In an era where data breaches and cyber attacks are on the rise, ensuring the security and integrity of digital transactions has become paramount. Enter blockchain technology, a decentralized and transparent system that has revolutionized industries ranging from finance to healthcare. At the heart of this revolutionary technology lies cryptographic techniques, acting as the guardians of data privacy and security. This article delves into the pivotal role of cryptographic techniques in enhancing blockchain security, exploring how these techniques work hand in hand with the blockchain to safeguard transactions and protect sensitive information. From the encryption and decryption of data to the verification and validation of transactions, cryptographic techniques play a crucial role in fortifying the blockchain against potential threats. Join us on a journey into the world of cryptography and discover how it contributes to the trust and reliability of blockchain technology.
If you don’t know what is Blockchain, then you can learn by spending just 3 minutes here. Blockchain explained in 3 minutes
Understanding the need for enhanced security in blockchain
The rise of blockchain technology has brought forth a need for enhanced security measures. Traditional centralized systems are vulnerable to attacks, as they rely on a single point of failure. Blockchain, on the other hand, offers a decentralized and distributed approach, making it inherently more secure. However, to ensure the integrity and confidentiality of data, cryptographic techniques come into play. These techniques provide a layer of protection against unauthorized access, tampering, and fraud. By understanding the need for enhanced security in blockchain, we can appreciate the vital role that cryptographic techniques play in safeguarding this revolutionary technology.
Cryptographic techniques provide a means of securing data by transforming it into an unintelligible form that can only be decrypted by authorized parties. Encryption, the process of converting plaintext into ciphertext, is a fundamental cryptographic technique used in blockchain security. It ensures that sensitive data remains hidden from prying eyes and can only be accessed by those with the appropriate decryption keys. Encryption acts as a powerful safeguard against data breaches and unauthorized access, making it an essential component of blockchain security.
Another crucial aspect of blockchain security is the use of digital signatures. Digital signatures provide a way to verify the authenticity of transactions and ensure that they have not been tampered with. By utilizing asymmetric encryption algorithms, digital signatures create a unique identifier for each transaction, making it virtually impossible to forge or alter the transaction details. This not only adds an extra layer of security to blockchain transactions but also enhances the overall trust and reliability of the technology.
Overview of cryptographic techniques
Before delving deeper into the role of cryptographic techniques in enhancing blockchain security, let’s take a moment to understand the basics of these techniques. Cryptography is the science of secure communication, encompassing various methods for protecting information from unauthorized access. It relies on mathematical algorithms and computational principles to transform data into a secure format.
There are two primary types of cryptographic techniques: symmetric and asymmetric encryption. Symmetric encryption, also known as secret-key encryption, uses a single key for both encryption and decryption. This key must be kept secret and shared securely between parties involved in the communication. Asymmetric encryption, on the other hand, utilizes a pair of keys: a public key for encryption and a private key for decryption. The public key can be freely distributed, while the private key must be kept secret.
In addition to encryption, cryptographic techniques also include other essential elements such as hash functions, public key infrastructure (PKI), and zero-knowledge proofs. Hash functions are mathematical algorithms that transform data into a fixed-length string of characters. They play a vital role in blockchain security by ensuring data integrity and providing a unique identifier for each block of transactions. PKI, on the other hand, establishes a trusted network of digital certificates and public keys, enabling secure communication and authentication in blockchain transactions. Zero-knowledge proofs allow a party to prove the knowledge of certain information without revealing the actual information itself, adding an extra layer of privacy and security to blockchain transactions.
Role of encryption in blockchain security
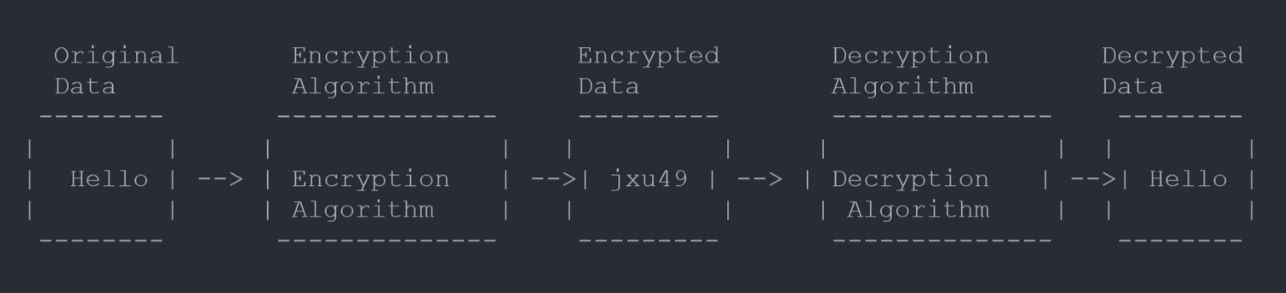
Encryption serves as a cornerstone of blockchain security, providing a robust mechanism for protecting sensitive data. When a transaction is initiated on the blockchain, encryption is utilized to transform the transaction details into an unreadable format. This ensures that even if the data is intercepted, it remains unintelligible to unauthorized individuals.
In blockchain, encryption is particularly crucial when it comes to storing sensitive information such as personal data or financial details. By encrypting this data, blockchain technology ensures that it remains secure and confidential, reducing the risk of identity theft or unauthorized access. Encryption algorithms like Advanced Encryption Standard (AES) or Elliptic Curve Cryptography (ECC) are commonly used in blockchain systems to provide a high level of security.
Encryption also plays a significant role in securing blockchain networks against potential attacks. By encrypting the communication between nodes and ensuring that only authorized participants have access to the decryption keys, blockchain technology establishes a secure and trusted environment for data exchange. This prevents malicious actors from intercepting or tampering with the data, enhancing the overall security and reliability of the blockchain network.
Importance of digital signatures in blockchain
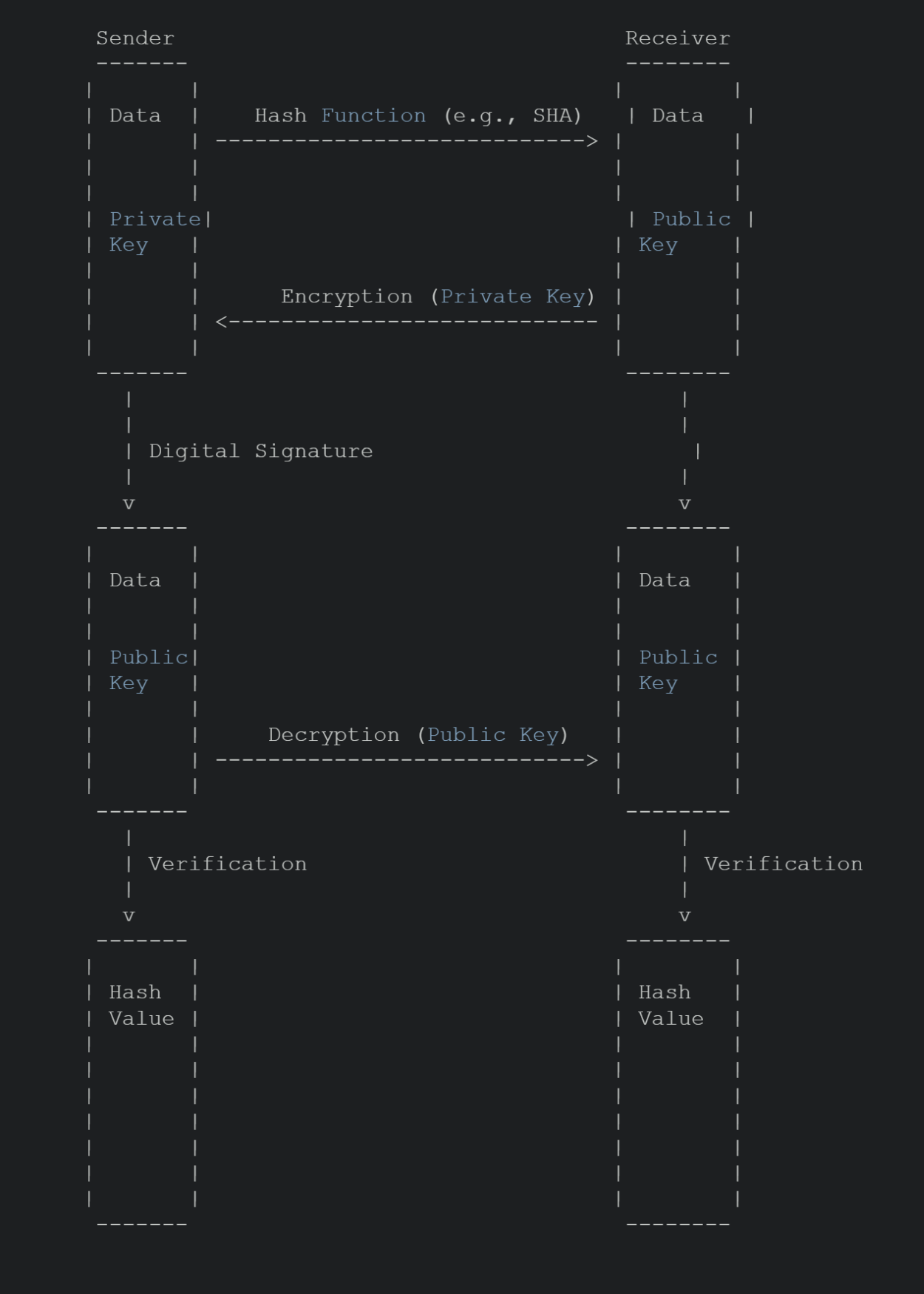
Digital signatures are a vital component of blockchain security, providing a means to verify the authenticity and integrity of transactions. In a blockchain network, every transaction is accompanied by a digital signature, which serves as a unique identifier for that transaction. This digital signature is generated using the private key of the sender and can be verified using the corresponding public key.
The use of digital signatures ensures that transactions on the blockchain cannot be tampered with or forged. Each digital signature is unique to a specific transaction and cannot be reused or replicated. This adds an extra layer of trust and reliability to the blockchain network, as any attempt to alter the transaction details would result in an invalid digital signature.
Digital signatures also enable non-repudiation, meaning that the sender of a transaction cannot deny their involvement in the transaction. As the digital signature can only be created using the sender’s private key, it serves as irrefutable proof of the sender’s identity and intent. This strengthens the integrity of the blockchain network and provides a robust mechanism for transaction verification.
Hash functions and their significance in blockchain security
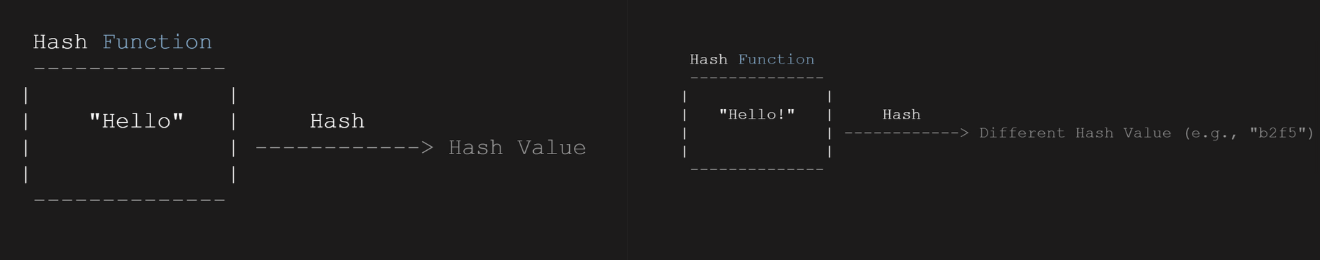
Hash functions are cryptographic algorithms that play a crucial role in ensuring the integrity and security of blockchain transactions. A hash function takes an input of any size and produces a fixed-size output, often referred to as the hash value or hash code. The output is unique to the input, meaning that even a small change in the input will result in a completely different hash value.
In blockchain, hash functions are used to create a unique identifier, or hash, for each block of transactions. This hash serves as a digital fingerprint of the block, allowing for easy verification of its integrity. Any modification to the transactions within the block will result in a different hash value, indicating that the block has been tampered with.
By linking each block to the hash of the previous block, blockchain technology creates an immutable and tamper-proof record of transactions. Any attempt to alter the data within a block would require recalculating the hash values for that block and all subsequent blocks, making it computationally infeasible to tamper with the blockchain. Hash functions thus provide a crucial mechanism for ensuring the security and integrity of blockchain transactions.
Public key infrastructure (PKI) in blockchain
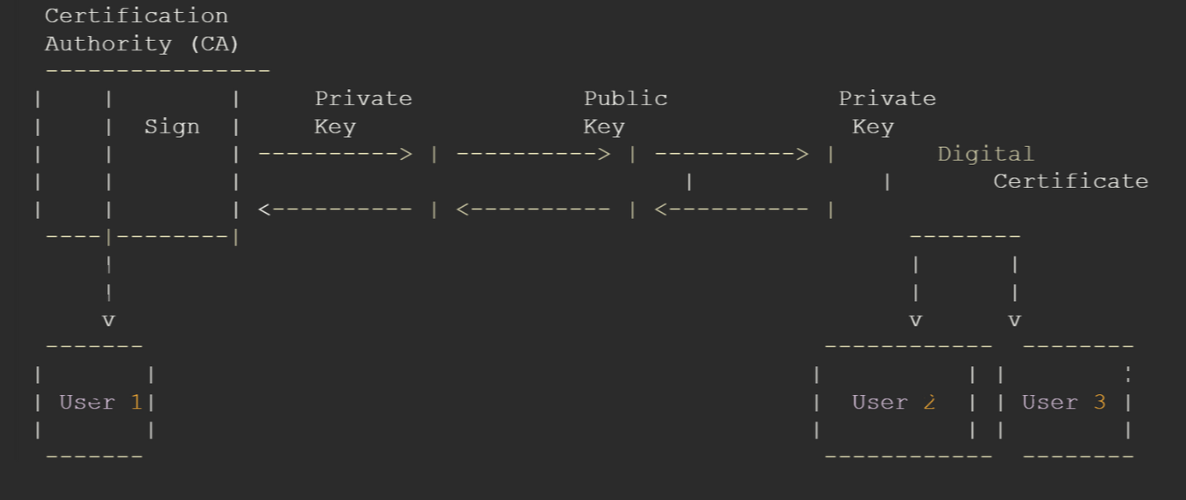
Public key infrastructure (PKI) is a critical component of blockchain security, providing a framework for secure communication and authentication. PKI utilizes digital certificates and public keys to establish trust in a network, ensuring that participants can securely exchange data and verify each other’s identities.
In a blockchain network, PKI enables secure communication between nodes and ensures that only authorized participants can access and contribute to the blockchain. Each participant in the network possesses a unique public-private key pair, with the public key acting as their digital identity. When a participant initiates a transaction, their public key is used to verify their identity and ensure that they have the necessary permissions to perform the transaction.
PKI also plays a significant role in transaction validation and consensus mechanisms in blockchain networks. By utilizing digital certificates, blockchain systems can establish a trusted network of participants and ensure that only valid transactions are added to the blockchain. PKI enables secure and efficient consensus algorithms, such as Proof of Stake (PoS) or Delegated Proof of Stake (DPoS), by providing a mechanism for verifying the identity and authority of participants.
Zero-knowledge proofs and their impact on blockchain security
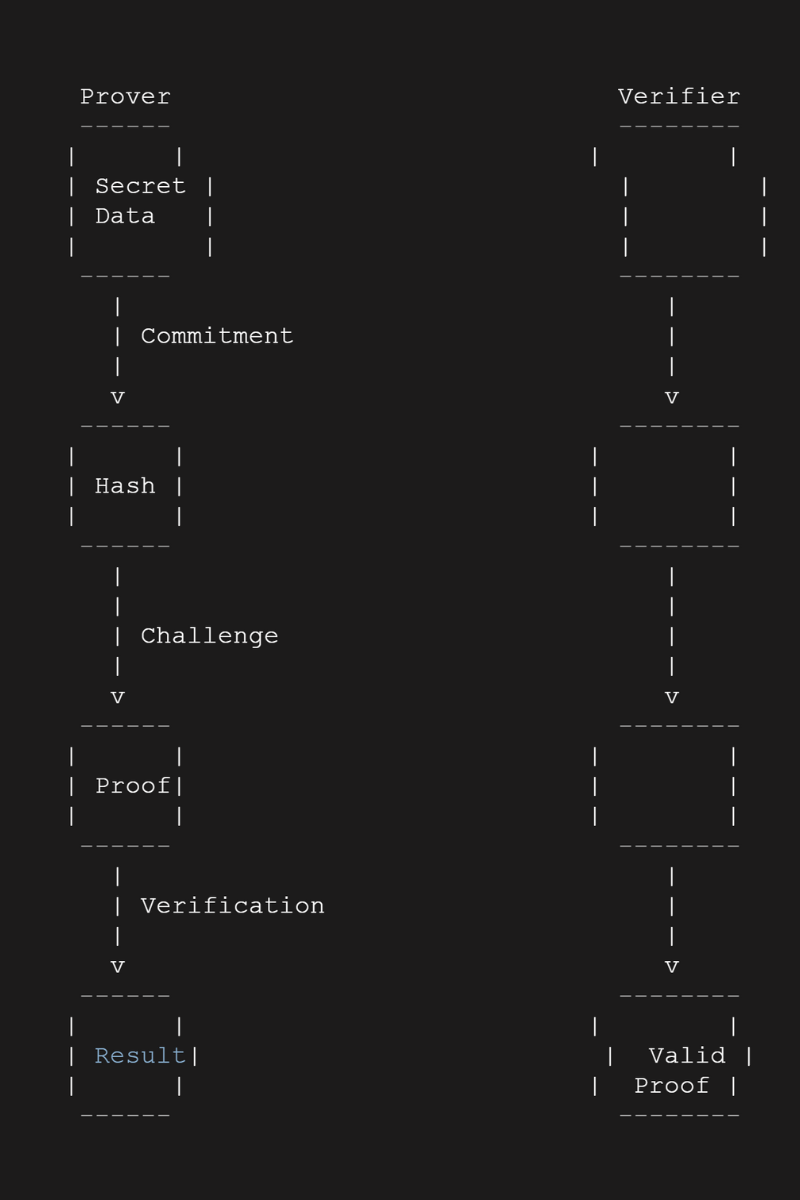
Zero-knowledge proofs (ZKPs) are cryptographic protocols that allow one party to prove the knowledge of certain information without revealing the actual information itself. This concept has significant implications for blockchain security, as it enables privacy-preserving transactions and verifiable computations.
In blockchain, ZKPs can be used to prove the validity of a transaction without revealing the transaction details or the parties involved. This provides an additional layer of privacy and confidentiality, making blockchain technology more appealing for applications that require secure and anonymous transactions.
ZKPs also play a role in ensuring the integrity of computations performed on the blockchain. By utilizing ZKPs, blockchain systems can verify the correctness of computations without revealing the actual inputs or outputs. This enables secure and verifiable smart contracts, ensuring that the results of computations are trustworthy and tamper-proof.
Challenges and limitations of cryptographic techniques in blockchain security
While cryptographic techniques play a crucial role in enhancing blockchain security, they are not without their challenges and limitations. One of the primary challenges is the potential for quantum computing to break existing cryptographic algorithms. Quantum computers have the potential to solve complex mathematical problems much faster than classical computers, posing a threat to the security of current encryption algorithms.
To address this challenge, researchers are exploring the development of quantum-resistant cryptographic algorithms that can withstand attacks from quantum computers. These algorithms aim to provide a secure and future-proof solution for blockchain systems, ensuring that the security of transactions remains intact even in the face of quantum computing advancements.
Another limitation of cryptographic techniques in blockchain security is the reliance on key management. Cryptographic systems require the secure generation, storage, and distribution of encryption keys, which can be a challenging task. If the keys are compromised or mishandled, the security of the blockchain network could be compromised. Key management solutions and best practices are essential for ensuring the long-term security and integrity of blockchain systems.

Future trends in blockchain security and cryptography
As blockchain technology continues to evolve, so too will the role of cryptographic techniques in enhancing its security. One of the emerging trends is the integration of multi-party computation (MPC) protocols into blockchain systems. MPC allows multiple parties to jointly compute a result without revealing their individual inputs, providing an additional layer of privacy and security.
Another trend is the exploration of homomorphic encryption in blockchain. Homomorphic encryption allows computations to be performed on encrypted data, without the need to decrypt it. This enables secure and privacy-preserving computations on blockchain systems, opening up new possibilities for secure data processing.
Additionally, advancements in post-quantum cryptography will play a crucial role in enhancing the security of blockchain against future quantum computing threats. Researchers are actively working on developing new cryptographic algorithms that can withstand attacks from quantum computers, ensuring the long-term security and integrity of blockchain systems.
Conclusion
Cryptographic techniques are the guardians of data privacy and security in blockchain technology. From encryption to digital signatures, hash functions to PKI, these techniques play a pivotal role in fortifying the blockchain against potential threats. As the need for enhanced security in digital transactions continues to grow, cryptographic techniques will remain at the forefront of blockchain security. By understanding the role of cryptography in blockchain, we can appreciate the trust, reliability, and integrity that this revolutionary technology offers. As blockchain technology continues to mature, advancements in cryptographic techniques will pave the way for a more secure and trusted digital future.