1. Implementing SSL/TLS Security
Securing data transmission between clients and servers is crucial, particularly when handling sensitive information. HTTPS implementation helps prevent various security breaches including MITM attacks and packet sniffing.
To implement TLS/SSL in Express 4.x:
First, generate SSL certificates:
openssl req -x509 -newkey rsa:2048 -keyout key.pem -out cert.pem -days 365
Then configure Express with HTTPS:
const fs = require('fs');
const https = require('https');
const express = require('express');
const NODE_ENV = process.env.NODE_ENV || 'development';
const PORT = process.env.PORT || 3443;
const app = express();
https.createServer({
key: fs.readFileSync('/path/to/key.pem'),
cert: fs.readFileSync('/path/to/cert.pem')
}, app).listen(PORT);
// Production HTTP to HTTPS redirect
if (NODE_ENV === 'production') {
app.use((req, res, next) => {
if (req.header('x-forwarded-proto') !== 'https') {
res.redirect(`https://${req.header('host')}${req.url}`);
} else {
next();
}
});
}
2. Essential Security Headers
Modern web applications require several critical security headers:
Strict-Transport-Security (HSTS): Forces browsers to use HTTPS connections exclusively. Example from major platforms:
Strict-Transport-Security: max-age=15552000
X-Frame-Options: Prevents clickjacking by controlling page embedding:
X-Frame-Options: DENY
X-Frame-Options: SAMEORIGIN
X-Frame-Options: ALLOW-FROM https://trusted-site.com
X-XSS-Protection: Activates browser’s built-in XSS prevention:
X-XSS-Protection: 1
X-Content-Type-Options: Prevents MIME type sniffing:
X-Content-Type-Options: nosniff
Content-Security-Policy: Defends against injection attacks, particularly XSS.
Implement these headers easily using the Helmet package:
const express = require('express');
const helmet = require('helmet');
const app = express();
app.use(helmet());
// Or configure individually:
app.use(helmet({
frameguard: {
action: 'deny'
}
}));
For Nginx users, add to nginx.conf:
add_header X-Frame-Options DENY;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection 1;
add_header Content-Security-Policy "default-src 'self'";
3. CSRF Protection Implementation
Protect against CSRF attacks using the csurf middleware:
const cookieParser = require('cookie-parser');
const csrf = require('csurf');
const bodyParser = require('body-parser');
const express = require('express');
const csrfProtection = csrf({ cookie: true });
const parseForm = bodyParser.urlencoded({ extended: false });
const app = express();
app.use(cookieParser());
app.get('/form', csrfProtection, (req, res) => {
res.render('send', { csrfToken: req.csrfToken() });
});
4. XSS Attack Prevention
Implement input sanitization using xss-filters:
const express = require('express');
const app = express();
const xssFilters = require('xss-filters');
app.get('/', (req, res) => {
let firstname = req.query.firstname;
res.send('<h1>Hello, ' + xssFilters.inHTMLData(firstname) + '!</h1>');
});
app.listen(3000);
Encode the minimal set of characters to thwart JavaScript executions, thus preventing XSS attacks while keeping most characters intact. Compared to the traditional blindly escape filter.
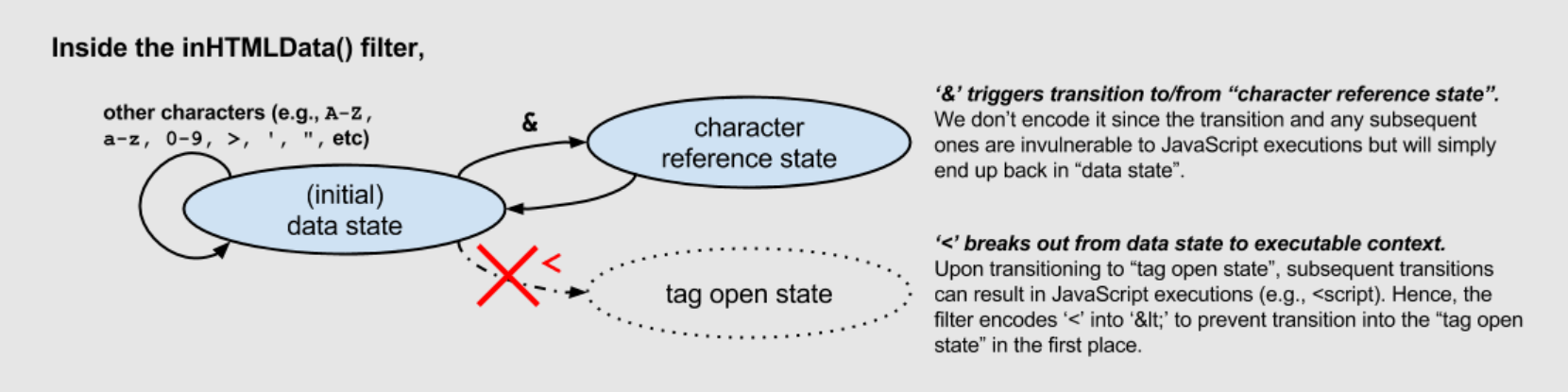
5. Secure Cookie Configuration
Protect cookies from theft and manipulation:
app.use(session({
secret: 'Your-Secret-Key',
cookie: {
httpOnly: true, // Prevents JavaScript access
secure: true // Requires HTTPS
}
}));
secure : this attribute tells the browser to only send the cookie if the request is being sent over HTTPS.
HttpOnly : this attribute is used to help prevent attacks such as cross-site scripting, since it does not allow the cookie to be accessed via JavaScript.
6. Rate Limiting and DoS Prevention
Implement rate limiting to prevent brute force attacks:
const RateLimit = require('express-rate-limit');
const limiter = new RateLimit({
windowMs: 15 * 60 * 1000, // 15 minute window
max: 100, // 100 requests per window
delayMs: 0 // No artificial delay
});
app.use(limiter);
Additional DoS prevention strategies:
- Use a reverse proxy to receive and forward requests to the Node.js application. Reverse proxies can provide caching, load balancing, IP blacklisting, etc. which reduce the probability of a DoS attack being effective.
- Correctly configure the server timeouts, so that connections that are idle or where requests are arriving too slowly can be dropped. See the different timeouts in
http.Server, particularly headersTimeout, requestTimeout, timeout, and keepAliveTimeout.
- Limit the number of open sockets per host and in total. See the http docs, particularly
agent.maxSockets, agent.maxTotalSockets, agent.maxFreeSockets and server.maxRequestsPerSocket.
7. Security Scanning Tools
Essential security tools for Node.js applications:
Node Security Project (nsp)
nsp check
Synk
npm install -g snyk
cd your-app
snyk test
Security Tools
- nmap: Network exploration and security auditing
- sqlmap: SQL injection detection and exploitation
- Burp Suite: Comprehensive web application security testing