
Hello, missed followers! It’s been a while, and I want to start by sincerely regretting taking an unexpected break. 😞 You were eagerly awaiting new content, but I was unable to post it since my reliable laptop made the decision to take a short vacation of its own. But what’s this? 🤔 We won’t be hindered any longer by unforeseen technological difficulties because I’ve returned and the laptop has been fixed.
I’m happy to share some good news with you. For each of you, I have been preparing something unique. We’re starting a brand-new blog series today, and it’s going to completely disrupt the game. 💥 The focus of this series is on Burp Suite’s potential as the ultimate tool for security enthusiasts and hackers. 🛡️ The purpose of “Burp Suite for Hackers 101” is to give you the information and abilities necessary to use Burp Suite to the fullest extent possible. This series will have something for everyone, regardless of your level of experience or desire to improve. 📈
In this blog’s opening post, we’ll establish the groundwork by delving into Burp Suite’s fundamentals. We’ll go over setup and configuration to make sure you’re prepared to investigate the tool’s potential. 🔍 Consider it the start of a trip that will immerse us further in the area of web application security testing. 🌎
From the following blog on, we’ll delve deeper into Burp Suite, covering its different features, methods, and cutting-edge advice that will make you a true expert. This series will serve as your road map whether your goal is to improve your security talents, engage in ethical hacking, or simply comprehend web application risks. 🔐
I hope you’re as excited as I am to start this journey together! 🤝 Let’s go! 🚀
🐞 Introduction
Burpsuite is a security tool that is primarily utilised for pentesting web application security. The organisation Portswigger created it. Among security experts and bug bounty hunters, it is well known.
It is used to find and take advantage of security flaws in web applications. It is a tool with many different features, including target analysis, extender and spidering, intruder, repeater, collaborator, and repeater.
In simple terms, Burp Suite captures and enables manipulation of all the HTTP/HTTPS traffic between a browser and a web server.
By intercepting requests, users have the flexibility to route them to various components within the Burp Suite framework, which we will explore in upcoming sections.
It also provides the ability to add extra features, either by utilising an already-existing extension or by creating a custom extension. In each blog, we will delve into more detail. ♥
🔥 Additionally, Portswigger offers Web Security Academy, a fantastic resource for learning web application pentesting. There, you may get detailed information on the different issue kinds.
🐞 Burp Editions
There are different editions of Burpsuite offered by the Portswigger. You should have a basic understanding of the different editions to choose from.
🛡️ Burp Suite Community Edition
This is the best suited for personal use, it is free of cost and offers basic web security testing capabilities. It also functionality of content discovery. It has a friendly-user interface for new users to accomodate easily.
Interface:
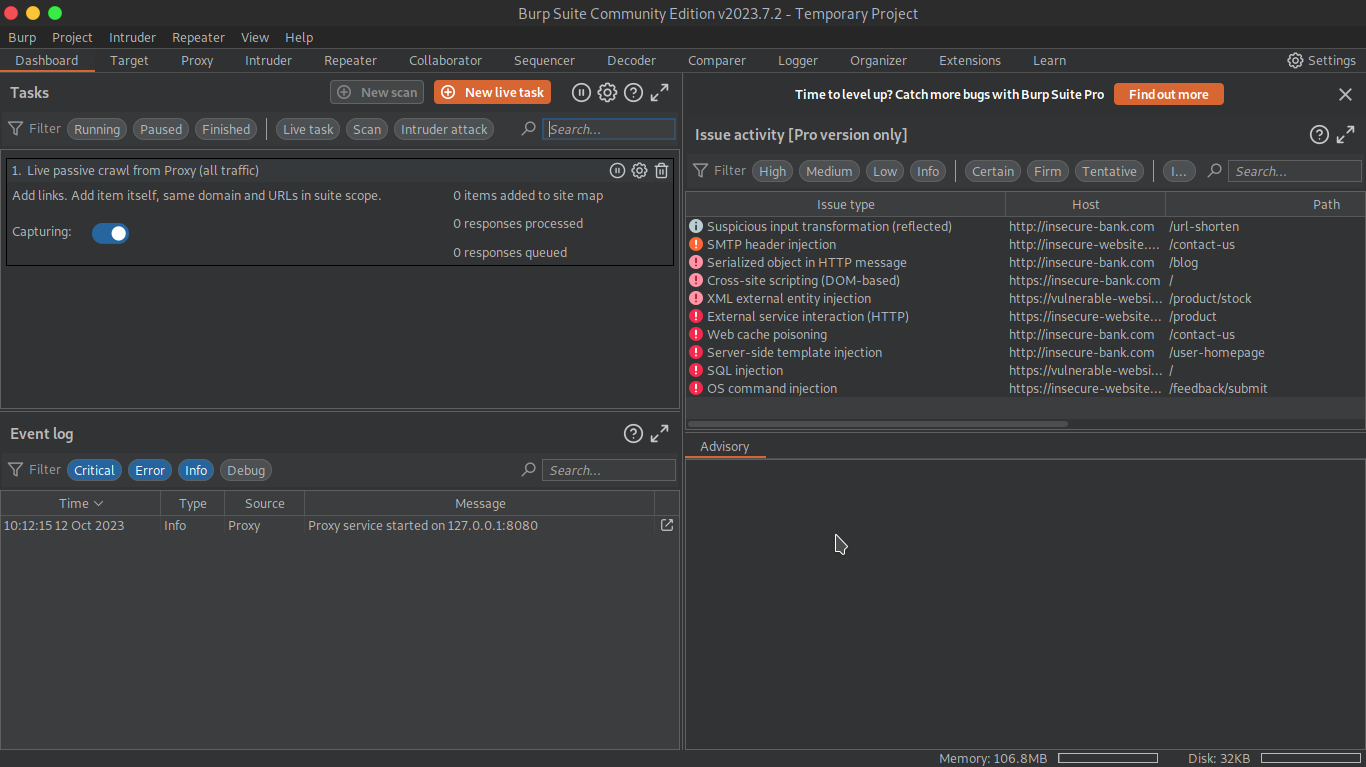
🛡️ Burp Suite Professional Edition
It is more advanced and fully-featured version, which includes all the features available in the community edition and adds more features like advanced scanning, content discovery and more extensive reporting capabilities.
Some of the features include
- Faster brute-forcing and fuzzing
- Deploy custom sequences of HTTP requests containing multiple payload sets
- Browser powered scanning
- Support for the latest OWASP Top 10 vulnerabilities : It searches for endpoints for OWASP Top 10 itself.
🔥 The pricing of the Burp professional is $449 of today.
🛡️ Burp Suite Enterprise Edition
It is best suited for the organizations of all sizes. it integrates with a variety of other tools, such as issue trackers, continuous integration (CI) servers, and continuous delivery (CD) servers and vulnerability.This makes it easy to automate security testing throughout the development process. It provides a centralized management and control allowing admins to oversee security across the organization.
Some of the features include:
- Automation capabilities to streamline vulnerability identification
- API support for automation and tool integration.
- Collaborative tools for multiple team members to work simultaneously.
Interface:
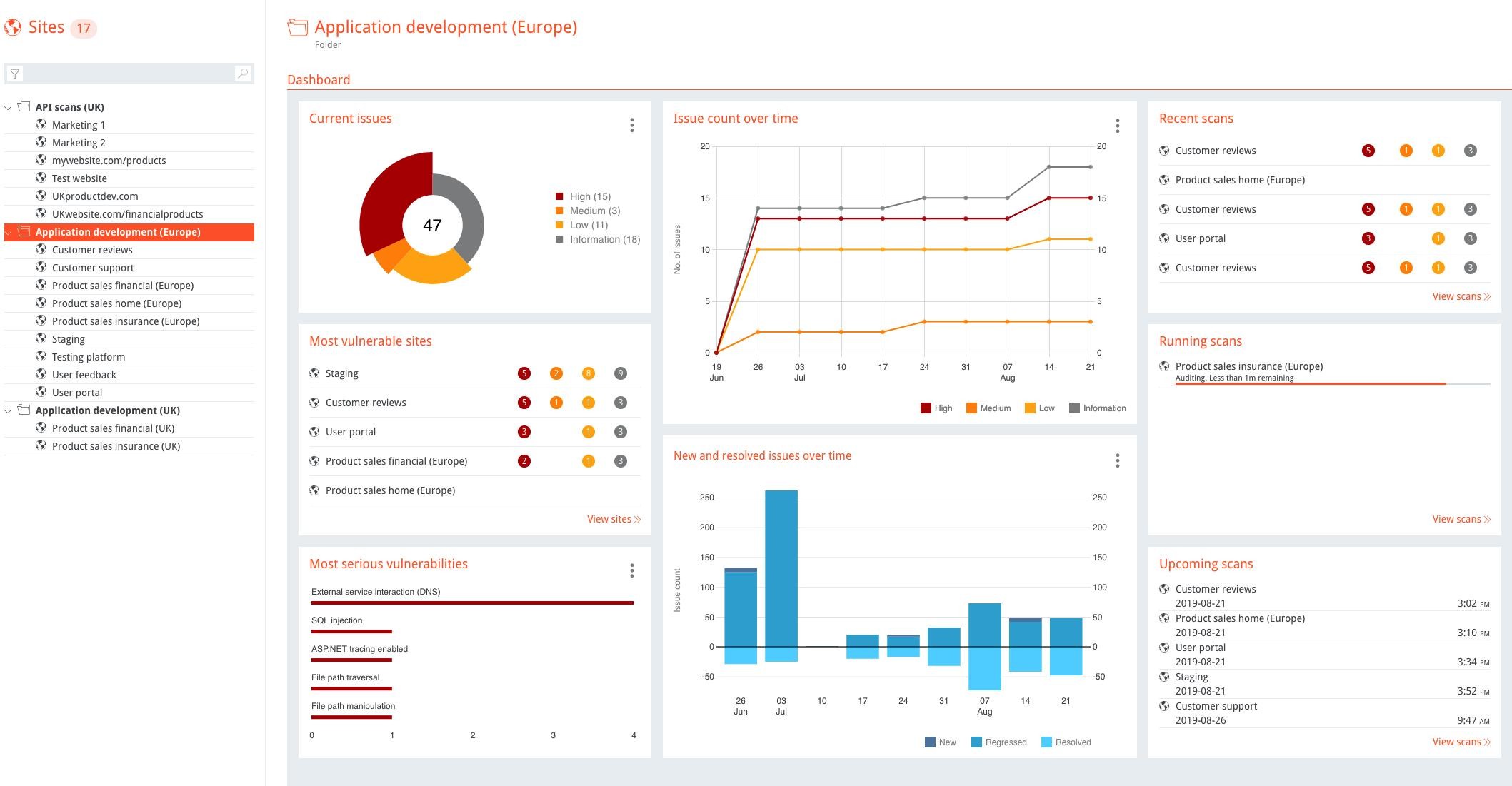
Due to requiring a license for the Professional and Enterprise editions, we will focus on the core feature set provided by the Burp Suite Community Edition.
Features of Burpsuite Community Edition
Burp Suite Community nevertheless offers an outstanding selection of tools that are very helpful for web application testing, despite having a more constrained feature set than the Professional edition.
Some of the key features are :
- Intercepting proxy: All HTTP(s) traffic between your browser and the intended web application can be intercepted by Burp Suite, allowing you to examine and alter requests and responses.
- Spider: The Spider tool can automatically scan and find all of a web application’s pages and resources, assisting you in determining its attack surface.
- Repeater: The Repeater tool makes it simple to test various attack scenarios by allowing you to resend individual requests with varied values.
- Sequencer: The Sequencer tool can be used to test a web application’s sequence sensitivity, which can be helpful for locating vulnerabilities like CSRF.
- Intruder: The Intruder tool can be used to launch automated attacks against web applications, such as brute-force attacks and fuzzing attacks.
- Decoder: The Decoder tool can be used to decode and encode data in a variety of formats, such as Base64, hexadecimal, and URL encoding.
- Comparer: The Comparer tool can be used to compare two pieces of data, such as two HTTP requests or responses, to identify differences.
🐞Installation
As this blog is from bottom to top , so we will also discuss the process to install the editions .
Installation on Linux (Debian/Ubuntu)
Download Burp Suite:
- Open your web browser and go to the Burp Suite download page.
- Select the “Linux” version and click the download button to save the file (e.g.,
burpsuite_community_linux_vxxx.sh) to your local directory.
Open Terminal:
- Open a terminal window on your Linux system.
Navigate to the Download Directory:
- Use the
cd command to navigate to the directory where you downloaded the Burp Suite installation file. For example:
cd /path/to/download/directory
- Make the Installer Executable:
- Use the
chmod command to make the downloaded installer executable:
`chmod +x burpsuite_community_linux_vxxx.sh’
- Run the Installer:
- Follow the Installation Wizard:
- The installer will launch an installation wizard. Follow the on-screen instructions to complete the installation.
- Launch Burp Suite:
- After the installation is complete, you can start Burp Suite from the terminal or your application launcher.
Windows
- Download Burp Suite:
- Open your web browser and go to the Burp Suite download page.
- Select the “Windows” version and click the download button to save the installer (e.g.,
burpsuite_community_vxxx.exe) to your computer.
- Run the Installer:
- Locate the downloaded installer and double-click it to run the installation.
- Follow the Installation Wizard:
- The installation wizard will guide you through the setup process. Follow the on-screen instructions.
- Launch Burp Suite:
- After the installation is complete, you can start Burp Suite from your Start menu or desktop shortcut.
🐞 Configuring your browser to work with Burp Suite
It’s essential to set up your web browser to function properly with Burp Suite before you start using it to assess the security of web applications. This step is crucial because Burp Suite serves as a proxy between your browser and the web application you are testing, enabling you to intercept and modify web traffic.
To do this, we will taking of a browser’s extension which is foxyproxy, which is a open-source browser extension that allows users to manage multiple proxy servers and allows to switch between them. It allows for easy proxy configuration.
Steps
Go to the browser extensions and search for “foxyproxy” in your browsers.
Links: 🦊Link
Chrome : 🦊Link
After installation you will see foxyproxy in your extension manager and then click on the options up there. You should land to page like this:
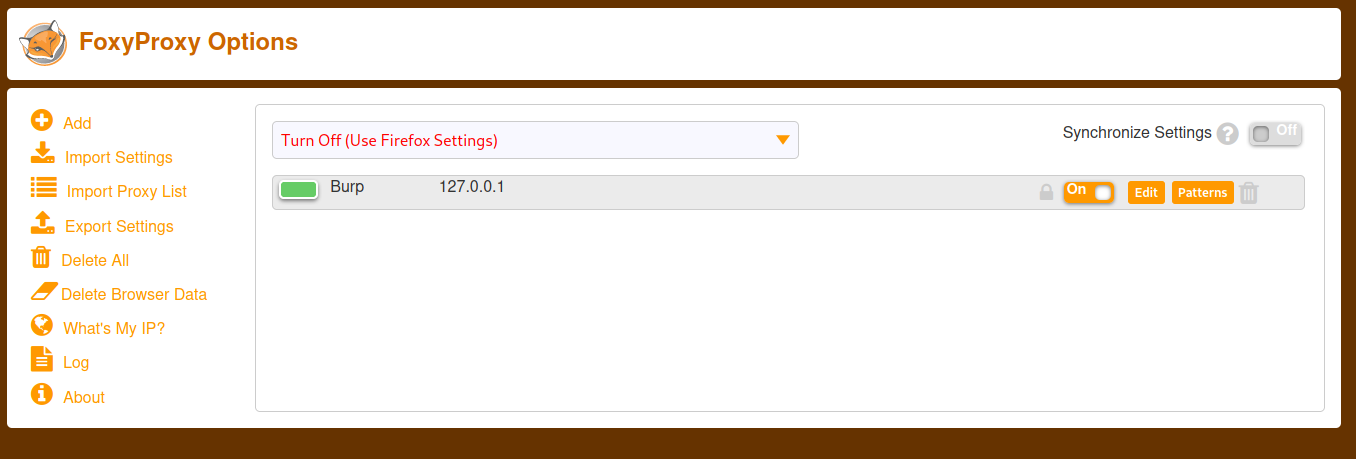
Click on add new proxy and setup as shown in the screenshot.
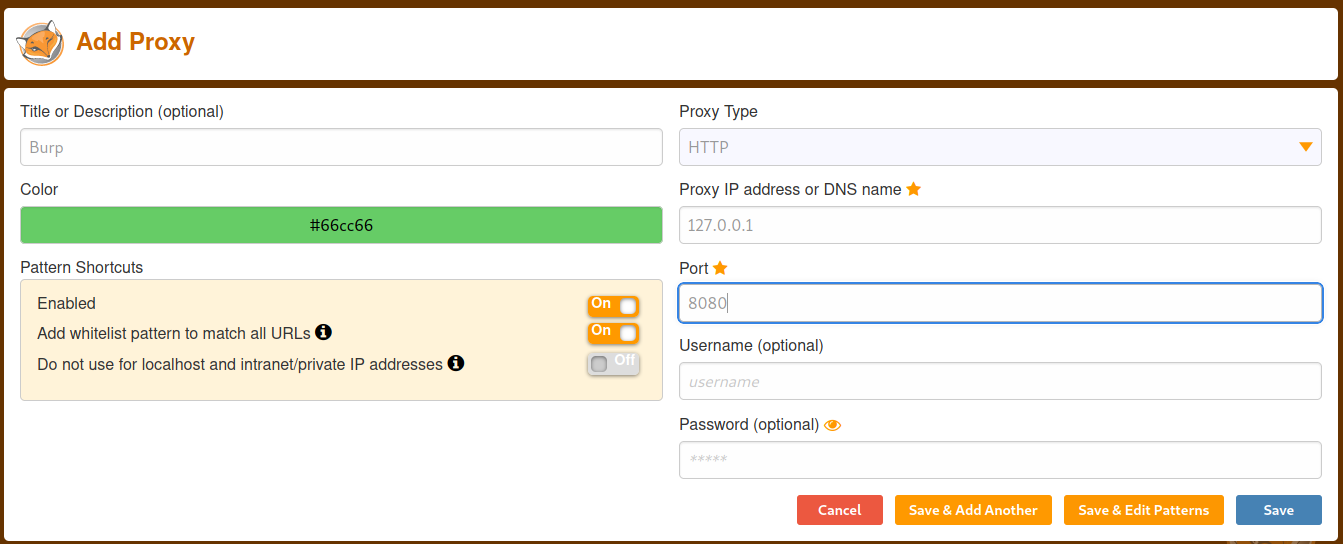
Click on save and move forward.
Now turn on burp and then go to this url http://127.0.0.1:8080on your browser after selecting the burp proxy in the foxyproxy extension.

Click on the CA CERTIFICATE button to download a certificate, which is a certificate issued by burp and we’ll have to install it in our external browser which we will be using.
After downloading the certificate , go to your browser and search certificates up there.
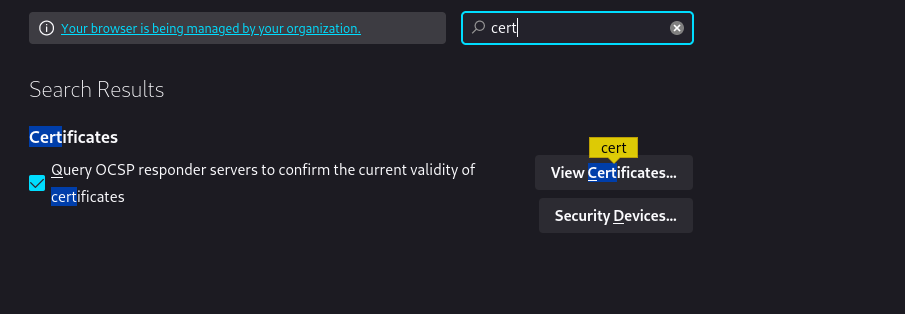
Click on view certificates and in the new window poped up , click on import certifcates and click on install cetificate.
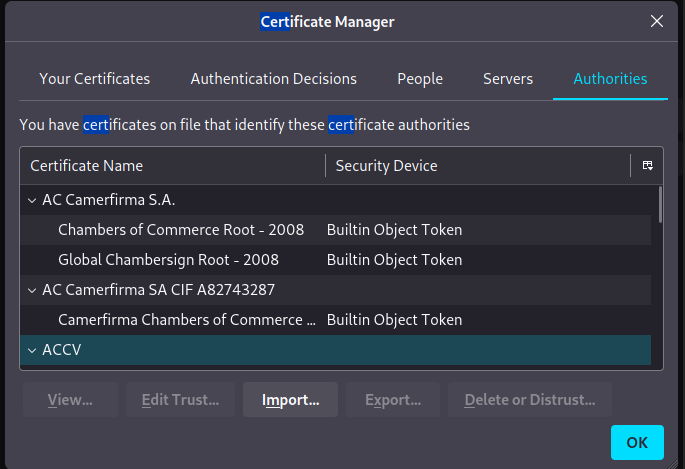
After you have done this , you are good to go, now you can use burp to intercept requests and do all kind of actions.
🤞🏻Conclusion
The first blog in our “Burp Suite for Hackers 101” series has come to a conclusion. There is still a lot to discover on this expedition, which is only getting begun. Stay tuned for further in-depth analysis and cutting-edge methods. I appreciate your participation in our adventure and am eager to explore Burp Suite in greater detail with you.