
⚒ Decoding Wireless Hacking
Wi-Fi is everywhere these days, connecting our devices and allowing us to access information and communicate effortlessly. But have you ever wondered how it actually works? And is it possible to manipulate Wi-Fi networks for different purposes? In this series “A Beginner’s Guide to Wireless Hacking”, we will go deep into the architecture and will learn what vulnerabilities can affect our Wifi and How can we exploit WiFi.
In this initial blog, we’ll cover the basics. We’ll explain how Wi-Fi networks function, break down important terms related to Wi-Fi and networking and dive into the history and key features of Wi-Fi technology.
⚡Introduction to WIFI
Wi-Fi, short for Wireless Fidelity, is a wireless networking technology that allows devices to connect to the internet or to each other without the use of wires. Wi-Fi uses radio waves to transmit data, which means that it can be used in areas where it is not possible to run cables.
Wi-Fi is the most popular way to connect to the internet in homes and businesses. It is also used in many public places, such as coffee shops, libraries, and airports.
⚡Features of WIFI
- Wireless connectivity: Wi-Fi is a wireless technology, which means that you do not need to run cables to connect your devices to the internet.
- Portability: Wi-Fi is a portable technology, which means that you can easily take your devices with you and connect to Wi-Fi networks wherever you go.
- Speed: Wi-Fi speeds have been steadily increasing over the years, and today’s Wi-Fi networks can provide speeds that are comparable to wired connections.
- Security: Wi-Fi networks can be secured with a variety of security protocols, such as WPA2 and WPA3.
- Compatibility: Wi-Fi is a widely supported technology, and most devices today have built-in Wi-Fi adapters.
- Range: The range of a Wi-Fi network depends on the type of network and the environment. In general, 2.4 GHz networks have a longer range than 5 GHz networks.
- Penetration: Wi-Fi signals can penetrate walls and other objects, but the signal strength will be reduced.
- Interference: Wi-Fi signals can be interfered with by other electronic devices, such as microwaves and cordless phones.
- Security: Wi-Fi networks can be secured with a variety of security protocols, but no security protocol is 100% foolproof.
⚡Base technology of WIFI
Wi-Fi technology relies on the principles of radio wave transmission and modulation to enable wireless connectivity, data transfer, and network communication between devices. Specifically, it utilizes the IEEE 802.11 family of standards, which define the protocols and specifications for wireless local area networks (WLANs).
💡The IEEE (Institute of Electrical and Electronics Engineers is an international organization that creates technical standards for various fields of engineering.
⚡History of WIFI
Wi-Fi technology was developed through collaborative efforts of organizations and researchers. The IEEE’s 802.11 group defined the technical standards for Wi-Fi, with contributions from various parties. The availability of unlicensed spectrum and advancements in wireless communication technologies played key roles. The Wi-Fi Alliance ensures interoperability and conducts certification programs. Wi-Fi evolved through versions like 802.11b, 802.11g, 802.11n, 802.11ac (Wi-Fi 5), and 802.11ax (Wi-Fi 6), with each version bringing improvements in speed, range, and efficiency.
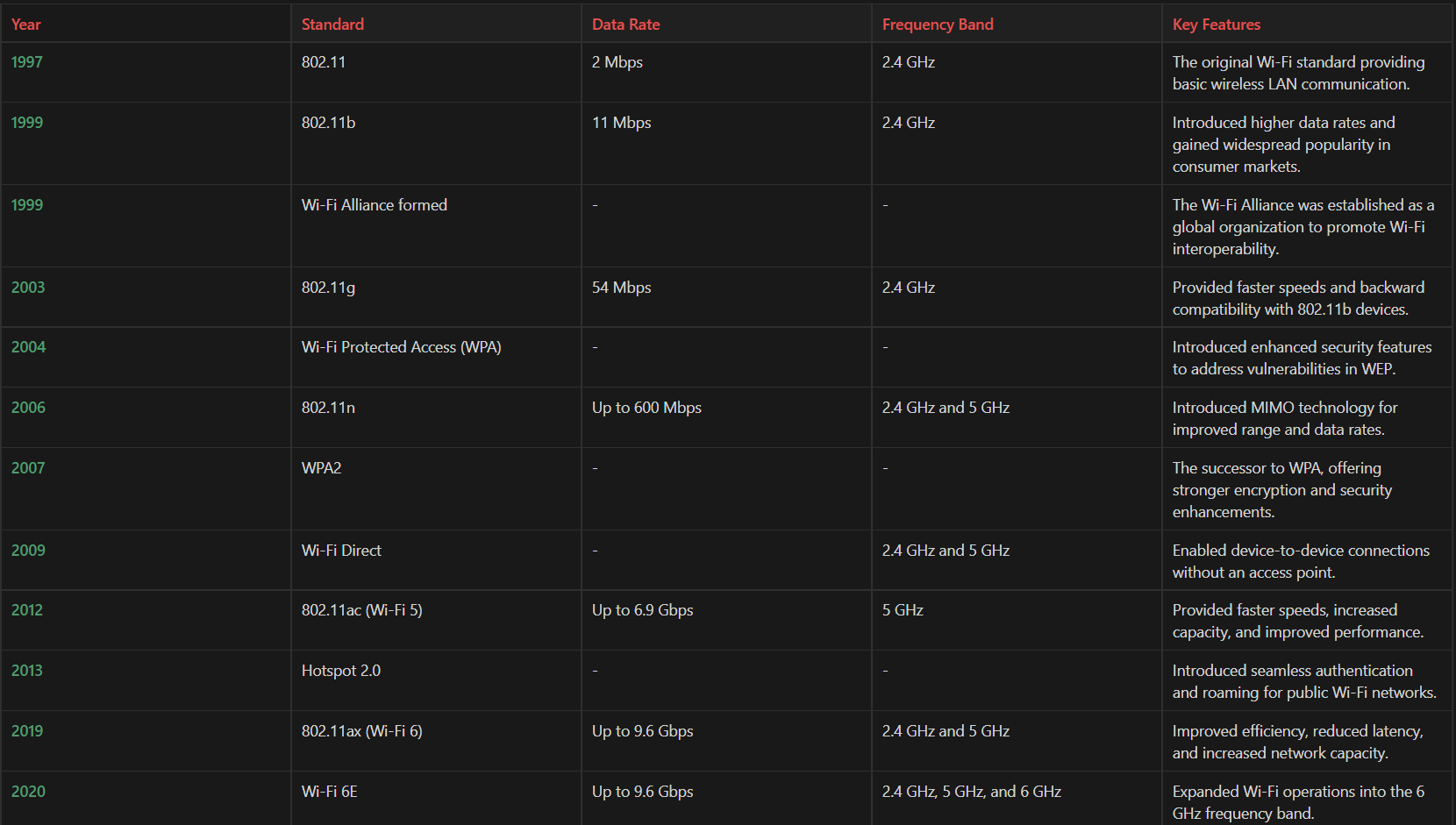
⚡Wireless security Protocols
Wireless security protocols are designed to protect wireless networks from unauthorized access, data breaches, and malicious activities. These protocols ensure the confidentiality, integrity, and authenticity of transmitted data.
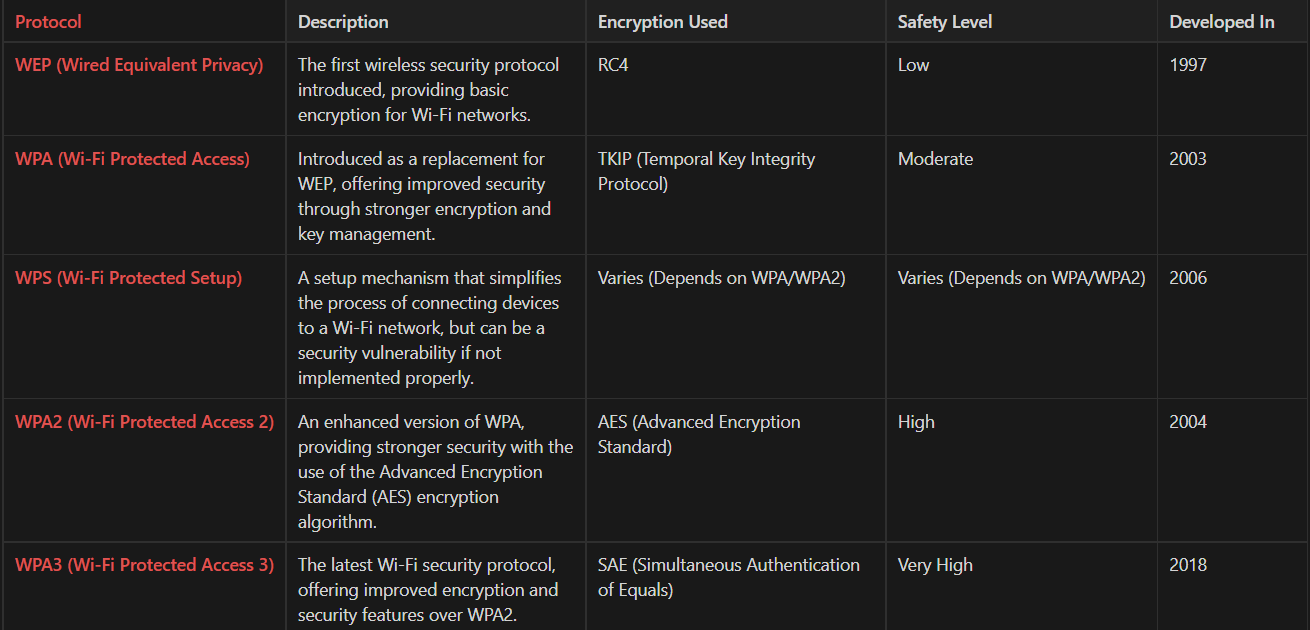
🎃 Some basic Terms related to WIFI
🐾 WiFi Adaptor
A Wi-Fi adapter, also known as a Wi-Fi dongle or wireless network adapter, is a device that enables a computer or other devices to connect to a Wi-Fi network. It allows devices that do not have built-in Wi-Fi capabilities to access wireless networks and connect to the internet or communicate with other devices wirelessly.
🔺Note : If you want to use WIFI functionality in a virtual machine, you will have to use an external WIFI adaptor and will have configure it with VMware or Virtual box.
🐾 AP (Access Point)
AP stands for Access Point in the context of Wi-Fi. An Access Point is a device that allows Wi-Fi-enabled devices to connect to a wired network wirelessly. It acts as a central hub or gateway for wireless communication, providing a bridge between Wi-Fi devices and a wired network.
🐾Frequency
Frequency bands refer to specific ranges of radio frequencies that are used for wireless communication. Wi-Fi operates in two main frequency bands: 2.4 GHz and 5 GHz.
- 2.4 GHZ : The 2.4 GHz band is the older and more widely used frequency band in Wi-Fi. It provides good coverage and can penetrate obstacles like walls more effectively.]
- 5 GHZ : The 5 GHz band is a newer addition to Wi-Fi and offers more available channels with wider frequency ranges. It provides faster data speeds and is less congested compared to the 2.4 GHz band since fewer devices operate in this frequency range. However, the 5 GHz signals have a shorter range and may encounter more attenuation when passing through walls and other obstacles
🐾Channels
Channels refer to specific frequencies within the wireless spectrum that are used for transmitting and receiving data. Wi-Fi channels are divided to reduce interference and allow multiple networks to operate in close proximity without conflicting with each other.
🔥 Each frequency band is divided into multiple channels, represented by numbers. For example, in the 2.4 GHz band, there are 11 channels available, usually numbered from 1 to 11. In the 5 GHz band, there are typically more channels available, such as 24 or more.
🔥 Channels in the 2.4 GHz band have a narrower frequency range and can partially overlap with each other. This means that neighboring Wi-Fi networks using nearby channels may experience interference, which can degrade the performance of both networks.
🐾 ESSID
ESSID stands for Extended Service Set Identifier. It is the name assigned to a Wi-Fi network. The ESSID acts as a unique identifier that allows devices to differentiate between different wireless networks in the vicinity. When you search for available Wi-Fi networks on your device, you see a list of ESSIDs to choose from.
🐾 BSSID
BSSID stands for Basic Service Set Identifier. It is a unique identifier assigned to each wireless access point (AP) in a Wi-Fi network. Each access point in a Wi-Fi network has its own MAC (Media Access Control) address, which is a unique identifier assigned to the network interface of the device. The BSSID is derived from the MAC address of the access point.
🐱Why BSSID is important?
Suppose you work in an office with multiple WiFi networks with the same name or ESSID. How would you connect to one of them? BSSID solves this issue as it is a unique identifier so your device can use it to differentiate b/w which WiFi to connect to!
🐾 Bandwidth
Bandwidth in Wi-Fi refers to the maximum data transfer rate or capacity of a wireless network. It represents the amount of data that can be transmitted over the network within a given time frame. Measured in Gigabits per second (Gbs) or Megabits per second (Mbs).
🐾Key/Passphrase
A key refers to a cryptographic code or password used for authentication and encryption purposes to secure a wireless network
There are two keys 🔑 when working with WIFI :
Network Security Key: Also known as a Wi-Fi password or passphrase, the network security key is used to authenticate a client device and grant access to the Wi-Fi network. When connecting to a secured Wi-Fi network, users are typically prompted to enter the network security key to prove their authorization. This key is used during the authentication phase of the Wi-Fi handshake process to establish a secure connection.
Encryption Key: Once a client device is authenticated and connected to a Wi-Fi network, an encryption key is used to encrypt and decrypt the data transmitted over the network. This key ensures that the data exchanged between the client and the access point is secure and cannot be intercepted or understood by unauthorized parties. Different encryption protocols, such as WPA2 or WPA3, use different encryption keys and algorithms to protect the confidentiality and integrity of the Wi-Fi communication.
📡Some Neccessary Networking Concepts
🖊Mac Address
A MAC address, which stands for Media Access Control address, is a unique identifier assigned to network interfaces, such as network cards or Ethernet ports.
A MAC address is a 48-bit (6-byte) value expressed in hexadecimal format, typically written in pairs separated by colons or hyphens.
Example : 00:1A:2B:3C:4D:5E, the first half of the MAC address is the Organizationally Unique Identifier (OUI), which identifies the manufacturer or vendor of the device, while the second half is the device-specific identifier.
🖊ARP
ARP stands for Address Resolution Protocol. It is a communication protocol used in computer networks to map an IP (Internet Protocol) address to a corresponding MAC (Media Access Control) address.
When a device wants to communicate with another device on the same network, it needs to know the MAC address of the destination device. The ARP protocol helps in this process by allowing a device to send an ARP request to the network, asking for the MAC address associated with a specific IP address.
👩🏭 Working of Arp
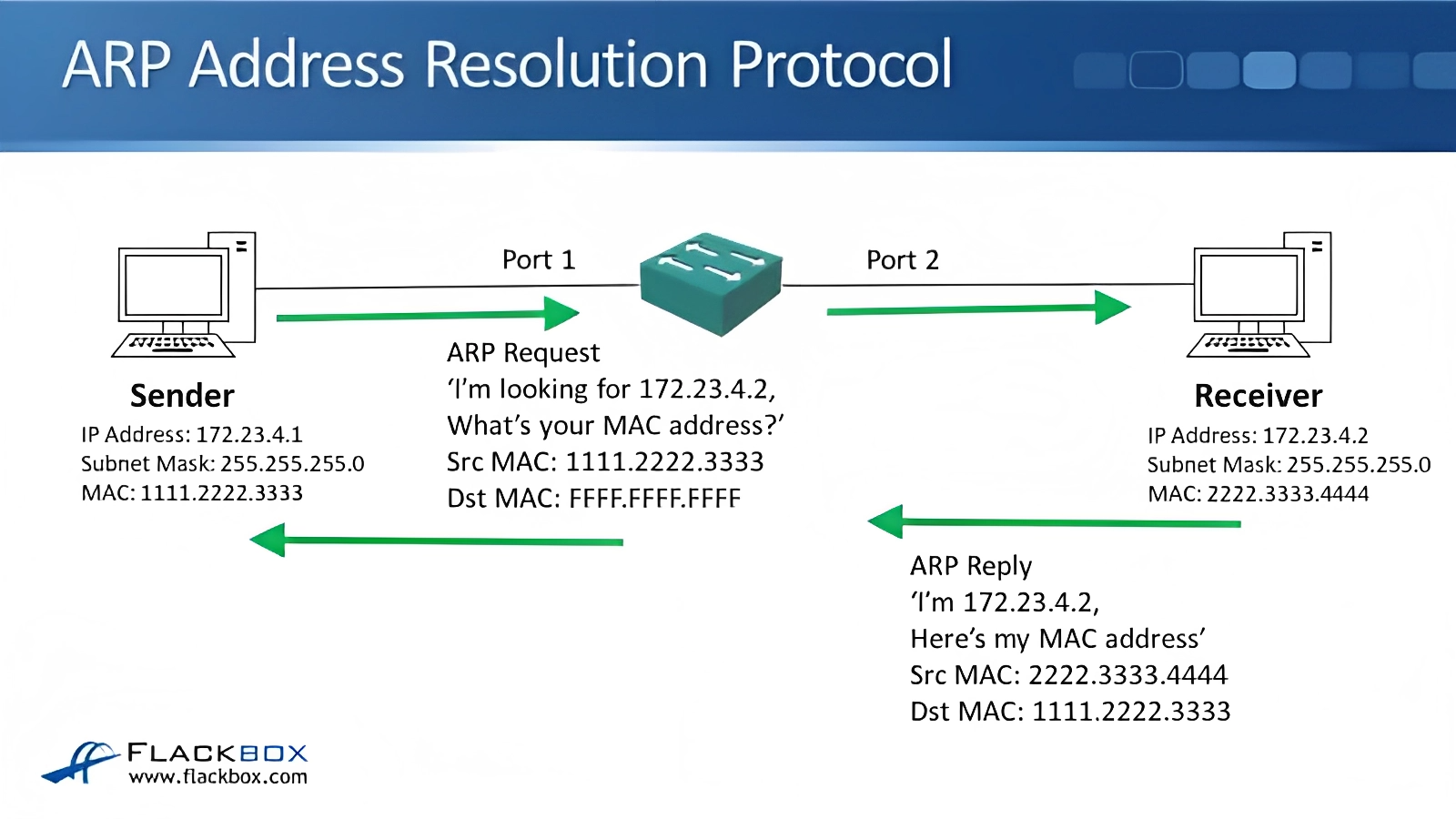
Source: https://www.flackbox.com/arp-the-address-resolution-protocol
The device that wants to send data (known as the sender) checks its ARP cache, which is a table that stores recently resolved IP-to-MAC address mappings. If the mapping for the destination IP address is found in the cache, the sender can use the corresponding MAC address directly.
If the mapping is not found in the ARP cache, the sender sends an ARP request broadcast message to the local network, asking “Who has this IP address?” The request includes the sender’s MAC address, IP address, and the IP address it wants to reach.
Every device on the local network receives the ARP request but only the device with the matching IP address responds. The device with the matching IP address (known as the target) sends an ARP reply message directly to the sender, providing its MAC address.
The sender receives the ARP reply and updates its ARP cache with the IP-to-MAC address mapping it received. The sender can now use the MAC address to send data directly to the target device on the local network.
🖊 IP Address
An IP address, or Internet Protocol address, is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. It serves as a unique identifier for devices, allowing them to send and receive data across the internet or within a private network.
Types of IP address :
Private IP Address: A private IP address is assigned to devices within a private network, such as a home network or an office intranet. These addresses are not globally routable on the internet, meaning they are not directly accessible from devices outside the private network. Private IP addresses are used for local communication within the network and are not unique globally. They are defined in certain reserved address ranges that are designated for private use. Commonly used private IP address ranges include:
IPv4 Private Address Range:
- 10.0.0.0 to 10.255.255.255
- 172.16.0.0 to 172.31.255.255
- 192.168.0.0 to 192.168.255.255
IPv6 Private Address Range:
- fc00::/7 (unique local addresses)
- fd00::/8 (private unique local addresses)
Private IP addresses allow devices within the private network to communicate with each other and share network resources, while external communication is typically done through network address translation (NAT) by using a public IP address.
Public IP Address: A public IP address is assigned to a device directly connected to the internet. It is globally unique and can be accessed from devices outside the local network. Public IP addresses are allocated by Internet Service Providers (ISPs) and are used to identify and communicate with devices over the Internet. These addresses allow devices to send and receive data directly from other devices on the internet.
📌 Public IP addresses can be static or dynamic.
🖊 Gateway
A gateway is a device or a computer system that serves as an entry point or an interface between different networks. It acts as a bridge or a link that allows devices in one network to communicate with devices in another network. The gateway facilitates the transfer of data between networks by forwarding data packets based on their destination address.
⚡ In modern days gateways, WiFi and router are installed in a single device, so you don’t need to purchase each device separately.
🖊 Router
A router is a networking device that connects multiple networks together and directs network traffic between them. It acts as a central hub for data transmission within a network or between different networks, making routing decisions based on the destination address of data packets.
Routers receive data packets from connected devices and forward them to the appropriate destination. Each packet contains information about the source and destination IP addresses, allowing the router to make routing decisions.
Routers often include built-in firewall capabilities to protect the network from unauthorized access and malicious activities
Many routers provide NAT functionality, which allows multiple devices within a local network to share a single public IP address. NAT translates the private IP addresses of devices on the local network to the router’s public IP address when communicating with devices outside the network. This enables devices on the local network to access the internet using a single public IP address.
Routers use a routing table to properly send data from one destination to another. A routing table is a data structure stored within a router that contains information about available network routes. It serves as a roadmap for the router to determine the appropriate path to forward data packets to reach their intended destination
🖊 Subnet
A subnet, short for subnetwork, is a logical division of an IP network. It allows for the segmentation of a larger network into smaller, more manageable networks. Subnetting is used to improve network performance, security, and organization by creating separate broadcast domains within a network.
When subnetting, a network administrator takes a portion of the host bits from the IP address and allocates them for network identification, creating subnets. This process involves defining a subnet mask, which determines the size of the subnet and the range of IP addresses it can accommodate.
🖊DHCP
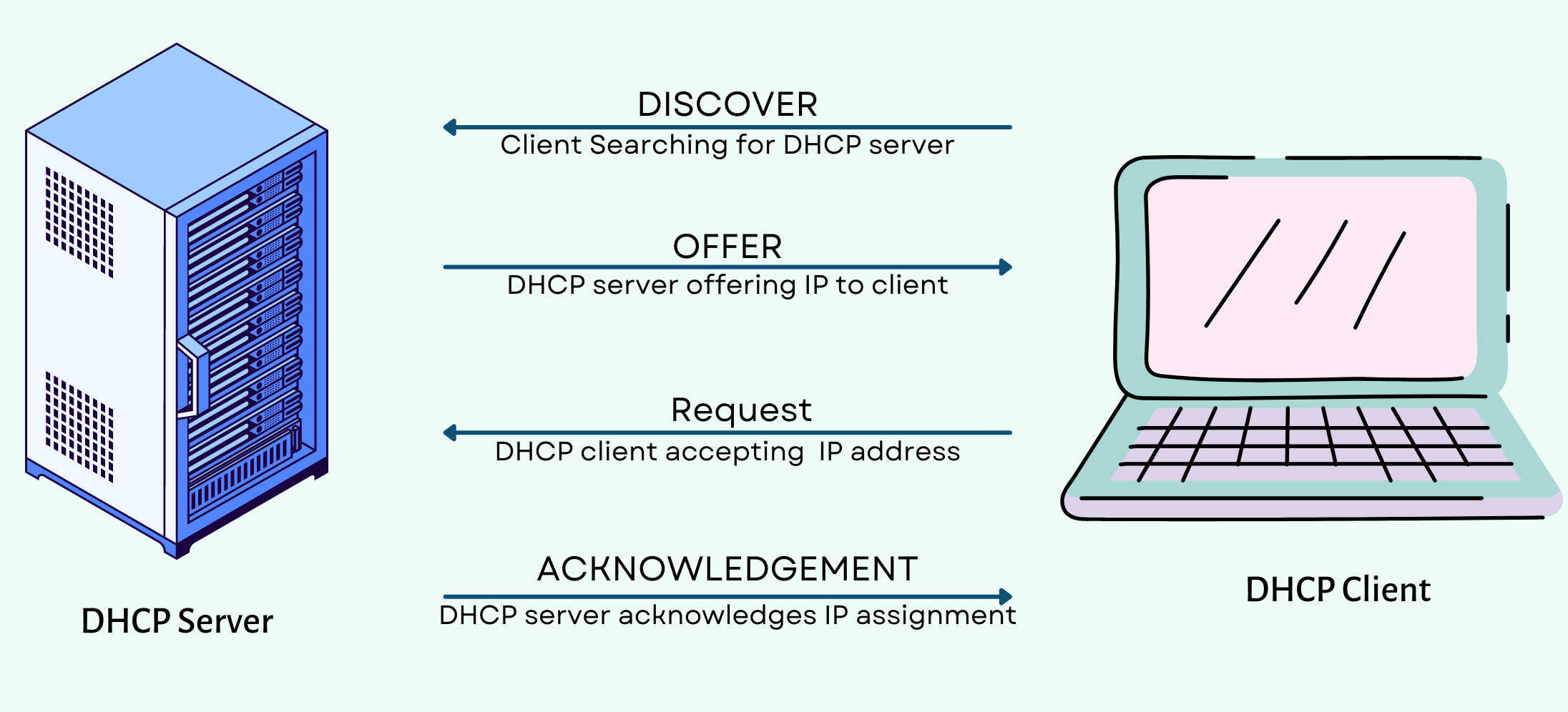
A DHCP (Dynamic Host Configuration Protocol) server is responsible for assigning IP addresses and other network configuration information to devices on a network. Here’s a simplified explanation of how a DHCP server works:
Request from a client: When a device (client) connects to a network, it sends a DHCP request broadcast message, called a DHCP Discover message, to find a DHCP server.
DHCP Offer: When the DHCP server receives the DHCP Discover message, it responds with a DHCP Offer message. The offer includes an IP address and other configuration details that the client can use.
DHCP Request: If the client receives multiple DHCP Offers, it chooses one and sends a DHCP Request message to the selected DHCP server, requesting the offered IP address.
DHCP Acknowledgment: The DHCP server receives the DHCP Request message and responds with a DHCP Acknowledgment message. This message confirms the IP address assigned to the client.
⚒Working Of WIFI
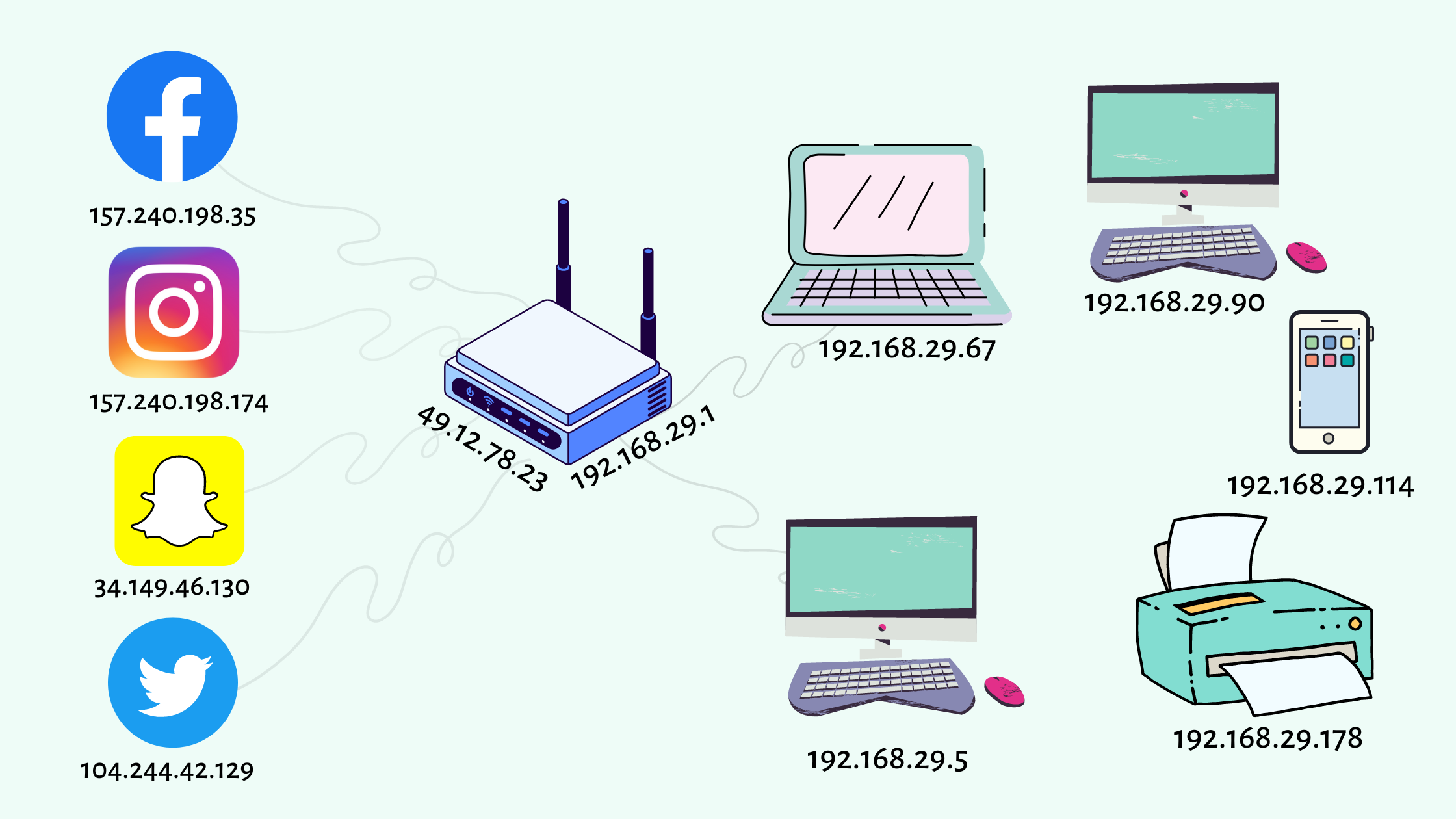
Device Connection to the Network: When a device (e.g., a computer, smartphone, or IoT device) connects to a network, it typically does so via a physical connection (e.g., Ethernet cable) or wirelessly through Wi-Fi. The device sends a request to join the network, and the network infrastructure, including the router, facilitates the connection.
Obtaining an IP Address: Once connected, the device needs to obtain an IP address to communicate on the network. There are two main methods for IP address assignment: static and dynamic. In the case of dynamic IP address assignment, the device sends a request to the router using the DHCP protocol, which we discussed earlier. The router then assigns an available IP address from its pool and provides it to the device.
Local Network Communication: With the assigned IP address, the device can now communicate with other devices on the local network. It can send data packets to other devices by addressing them using their IP addresses within the same network. This communication happens directly between devices within the network without involving the router.
Destination Outside the Local Network: If the device wants to communicate with a destination outside the local network (e.g., a website or a server on the internet), it follows these steps:
a. Determining the Gateway: The device checks its network configuration and identifies the default gateway, which is the IP address of the router. The default gateway acts as the exit point for traffic leaving the local network.
b. Data Routing: The device encapsulates the data it wants to send within packets. Each packet contains the destination IP address, among other information. When the device sends the packets, it forwards them to the default gateway (router).
c. Network Address Translation (NAT): Upon receiving the packets, the router performs Network Address Translation. It replaces the source IP address of the packets with its own public IP address, effectively hiding the private IP addresses of the devices on the local network. This allows the response packets from the destination to be routed back to the router.
d. Routing to the Internet: The router examines the destination IP address of the packets and consults its routing table to determine the next-hop router or gateway that can reach the destination network (in this case, the internet). The router forwards the packets to the appropriate next-hop router, continuing this process until the packets reach the destination network.
e. Public IP Communication: As the response packets return from the destination network, they are routed back to the router using its public IP address. The router maintains a record of the devices on the local network and uses Network Address Translation to translate the destination IP address of the packets back to the appropriate private IP address of the device that initiated the communication.
f. Delivery to the Device: Finally, the router forwards the response packets to the requesting device on the local network. The device receives the packets and processes the data, allowing the user to view the requested webpage, receive an email, or perform any other internet-related task.
Each device on the network uses Router’s Public Ip address to communicate to the whole world.
⚡ WIFI Adaptor Operating Modes
Wi-Fi adapters can operate in different modes, also known as operating modes or wireless modes, depending on their capabilities and configuration. The operating mode determines how the adapter behaves in terms of transmitting and receiving wireless signals.
Infrastructure/Managed Mode: This is the most common operating mode used by Wi-Fi adapters. In infrastructure mode, the adapter connects to a wireless access point (AP) or router to join an existing Wi-Fi network. It allows the device to access the internet and communicate with other devices on the network.
Soft AP Mode: Some Wi-Fi adapters support soft access point (soft AP) mode, where the adapter can act as a virtual access point. In this mode, the adapter creates its own Wi-Fi network, allowing other devices to connect to it. This is useful for sharing an internet connection from a single device to multiple devices or for creating a temporary network.
Monitor Mode: Monitor mode is a special operating mode that allows Wi-Fi adapters to capture and analyze wireless traffic without actively participating in network communication. In this mode, the adapter can passively listen to all Wi-Fi signals in its range, making it useful for network monitoring, packet sniffing, or troubleshooting.
Promiscuous Mode: Similar to monitor mode, promiscuous mode is a mode in which the Wi-Fi adapter can capture and analyze network traffic. It is often used in network analysis or security auditing tools to inspect network packets and detect any abnormalities or potential security threats.
🔺Note :
All of the above-mentioned modes are not available in all WIFI adaptors, there are only specific WIFI adaptors in the market that supports modes other than managed mode. So to fully learn from these series you will have to get an adaptor which these modes.
There is a list of WIFI adaptors from which you can choose:
- Alfa AC1900 WiFi Adapter | Link to Buy
- Alfa Long-Range Dual-Band AC1200 Wireless USB 3.0 | Link to Buy
- TP-Link Nano USB Wifi Dongle 150Mbps High Gain Wireless Network Adapter | Link to Buy
- TRENDnet AC1900 High Power Dual Band Wireless USB Adapter | Link To Buy
- Alfa AWUS036NHA | Link to buy
- Panda Wireless® Mid Range 150Mbps | Link to Buy
For this whole series, I will be using an old adaptor named Panda Pau06 for Pentesting.

🦅 Wireless Hacking: An Introduction
In this blog, we have introduced the basics of wireless hacking. We have covered what WiFi is, some important WiFi terms, the history of WiFi, and how WiFi works. In the next blog, we will start covering wireless attacks.* Join us for an engaging journey that combines learning, awareness, and securing our wireless connections.