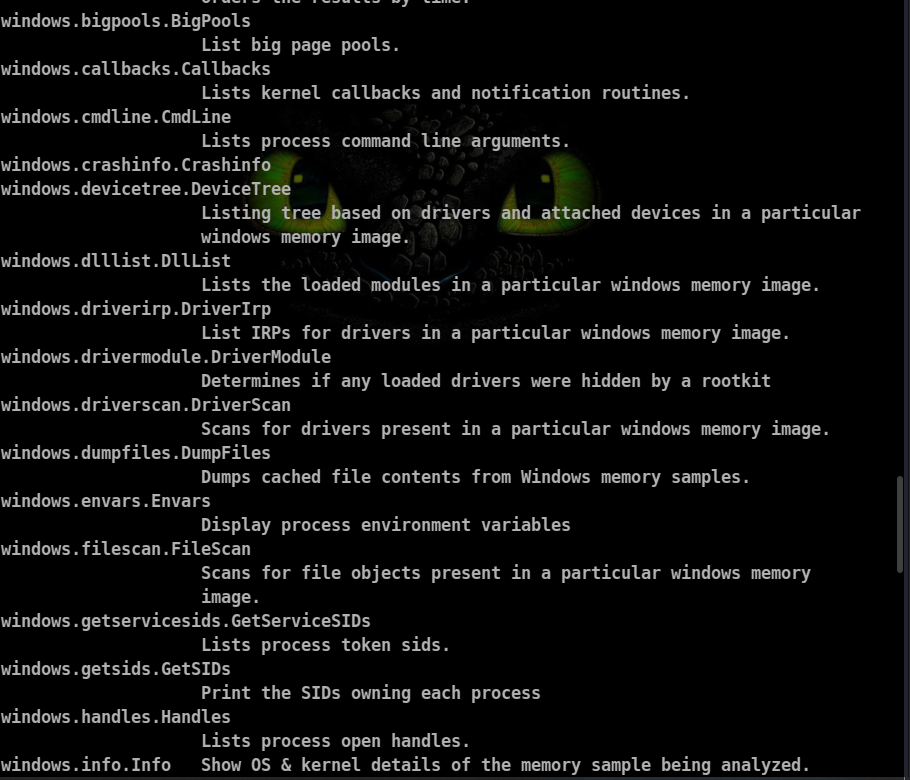
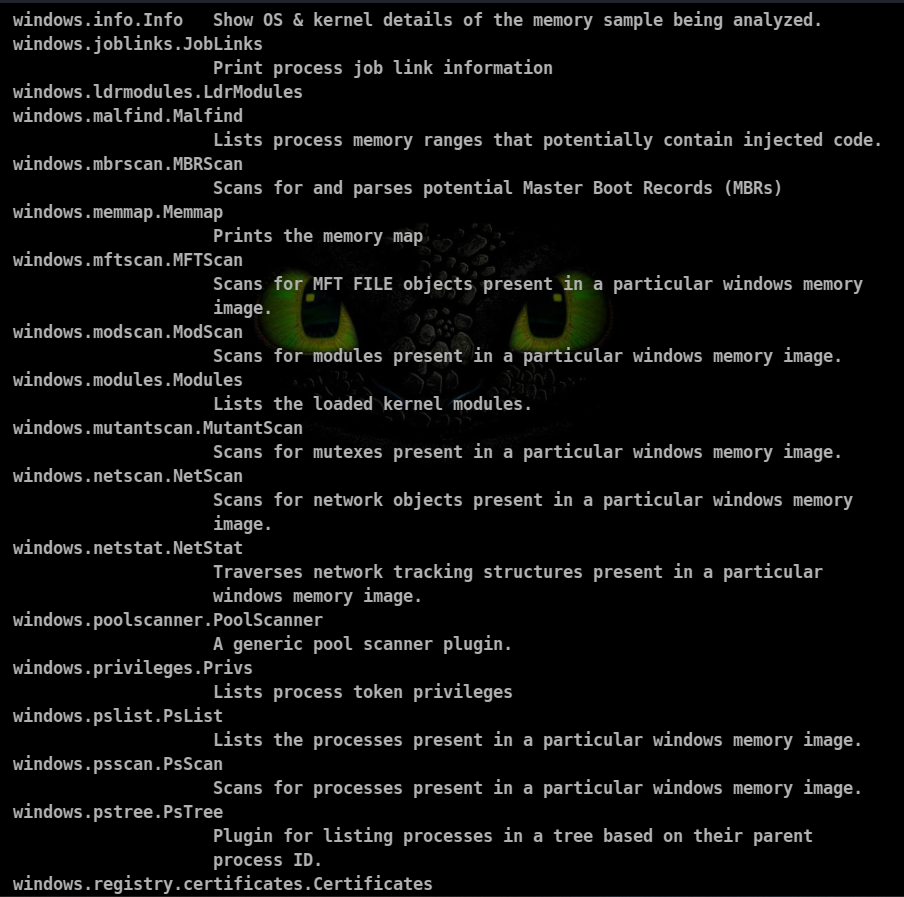
Process Scan
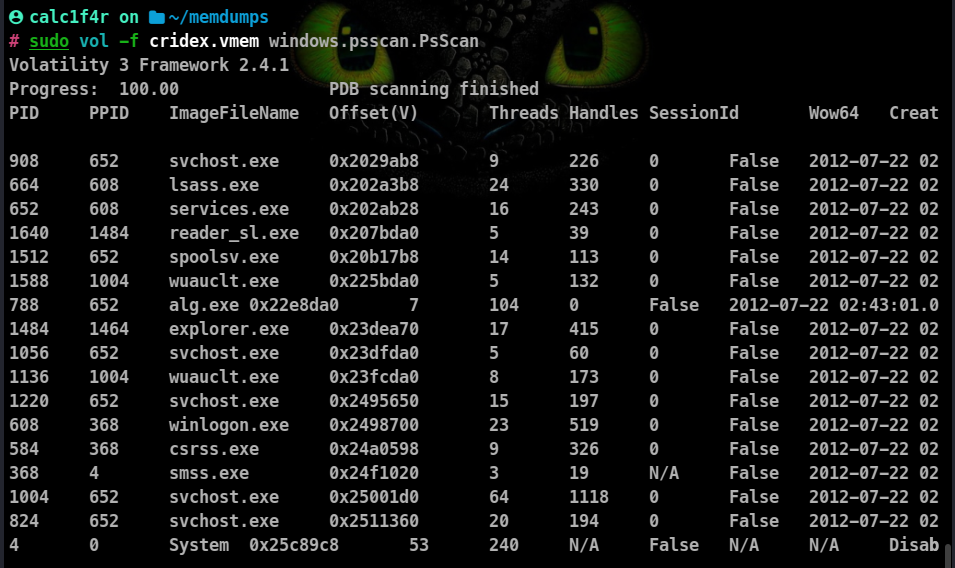
Process Scans also show processes that are trying to keep themselves hidden.
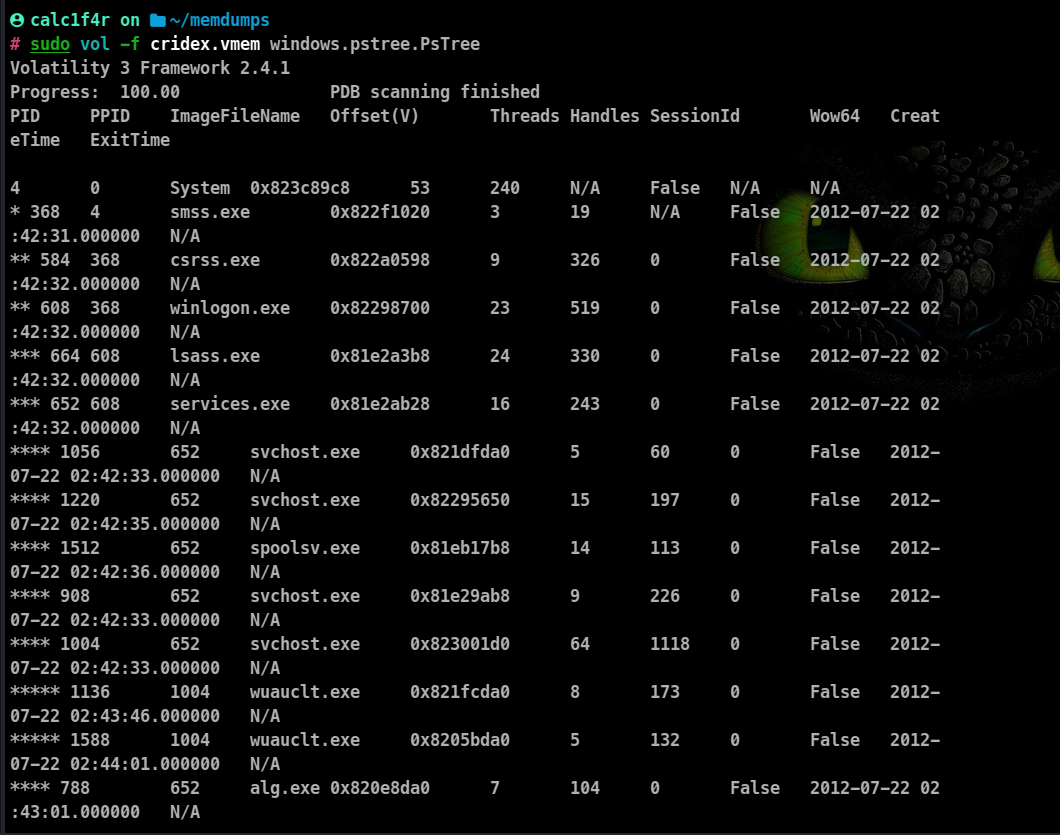
Process Tree Structure
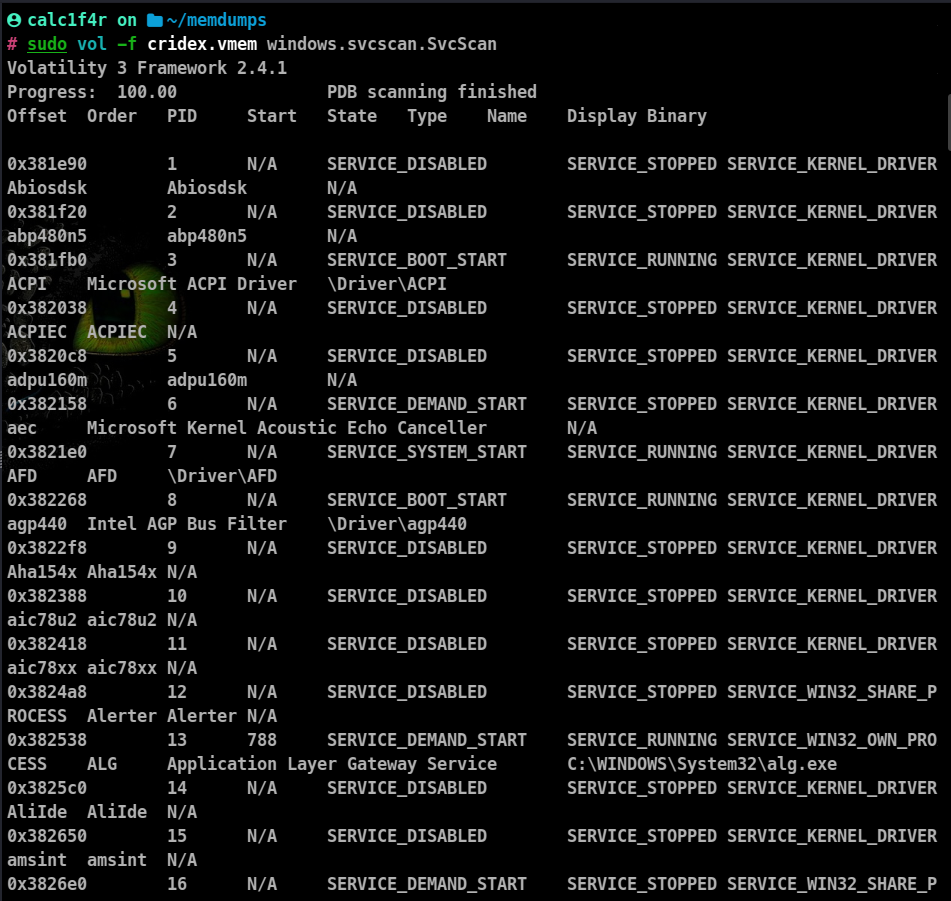
Windows Services
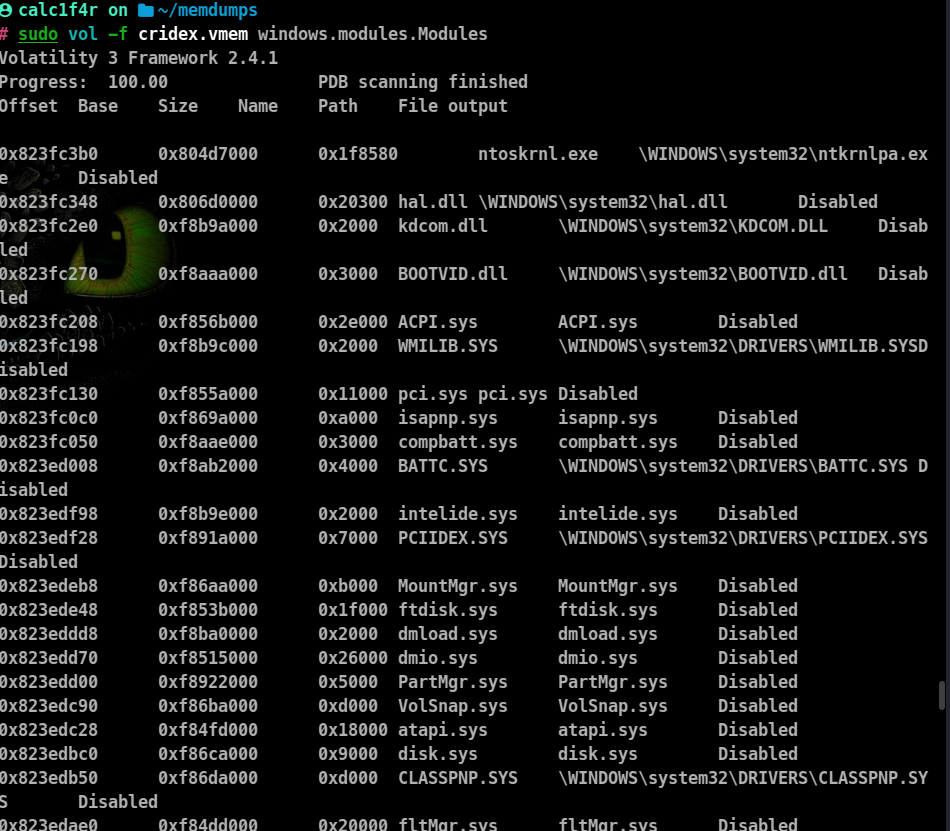
Kernal Scan
🎇 Conclusion
In conclusion, Linux has proven to be an invaluable asset in the field of forensics. From memory forensics to image forensics and disk recovery, Linux-based tools have empowered investigators to extract vital evidence and uncover hidden insights. In our next blog, we will explore additional branches of forensics that can be performed using Linux, expanding our toolkit and further enhancing our capabilities in the realm of digital investigation. Stay tuned for more exciting discoveries in the world of Linux forensics.