Configuring Android emulator/Device can be Quite hectic Process To Properly Setup. So here I made a simple Step By Step Guide To Configure The Emulator With Burp Proxy.
So lets Get Started :
1.First of all we need A Emulator Device . We can Choose any emulator like Android studio, NOX, Genymotion.
- I’m using The NOX Emulator .

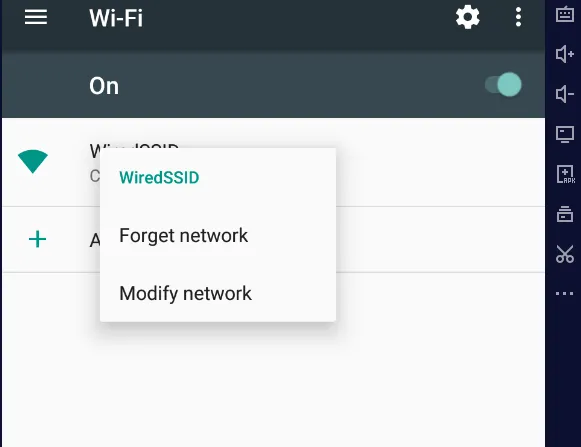
3.Click On Wifi And then Select Modify Network Options.
4.Fire Up Your Burp And Then navigate to The Proxy Tab > Proxy Settings .
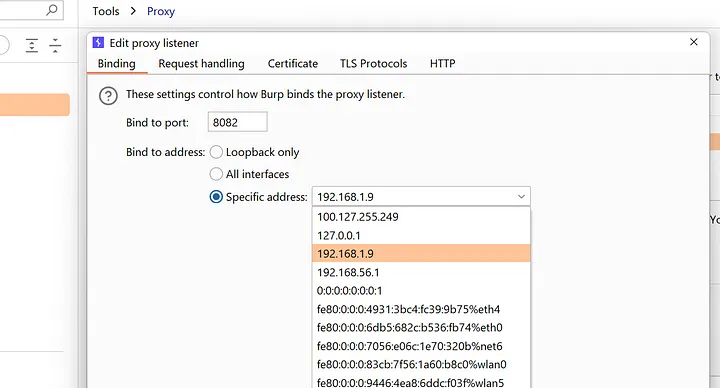
- Set Up the Port As you wish Too & then Click On Specified Address .
6.Select the IP With 192.168.1.* can be Different in Your machine .Select accordingly.
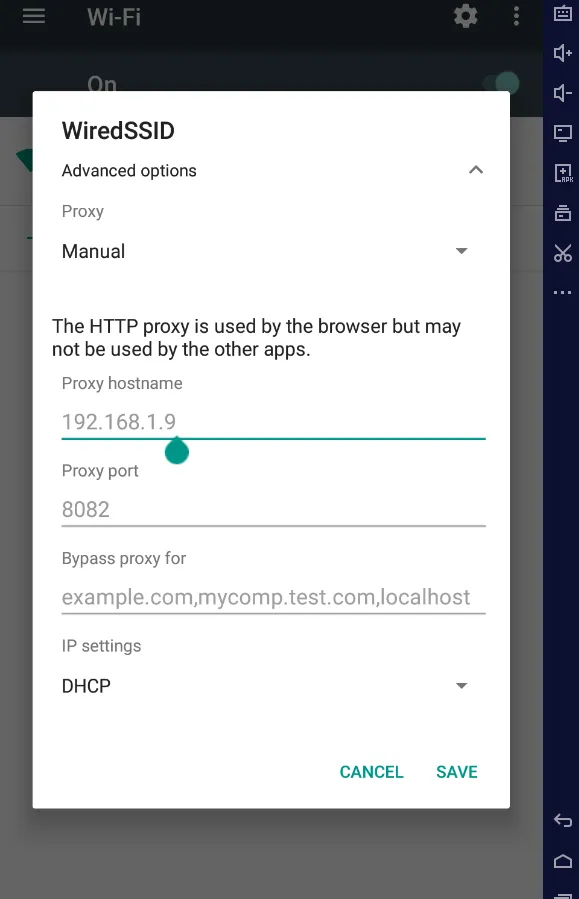
- Then Again Switch To Emulator Click On Advanced Options & Set the Configuration as Specified in Burp Proxy Section.
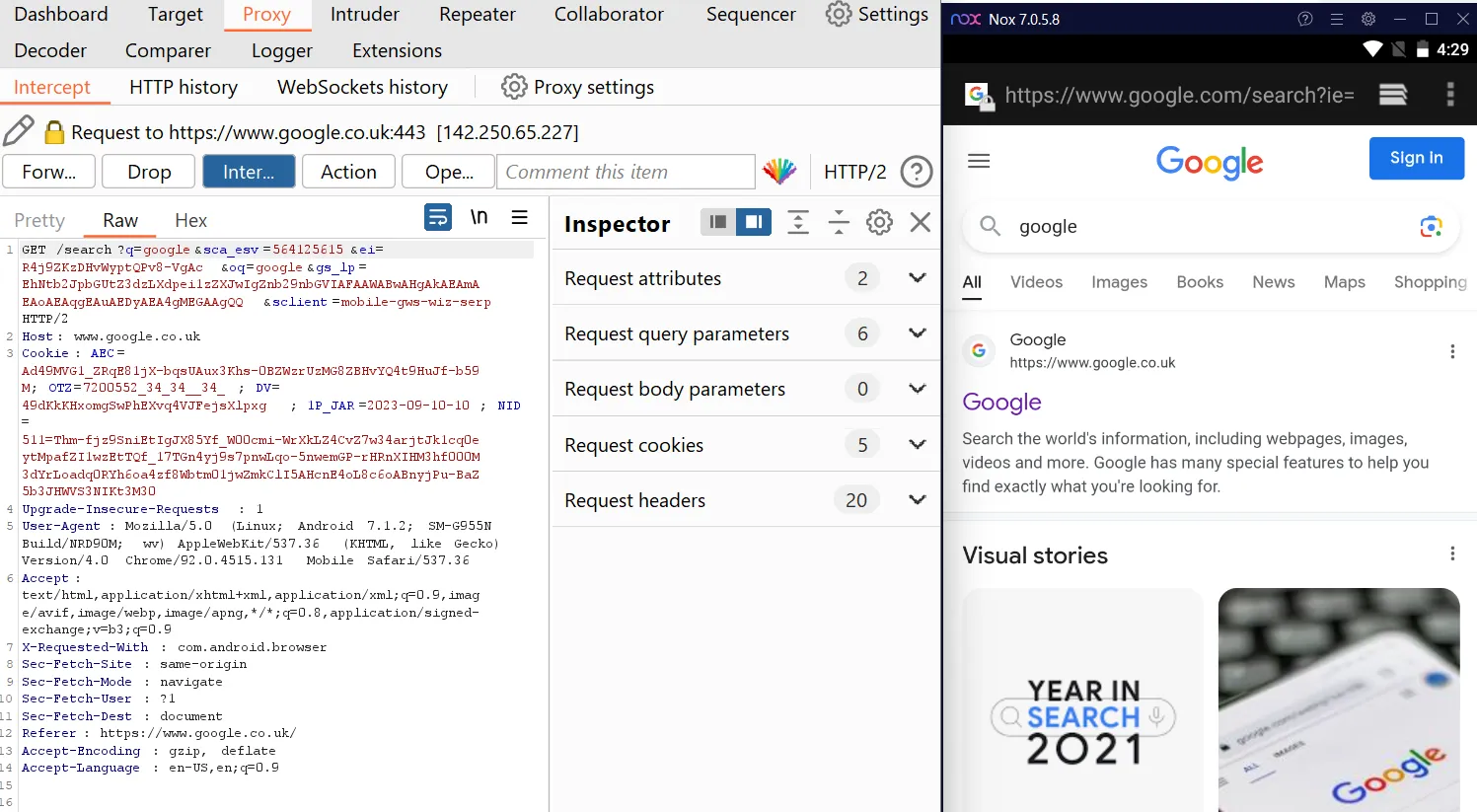
Now we will test If the Proxy Is Properly Setup or not. As shown below The Network is being Intercepted Via Burp.
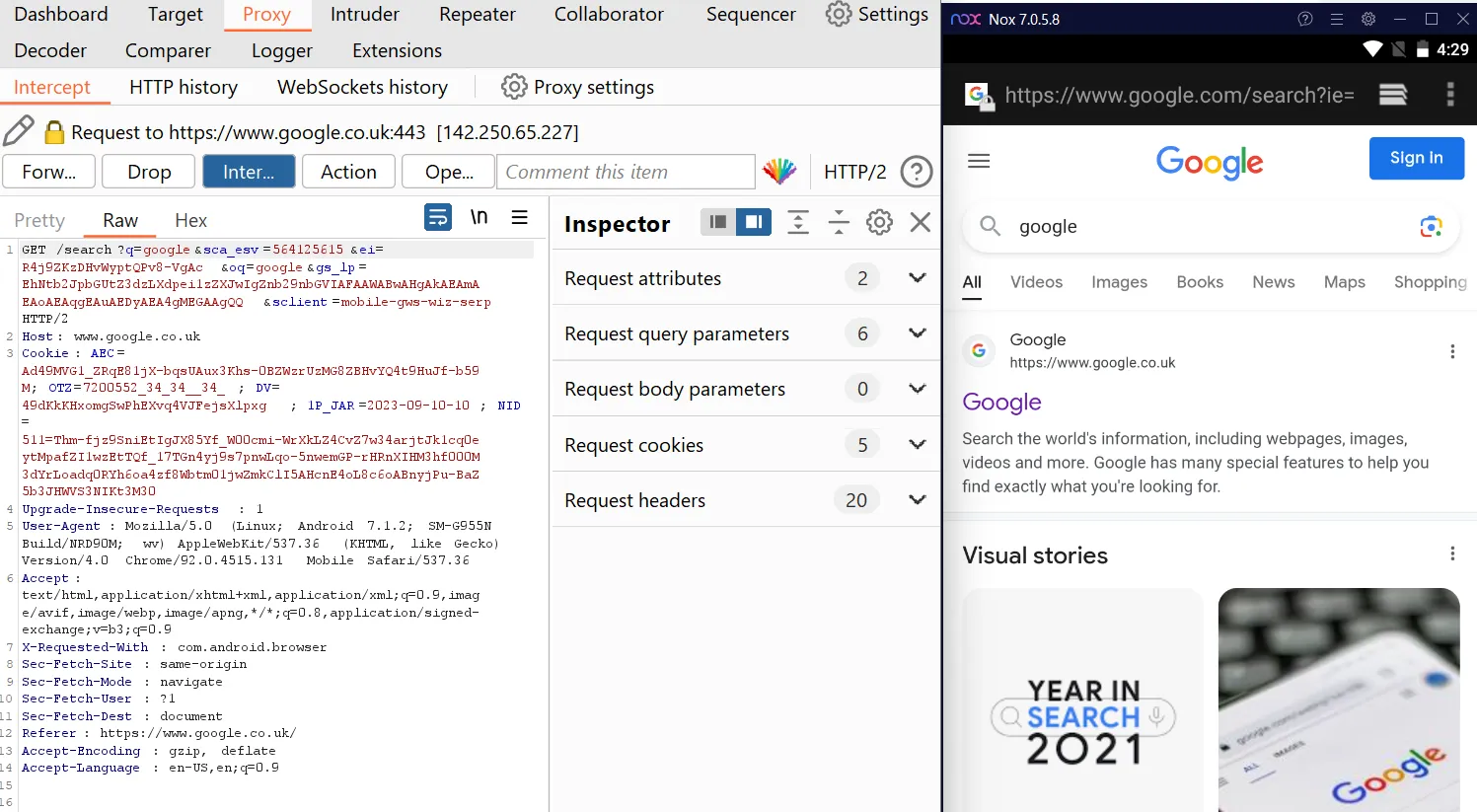
Note: Please Note That I’m Assuming that Developer Options is enabled And Usb Debugging Also Enabled On the Emulator.
In The Next Part I’ll Be Sharing How To Set-Up/install the Trusted Certificates To The Android For Intercepting the Web As Well As App Traffic.
If you Like this Write-up Do clap and share With Other fellow Hacker’s
Till Then Do Follow Me .
Twitter : bug_X_hunter
Telegram : Private group
Stay Tuned !!!
Android hacking has become one of the most popular topics in cybersecurity because of one simple fact: not everyone has a computer. But you know what everyone has? A mobile phone. And you can almost guarantee that device is an Android. Every kid with an Android phone at age 14 who is playing Android games, will ultimately find someone who is cheating in one of those games, and once their curiosity is peaked, you better bet they’re searching “android game hacking” on Google.
It’s become an insanely popular topic and all forms of android hacking are based on the same techniques. For example, in this article we showed how to use burp suite to penetration test an android app. Instead of burpsuite, you can also use Frida to hack Android games, in the same manner, as they teach you at Guided Hacking. Reversing Android malware is similar too, it’s amazing how so many skills can crossover into different realms of cybersecurity.