You can access the room here :
Introduction to Cryptography | TryHackMe
Task 1: Introduction
Question -1 :
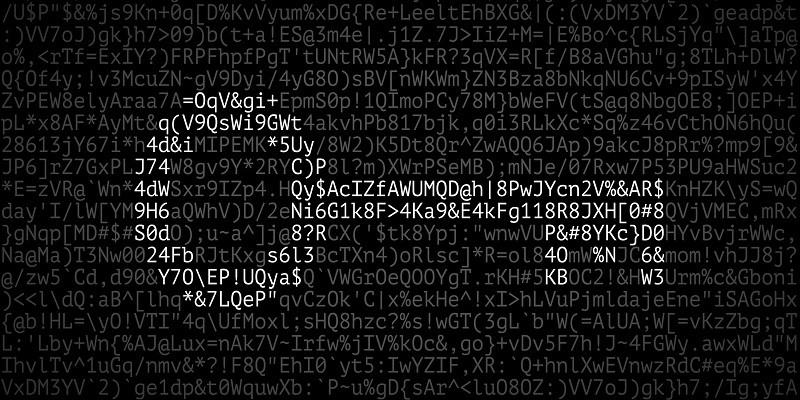
You have received the following encrypted message:
“Xjnvw lc sluxjmw jsqm wjpmcqbg jg wqcxqmnvw; xjzjmmjd lc wjpm sluxjmw jsqm bqccqm zqy.” Zlwvzjxj Zpcvcol
You can guess that it is a quote. Who said it?
Solution :
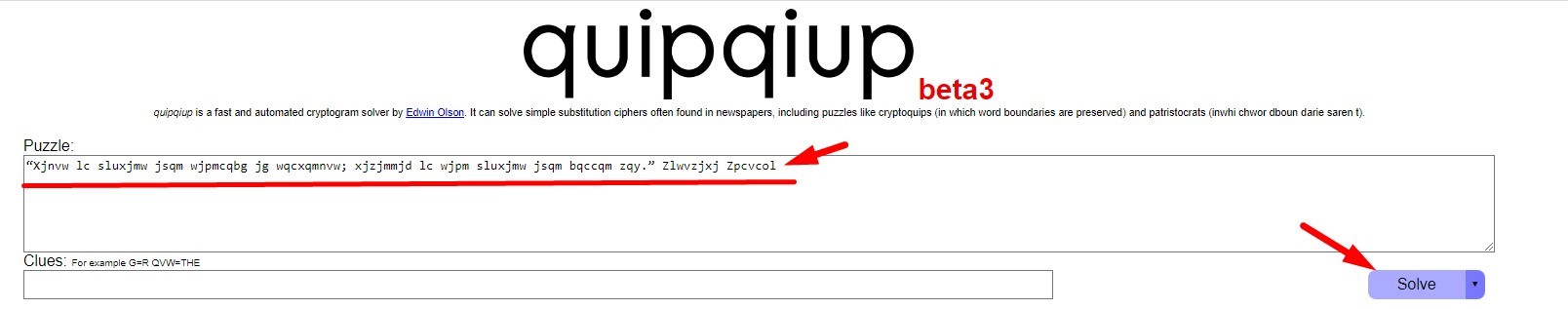
Answer : Miyamoto Musashi
Task 2: Symmetric Encryption
“The necessary files for this task are located under /root/Rooms/cryptographyintro/task02. The zip file attached to this task can be used to tackle the questions of tasks 2, 3, 4, 5, and 6.”
I downloaded the necessary files into my machine. You can also prefer to use the Attackbox VM directly, no matter.
Answer the questions part :
Question -1 :
Decrypt the file quote01 encrypted (using AES256) with the key s!kR3T55 using gpg. What is the third word in the file?
Solution :
It would be better to check the version of gpg first to avoid any errors.
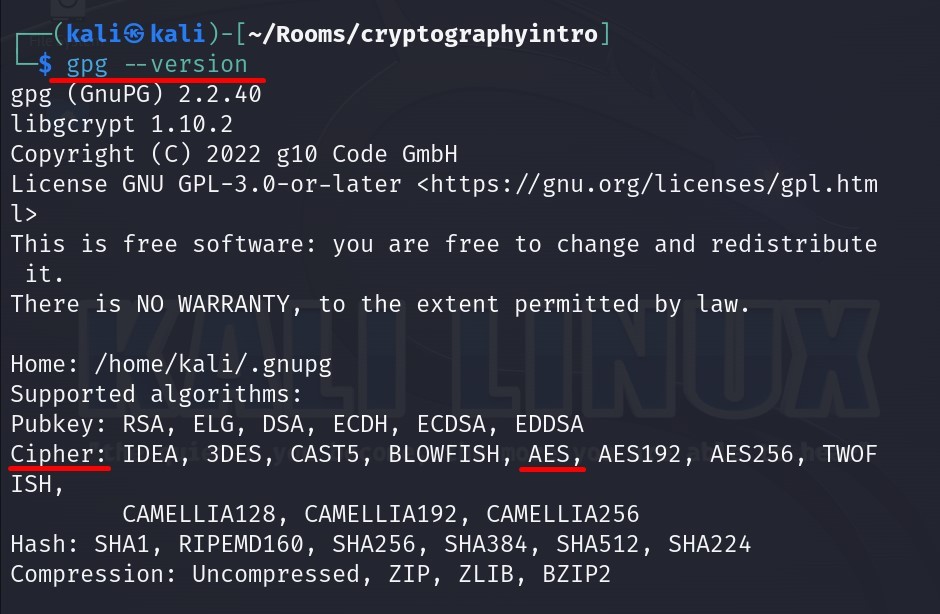
As you can see above, it supports AES and its variants as Cipher algorithms.
In that case, we can begin to use gpg to decrypt the respective file.
Firstly navigate to the directory which contains encrypted file “quote01” :

Now, we can use the following command in order to decrypt the file “quote01” :
gpg --output quote01_decrypted.txt --decrypt quote01.txt.gpg
When you type the command and enter it, you will encounter a window which asks you the secret key as passphrase in order to decrypt the file as seen below :
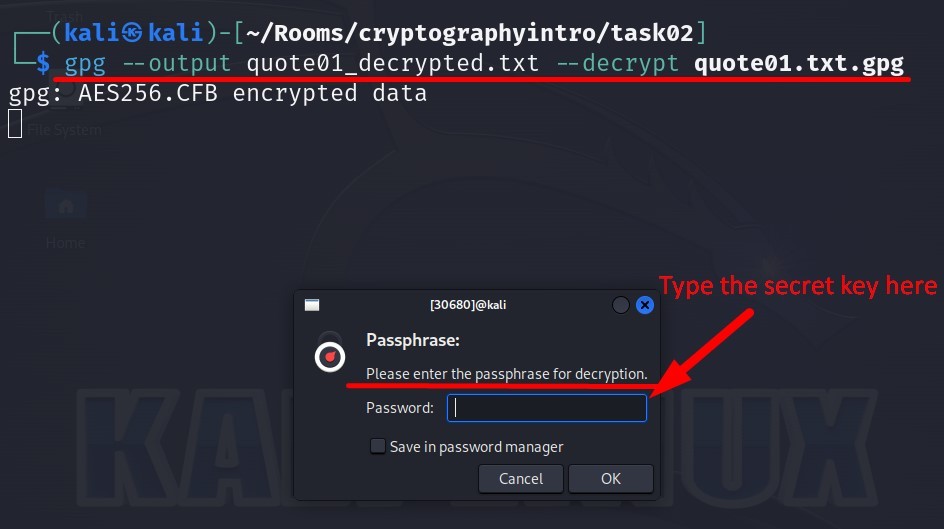
Type the key “s!kR3T55” given in the question into Password field and click on the OK button.
After decrypting process, now we have our decrypted file named “quote01_decrypted.txt” as the output :
Let us read the file right now :
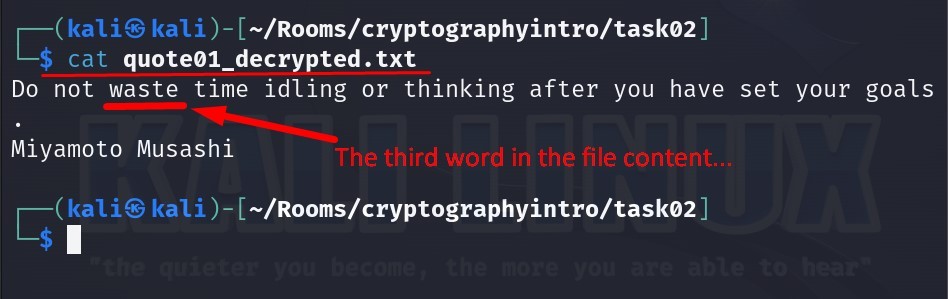
Answer : waste
Question -2 :
Decrypt the file quote02 encrypted (using AES256-CBC) with the key s!kR3T55 using openssl. What is the third word in the file?
Solution :
The encrypted file is quote02 :
This time we will use the openssl in that way :
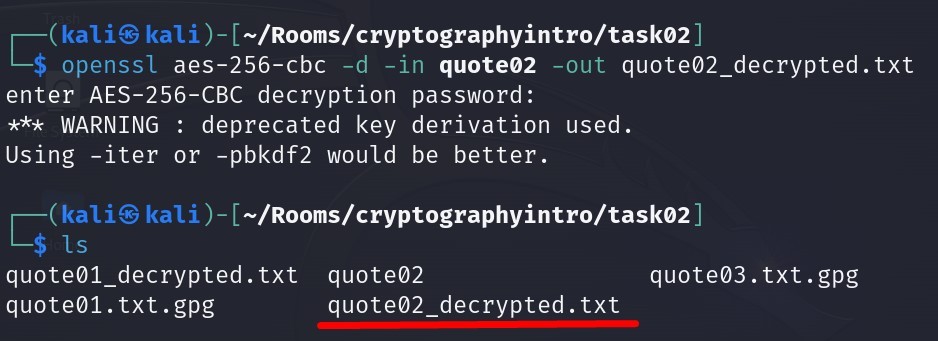
openssl aes-256-cbc -d -in quote02 -out quote02_decrypted.txt

After we entered the key value, the decryption is completed.
And we obtained the decrypted version of quote02 as “quote02_decrypted.txt” :
Let us read the file right now :
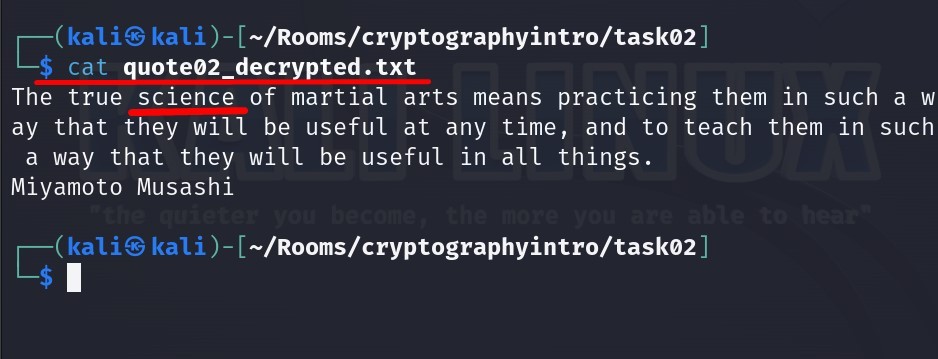
The third word in the file is “science”.
Answer : science
Question -3 :
Decrypt the file quote03 encrypted (using CAMELLIA256) with the key s!kR3T55 using gpg. What is the third word in the file?
Solution :
First of all, let’s check the supported cipher algorithms by gpg :
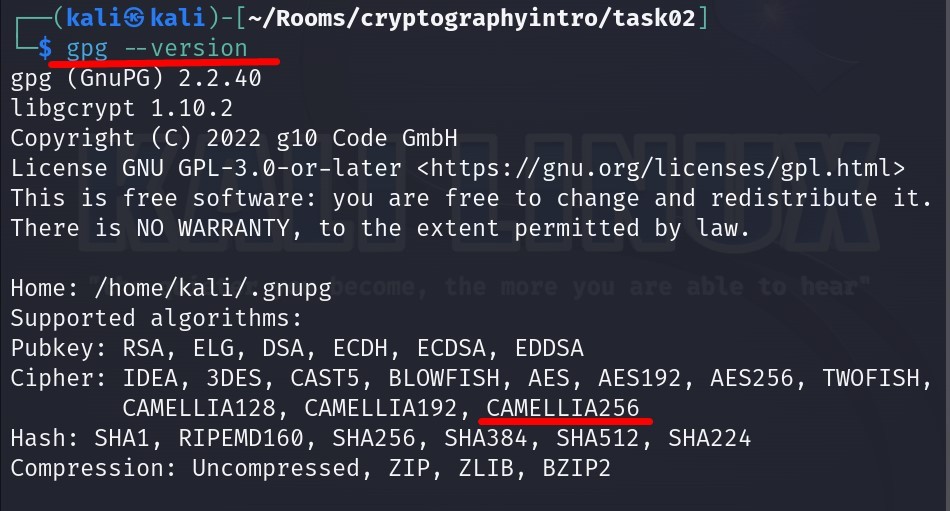
Yes, we have the necessary algorithm(CAMELLIA256) as you can see above.
Then we can use the gpg right now.
The command :
gpg --output quote03_decrypted.txt --decrypt quote03.txt.gpg
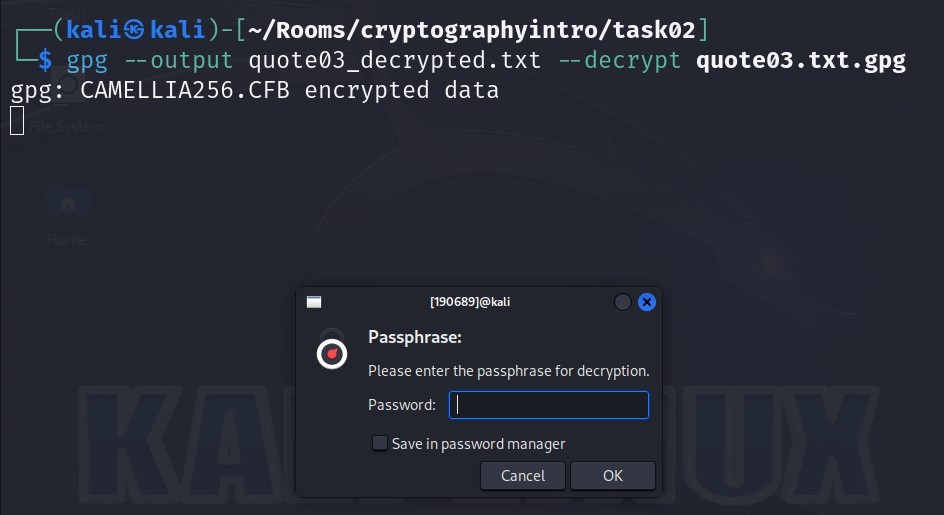
Type the key “s!kR3T55” given in the question into Password field and click on the OK button.
After decrypting process, now we have our decrypted file named “quote03_decrypted.txt” as the output :
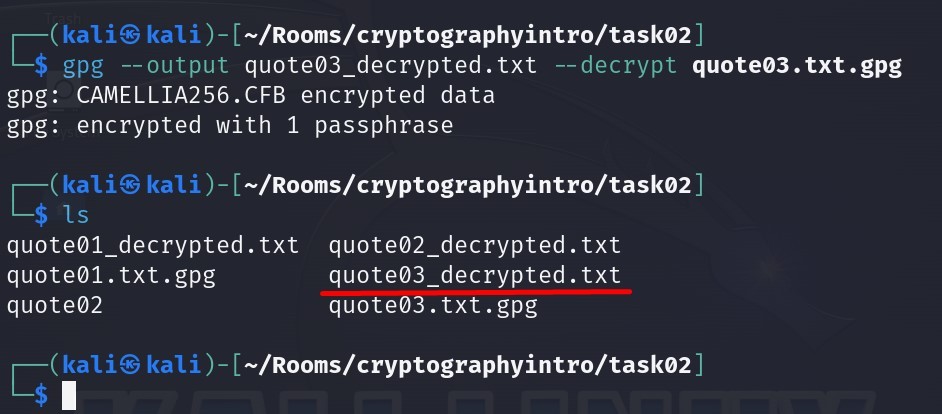
Let us read the file right now :
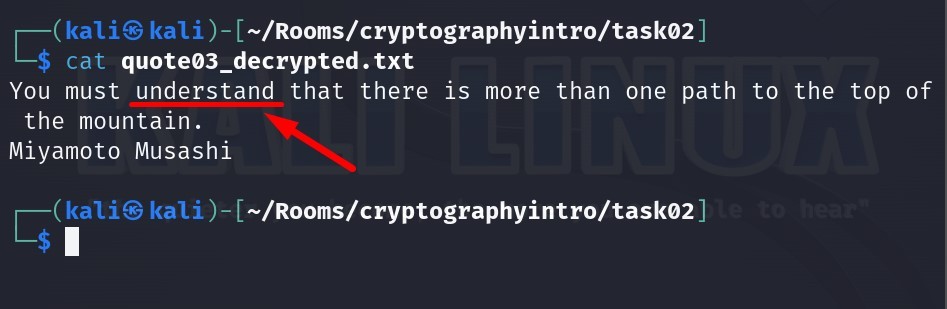
Answer: understand
Task 3: Asymmetric Encryption
Answer the questions part :
On the AttackBox, you can find the directory for this task located at /root/Rooms/cryptographyintro/task03; alternatively, you can use the task file from Task 3 (“Task 2” was mistakenly written on TryHackMe) to work on your own machine.
Question -1 :
Bob has received the file ciphertext_message sent to him from Alice. You can find the key you need in the same folder. What is the first word of the original plaintext?
Solution :
Let’s navigate to the task03 directory to see the files we will work on :
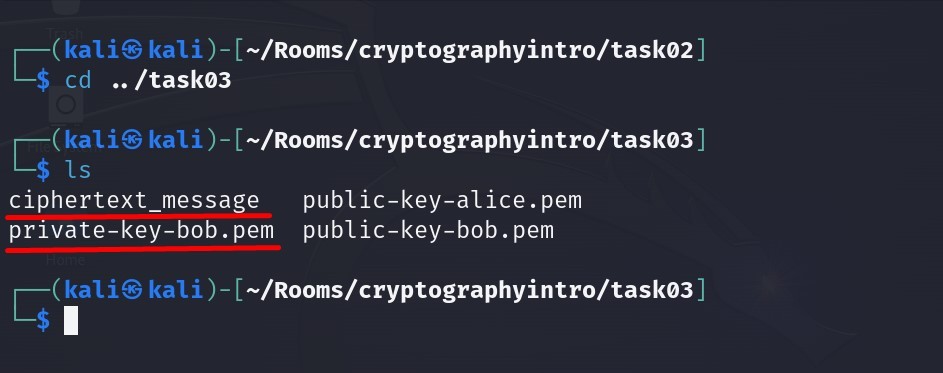
In order to figure out the first word of the original plaintext, we first need to decrypt the encrypted file ciphertext_message .
Since Alice encrypted the file of “ciphertext_message” by using Bob’s public key, we use Bob’s private key (private-key-bob.pem) in order to decrypt the file. And let’s name the output file (decrypted file) as “decrypted_ciphertext_message.txt”
The command to do this :
openssl pkeyutl -decrypt -in ciphertext_message -inkey private-key-bob.pem -out decrypted_ciphertext_message.txt
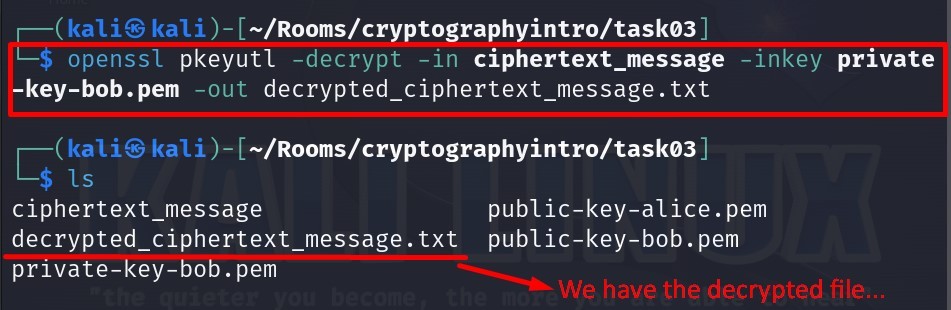
Let us read the file right now :
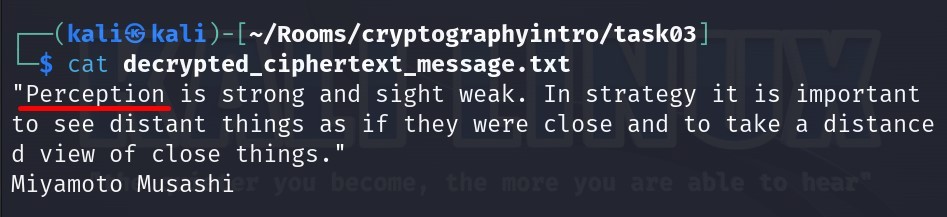
Answer : perception
Question -2 :
Take a look at Bob’s private RSA key. What is the last byte of p?
Solution :
Bob’s private key file is “private-key-bob.pem” .
To read this file, the command we need is :
openssl rsa -in private-key-bob.pem -text -noout
The “p” value corresponds to the “prime1” section in the private key. We will look at the “prime1” section.
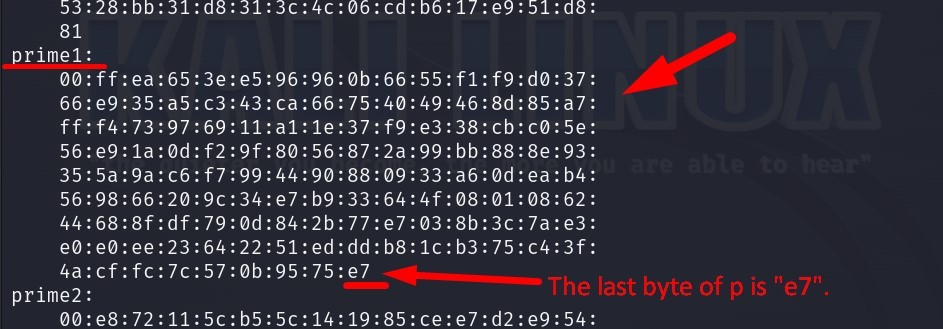
Answer : e7
Question -3 :
Take a look at Bob’s private RSA key. What is the last byte of q?
Solution :
We already have had the private key value in the previous question.
Now we look at the “q” value over the same output.
The “q” value corresponds to the “prime2” section.
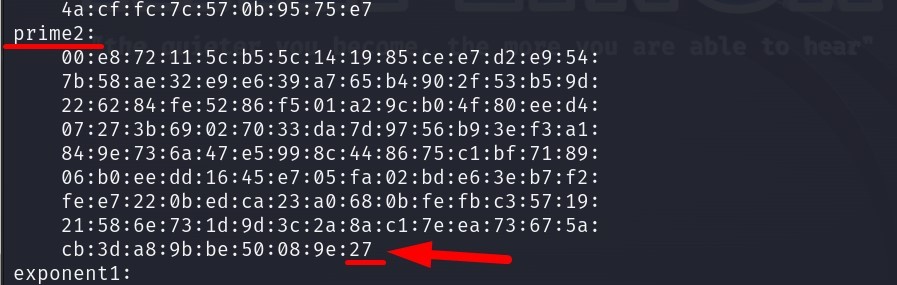
Answer : 27
Task 4: Diffie-Hellman Key Exchange
Answer the questions part :
On the AttackBox, you can find the directory for this task located at /root/Rooms/cryptographyintro/task04; alternatively, you can use the task file from Task 4 to work on your own machine.
Question -1 :
A set of Diffie-Hellman parameters can be found in the file dhparam.pem. What is the size of the prime number in bits?
Solution :
To read this file, the command we need is :
openssl dhparam -in dhparams.pem -text -noout
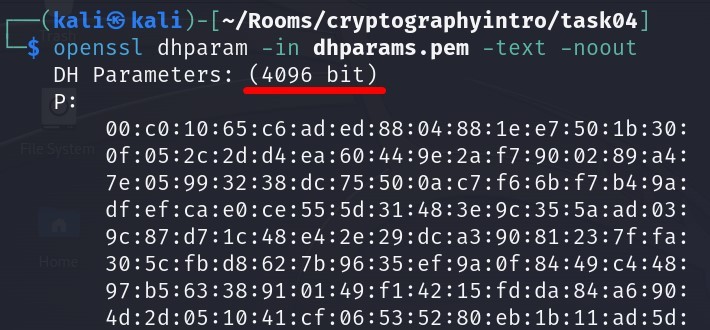
For a 4096-bit Diffie-Hellman key exchange, the prime number P will be 4096 bits.
Answer : 4096
Question -2 :
What is the prime number’s last byte (least significant byte)?
Solution :
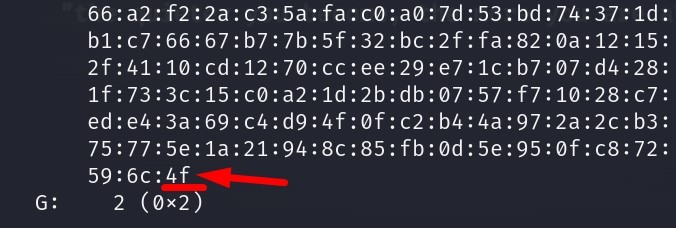
Answer : 4f
Task 5: Hashing
Answer the questions part :
On the AttackBox, you can find the directory for this task located at /root/Rooms/cryptographyintro/task05; alternatively, you can use the task file from Task 05 to work on your own machine.
Question -1 :
What is the SHA256 checksum of the file order.json?
Solution :
In order to obtain the SHA256 checksum of the file “order.json”, we use the command below.
sha256sum order.json
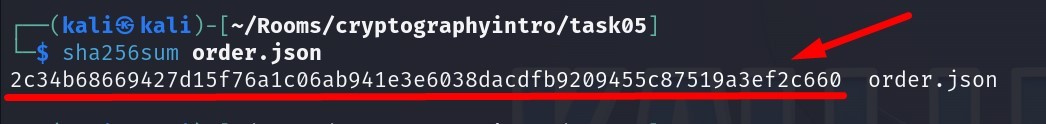
Answer : 2c34b68669427d15f76a1c06ab941e3e6038dacdfb9209455c87519a3ef2c660
Question -2 :
Open the file order.json and change the amount from 1000 to 9000. What is the new SHA256 checksum?
Solution :
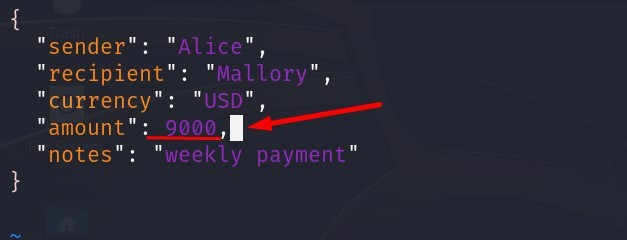
After changing the amount value, we can produce the new SHA256 checksum value of the order.json.
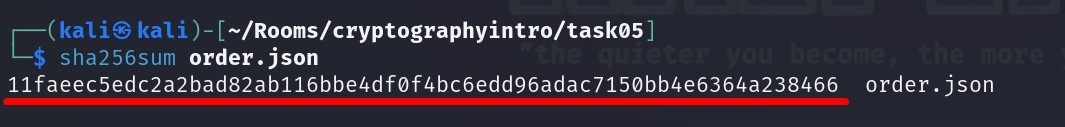
Answer :
11faeec5edc2a2bad82ab116bbe4df0f4bc6edd96adac7150bb4e6364a238466
Question -3 :
Using SHA256 and the key 3RfDFz82, what is the HMAC of order.txt?
Solution :
To find the HMAC of order.txt, the command will be this :
hmac256 3RfDFz82 order.txt
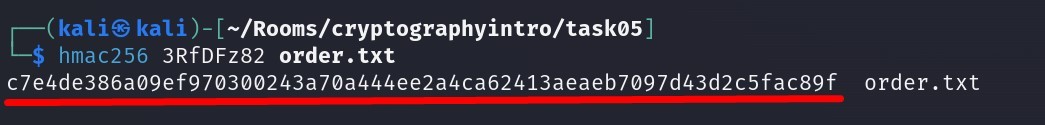
Answer :
c7e4de386a09ef970300243a70a444ee2a4ca62413aeaeb7097d43d2c5fac89f
Task 6: PKI and SSL/TLS
To answer the questions below, you need to inspect the certificate file cert.pem in the task06 directory. You can use the following command to view your certificate:
openssl x509 -in cert.pem -text
Answer the questions part :
On the AttackBox, you can find the directory for this task located at /root/Rooms/cryptographyintro/task06; alternatively, you can use the task file from Task 06 to work on your own machine.
Question -1 :
What is the size of the public key in bits ?
Solution :
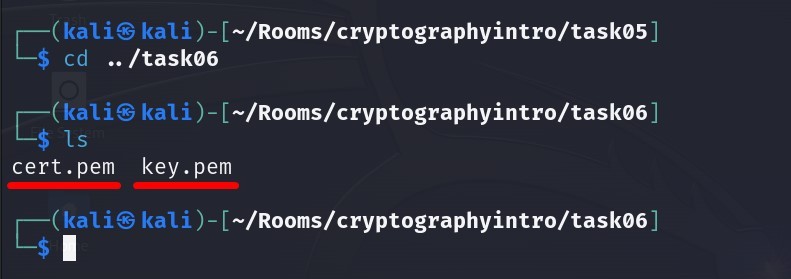
We use the following command to view the public key and its details in our certificate. Also this command has already given above to view the certificate.
openssl x509 -in cert.pem -text
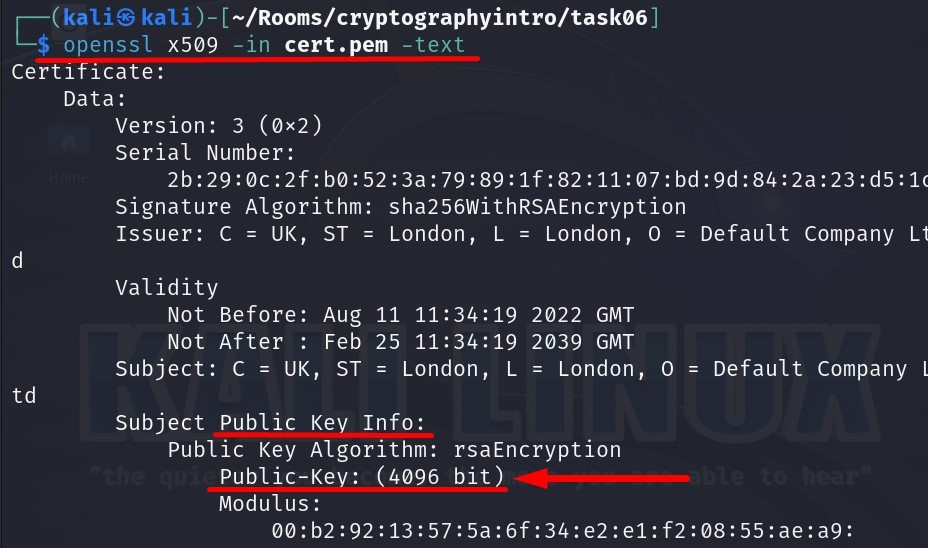
We will use this output which contains certificate details to answer the question-2.
Answer : 4096
Question -2 :
Till which year is this certificate valid?
Solution :
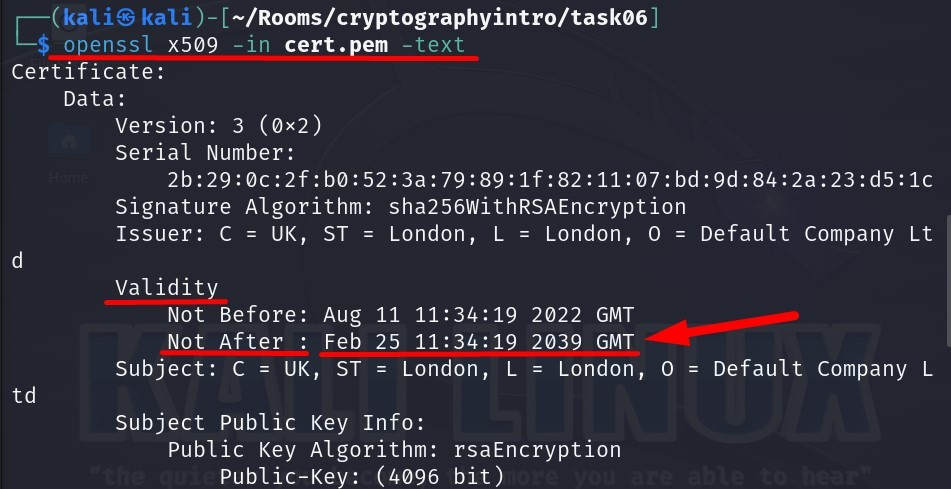
Answer : 2039
Task 7: Authenticating with Passwords
Answer the questions part :
Question -1 :
You were auditing a system when you discovered that the MD5 hash of the admin password is 3fc0a7acf087f549ac2b266baf94b8b1 . What is the original password ?
Solution :
Hint: Use an online MD5 crack tool such as md5online.org or md5decrypt.net
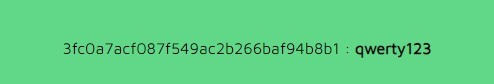
Answer : qwerty123
Task 8: Cryptography and Data — Example
“No answer needed”
The room is completed…