In The First Part I’ve Shared about How to Configure The Android Emulator/Device With Proxy (Burp)
I’d recommend If you haven’t checked The First Part. Check It out .
Here’s the link to the Series-I Part .
So Let’s Get Started With our Second Part:
- Fire Up Your Burp Then Navigate to The Proxy Tab > Proxy Settings.
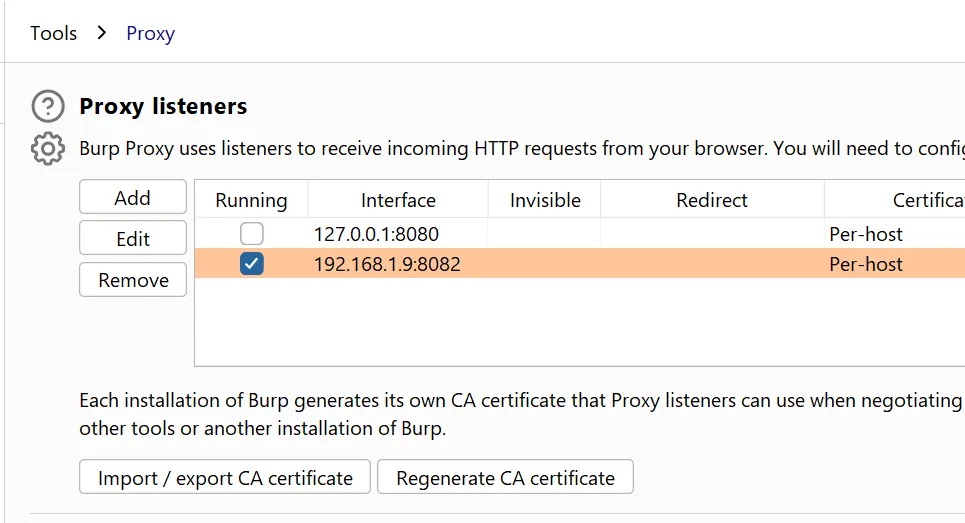
- Click On Import/export CA certificate. Click On Certificate In DER Format.
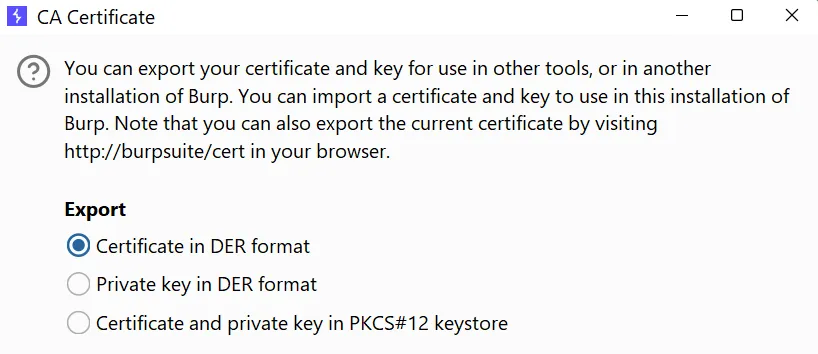
- Then Select The Path To Save then Certificate. Make Sure You Should Change The Extension to “CER”.
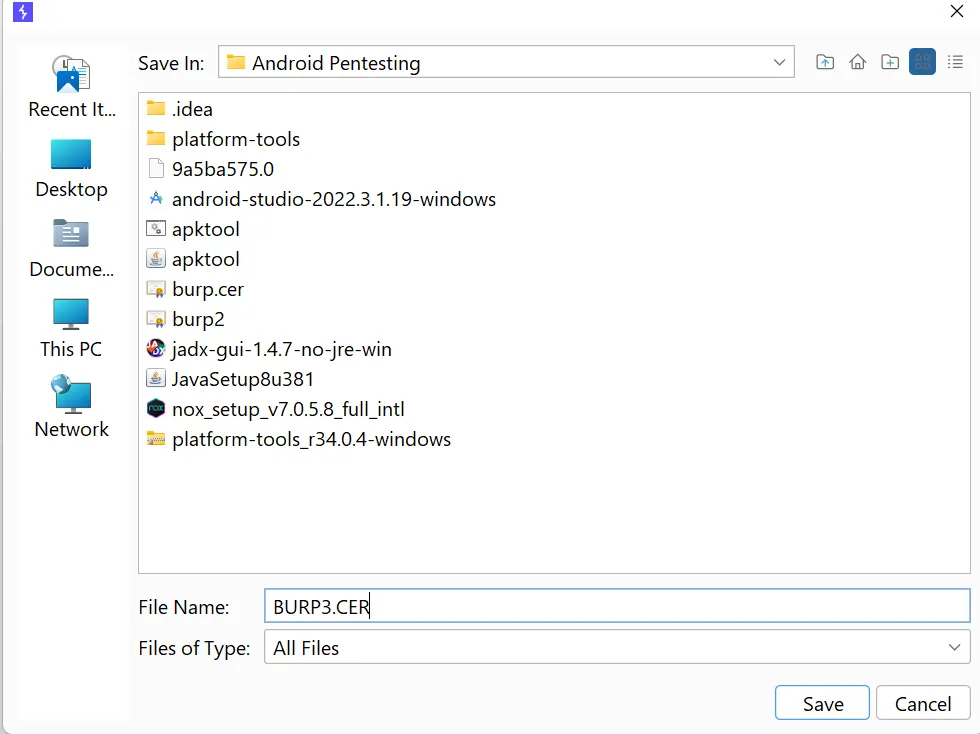
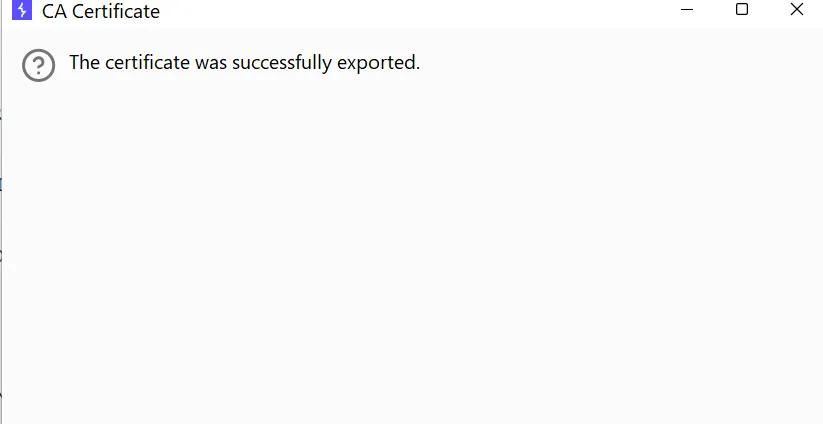
- After saving It Will Export Successfully to your Desired Path.
- Next Run Your Emulator In The Emulator . We can Easily Drag & Drop The Cert To The Android’s Folder.

- Next Navigate to Android Settings > Security > Credential Storage.

Click On Install from SD card . Select Burp.CER
Then name The Cert As You want And Set as Vpn&App uses.
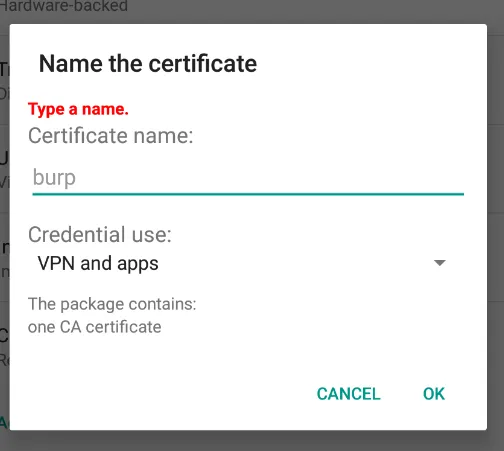
- Now we Can See that Cert Has been Installed Successfully.
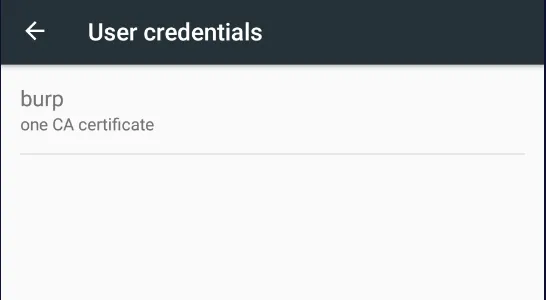
As Now We Can easily Intercept The Web Trafffic Via Burp Proxy .
If you Like this Write-up Do clap and share With Other fellow Hacker’s
Till Then Happy Hacking .
Twitter : bug_x_hunter
Any Queries Do Reach me out.
Note : Its Only For The Web Traffic By this We cannot Intercept The App Traffic .
For That Stay Tuned For The Next Part .