
Hey there, fellow hackers!
I hope you’re all doing incredibly well. Now, let’s address a little something that’s been on my mind. Remember that write-up I mentioned earlier? Well, guess what? I made a rookie mistake and deleted it. Oops! My bad, folks. But fear not, because I’m a person of my word, and I’m here to make it right!

Drumroll, please… I present to you the republished version of “Hacking the Hackers: Part 1”! It’s back, it’s better than ever, and it’s just the beginning of an epic hacking saga. Buckle up, folks, because we’re about to embark on a thrilling adventure together.
Many of us often assume that big companies are more secure compared to others, leading to fewer bug bounty hunters actively participating in their programs. However, this is a misconception. Every company, regardless of its size, can have vulnerabilities. The key lies in investing time and effort in understanding the company’s product and becoming familiar with its features.
Now, I have selected HackerOne as my target. HackerOne is a platform with numerous resolved reports, and many hunters are actively participating in bug hunting on this platform. It is well-known, and most people are already familiar with its features. In order to stand out and make a difference, I realized that I needed to take a different approach.
During my research, I came across an interesting report that caught my attention.
By exploring the less commonly used features, I aimed to identify potential vulnerabilities that might have been overlooked by others. This approach allowed me to think outside the box and discover unique security issues that could make a significant impact.
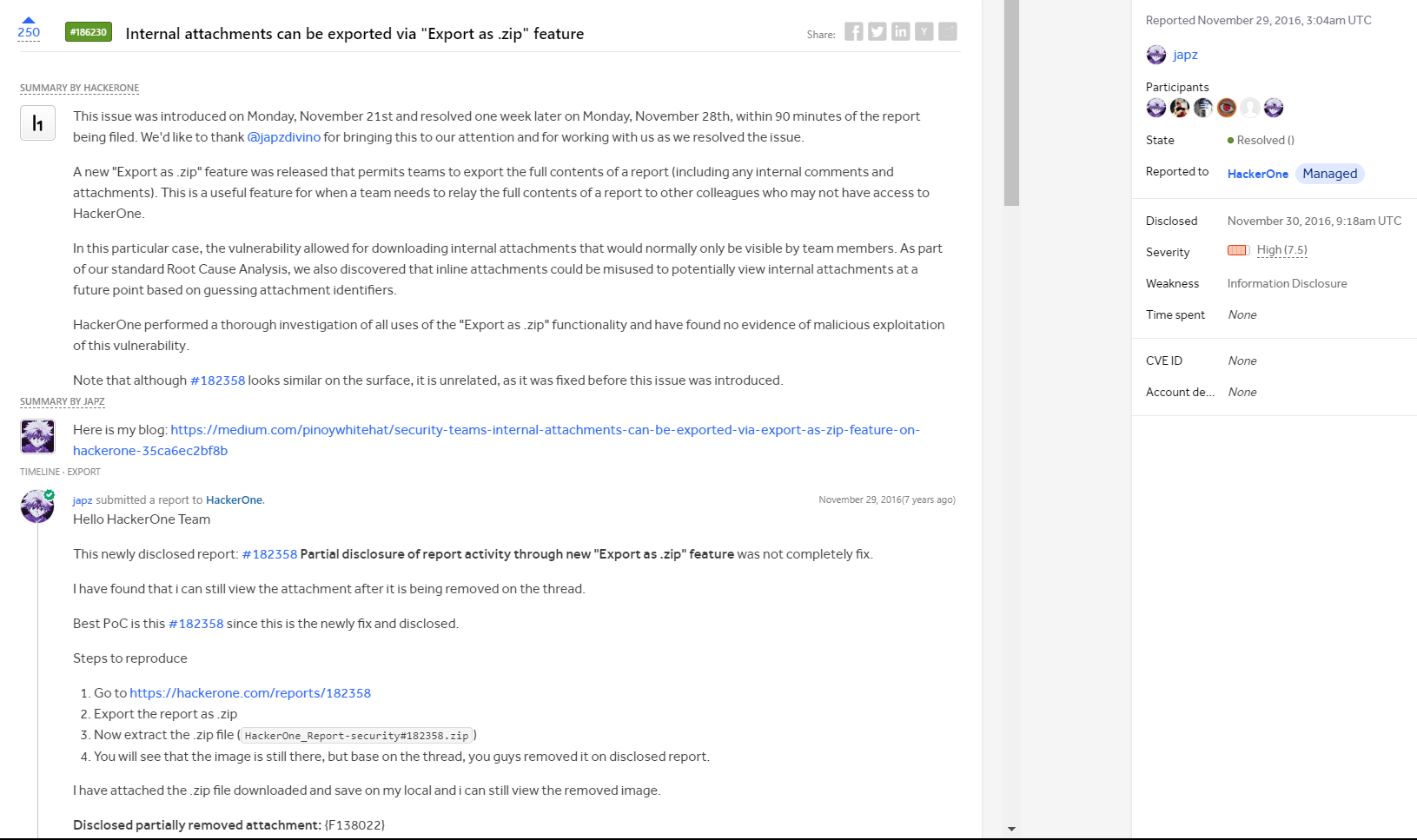
I found this particular report to be intriguing and captivating. Motivated by my curiosity, I decided to explore the export features of HackerOne and began exporting every disclosed report. However, despite my efforts, I couldn’t find any significant vulnerabilities through this approach. However, one day, HackerOne made an intriguing disclosure - a new report came to light.
As usual, I attempted to export the disclosed report as a zip file. After downloading the file and opening it, I initially found nothing of particular interest. Feeling a bit discouraged, I decided to take a break and rest for a while, hoping to regain a fresh perspective.
The following day, while casually scrolling through the contents of the downloaded report, something caught my eye.
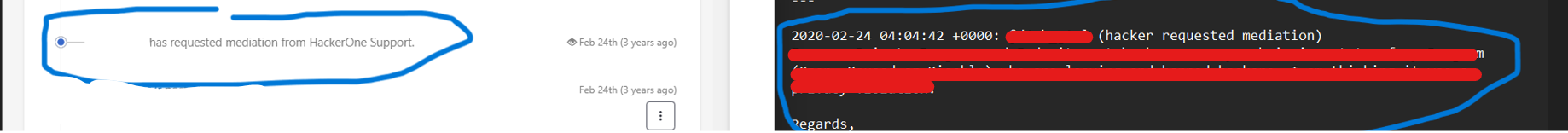
Without wasting any time, I swiftly navigated through the recently disclosed report. I scrolled down with purpose, determined to find the section that contained the crucial Mediation Request. It was within this section that I anticipated potential clues or vulnerabilities. And Noticed Something

I was like what was that:

Filled with a mix of excitement and a hint of uncertainty, I wasted no time in crafting a comprehensive report detailing the vulnerability I had discovered. Despite my initial concern that it might be considered a duplicate, I decided to take the chance and
submitted it to HackerOne.
To my surprise and delight, the report was swiftly marked as “Triaged” by the
HackerOne team.
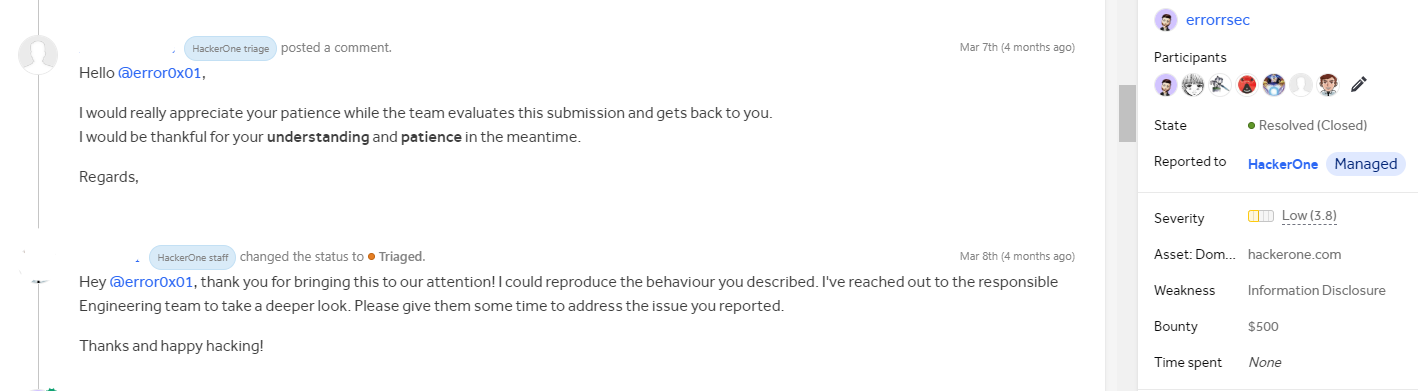
And there you have it, my amazing mates! It’s just the beginning of an extraordinary journey. “Hacking the Hackers: Part 1” has been unleashed, but guess what? There’s so much more in store for all of you! So, stay tuned, buckle up, and get ready for the thrill ride
Hope you all enjoyed the write-up. Stay tuned, more exciting things are on the way!
Don’t forget to follow me on Twitter:
Twitter: errorsec_