An interesting dissertation
I recently read a dissertation titled “How Hackers Think: A Mixed Method Study of Mental Models and Cognitive Patterns of High-Tech Wizards” by Timothy C. Summers which focused on understanding the cognitive abilities of ethical hackers, aiming to shed light on their thought processes and problem-solving techniques. I wanted to share it with you because Mindsets is crucially important, it affect everything we do, feel, think, and experience.
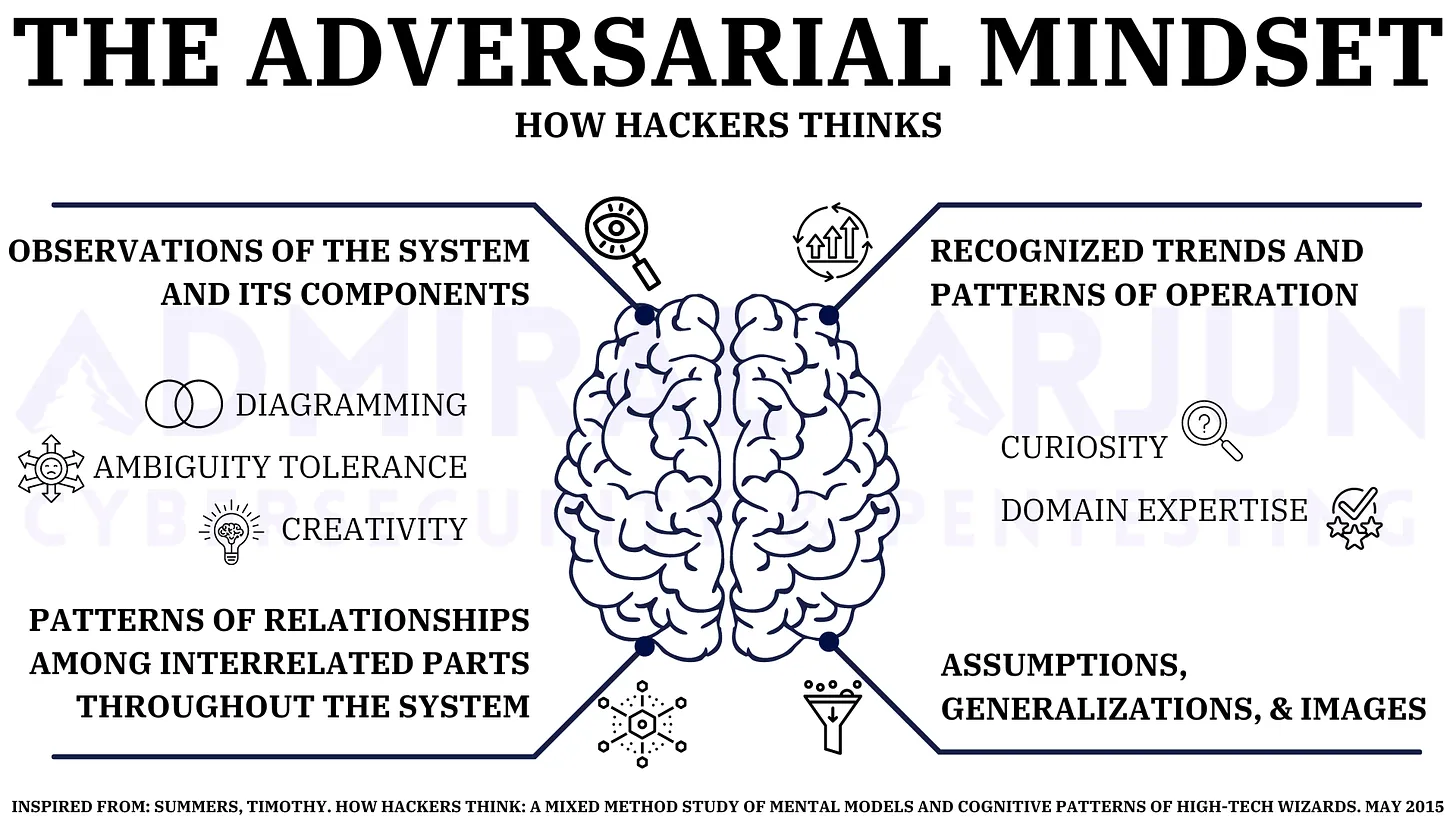
Since I’m an aspiring hacker and I strongly believe so you are if are reading this far, I just wanted to get this mindset right and kinda write about it a bit. The dissertation answered several questions that were hypothesized by 3 studies conducted with 100+ hackers around the world. Let’s enumerate them;
Study I: How Hackers Think: A Study of Cybersecurity Experts and Their Mental Models
- Finding #1: Hackers have a high tolerance for ambiguity in their work environment.
- Finding #2: Skilled hackers exhibit elevated creativity and curiosity in their problem solving.
- Finding #3: A hacker’s effectiveness depends on their mental models.
- Finding #4: Expertise and diagramming are instrumental for building effective mental models for hackers.
- Finding #5: Patterning is a key element of the hacker mind.
Study II: How Hackers Think: Understanding the Mental Models and Cognitive Patterns of High-Tech Wizards
- Finding #1: Expertise and diagramming are instrumental for learning and forward thinking.
- Finding #2: Curiosity facilitates the learning process for hackers.
- Finding #3: Creativity is everywhere.
Study III: How Hackers Think: Sociocultural Facets and Understanding Their Impact on the Hacker Mind
- Finding #1: Hackers that do not attend conventions have more expertise.
- Finding #2: Differences between credential holders and those that do not possess credentials.
What is adversarial thinking?
Adversarial thinking is one of many natural ways of looking at the world, especially security. Hackers tend to have this mindset. Adversarial thinking involves understanding the technological capabilities of potential hackers and anticipating where, when, and how they might attack.
Hackers are often stereotyped as malicious actors who break into computer systems for personal gain. However, the reality is that hackers are a diverse group of people with a wide range of motivations. Some hackers are indeed malicious, but others are security experts, ethical researchers, and creative problem-solvers. To better understand this, let’s look at the etymology (although not official) of the word “hack“;
“The ‘original’ hackers were computer professionals who, in the mid-sixties, adopted the word ‘hack’ as a synonym for computer work, and particularly for computer work executed with a certain level of craftsmanship.
Then in the seventies, assorted techno-hippies emerged as the computerized faction of the counterculture of the day. …What characterized the second wave hackers was that they desperately wanted computers and computer systems designed to be useful and accessible to citizens.
Finally, in the second half of the eighties the so-called cu [computer underground] emerged, appropriated the terms ‘hacker’ and ‘hacking’ and partly changed their meaning.
To the computer underground, ‘to hack’ meant to break into or sabotage a computer system, and a ‘hacker’ was the perpetrator of such activities”
Says “Gisle Hannemyr”
Developing the Adversarial Mindset
I believe developing this adversarial mindset will only elevate our current understanding and perspective of the security posture. Whether it’s blue teaming or red teaming, since both goes hand-in-hand, this mindset would definitely come in clutch. This mindset can shape the way we view the tech and constrict or expand the way we engage with them.
“Attack is the secret of defense; defense is the planning of an attack” - Sun Tzu
Here are couple of way I personally believe will contribute towards the development of adversarial mindset; feel free to add more in comment… (^^)
- Practice thinking like an attacker: When you’re using a system or process, try to think of ways that it could be exploited or broken. Think how possibly it could go wrong.
- Challenge your assumptions: Don’t take anything at face value. Question everything and look for weaknesses. Usually, asking “What”, “How” and “Why“ sorta questions will uncover lot of things.