Hey there, fellow readers! It’s been a while, but I’m back! Today, we’re going to dive into something fascinating – “Javascript”. In this blog, you’ll learn how to analyze JS files and uncover hidden secrets! Let’s get started!! 🔍🕵️♂️

What is “Javascript” and how do application use it?
-> JavaScript is a versatile programming language primarily used to enhance the interactivity and functionality of websites. It runs in the browser, allowing developers to create dynamic content, such as interactive forms, animations, and real-time updates without needing to reload the page. Applications use javascript in various ways. Some of them are:
- Interactive User Interfaces: JavaScript powers dynamic content changes without reloading the page, enhancing user interaction.
- Form Validation: It checks user input in forms for errors before submission, improving data integrity.
- Asynchronous Data Loading: JavaScript fetches data in the background, allowing seamless content updates (e.g., through AJAX).
- Animations and Effects: It creates animations and visual effects, making websites more engaging.
- Event Handling: JavaScript responds to user actions like clicks, hovers, and keystrokes, providing a responsive experience.
What is “JS Recon”?
JS Recon, short for JavaScript Reconnaissance, involves analyzing JavaScript files within web applications to uncover hidden secrets and sensitive information. Here are some ways it’s being done:
- Source Code Analysis: Analyse JavaScript files to find hardcoded secrets like API keys, credentials, and configuration details.
- Endpoint Discovery: Identify API endpoints and network requests to reveal backend server information.
- Function Analysis: Analyse JavaScript functions to detect insecure practices or logic flaws.
- Hidden Parameters: Uncover hidden or undocumented parameters used for debugging or additional functionality.
How to do JS Recon and how “I” do it?
Alright guys, now the fun part begins, In this part I’m gonna tell you about 2 methods which I follow for JS-Recon.
Method-1:
Suppose we have a target “website.com”. Now Let’s see some Tools
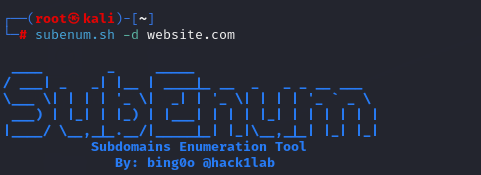
> Subenum
The first thing I do is use “subenum.sh” by Bing0o. This script is super helpful in finding subdomains.
Command: subenum.sh -d website.com
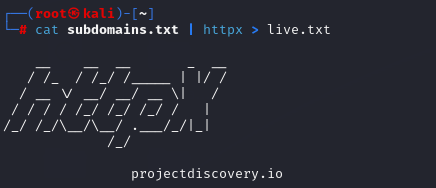
Httpx
After fetching all the subdomains, I filter the live domains using “ Httpx ” by ProjectDiscovery
Command: cat collected_subdomains.txt | httpx > live.txt
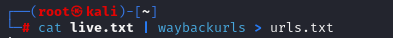
WaybackUrls
After collected live domains, I gather URLs using “Waybackurls” by Tomnomnom
Command: cat live.txt | waybackurls > urls.txt
For this step you can also use tools like Katana, Gau etc. Then combine all the URLs in a single file.
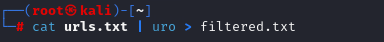
URO
We have the URLs, but most of the data will be similar, so we have to filter the data. We will use “URO” by s0md3v
Command: cat urls.txt | uro > filtered.txt
Grep
Now we have the required data and we can begin Looking for JS-Files. We will use Grep for this step.
Command: cat filtered.txt | grep "\.js\b" > js-files.txt
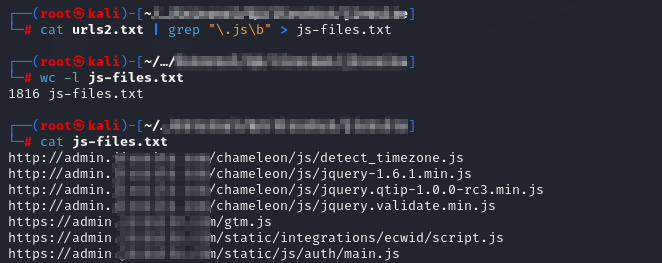
Let’s First break what our command is doing:
- grep: The command-line utility used for searching text.
- ‘.js\b’: The pattern to match.
- . matches a literal period.
- js matches the string “js”.
- \b is a word boundary that ensures “js” is not followed by any alphanumeric characters, meaning it matches exactly “.js”.
=> Now Theres another thing in this step. After you grab all the JS files, obviously there will be lot on unnecessary JS files, which are present by default on the application and have no use for us. You have to identify such type of files yourself, or otherwise you are going to end up wasting your time looking into unnecessary JS files. For Ex- In image you can see some files as: time-zone.js, gtm.js. These files have no purpose can does not contain Sesnsitive information. However if you look carefully, you can see a file named: “main.js”, hmm that’s something interesting. Here are few Interesting JS-Files to look for-
main.js
config.js
env.js
prod.js
etc
Httpx
We will again use Httpx to gather Live Js-URLs from the file.
Command: cat js-files.txt | httpx -mc 200 > live-js-files.txt
By this you’ll be having only valid JS files too look into.
URL Opener
Now that you have all the live URLs, it’s time to check those JS-Files manually, but if you copy each url one by one and paste in browser, you’ll be wasting a lot of your time. Instead use a service like “URL-Opener” to open bulk URLs at once. You can then check each JS files for secrets, and other sensitive information.
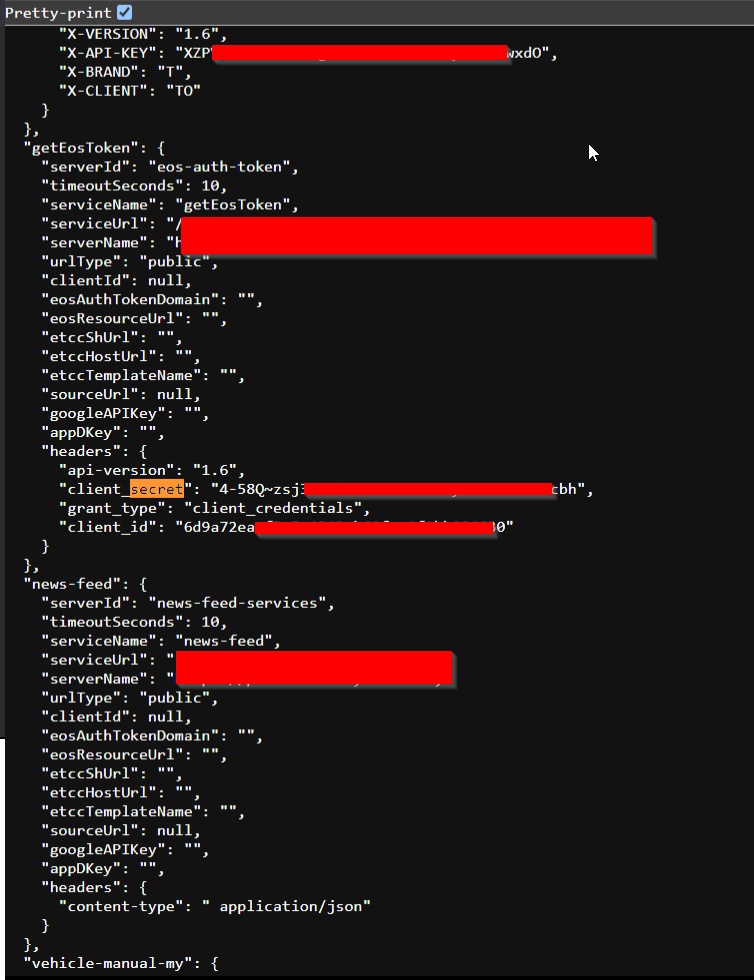
You can now grep keywords like “apikey” “Client-ID” “Client-Secret” etc to find sensitive information. For Ex-
Method-2:
For Method 2, I do similar steps, Collect Subdomains > Gather Live domains. Now once I have live domains. I use a custom script which checks the hosts and gives all the js files in that domain in a txt file.
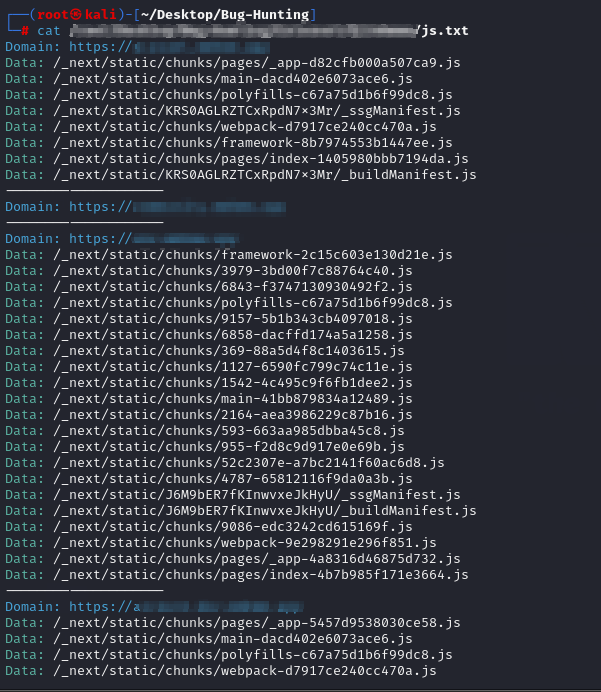
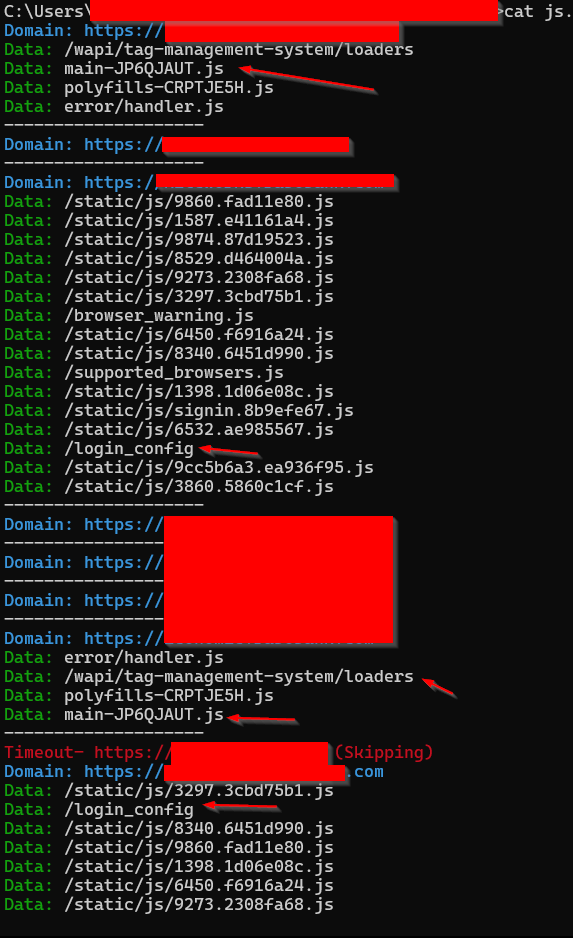
After I get all the files, I check for interesting files and then view the file in browser to analyse the JS-file.
Note- This script is private, and I'll not be sharing it right now.
Conclusion
JS Recon is crucial for uncovering hidden information that is often overlooked by researchers. Analyzing JavaScript files can reveal sensitive data like API keys, credentials, and hidden endpoints, which are essential for understanding an application’s security posture. By performing JS Recon, you gain deeper insights into the application’s structure and potential vulnerabilities, making it an indispensable part of thorough web security assessments.
Bonus
Hey! It’s the Bonus Part! This time I’m gonna talk about 1 browser extention which helps a lot in gathering secrets and it can gain you some cool info.
Trufflehog
Trufflehog is a powerful open-source tool designed to help security professionals and developers detect sensitive information in source code repositories. By scanning for high-entropy strings and other patterns that indicate the presence of secrets like API keys, passwords, and tokens, Trufflehog helps prevent the inadvertent exposure of sensitive data. It’s particularly useful for ensuring codebase integrity and security during the development process. The Trufflehog extension integrates this functionality seamlessly into your development workflow, making it easier to identify and mitigate potential security risks before they can be exploited.
Download- https://chrome.google.com/webstore/detail/trufflehog/bafhdnhjnlcdbjcdcnafhdcphhnfnhjc/
That’s it for this Blog Guys! Hope you Enjoyed and learnt something from this blog. Do share your feebacks! See you soon!