First, Let’s understand what is this software & its use cases

Confluence Server and Confluence Data Center are both software apps developed by Atlassian for collaboration, documentation, and team productivity. Here’s a brief explanation:
- Confluence Server: Confluence Server is software that you install on your own physical or virtual servers. It’s deployed in your own on-premises infrastructure, and you are responsible for managing the server, its hardware, and the software installation. Users within your organization access Confluence Server through web browsers or client applications. Confluence Server is suitable for smaller organizations or teams that prefer to maintain full control over their Confluence instance.
- Confluence Data Center: Confluence Data Center is also a software application, but it’s designed for larger enterprises and organizations with higher scalability and performance needs. It offers features like load balancing and clustering to ensure high availability and better performance. It is not a physical server but can be installed on multiple servers to distribute the workload and enhance performance. Confluence Data Center is typically hosted in an organization’s data centre or cloud infrastructure.
About this CVE (Deep-Dive into Code & Exploiting)
Vulnerability type: Broken access control vulnerability leading to High Privilege Access
Severity Score: CVSS score of 10.0
Affected version [‘8.0.0’, ‘8.0.1’, ‘8.0.2’, ‘8.0.3’, ‘8.0.4’, ‘8.1.0’, ‘8.1.1’, ‘8.1.3’, ‘8.1.4’, ‘8.2.0’, ‘8.2.1’, ‘8.2.2’, ‘8.2.3’, ‘8.3.0’, ‘8.3.1’, ‘8.3.2’, ‘8.4.0’, ‘8.4.1’, ‘8.4.2’, ‘8.5.0’, ‘8.5.1’]
When deploying Confluence for the first time, users undergo an initial setup process, allowing them to configure essential parameters and create an administrative account. This process is typically accessible via ‘http://<IP/Domain>/setup/'.
Once you complete the above steps, If you try to access the initial setup you won’t be able to go through the setup again but will be greeted with a message stating that the setup process is already complete or redirect to another page such as login.

Now comes this vulnerability in the picture which allows an attacker to re-enable the initial setup process. In doing so, the attacker can go through the step of creating a new administrator all over again.
The vulnerability in question arises from the underlying architecture of Confluence, which relies on the Apache Struts framework in conjunction with the XWork package.
The Struts framework facilitates the definition of Actions through Java classes. These Actions can be invoked through specific URLs, wherein the corresponding Java class processes the request, executes the necessary functions, and generates a response. In this context, invoking an Action URL triggers the ‘execute()’ method within the associated class.
Calling Getters/Setters via XWork
Beyond invoking Actions, Confluence’s structure allows for the interaction with getters and setters in Action classes by specifying HTTP parameters in the URL. For instance, if the ‘login’ Action class contains a ‘setId()’ method, this method can be invoked through a URL like ‘http://<IP/Domain>/login.action?Id=123′, effectively triggering ‘setId(‘123’)’ as defined in the Action class.
Chaining Getters/Setters to Re-enable the Initial Setup
Exploiting this vulnerability hinges on targeting the ServerInfoActionThe choice of this specific Action is strategic, as it enables the construction of a chain of getters and setters to manipulate the configuration parameter governing the initial setup.
The ServerInfoActionclass extends the ConfluenceActionSupportclass, thereby inheriting its methods. One particularly significant method is the BootstrapStatusProviderwhich returns a ‘BootstrapStatusProvider’ object. This object is critical because it offers another getter method to access an ApplicationConfigurationobject from it to set the configuration parameter that turns the initial setup on or off.
If you analyse the code of the ServerInfoAction class, you’ll see it extends the ConfluenceActionSupport class. By doing so, it will inherit all of its methods as well. One such method is a getter that returns an BootstrapStatusProvider object.
public class ConfluenceActionSupport extends ActionSupport implements LocaleProvider, WebInterface, MessageHolderAware {
public BootstrapStatusProvider getBootstrapStatusProvider() {
if (this.bootstrapStatusProvider == null)
this.bootstrapStatusProvider = BootstrapStatusProviderImpl.getInstance();
return this.bootstrapStatusProvider;
}
}
We care about the BootstrapStatusProvider class because it has another getter method we can use to retrieve an ApplicationConfiguration object:
public class BootstrapStatusProviderImpl implements BootstrapStatusProvider, BootstrapManagerInternal {
public ApplicationConfiguration getApplicationConfig() {
return this.delegate.getApplicationConfig();
}
}
As you have probably guessed by now, this object contains the application’s configuration, including an attribute that tells Confluence if the initial setup has been finished. Such attributes can be modified by using a setter in the
ApplicationConfig class
public class ApplicationConfig implements ApplicationConfiguration {
public synchronized void setSetupComplete(boolean setupComplete) {
this.setupComplete = setupComplete;
}
}
If we call setSetupComplete(false), we will effectively re-enable the initial setup. Putting it all together, we can call that chain of getters/setters by accessing the following URL: http://<IP/Domain>/server-info.action?bootstrapStatusProvider.applicationConfig.setupComplete=false
This will be effectively translated by XWork into a call to getBootstrapStatusProvider().getApplicationConfig().setSetupComplete(false)
Now, go to your browser and navigate to the crafted URL to trigger the vulnerability. You should get the following response from the server:
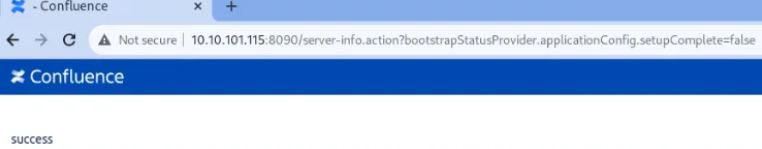
Now that we can access the initial setup once again by navigating to this URL http://<IP/Domain>/setup/setupadministrator-start.action & create an admin account. If all goes well, you should get access to the Confluence App with administrative privileges
To Confirm if this user has administrator privileges simply go to this URL http://<IP/Domain>/admin/users/viewuser.action?username=<Your-created-username> & you can see this user is part of the confluence-administrators group.

Detection & Mitigation
If you are currently running a version of Confluence that is susceptible to this vulnerability, it is crucial to take the following steps:
- Monitoring:
Examine network access logs for any requests to URLs ending with ‘/setup/*.action’. These URLs should not be accessed by regular users after the initial installation.
Review network access logs for requests to ‘/server-info.action?bootstrapStatusProvider.applicationConfig.setupComplete=false’.
Scrutinize your Confluence user base for any suspicious accounts and members of the ‘confluence-administrators’ group.
- Upgrade:
All instances of Confluence running vulnerable versions should be upgraded to at least one of the following versions:
8.3.3
8.4.3
8.5.2
- Temporary Mitigation:
If immediate upgrading is not feasible, it is advisable to block access to the ‘/setup/*’ endpoints as a temporary security measure. This can be achieved by adding the following security constraint within the <web-app> section in the ‘/<confluence-install-dir>/confluence/WEB-INF/web.xml’:
<security-constraint>
<web-resource-collection>
<url-pattern>/setup/*</url-pattern>
<http-method-omission>*</http-method-omission>
</web-resource-collection>
<auth-constraint />
</security-constraint>
Please note that these mitigation instructions serve as an interim security measure and should not be considered a definitive patch. Upgrading to secure versions of Confluence remains the most effective long-term solution to address this vulnerability.
Exploit Code & Vulnerability Scanners
You can use Shodan or Censys to find vulnerable instances of this software.
PoC (Python code it just confirms if a vulnerability exists or not this program doesn’t exploit it)
PoC (python — Exploit code)
External Articles & References
https://tryhackme.com/room/confluence202322515
https://attackerkb.com/topics/Q5f0ItSzw5/cve-2023-22515/rapid7-analysis?referrer=moreFromAKB