Hey guys! What’s Up!? Hope you all are doing great! This is my first blog @Hacklido
This is a copied blogpost of mine, which was originally written on Medium. I will Publish some cool blogs specifically for hacklido community, So Stay Tuned!!
What is RECONNAISSANCE?
Reconnaissance refers to a set of processes and techniques, such as footprinting and scanning and enumeration, that are used to gather and covertly discover as much information as possible about a target system. Reconnaissance is an essential step in locating and stealing confidential information. There are two types of Reconnaissance:
• Active Reconnaissance.
• Passive Reconnaissance.
What is Active and Passive Reconnaissance?
Well, the simplest answer is,
In Active Reconnaissance we gather information about our target or website by interacting with it. For example: If we want to find the services running on the website, we will have to interact with the website.
Passive Reconnaissance is just the opposite, in this type of Reconnaissance, we collect information without interacting with the target. For example: If we gather some historical data, using websites such as web-archive, we are not directly interacting with the website.
I believe by now you know what Reconnaissance is and about its types.
Why do you need Reconnaissance?
Reconnaissance itself holds an important role in Penetration-Testing. Reconnaissance is an important tool for penetration testing and the beginning point of many data breaches. It is the very first step whenever you start any kind of testing, in this step you gather info about your target, hosts, and a bunch of things! Testing without Reconnaissance is like going into a dark tunnel without a torch.
Benefits of doing Reconnaissance.
• You get to know about your target.
• You explore your target, and try to understand the workflow of the website, which helps you in your attacking stage.
• Sometimes you find Sensitive-Information, which can affect the website in many ways.
• Sometimes you find exposed secrets of the website, which weren’t meant to be public.
Management skills:
I’ll share how I do my recon for any domain, but before that I wanna talk about some skills which will help you keep your things neat and clean.
According to me, if you keep your work clean, you’ll be more productive. So, let’s suppose you’ve picked a program on Bugcrowd, and you are starting with your testing, Make a separate folder for each thing, example:
cd Desktop
mkdir Bug-Hunting
cd Bug-Hunting
mkdir Bugcrowd
cd Bugcrowd
mkdir Program-Name
cd Program-Name
Now whatever you want to test under this directory i.e. /Desktop/Bug-Hunting/Bugcrowd/Program-Name/.
Also make sure to write the output of every tool into separate files, for example if you gathered subdomains, save them in a file, if you did a Nmap scan, save the result in the file. This will help you keep all your findings in one place and you can view them whenever you want.
Here the cool part begins! Below is my Tools!
So, whenever I start testing any domain the first thing, I do is start my Passive recon. Below I mentioned every tool/website I use. Let us first talk about some CLI-Tools.
1. Dig
Dig stands for Domain Information Groper, it is a Linux Command line tool that performs DNS lookup by querying name servers and displaying the result to you. In this tutorial, you’ll find all the basic uses of the command you should know in the Linux operating system. It’s helpful in finding the cnames, MX records etc. You can use this command for finding every info what dig can give:
~#root㉿kali: dig target.com any
2. Subfinder
Subfinder is a subdomain enumeration tool written in the Go programming language. Subfinder is used for discovering passive subdomains of websites by using digital sources like Censys, Chaos, Recon.dev, Shodan, Spyse, Virustotal, and many other passive online sources. Command for enumerating subdomains:
~#root㉿kali:subfinder -d google.com
You can also use verbose mode but assigning “-v” in the command
~#root㉿kali:subfinder -v -d google.com
3. Httprobe
Httprobe is available on Github and the tool was created by Tom Hudson aka tomnomnom. It takes a list of domains and probe for working http and https servers. Basic Command:
~#root㉿kali:cat domains.txt | httprobe
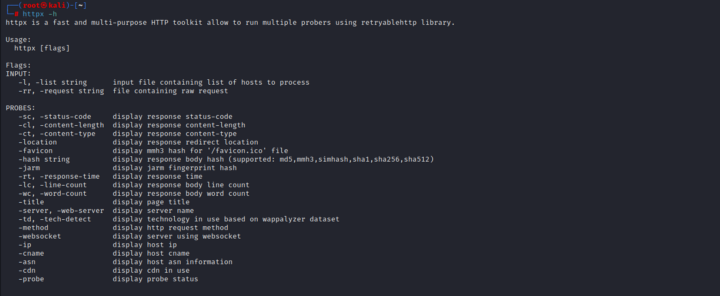
4. Httpx
Httpx is a fast and multi-purpose HTTP toolkit allow to run multiple probers using retryablehttp library. Basic Command:
~#root㉿kali:cat domains.txt | httpx -sc
5. Ffuf
Ffuf is a fast directory fuzzing tool, you can use it to enumerate more directories in less amount of time. It has several useful features such as showing the output of the status codes which you desire. Baic Command:
~#root㉿kali: ffuf -u https://targett.com/FUZZ -w /usr/share/wordlists/dirb/common.txt/
Now let us talk about some cool GUI tools.
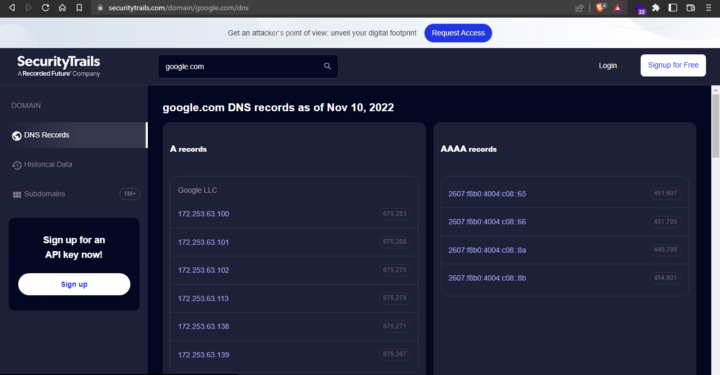
1. SecurityTrails
SecurityTrails enables you to explore complete current and historical data for any internet assets. IP & DNS history, domain, SSL, and Open Port intelligence. Just enter the domain name you want to get the details of it’ll give every MX, DNS, TXT, etc details.
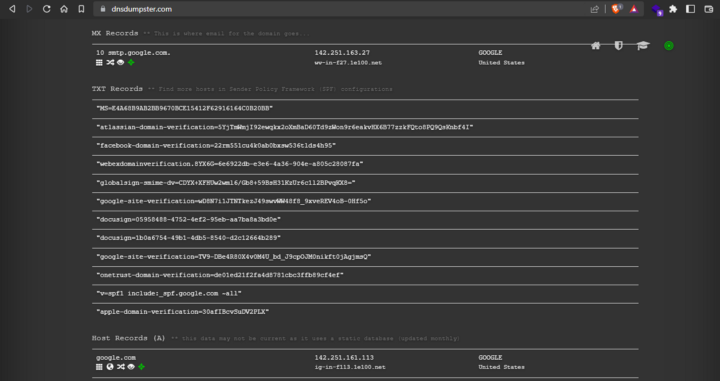
2. DnsDumpster
DnsDumpster is very similar to dig, difference is, it provides a GUI for you to work on. It also provides you the graphs which are very helpful in enumerating. Just enter the domain name you want to get the details of.
3. Censys
Censys is a platform that helps you to discover Information of any website that is accessible from the Internet. With the help of Censys, you could find information such as:
IP Address
Open Ports
SSL Certs
Hosting Providers
etc.

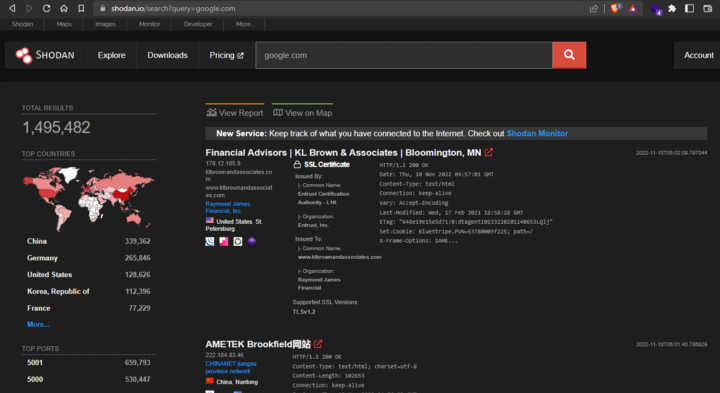
4. Shodan
Ah! Comon… How can we forget Shodan!?
Shodan is the world’s first search engine for Internet-connected devices. Discover how Internet intelligence can help you make better decisions. Sign Up Now. Explore the Platform. Beyond the Web, Websites are just one part of the Internet. Use Shodan to discover everything from power plants, mobile phones, refrigerators and Minecraft servers. You can get a lot of valuable information using Shodan such as:
Organizations
Ip Addresses.
SSL Certificates.
Services.
Favicon Hashes.
etc.
5. Zoomeye
I came across one more website and that is ZoomEye. It is another Search engine and can be used to discover:
Web Servers.
IP & Ports.
Headers & Status Codes.
Vulnerabilities.
etc.
I hope these tools will help boost your recon! Good luck hacker!
BONUS PART!!
I would like to add a Bonus Part to this blog. This bonus part will contain how you can make your testing easier, and organize your work the right way. I know you may ask; you’ve already said these things above… That’s Half of it, here I’ll complete it. I will also talk about some more recon methods like source-code review, some Shodan dorks, and lastly some amazing Twitter accounts, which provide cool bug-bounty tips, and will be helpful for you. Let’s start!
Method to make your recon faster and useful:
This is focused on beginners who want to make the best use of their work. As mentioned above you can create separate folders for different targets to keep yourself organized, let’s now talk about how you can make best use of your outputs!
For example, you were given a domain as: *.anywebsite.com.
You can follow this to keep all of your files at one place with desired outputs:
cat target_domains.txt | httprobe > target_live_domains.txt
cat target_live_domains.txt | waybackurls > target_waybackurls.txt
cat target_waybckurls.txt | httpx -sc -title > target_status.txt
Now you can sort between files, and also view and use them whenever you want!
Let us now talk about source code review!
🗲What do you mean by Source Code Review?
A secure code review is a line-by-line analysis of the source code of an application, usually performed to find any security-related errors overlooked during the development phase. These security vulnerabilities may have bypassed penetration testing. You can find js files which can contain some juicy information such path to Internal-Login-Panels, exposed database secrets, exposed keys, token etc.
Shodan-Dorking
Wohooo! We’ve reached a very cool part! Shodan dorking is one of the most favorite things of most of the hackers!
🗲What is Shodan Dorking?
It is almost similar to Google-Dorking, but in this instead to searching on google you search in Shodan. Wanna know some cool Shodan dorks? Here are few of them:
"Set-Cookie: mongo-express=" "200 OK"
mysql port:"3306"
port:"9200" all:"elastic indices"
port:5432 PostgreSQL
http.title:"BIG-IP®-+Redirect"+”Server"
http.favicon.hash:anyfaviconhash
http.html:UA-xxxxxxxxx-x
Note: There are many more dorks, you can search for them on google or twitter!
#Twitter Handles:
Let us view some cool twitter handles which share bug-bounty related resources every day!
Abhishek Meena.
Begin n Bounty.
Anton.
There are some cool ones too:
rez0.
Aditya Shende.
zseano.
SickSec.
Arth Bajpai.
Remonsec.
Nagli.
Jhaddix.
GodFather Orwa.
dccybersec.
XSSRat.
Bugcrowd.
Mohsin Khan.
Dawgyg.
Intigriti.
DrSniper.
Reganathan.
Gothwam Naidu Poona
Thank you so much Guys for your time reading this blog, I hope you liked it! Please leave any kind feedback you have in the comments. If you have any questions, please reach out to me on my twitter.
My Twitter: Agent472458