
Setup
First, we need to connect to the HTB network. There are two different methods to do the same:
- Using Pwnbox
- Using OpenVPN
(Click here to learn to connect to HackTheBox VPN)
Introduction
This machine helps us to familiarize ourselves with the Server Message Block (SMB) services.
Using the SMB protocol, an application (or the user of an application) can access files at a remote server, along with other resources such as printers. Thus, a client application can read, create, and update files on the remote server. It can also communicate with any server program that is set up to receive an SMB client request.
Mostly SMB services are seen running on windows machines. Usually, SMB runs at the Application or Presentation layers of the OSI model. The Transport layer protocol that Microsoft SMB Protocol is
most often used with is NetBIOS over TCP/IP (NBT)
An SMB-enabled storage on the network is called a share. These can be accessed by any client that has the address of the server and the proper credentials
Scanning and enumeration
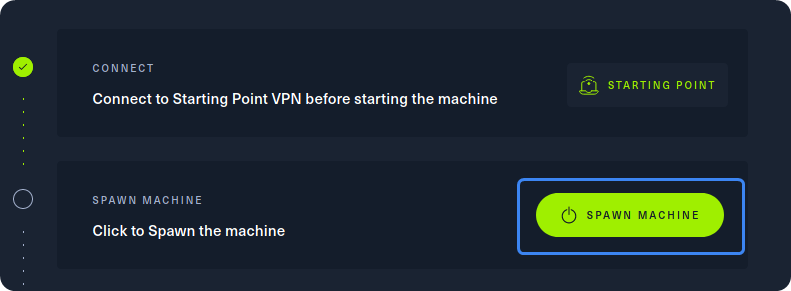
After our connection to the HTB network is successfully established, we can spawn the target machine from the Starting Point lab’s page by clicking on “SPAWN MACHINE” as show above. After spawning the machine, we can check if our packets reach their destination by using the ping command.
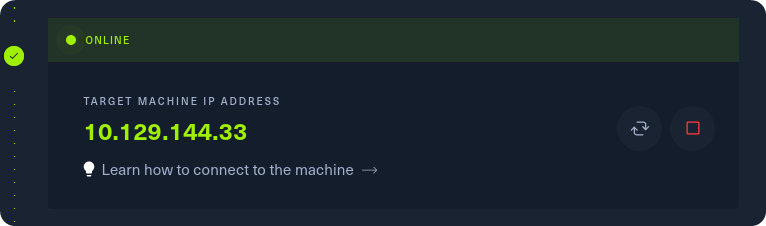
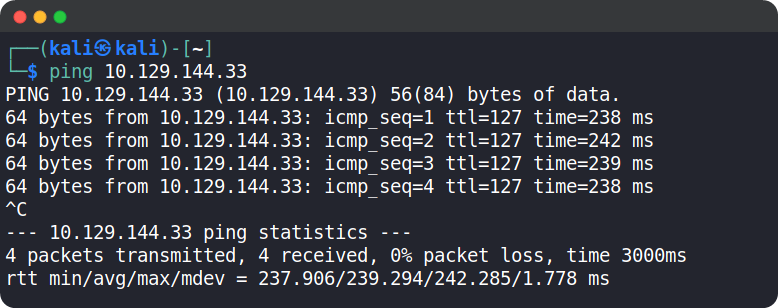
Grab the IP address of your current target and paste it into your terminal after typing in the ping command. After 4-5 successful replies from the target, we can confirm that our connection is formed and stable. We can cancel the ping command by pressing the Ctrl + C combination on our keyboard.
Now let’s start scanning the target using nmap. nmap will send requests to the target’s ports in hopes of receiving a reply, thus determining if the said port is open or not.
We can use the following nmap command: sudo nmap -sV {target_ip}
{target_ip} has to be replaced with the IP address of the Dancing machine.
The -sV switch is used to display the version of the services running on the open ports.
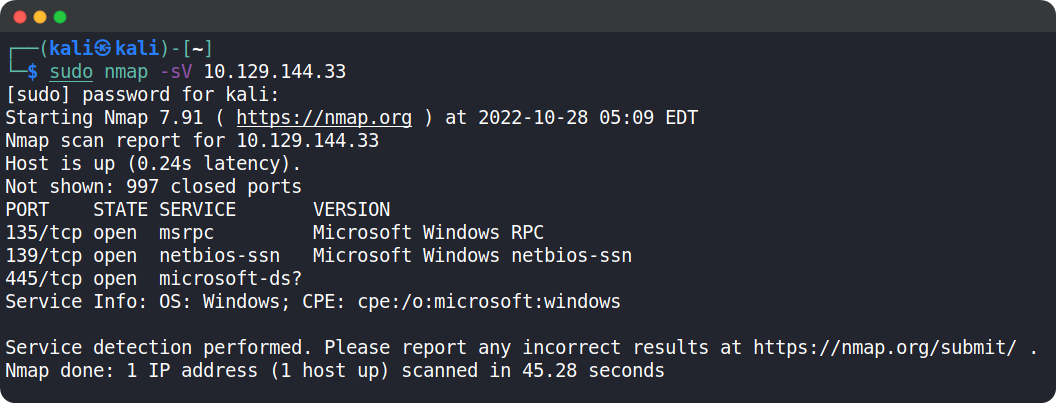
After the completion of the scan, we can see that port 445/tcp for SMB is up and running and it means that we have an active share that we could potentially explore
A script called smbclient can be used to enumerate the share content on the remote system.
If you don’t have smbclient , you can use the following command to install it:
sudo apt-get install smbclient
Now, we can try to connect to the target using smbclient
Type in the following command and press enter: sudo smbclient -L {target_ip}
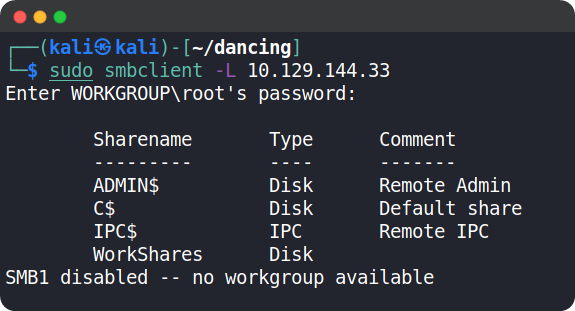
Smbclient will attempt to connect to the remote host and check if there is any authentication required. By default, if we do not specify the username, it will use our local machine’s username. Since we do not know about any remote usernames present on the target host, we will continue with our local machine’s username and a random password.
After running the command, we can see there are 4 separate shares:
- ADMIN$ = These are hidden network shares. These allow system administrators to have remote access to every disk volume on a network-connected system. These shares cannot be permanently deleted but may be disabled.
- C$ = The operating system is hosted here.
- IPC$ = Used for inter-process communication via named pipes and is not part of the file system.
- WorkShares = This is a custom share
Foothold
Now we will try to connect to each of the shares (except IPC$) using our local machine’s username and a blank password.
On trying ADMIN$ and C$ using the following command:
smbclient \\\\{target_ip}\\{share_name}
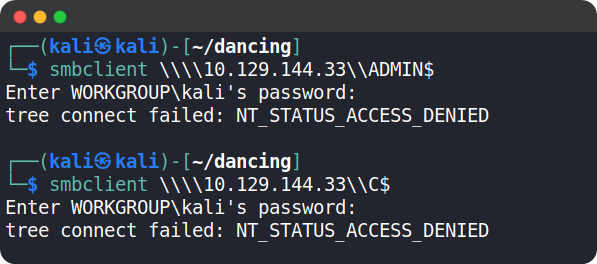
We get an error saying we don’t have the permission to access it.
Now, let’s try to log in to the custom WorkShares SMB share. Since this is human made, we might get lucky and gain access to the share.
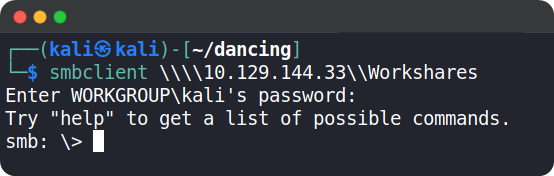
🥳 Bingo! We got logged in.
We can use the help command to see what we can do in this shell.
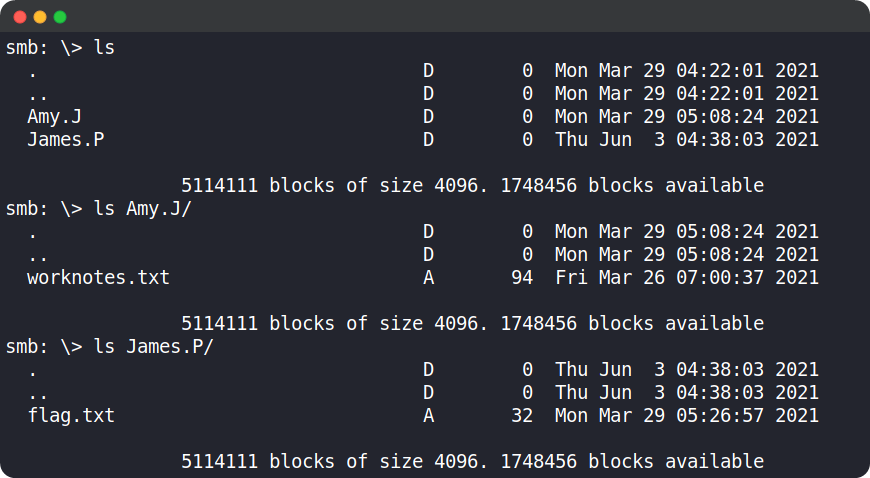
On typing the ls command, we can see that there are two files, Amy.J and James.P. The Amy.J directory contains a file called worknotes.txt and James.P contains a file called flag.txt, both can be downloaded using get command.
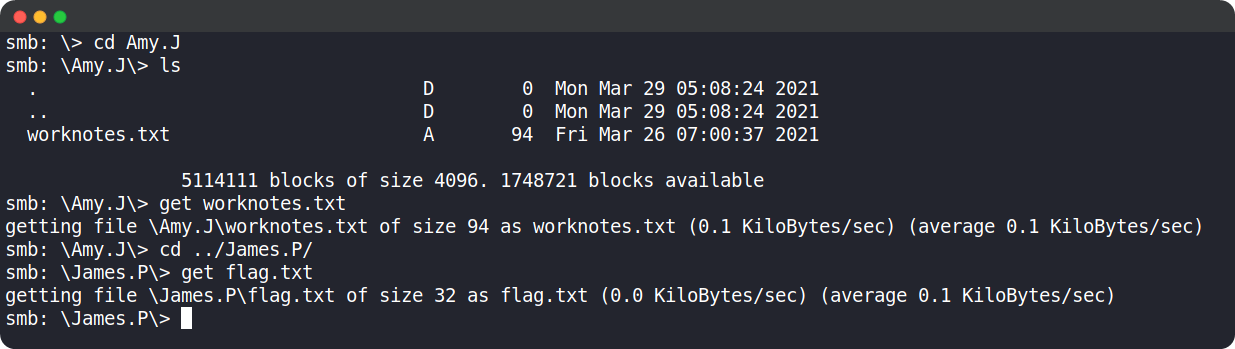
After downloading both files, we can type exit and come out of the smb shell and check the downloaded files in the current directory of our local machine.
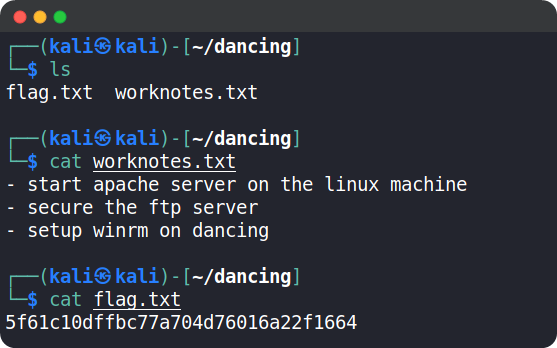
The worknotes.txt file contains other services that could be exploited, in our case this is just a proof of concept. So, we will not need this file
The flag.txt file contains the flag for this machine. Copy the flag and paste it into the Starting Point lab’s page to complete your task.
Congrats, you have just pwned Dancing! 👏
—
Task answers
Task 1: What does the 3-letter acronym SMB stand for?
Server Message Block
Task 2: What port does SMB use to operate at?
445
Task 3: What is the service name for port 445 that came up in our Nmap scan?
microsoft-ds
Task 4: What is the ‘flag’ or ‘switch’ we can use with the SMB tool to ‘list’ the contents of the share?
-L
Task 5: How many shares are there on Dancing?
4
Task 6: What is the name of the share we are able to access in the end with a blank password?
WorkShares
Task 7: What is the command we can use within the SMB shell to download the files we find?
get
⛳ Root flag:
5f61c10dffbc77a704d76016a22f1664