
Setup
First, we need to connect to the HTB network. There are two different methods to do the same:
- Using Pwnbox
- Using OpenVPN
(Click here to learn to connect to HackTheBox VPN)
Introduction
This box will help us to practice performing an SQL injection against an SQL database enabled web application.
SQL Injection is a common way of exploiting web pages that use SQL Statements to retrieve and store user input data.
Scanning and enumeration
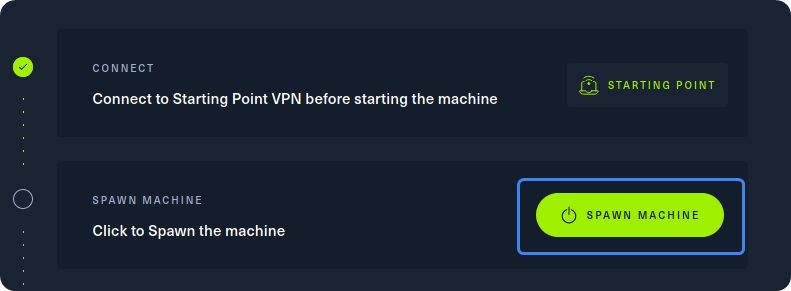
After our connection to the HTB network is successfully established, we can spawn the target machine from the Starting Point lab’s page by clicking on “SPAWN MACHINE” as show above. After spawning the machine, we can check if our packets reach their destination by using the ping command.
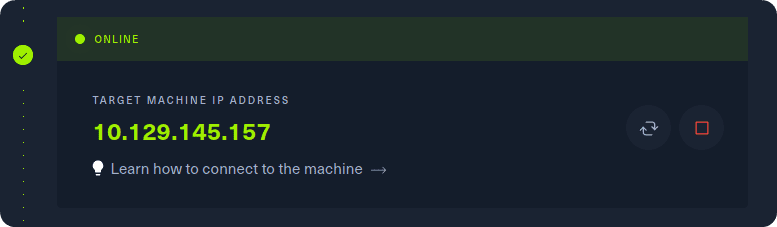
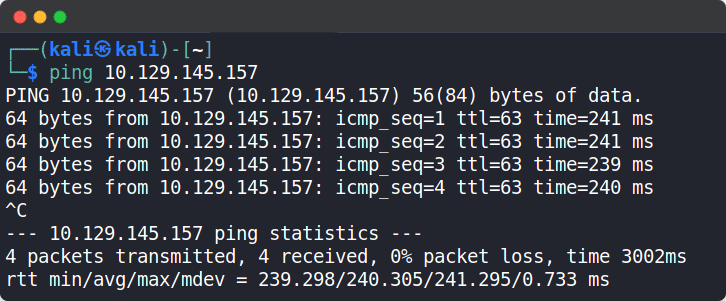
Grab the IP address of your current target and paste it into your terminal after typing in the ping command. After 4-5 successful replies from the target, we can confirm that our connection is formed and stable. We can cancel the ping command by pressing the Ctrl + C combination on our keyboard.
Now let’s start scanning the target using nmap to find any open ports and services
We can use the following nmap command: sudo nmap -sC -sV {target_ip}
{target_ip} has to be replaced with the IP address of the Dancing machine.
The -sC switch is used to perform script scan using the default set of scripts. The -sV switch is used to display the version of the services running on the open ports.
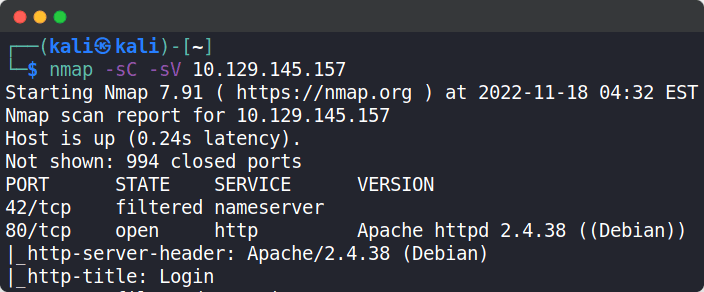
From the nmap scan, we can see that port 80 is open and it is running Apache httpd server with version 2.4.38
Apache httpd server is used for running web pages on either physical or virtual web servers.
If we type the IP address of the device into the address bar of our browser, we can see a website with a login form
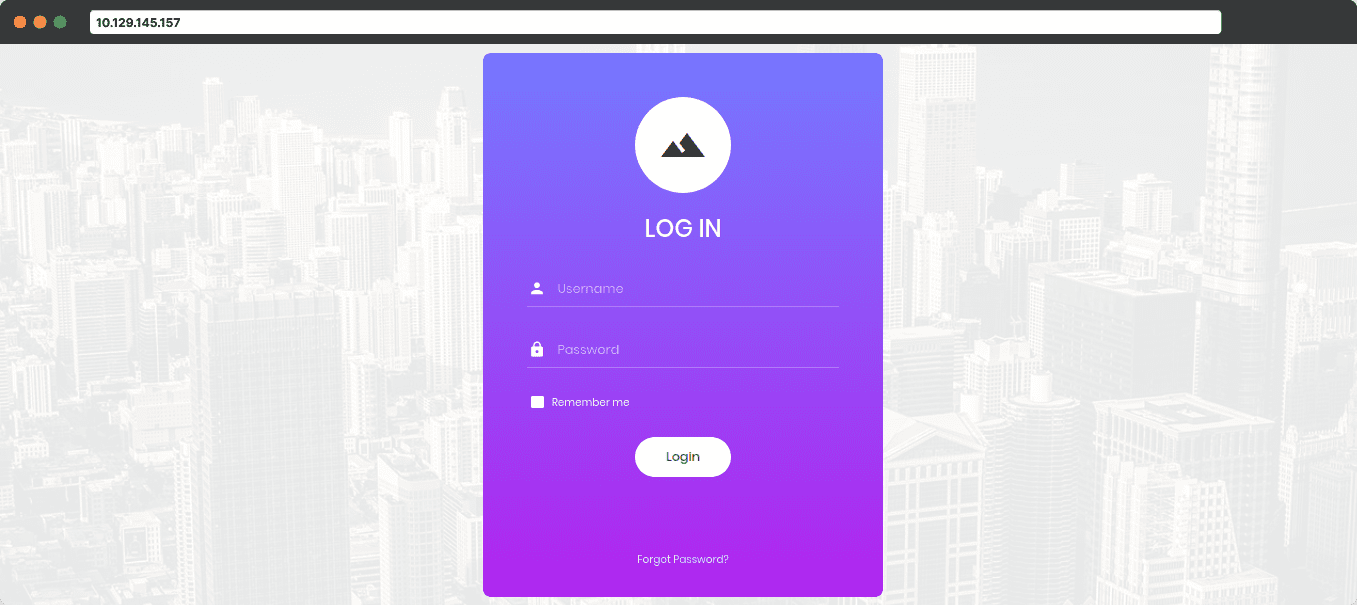
Foothold
We can pass in default credentials or use brute-forcing attacks to bypass the login system. But even after doing those we are unable to login.
So, we will try for any possible SQL injection vulnerability in the login form.
Below is an example SQL query to verify username and password and log the person in
SELECT * FROM users WHERE username='$username' AND password='$password’
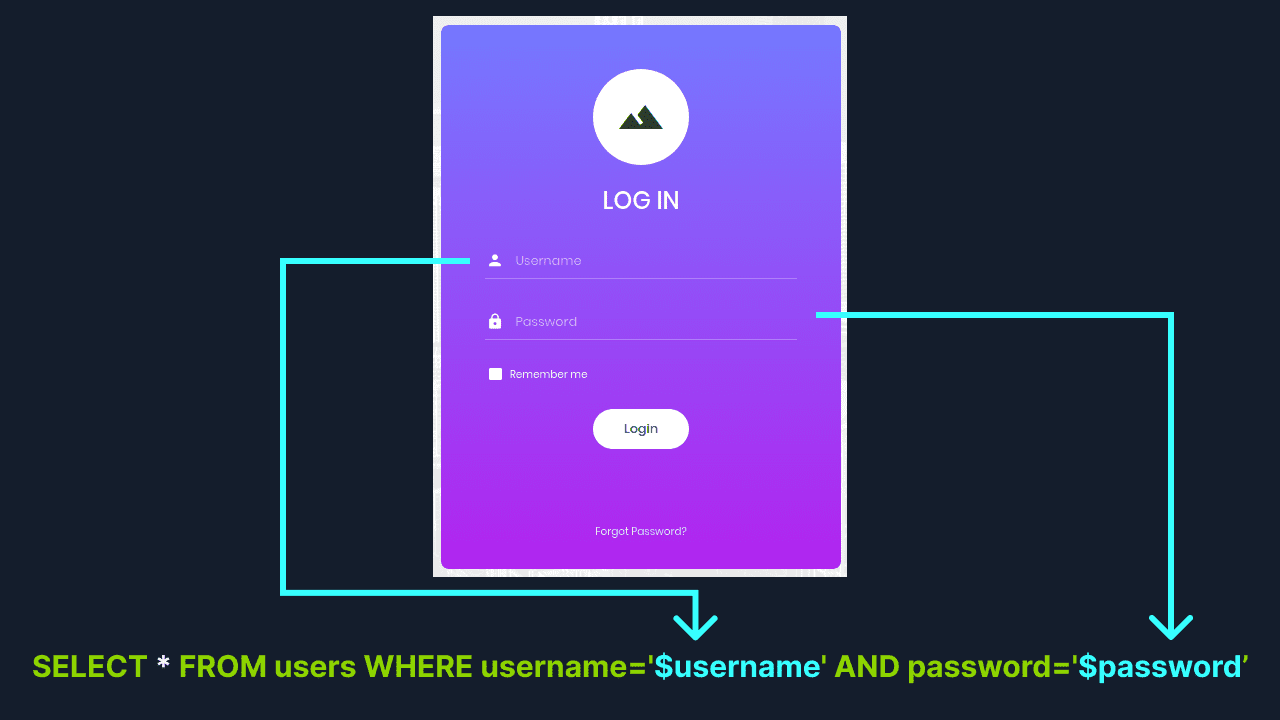
$username will be replaced by whatever we type in the username field of the form and similarly for $password
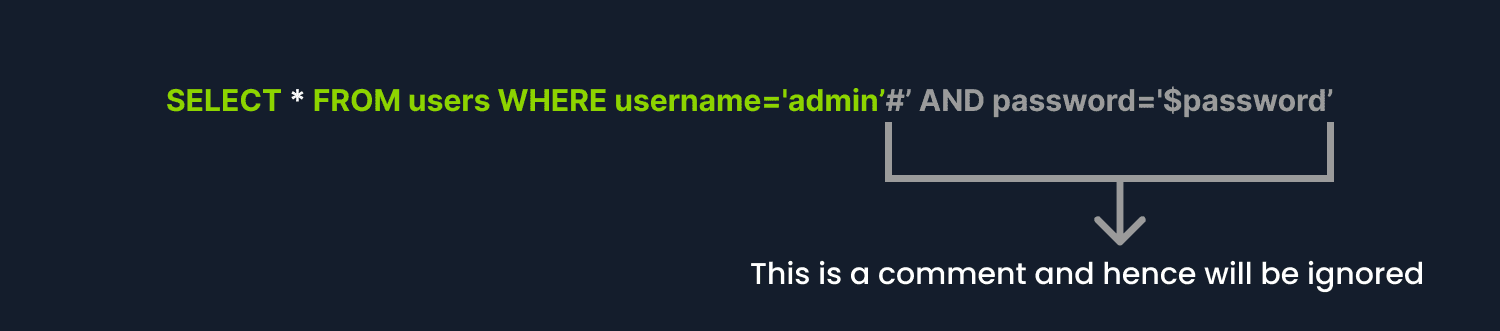
In PHP, we use #to comment lines of code.
With this much knowledge we can try to do SQL injection in the login form provided to us.
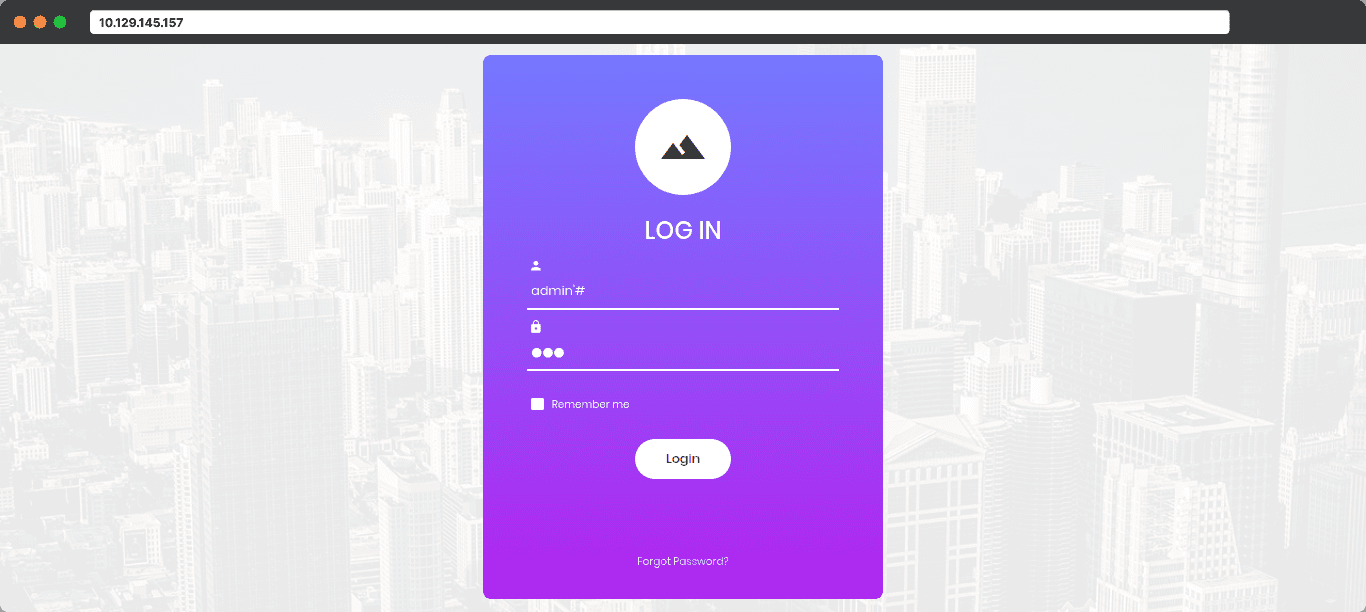
In the username field, we can type admin'# . This line will go inside the code, and it will put the username as admin and because of # the rest of the line is commented, so the code only checks for the usernames with admin and ignores the password validation. So, we can put any value in password field and login.
After filling the form and clicking on the login button, this is how the SQL query will look like 👇
After submitting the form, we get a page like:
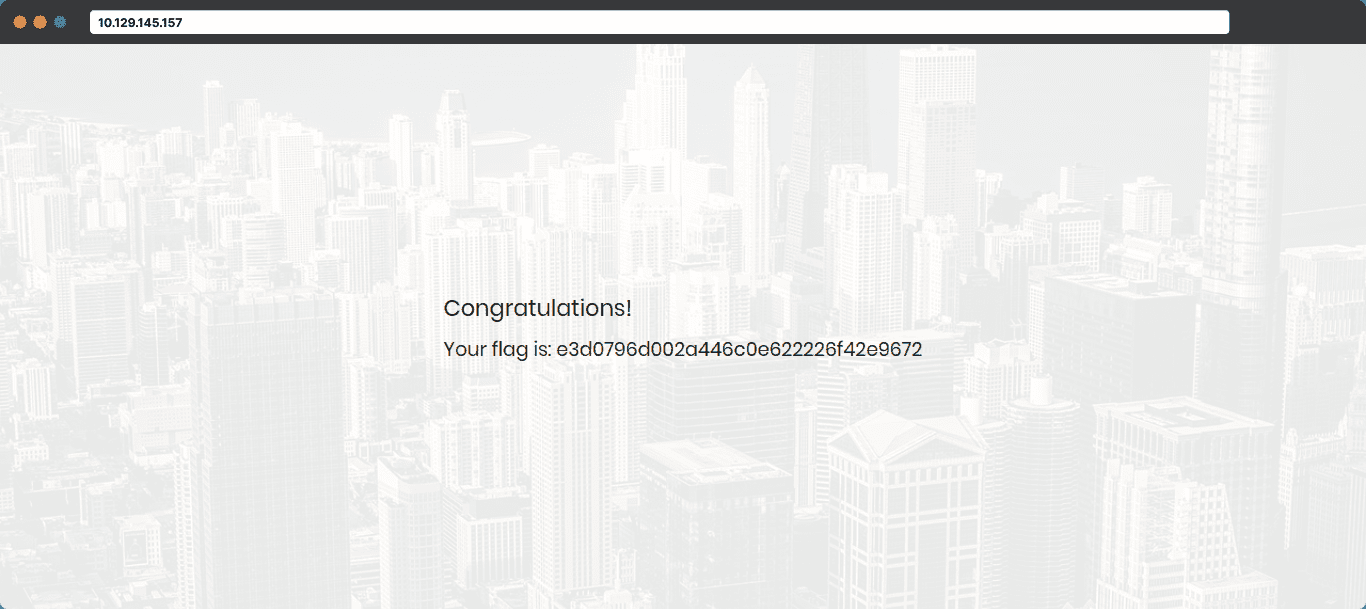
This shows that the login form on the website was vulnerable to SQL injection, and we have successfully exploited it.
Copy the flag value and paste it into the Starting Point lab’s page to complete your task.
Congrats, you have just pwned Appointment! 👏
—
Task answers
Task 1: What does the acronym SQL stand for?
Structured Query Language
Task 2: What is one of the most common type of SQL vulnerabilities?
SQL injection
Task 3: What does PII stand for?
Personally Identifiable Information
Task 4: What does the OWASP Top 10 list name the classification for this vulnerability?
A03:2021-Injection
Task 5: What service and version are running on port 80 of the target?
Apache httpd 2.4.38 ((Debian))
Task 6: What is the standard port used for the HTTPS protocol?
443
Task 7: What is one luck-based method of exploiting login pages?
brute-forcing
Task 8: What is a folder called in web-application terminology?
directory
Task 9: What response code is given for “Not Found” errors?
404
Task 10: What switch do we use with Gobuster to specify we’re looking to discover directories, and not subdomains?
dir
Task 11: What symbol do we use to comment out parts of the code?
#
🚩 Root flag:
e3d0796d002a446c0e622226f42e9672
This HackTheBox Meow walkthrough should have gotten your feet wet learning the basics, but I’m sure at some point you’ll be asking yourself, is this it? Well you’re not alone, this one was too easy! After the first few boxes, you might wanna try something harder and really challenge yourself. There are hundreds of challenges to choose from, that’s why HackTheBox is so amazing. Don’t feel bad if you get stuck, and don’t be afraid to use walkthroughs like this one to keep you from getting too frustrated, it’s really the best way to learn anyways. If you’re looking for a good challenge, testing out your Linux, nmap & SQL injection skills try this HackTheBox Faculty Writeup at GuidedHacking.