What is YARA???

YARA is a type of language where we write rules to detect strings, files, file formats etc. Which will ultimately help us in detecting malwares present in certain files/folder or system.
How to write yara rules
- The rule file we create.
- Name of file, Directory, or process ID to use rule for.
- Every rule must have a name and condition.
- The file extension is .yar
ex-
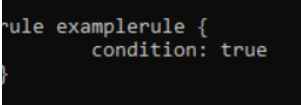
How to use it:–
** yara myrule.yar testfile**
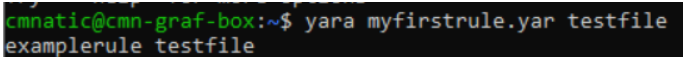
if the rule is not satisfied it will probably give an error.
more example of rule:
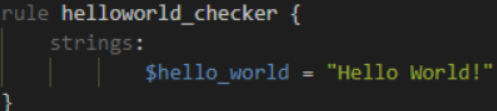
We define the keyword Strings where the string that we want to search, i.e., “Hello World!” is stored within the variable $hello_world
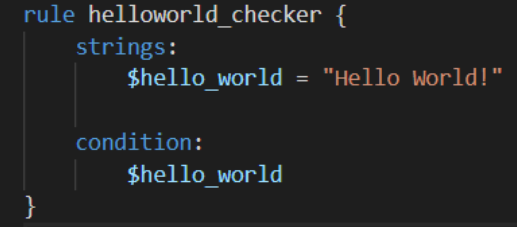
Essentially, if any file has the string “Hello World!” then the rule will match. However, this is literally saying that it will only match if “Hello World!” is found and will not match if “hello world” or “HELLO WORLD.”
YARA Tools
Some YARA Tools:
- LOKI
- THOR
- FENRIR
- YAYA
How to use Loki
python ../Loki/loki.py -p
use this command in the suspected directory and if that directory is compromised by malware it will give a positive result.
But the fact is loki is sometimes not sufficient so we need to Generate our own rule using some similar malwares which is suspected in the system and import those rules to Loki.
How to generate OWN rule
YarGen is the tool
To use yarGen to generate a Yara rule
python3 yarGen.py -m /home/cmnatic/suspicious-files/file2 --excludegood -o /home/cmnatic/suspicious-files/file2.yar
A brief explanation of the parameters above:
-m is the path to the files you want to generate rules for
–excludegood force to exclude all goodware strings (these are strings found in legitimate software and can increase false positives)
-o location & name you want to output the Yara rule
python3 yarGen.py -m /home/cmnatic/suspicious-files/file2 --excludegood -o /home/cmnatic/suspicious-files/file2.yar
This will generate a yara rule which will make a alert if there is a similar malware like /home/cmnatic/suspicious-files/file2 what it does is it generate the rules for strings and other info in that folder/file and exclude the normal strings and all that which is expected to present in all normal codes.
You can also analyze the file by searching its hash value in Valhalla and VirusTotal