
The fifth chapter of our “Burp Suite 101” series is here. In this blog, we’ll go over Burp Intruder, one of the most powerful capabilities included with Burp Suite.
Burp Intruder is the answer to fully automating web application testing, discovering vulnerabilities, and analyzing online applications. Whether you’re new to web security or an expert in the field, this article will provide you with the knowledge and skills you need to explore all of Burp Intruder’s features.
Let us dive in and discover the secrets of this amazing tool.
🐞Burp Intruder
Burp Intruder is a tool for performing automated assaults on web applications. It may be used to test for a wide range of security flaws, including SQL injection, cross-site scripting, and brute-force attacks.
Burp Intruder operates by making a sequence of queries to a web server, each with a slightly changed payload. The payload is the data delivered to the web application, such as a login form’s username and password.
Features of Burp intruder
- Customizable assault Types : Supports a variety of assault methods such as Sniper, Battering Ram, Pitchfork, and Cluster Bomb that may be customized to your testing requirements.
- Payload Customization: Allows you to manually generate and customize attack payloads or import them from other files.
- Positional Markers: Allows you to easily indicate where payloads should be included in the request, focusing on specified parameters or headers.
- Payload Processing Rules: Apply rules to payloads such as URL encoding, base64 encoding, or custom transformations.
- Payload Sets: For complicated testing, organize and employ many payload sets in a single assault.
- Brute Force and Fuzzing: Ideal for iterative brute force, dictionary, and fuzzing attacks that iterate across payloads to uncover vulnerabilities.
- In Attack Configuration, configure concurrent requests, request delays, and response processing.
- Automatic Result Handling: Automatically highlights answer differences to discover potential flaws.
- Integration : It integrates effectively with other Burp Suite tools such as Proxy, Scanner, and Repeater.
- Session Handling: Manages sessions and cookies in order to test approved web application components.
- Save and Restore State: Pause and resume testing by saving and restoring attack state.
- Sequencer Integration: Easily analyze token randomness and predictability with Burp Sequencer integration.
How to send a request to burp intruder
- Intercept the request you want to send to burp intruder
- Right click on the intercepted request and select send to intruder.
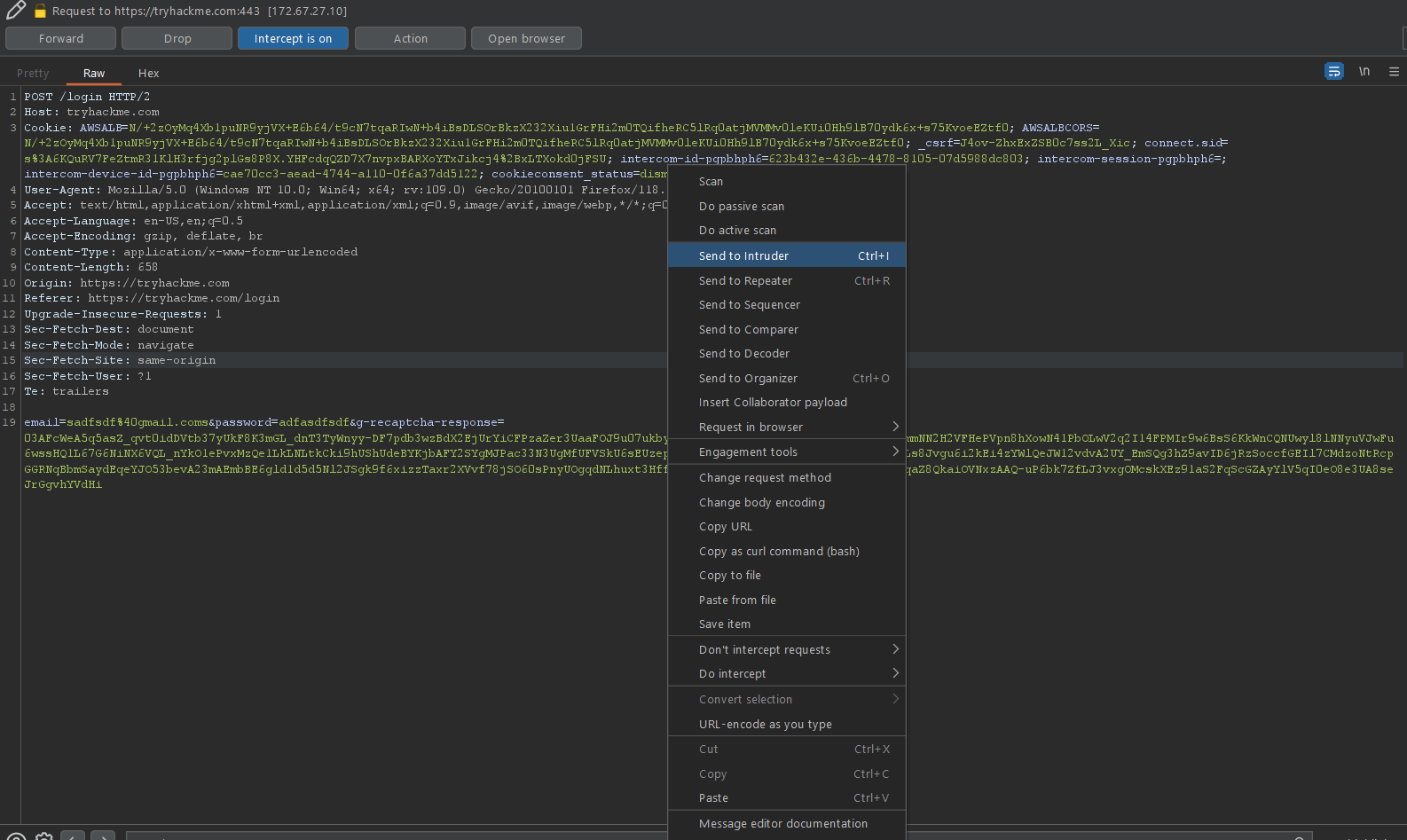
- Now in the burp intruder window, you can see the request
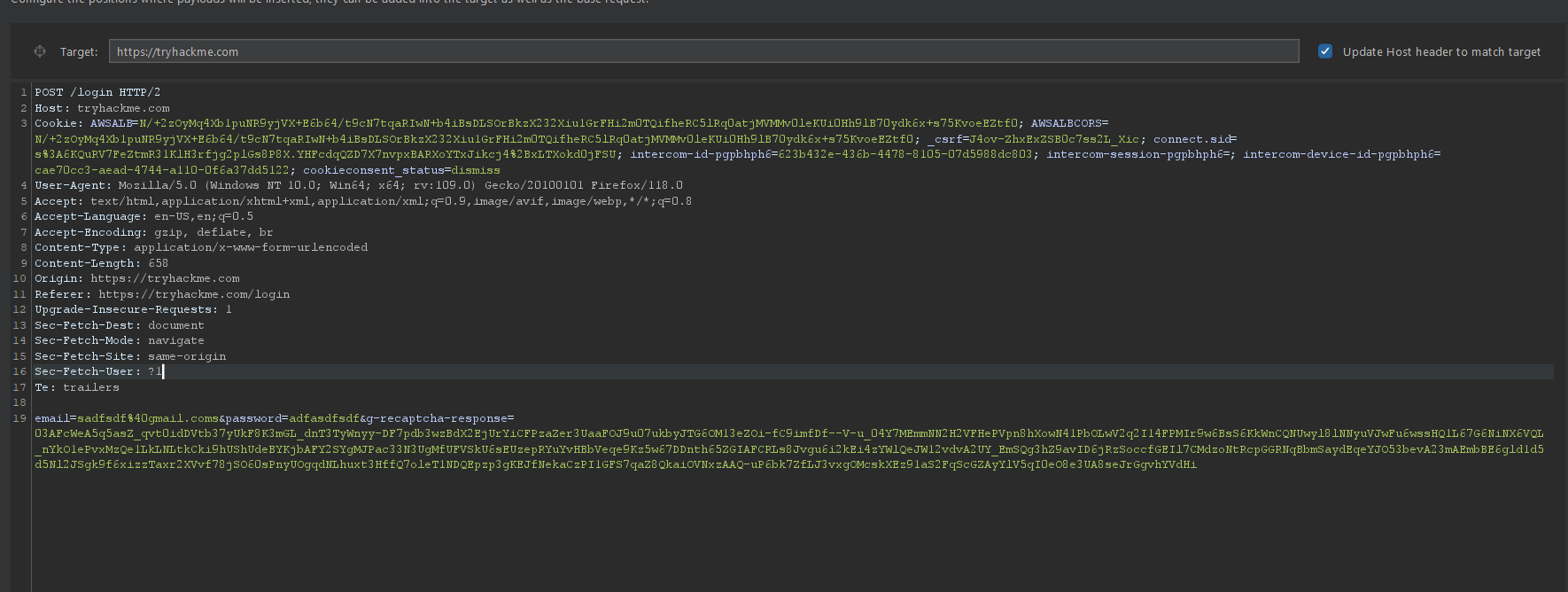
Positions payloads
As you know, Burp Intruder can assist in brute-forcing by sending multiple requests with varying payload data in a specific area of the request multiple times , well How can you also do that ?
“To determine where payloads are placed by Burp Intruder during an attack, you can specify payload positions in the request.”
“Positions” refers to the specific locations within an HTTP request where you want to insert or inject different payloads during a security assessment or penetration test
When using Burp Intruder, you can define these positions using markers
You can define various positions in the same request itself and then also choose attack type (discussed furthur below)
How to define a position
- Just the select the area which you want to replaced with you payload.
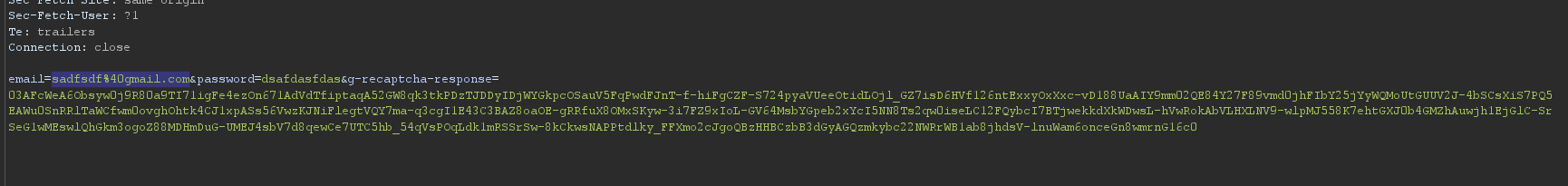
- Then click on
Add $ button on the right corner of the window.
- After getting it marked , it will be replaced by the payload.
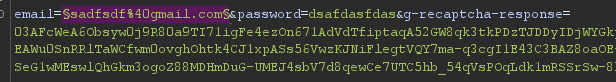
🎇 You can use auto $ to place payloads on our own.
Attack types
There are various scenarios where you want different payloads in different positions, for that there are various attack configurations in Burpsuite predefined. Let’s discuss those:
Sniper attack
In this attack Intruder injects payloads into a single defined point in the request one at a time. This kind is suitable for cases where you only want to test one primary parameter.
The total number of requests generated in the attack is the product of the number of positions and the number of payloads in the payload set
If you have multiple positions then Burp Intruder systematically injects each payload into all specified positions one after another. It cycles through each position for one payload before moving to the next payload, collecting responses for every combination of payload and position.
Use-case
- Scenario: You want to brute-force the password field of a login form to gain unauthorized access.
- Payload: A list of common passwords.
- Injection Point: The password input field.
- Process: Burp Intruder iterates through the list of common passwords, testing each one in the password field sequentially.
Battering ram:
This attack places the same payload into all of the defined payload positions simultaneously. It uses a single payload set.
The total number of requests generated in the attack is the number of payloads in the payload set.
Use-case
- Scenario: You want to test every input form for the cross-site scripting.
- Payload: A list of common XSS payloads
- Injection Point: The form input field.
- Process: Burp Intruder iterates through the list of common payloads, and places the payload in all the defined positions.
Pitchfork
This attack iterates through a different payload set for each defined position. Payloads are placed into each position simultaneously. For example, the first three requests would be:
If you want to have a different payload set for every position defined , then you can go for this attack type.
- Request one
-
Use-case
- Scenario: You want to bruteforce a login page with a set pair of usernames and passwords.
- Payload: List of common usernames, list of common passwords
- Injection Point: The form input field.
- Process: Burp Intruder iterates through the list of common payloads, and places the payload from the payload set 1 in the position 1 and payload from the payload set 2 in the position 2.
Cluster Bomb
This attack iterates through a different payload set for each defined position. Payloads are placed from each set in turn
The total number of requests generated in the attack is the product of the number of payloads in all defined payload sets - this may be extremely large.
🔥 This is very helpful where an attacker requires unrelated and unknown input.
Request one
- Position 1 -> first payload from set 1
- Position 2 -> First payload from set 2
Request two
- Position 1 -> First payload from set 1
- Position 2 -> Second payload from set 2
Request three
- Position 1 -> First payload from set 1
- Position 2 -> Third payload from set 2
.
.
.
.
.
Request [number]
Position 1 : Second payload from set 1
Position 2 : First payload from set 1
Use-case
Scenario: You want to test for sql injection, xss in the login page
Payload: List of common xss payloads, list of common sql payloads
Injection Point: The form input field.
Process: goes through a list of common payloads prepared for a brute force assault carefully. It adds a payload from the first payload set into position 1 for each iteration. At the same time, it chooses a payload from the second payload set and places it in position 2.
Payloads
“Payloads” refer to the data that you want to inject or manipulate in the target application during various types of attacks, such as brute force attacks, fuzzing, or other vulnerability tests.
Burp Suite has a dedicated payloads configuration tab under the intruder module, where you can change payloads configurations,
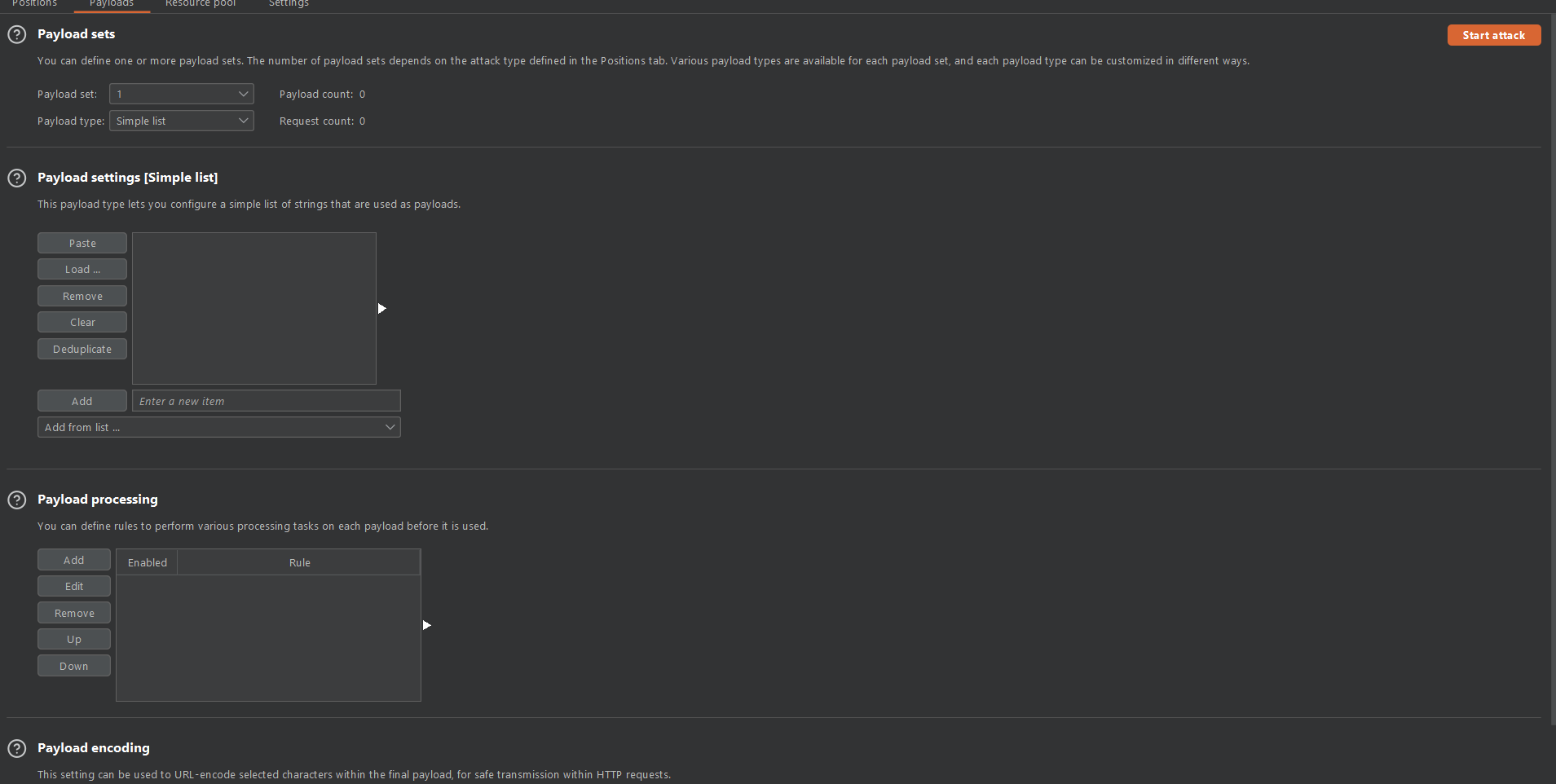
Payload sets
🔥 “payload set” is a collection of data that you want to use as inputs during the various types of attacks, such as brute-force attacks.
There are various predefined payload set type, which you can also use, those predefined payloads sets include:
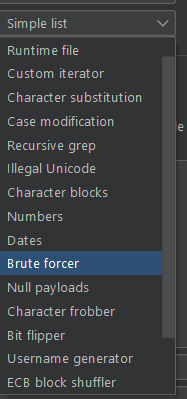
Some of these payloads, has some configurations on his own.
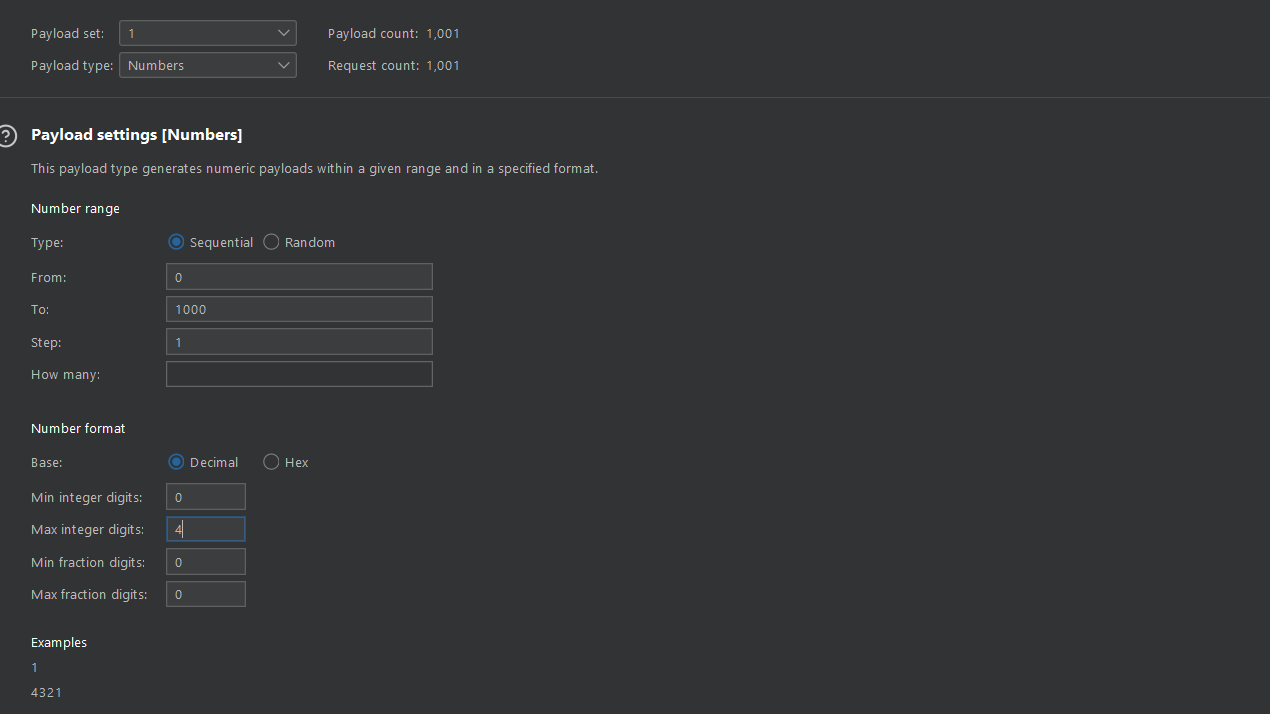
🔥 To learn about more payload-set and their configurations , you can visit : Burp documentation
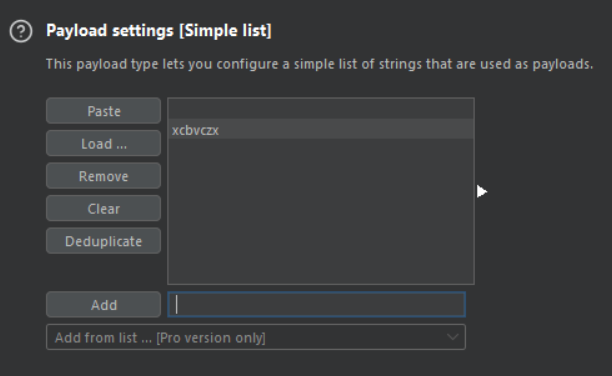
Payload settings
In the Payload settings section, you can modify each payload type. Many kinds include the following default configuration options.
- Paste: Insert a list from your clipboard
- Load: Load from a list of file {Premium}
- Remove : Remove the highlighted item
- Clear : Clear the list
- DeDuplicate: Remove duplicate entries from your list.
- ADD: Enter a new item
Payload Processing Rules:
Another characteristic of burp intruder is payload preprocessing, which refers to the ability to manipulate and prepare payloads prior to usage in an attack.
It is commonly used to tailor payloads to the needs of the target application.
How to add Preprocessing rules
- Scroll down to the Payload Processing field under Intruder > Payloads.
- Select Add. A window with a drop-down list of processing rules appears.
- Choose a rule type from the drop-down menu. Fill up any other needs to configure the rule.
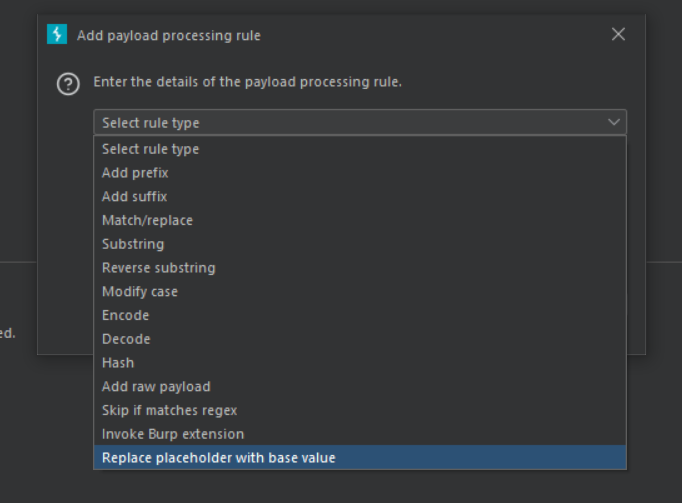
Let’s discuss some of these pre-processing rules
- Add prefix : Before the payload, include a literal prefix.
- Add suffix : After the payload, include a literal prefix.
- Match / replace - Replace all elements of the payload that match a given regular expression with a literal string.
- Substring - Extract a subset of the payloads beginning at a particular offset (0-indexed) and ending at a specified length.
- Reverse substring - This functions as for the substring rule, but the end offset is specified counting backwards from the end of the payload, and the length is counted backwards from the end offset.
- Modify case - Modify the case of the payload.
- Encode - Encode the payload using one of the following schemes: URL, HTML, Base64, ASCII hex, or built strings for different systems.
- Decode - Decode the payload using one of the following schemes: URL, HTML, Base64, or ASCII hex.
- Hash - Carry out a hashing operation on the payload.
- Invoke Burp extension - To process the payloads, run a Burp extension. An Intruder payload processor must have been registered by the extension. The required processor can be chosen from a list of available processors registered by presently loaded extensions.
- Replace placeholder with base value - Replace all sections of the payload that match ‘base’ with the payload position’s base value.
- Replace placeholder with collaborator payload - A Collaborator payload is used to replace any elements of the payload that match a certain regular expression. You have the option of including the Collaborator server location in the Collaborator payload.
Resource pool
In Burp Intruder, a resource pool is a group of tasks that share a quota of resources. This comprises both the amount of concurrent requests and the rate at which requests can be made.
The resource pool tab is located under the sab tab of the burp intruder.
User Interface:
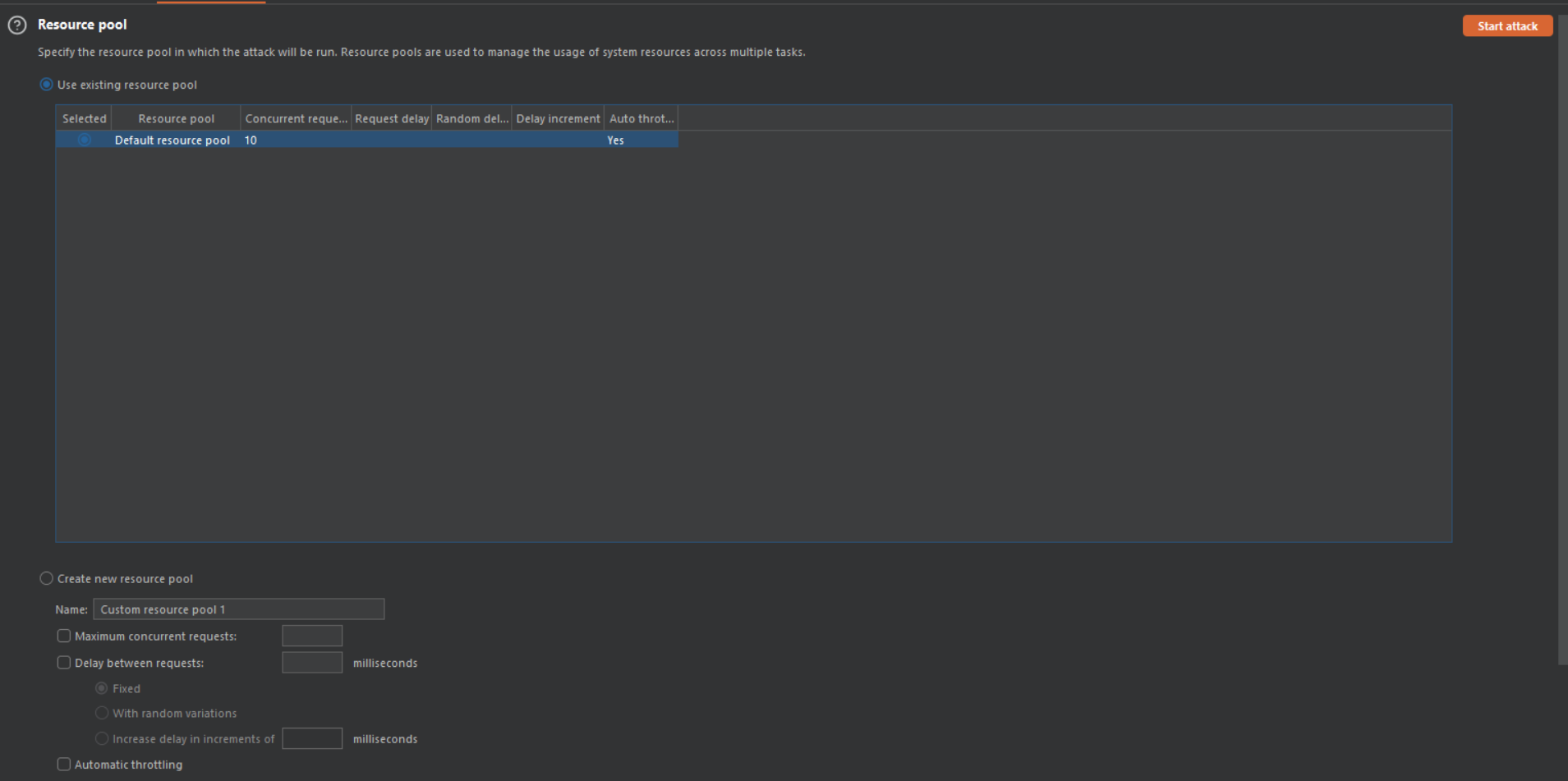
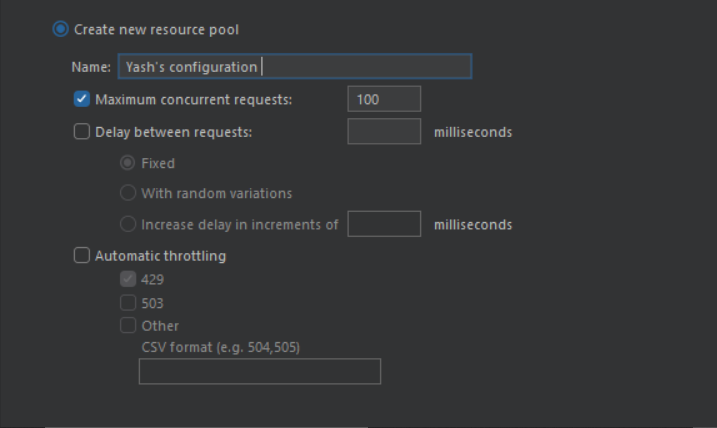
Steps to create a resource pool
- Go to Intruder > Resource pool.
- Click the Create new resource pool button.
- Enter a name for the pool and configure the pool settings. The following settings are available:
- Maximum concurrent requests: Specify a limit to the number of requests that are sent simultaneously.
- Delay between requests: Set a delay time in milliseconds.
- Fixed
- With random variations
- Increase delay in increments
- Use proxy: Select this option to use a proxy server for all requests in the pool.
- Click the OK button to create the pool.
Attack Settings
Before launching an attack, you can configure Burp Intruder attack settings under the assault tab under Settings.
The user interface for attack settings:
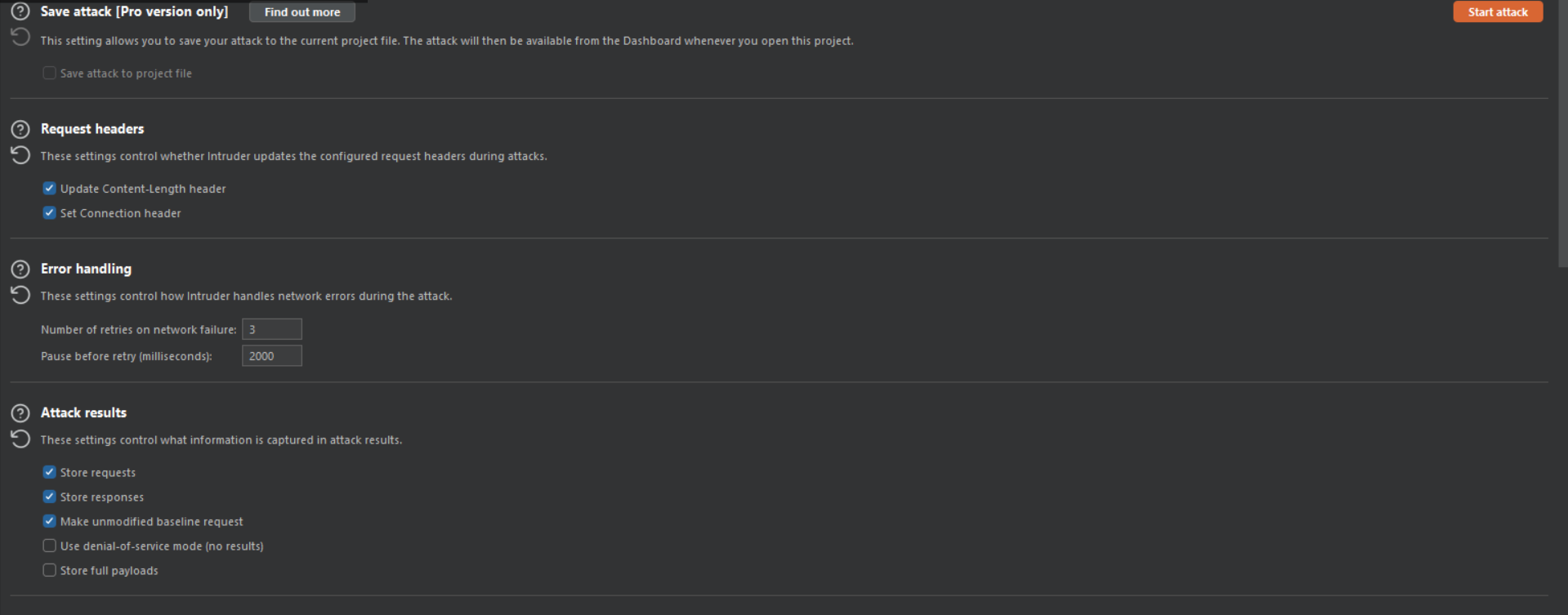
Save Attack {Premium feature}
You can save all your attack results into a file, even if you close burp suite those attack the attack results remains, if you find something interesting, then you can save it in a file.
Request headers
During assaults, these options determine whether Intruder changes the preset request headers:
- Update Content-Length header: In each request, add or update the Content-Length header with the right length of the HTTP body.
- Set Connection header: Add or update the
Connection header with the value close.
Error handling
These settings control how Intruder handles network errors during an attack:
- Number of retries on network failure: Specify the number of times Burp retries a request when a failure occurs
- Pause before retry: Specify the time (in milliseconds) that Burp waits before retrying a failed request
Attack results
These options govern what data is gathered in the attack results:
- Store requests / response : specify whether the attack saves the contents of individual requests and responses.
- Make unmodified baseline request : In addition to the predefined attack requests, configure the attack to issue the template request with all payload positions set to their default values.
- Use denial-of-service mode : Set the attack to not process any responses received from the server. It is useful for application-layer denial-of-service attacks against susceptible apps because it sends requests that launch high-workload operations on the server frequently while avoiding locking up local resources by keeping sockets open for the server to react.
- Store full payloads: For each result, save the whole payload values.
Grep-match
These settings flag result items that contain specified expressions in the response.
Burp adds a results column for each expression in the list during the attack. This counts how many times the expression appears in the response. To identify results with the expression, sort the results by clicking on the column header.
Grep - extract
These settings extract information from responses. It is often necessary to follow redirections to achieve the objectives of your attack
Redirections
These options govern how Burp handles redirections during assaults.
You can configure redirections to follow for the following cases as well :
- Never
- On-site only
- In-scope only
- Always
HTTP version
Use this setting to control whether Burp Intruder uses HTTP/2 or HTTP/1 for the current attack.
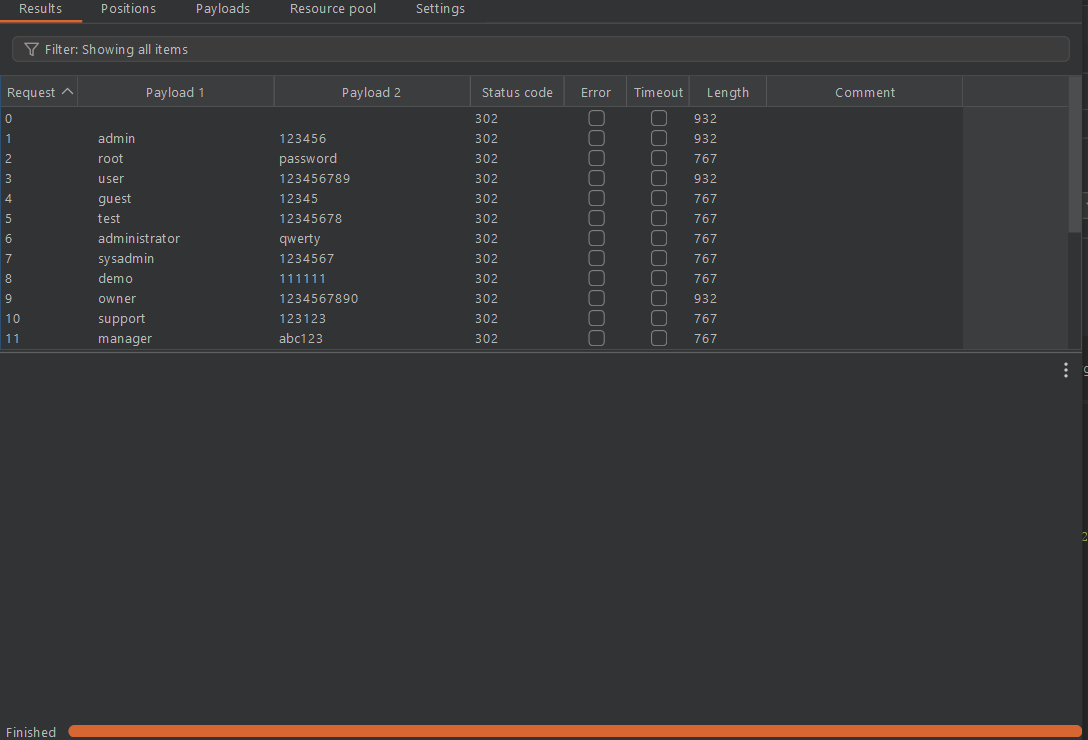
Attack results
Whenever you push to launch an attack, it starts in his own new window.
You can get the following information through the request :
- Http Status Code
- Length of response body
- Response Headers:
- Cookies
- Redirects
- Custom Error Messages:
- Timing Analysis
- Content-Length
- Regex Matching:
Controlling an attack
You can pause, stop and restart an ongoing attack.
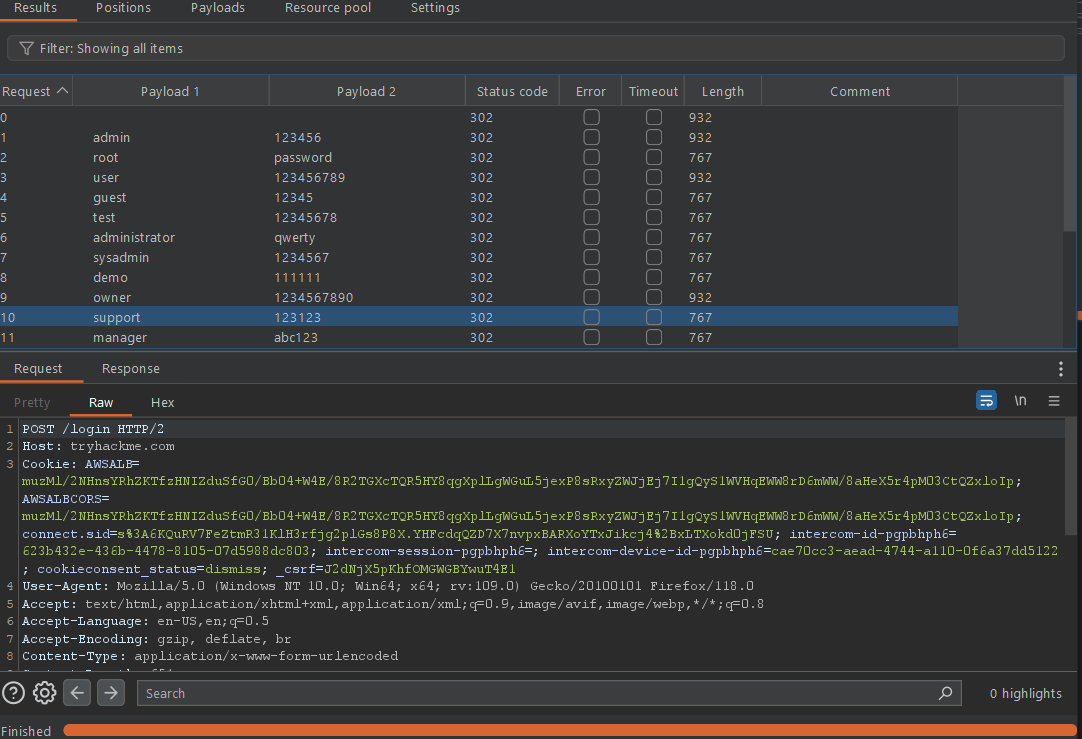
Viewing a request
If you find something phishy in the response you can view the full response by clicking on the response.
🐋Conclusion
We’ve explored the darkest corners of Burp Intruder in this blog. We’ve covered everything from the fundamentals to advanced techniques.
We hope that this tutorial will help you use security testing efficiently. It’s now up to you to explore, study, and secure the digital universe. Good luck with your testing!