
Hello and welcome back to the fourth part of our “Burpsuite 101” series, where we keep things easy and effective. Today, we’re going to explore “Burp Repeater and Burp Comparer.” 🚀 These useful web testing tools will assist you in improving your HTTP requests and analyzing results. Ready to learn the secrets of Burp Repeater and Burp Comparer and level up your online security game? Let’s get started! 🕵️♂️💻🔍
🐞Burp Repeater
Burp Suite Repeater, in essence, allows us to change and resubmit intercepted requests to a target of our choice. It enables us to alter requests intercepted by the Burp Proxy and send them again as needed.
In basic terms, you can capture a request, edit it, and instantly get the response. You can even go back to the original request, modify it, and then see the response to see if you received the results this time.
Burp Repeater opens each new HTTP or WebSocket message in a new tab. This enables you to work on multiple messages at once. You can use the controls on the tab header to create new tabs and make various changes to existing ones.
To send a request to Burp Repeater, you can right-click on it anywhere in Burp and select Send to Repeater. A new tab will be added to Repeater containing the request. You can then modify the request as needed and click Send to send it to the target server
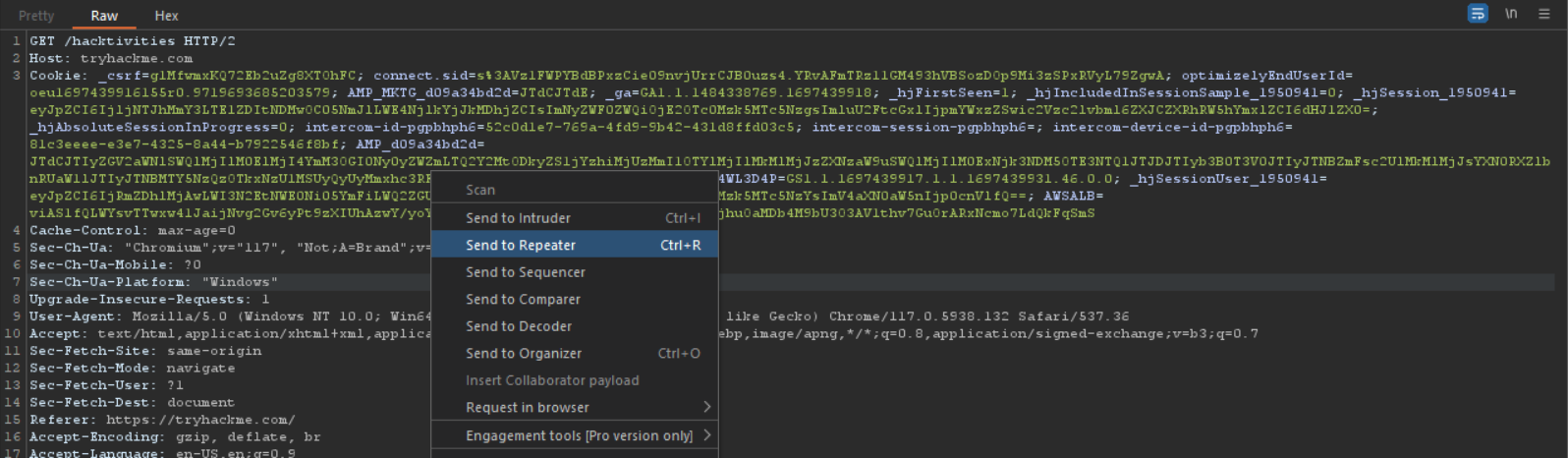
And the request pops up in the repeater :

Some features of Burp repeater:
- Send modified HTTP and WebSocket requests
- Test for input-based vulnerabilities
- Verify issues reported by Burp Scanner
- Work on multiple requests at once
- Keep a history of all requests and responses
- Add notes to each request
- Has the ability to edit and resend requests multiple times making it accessible for manual exploration and testing various endpoints.
🔥 In most cases, it is used to manually confirm if the vulnerability is there or not.
The repeater interface
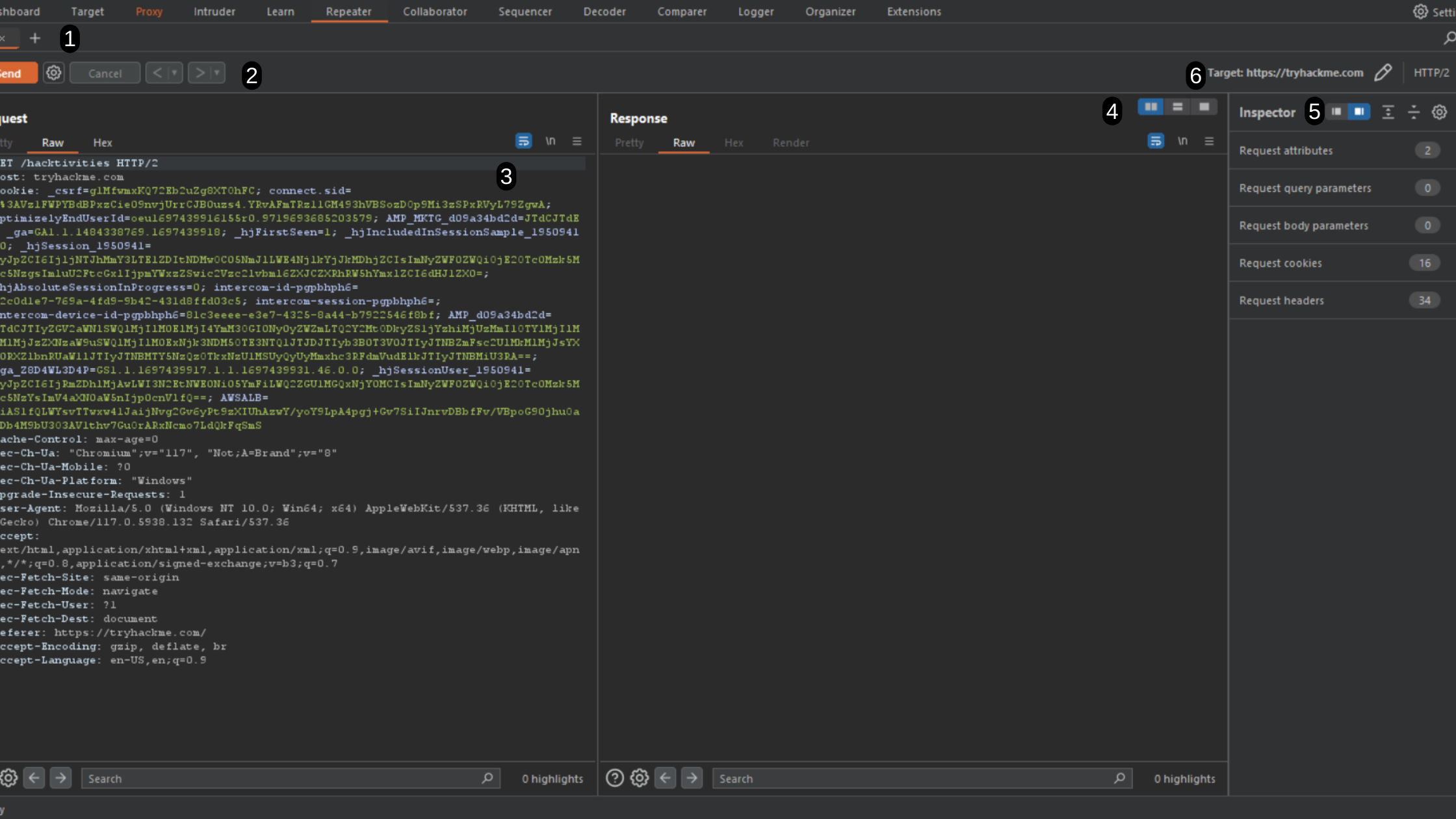
The repeater section contains six main sections
- Request List : It is the number of the requests which you have imported in the repeater tab and you can manage these all requests simultaneously.
- Request Controls: From here you can forward a request, cancel a request and also after a lot of changes you can also see its history.
- View for request & response : This is the main interface where you can both the request and response of the request, here we can edit the request.
- Layout Options: The default view of the request and response tab is side-by-side, but from the options there you can choose to do it top-bottom or also combine them in separate tabs.
- Inspector: Allows us to analyze requests in a more effective manner with more detailed view about things.
- Target: Burp Repeater allows you to specify the target server that you want to send your requests to. You may wonder how it can be helpful ,here are certain cases where this can be helpful :
i. Testing for vulnerabilities on different targets: If you’re working on a project with many targets, you may rapidly move between them by using the Target field. This can save you a significant amount of time and work.
ii. Testing for vulnerabilities in a specific environment: If you are testing for vulnerabilities in a specific environment, such as staging or production, you may utilize the Target field to guarantee that your requests are being sent to the proper environment.
iii. Testing for vulnerabilities in a specific version of an application: When testing for vulnerabilities in a certain version of an application, you may utilize the Target field to guarantee that your requests are being sent to the proper version.
Working with Burp repeater
Practical example:
This is the attempt login request for the tryhackme login webpage. here at the bottom we can see the email and password section.
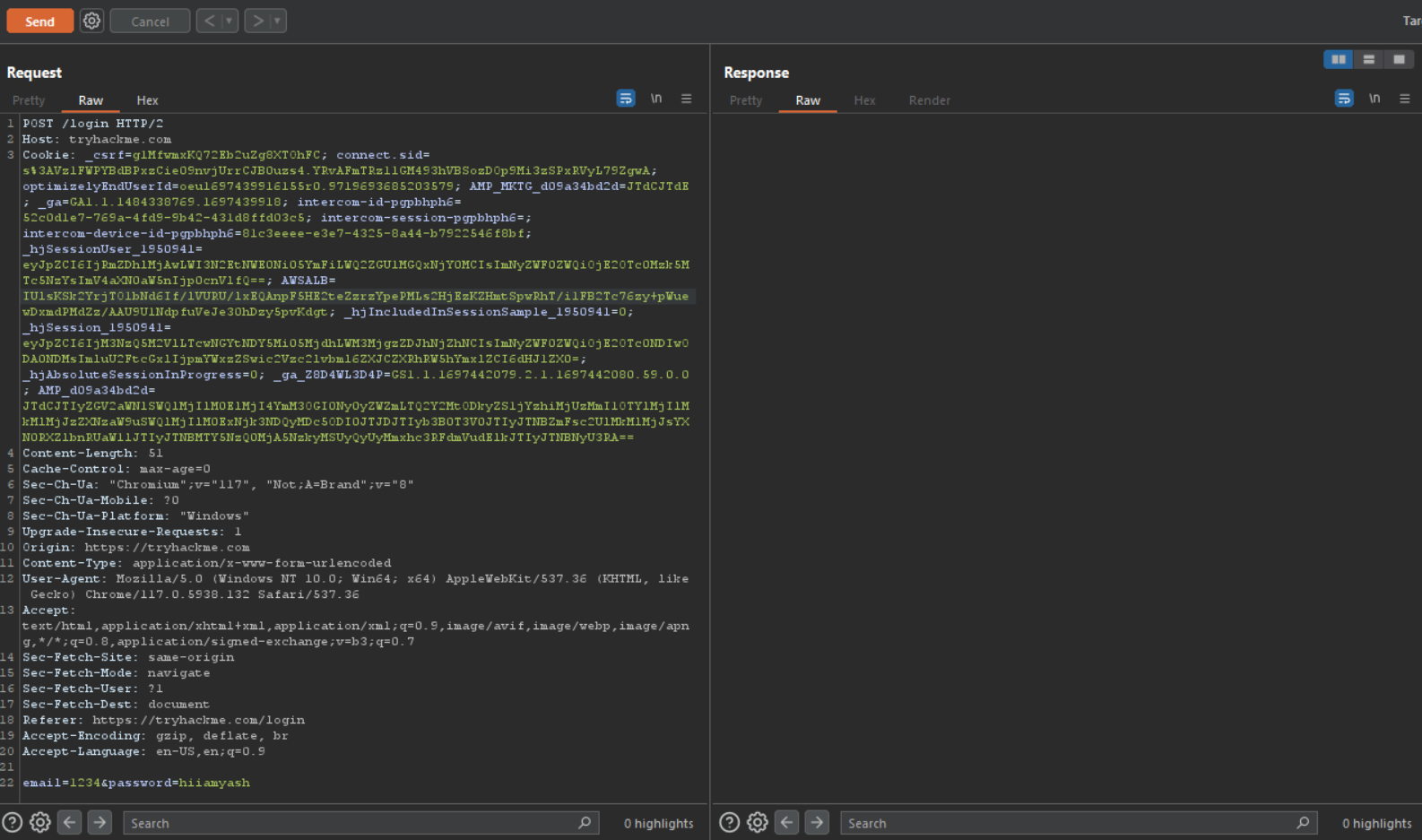
Now in these parameter we can check for sql injection attack let’s put some sql payloads in here.
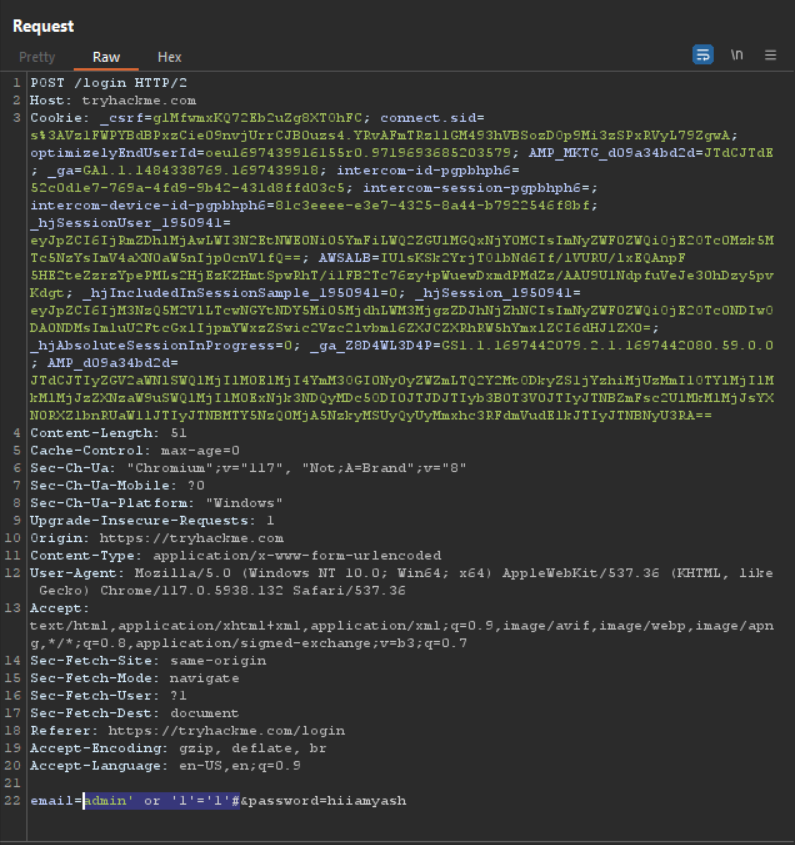
let’s send this request and response , if you some changes in the response other than the usual stuff then there are chances that vulnerability may be there.
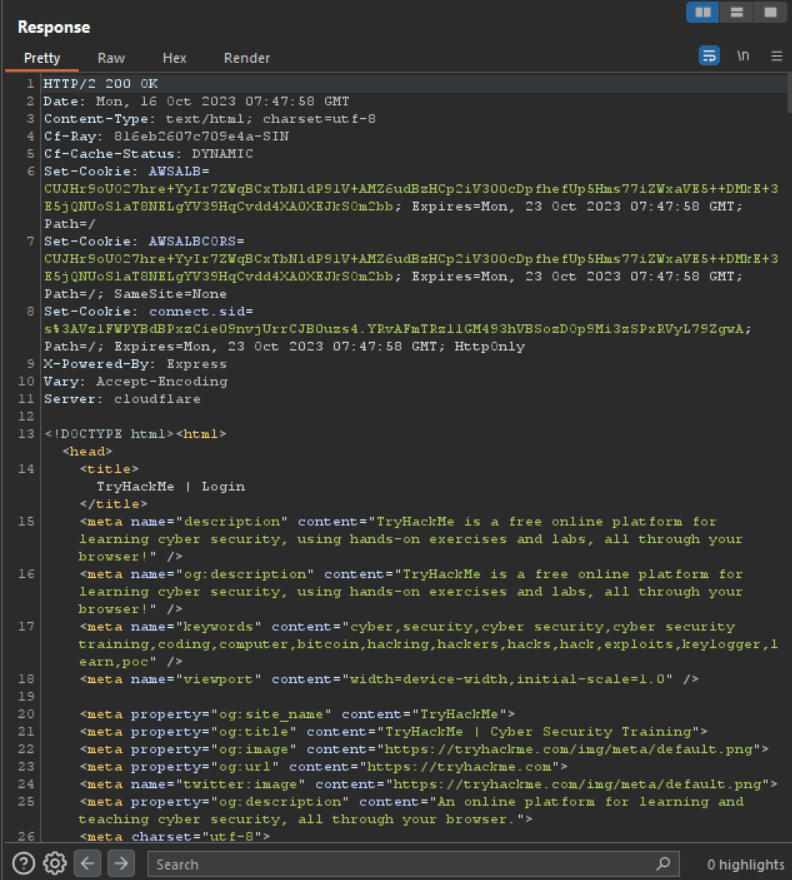
In the response , we just see the usual stuff so there is no vulnerability , just like this you can test for other vulns manually.
Message Analysis Toolbar

The message analysis toolbar in Burp Suite is a set of tools that can be used to analyze HTTP and WebSocket messages.
The default tabs in the message analysis toolbar are :
- Pretty: This tab shows the message content in a human-readable format.
- Raw: This tab shows the message content in its raw binary form.
- Hex: This tab shows the message content in hexadecimal format.
- Render: This tab attempts to render the message content as it would be displayed in a web browser.
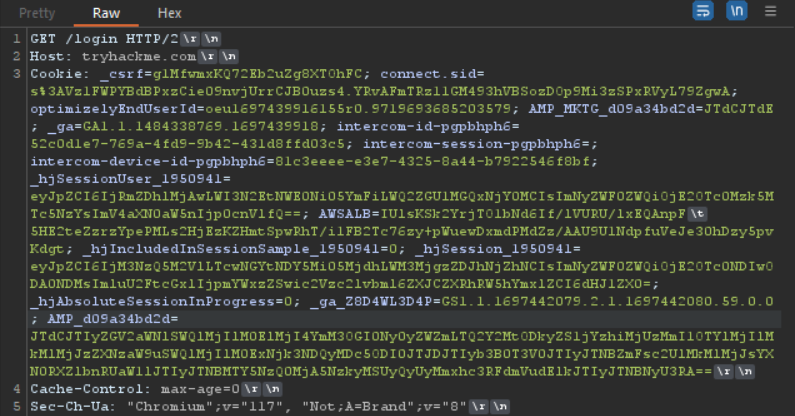
At the right of the view buttons, we can find \n which shows non-printed characters button \n. This functionality enables the display of characters that may be not easily with raw or pretty formatting.
This usually show the new line break and carriage return \r\n.
When clicked the request looks like this,
Inspector
The Inspector tool in the Burp Repeater tab is an effective tool for seeing and editing the components of HTTP and WebSocket communications. It allows you to inspect the decoded values of parameters, headers, cookies, and other message components, as well as alter the values of parameters, headers, cookies, and other components for testing SQL injection and cross-site scripting. You may also use this to reorganize message components.
Different components of the inspector are :
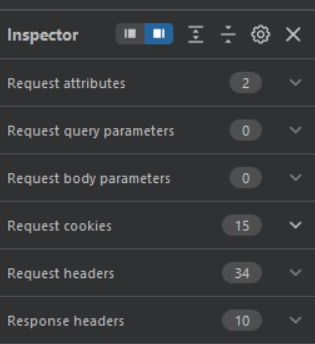
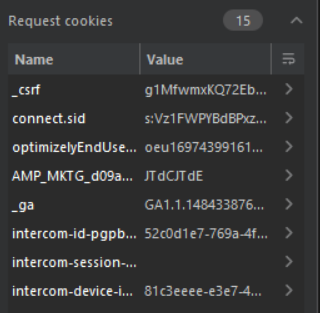
When in collapse it , you can see various requests and its parameters.
![]()
🐞 Burp comparer
Burp Comparer is a tool in Burp Suite that allows you to compare two items of data, such as HTTP requests or responses. This can be used find any subtle difference between two requests or responses.
Usage
Here are some of the different use cases of Burp Comparer:
Identifying Vulnerability:
Username Enumeration : By comparing the responses to failed logins with valid and invalid usernames, you can identify any differences that could be exploited to enumerate valid usernames
XSS: By comparing the responses to requests that contain different input values, you can identify any differences that could be exploited to inject malicious JavaScript code into the web page.
SQL injection: Just like other, you can send a payload and monitor the different responses (one with the payload and other without the payload) , if you find any distinction it can be helpful in further exploitment.
Broken Access Control : You can find any variations that could be exploited to obtain unauthorized access to sensitive resources by comparing the answers to requests made with various permissions
Session Token Analysis: By comparing authenticated and unauthenticated requests, you can identify how session tokens or cookies are generated.
Parameter Tampering Detection: By comparing requests with various input values, security testers can uncover parameter manipulation issues. This can help in identifying scenarios in which an attacker may modify settings to obtain unauthorized access or exploit program vulnerabilities.
API Testing: when testing APIs, comparer can be used to analyze and compare API requests and responses which can help in finding security issues in APIs such as improper handling of authentication tokens, missing input validation and many others.
Error analysis: If a web app uses custom error pages for different error conditions, comparer can help analyze these pages to detect potential security weakness or information leakage through error messages.
🙌 Steps
- Locate the messages that you want to analyze within Burp Suite. This could be two requests, two responses, or a request and a response.
- Right-click on each message and select Send to Comparer. You can send a message from anywhere in Burp, including the Proxy, Repeater, Sequencer, and Intruder tabs.
- Go to the Comparer tab. The messages are listed in the two item tables.
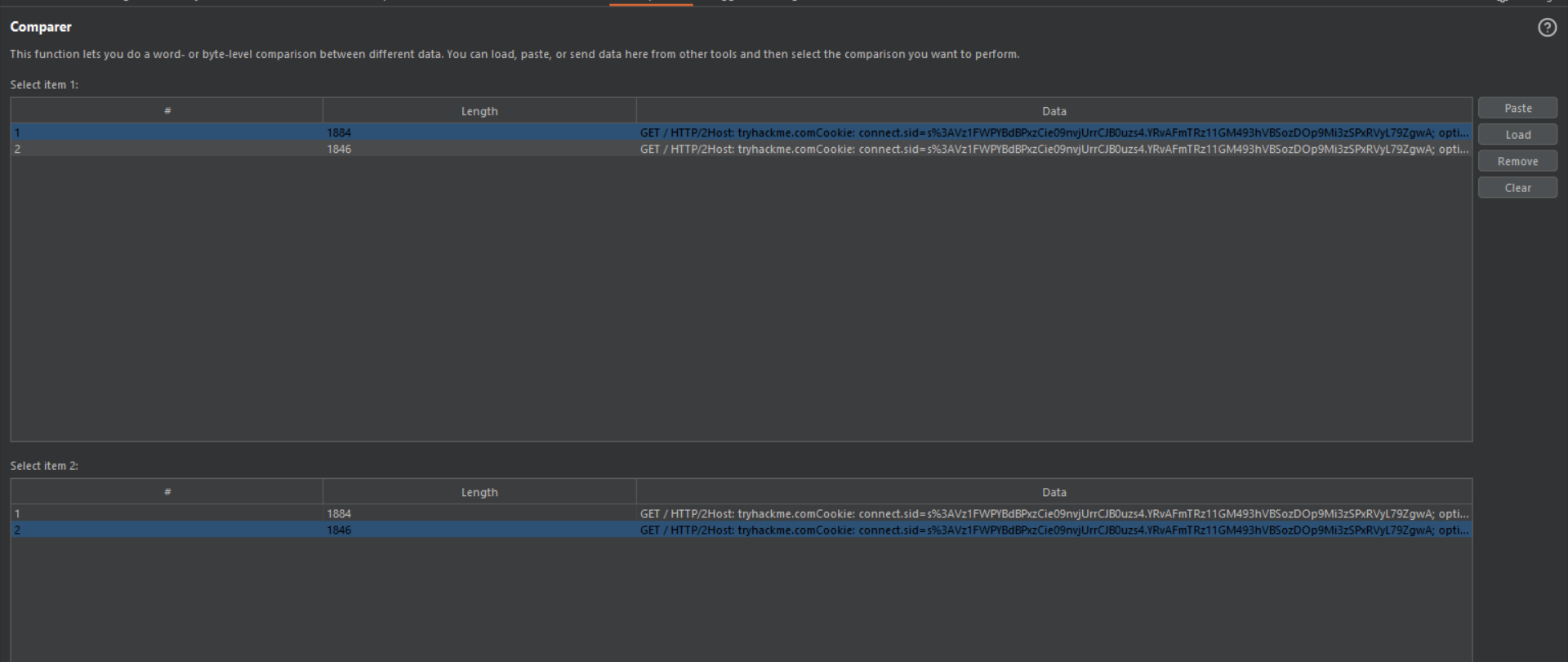
- Select the two messages you want to compare.
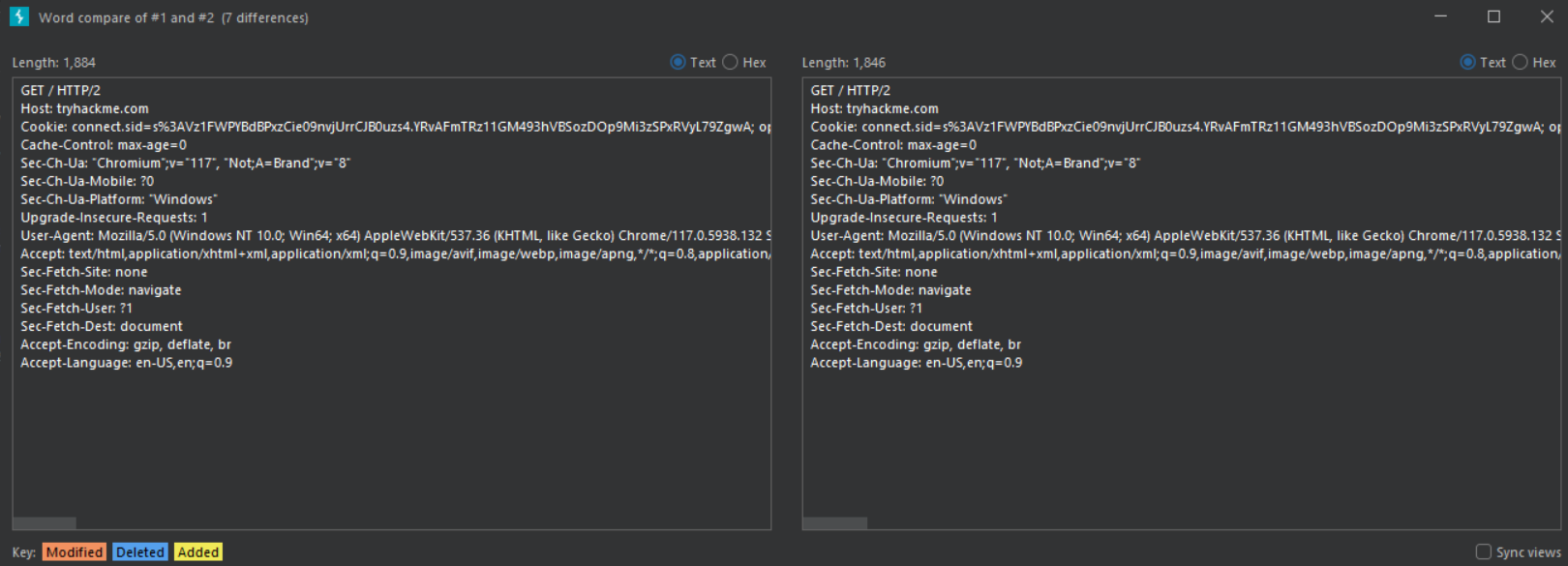
- Click the Words or Bytes button to compare the messages.
- A new window opens with the results of the comparison
🐋Conclusion
Finally, this article has focused on understanding the variety and value of Burp Repeater and Burp Comparer. We’ve looked at how these technologies may make web testing and security tasks easier to handle and more useful.
Let’s conclude by looking forward to our next adventure in the “Burpsuite 101” series. In the next blog, we’ll continue our adventure by delving into the mysteries of “Burp Intruder and Decoder.”
So, stay tuned for our future blog, and let’s keep expanding our knowledge and talents in the world of Burp Suite. Stay curious while remaining safe! 🚀🕵️♂️🔐💡