
In today’s rapidly evolving digital world, cyber threats are becoming more sophisticated by the day. Traditional security systems that rely on static rules often fall short when dealing with dynamic and unpredictable attacks. This is where User and Entity Behavior Analytics (UEBA) steps in, offering a smarter, behavior-based approach to detecting security threats. Think of it as having a vigilant security guard in your organization, continuously analyzing activities to spot anything unusual before it’s too late.
In this blog, we’ll dive into the fundamentals of UEBA, its components, real-world applications, and the benefits and challenges of implementing it. Plus, we’ll explore practical insights to help you better understand how this cutting-edge technology can fortify your cybersecurity strategy.
What Is UEBA?
At its core, UEBA leverages machine learning (ML) and behavioral analytics to establish a baseline for normal behavior across users and entities in an organization. It then monitors for deviations from this baseline, flagging anything out of the ordinary that could indicate a security threat.
Let’s simplify it further: Imagine you work with a colleague who logs into the system at 9 AM daily and accesses specific files. One day, their account logs in at 3 AM from another country and downloads a massive amount of sensitive data. UEBA recognizes this as an anomaly and raises an alert. Unlike traditional security measures that might miss such subtle clues, UEBA focuses on behavior patterns, making it an indispensable tool for modern enterprises.
The Evolution of Cybersecurity: Why UEBA Matters
Cybersecurity has come a long way from basic firewalls and antivirus software. While these tools still play a role, they primarily focus on known threats and rule-based detection. However, modern attackers have become adept at bypassing these systems through tactics like credential theft, insider threats, and malware-free attacks.
This is where UEBA shines. By analyzing behavior rather than relying on predefined rules, it can detect threats that traditional tools might overlook. It’s especially effective against:
Insider Threats: Malicious or accidental actions by employees that compromise security.
Credential Theft: When attackers use stolen login credentials to access sensitive systems.
Automated Attacks: Abnormal behavior from bots, compromised devices, or servers.
How UEBA Works: The Key Components
UEBA combines several components and processes to provide a comprehensive security framework. Let’s break it down:
- Data Collection
To establish a behavioral baseline, UEBA relies on data from various sources, such as:
System logs
Network traffic
Application usage patterns
User activity logs
The more data UEBA has, the better it can understand normal behavior and identify anomalies.
- Analytics Engines and Machine Learning
Once data is collected, UEBA uses machine learning algorithms to analyze it. These algorithms establish a baseline for what constitutes “normal” behavior in your organization. They can adapt over time, learning new patterns as the organization evolves.
- Continuous Monitoring
UEBA continuously monitors your network, comparing real-time activities against the baseline. If it detects deviations—like unusual login times, excessive file downloads, or access from unexpected locations—it flags them for further investigation.
- Alerting and Response
When an anomaly is detected, UEBA sends an alert to your security team. From there, security experts validate the alert and take appropriate actions, such as:
Changing user permissions
Isolating compromised devices
Investigating the root cause of the anomaly
Real-World Applications of UEBA
UEBA isn’t just a theoretical concept; it’s actively used by organizations to address real-world challenges. Here are a few practical applications:
- Insider Threat Detection
Insider threats—whether malicious or accidental—are among the hardest to detect. UEBA analyzes behavioral patterns to spot unusual activities, like an employee accessing sensitive files they’ve never touched before.
- Credential Theft Prevention
If an attacker steals an employee’s login credentials, UEBA can detect unusual activity, such as logins from unexpected locations or devices, and trigger an alert.
- Network Security
UEBA monitors how users and entities interact with network resources. If a server suddenly starts communicating with unfamiliar devices, UEBA flags it as a potential threat.
- Cloud Security
In an era of remote work and cloud-based systems, UEBA helps secure cloud environments by monitoring user and entity behavior in real-time.
Benefits of UEBA
UEBA offers several advantages that make it an essential component of modern cybersecurity strategies:
Proactive Threat Detection: Unlike traditional tools that react to known threats, UEBA identifies anomalies in real time, allowing you to address issues before they escalate.
Regulatory Compliance: By maintaining detailed logs and conducting regular behavioral analysis, UEBA helps organizations meet compliance requirements like GDPR, HIPAA, and PCI-DSS.
Reduced Human Error: Automation and AI minimize the risk of overlooking critical threats, ensuring a more robust security posture.
Challenges of Implementing UEBA
While UEBA is a powerful tool, it’s not without its challenges:
False Positives: Sometimes, normal activities may be flagged as suspicious, leading to wasted time and resources.
Implementation Complexity: Setting up UEBA requires expertise in machine learning and behavioral analytics, which may be daunting for smaller organizations.
Data Privacy Concerns: Extensive data collection can raise privacy issues, making it crucial to balance security and ethical considerations.
Real-World Case Study: Stopping a Data Breach
Let’s consider a real-life scenario. A financial services company implemented UEBA to monitor employee behavior. One night, UEBA flagged unusual activity: an employee’s account was used to download large amounts of sensitive client data from an unfamiliar IP address. Upon investigation, the security team discovered the account had been compromised. Thanks to UEBA, the breach was stopped before any data was leaked.
Future of UEBA: AI-Powered Defense
As cyber threats continue to evolve, so does the technology used to combat them. The future of UEBA lies in its integration with advanced AI and predictive analytics. Emerging trends include:
Integration with Zero Trust Models: UEBA complements Zero Trust by continuously validating user and entity behavior.
Edge Computing: With data processing closer to the source, UEBA systems can deliver faster threat detection.
Predictive Analytics: Beyond detecting anomalies, future UEBA systems will predict potential threats based on historical data.
Practical Steps to Implement UEBA
If you’re considering UEBA for your organization, here’s a step-by-step guide:
Identify Data Sources: Gather data from system logs, network traffic, and user activities.
Choose the Right Tools: Select a UEBA platform that aligns with your organization’s needs.
Train Your Team: Ensure your security team understands how to interpret UEBA alerts.
Monitor and Refine: Continuously update your UEBA system to adapt to new threats and organizational changes.
Closing Thoughts
UEBA isn’t just another buzzword in the cybersecurity world. It’s a vital tool for detecting and mitigating modern threats. By focusing on behavior rather than predefined rules, UEBA provides a proactive and adaptive approach to security. Whether you’re safeguarding sensitive data, meeting compliance standards, or staying ahead of sophisticated attackers, UEBA has you covered.
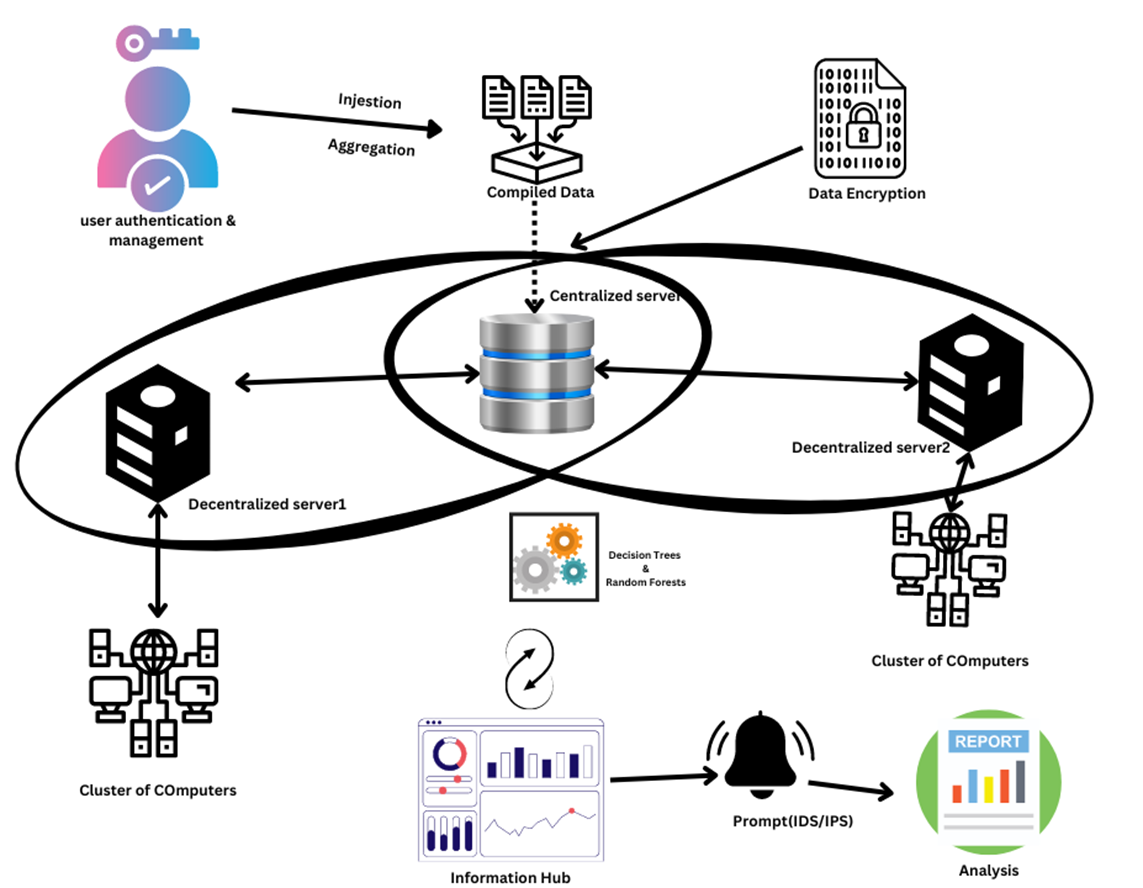
Understanding the UEBA Framework Through the Diagram
To truly appreciate the power of User and Entity Behavior Analytics (UEBA), it’s essential to understand the ecosystem behind it. The diagram above provides a glimpse into a centralized-decentralized hybrid system that enables organizations to collect, analyze, and respond to anomalies in real time. Let’s break it down step by step.
1. User Authentication & Management: The Frontline Defense
Every robust cybersecurity framework starts with securing the doors—and that’s exactly what user authentication does. This component ensures that only authorized users can access the system. Think of it as your organization’s security checkpoint, verifying identities before they step inside.
But it doesn’t stop there. Once a user is authenticated, their activities are tracked and aggregated, forming a data trail that feeds into the rest of the system. This step creates the foundation for UEBA’s behavior-based analysis.
2. Data Compilation and Encryption: Guarding the Data
Once user activities are authenticated, the next step is compiling and encrypting this data. Data compilation involves gathering information from various sources, such as user actions, network traffic, and system logs.
Data encryption ensures that sensitive information remains secure, both during transit and storage. This is particularly crucial in preventing unauthorized access or data breaches. With UEBA, this encrypted data is analyzed to establish what constitutes “normal” behavior, paving the way for detecting anomalies.
3. The Centralized Server: The Brain of the System
The centralized server is the system’s brain, responsible for unifying data from all sources. It acts as the main hub where all the compiled data flows in for processing and analysis.
Why is this central node important? Because it provides a big-picture view of your organization’s behavior. By connecting to decentralized servers, it ensures that no unusual activity slips through the cracks, regardless of where it originates.
4. Decentralized Servers: Local Guardians
Imagine your organization as a bustling city with multiple neighborhoods. Each neighborhood (or department) has its own security team—these are your decentralized servers.
Decentralized servers work alongside clusters of computers, collecting localized data and feeding it back to the centralized server. This hybrid approach combines the scalability of decentralized systems with the efficiency of centralized analysis. It’s like having security teams stationed in every corner, while still reporting back to the central headquarters.
5. Clusters of Computers: Where the Action Happens
Clusters of computers represent the endpoints—where users and devices interact with the system. This is where the raw data originates: logins, file access, unusual requests, and more.
The decentralized servers monitor these activities, ensuring that every piece of data is captured and analyzed. For example, if a server in a specific cluster suddenly starts communicating with an unknown device, this abnormal activity is flagged for further inspection.
6. Machine Learning: Turning Data into Insights
Here’s where the real magic happens. Once the data flows through the servers, machine learning algorithms—like decision trees and random forests—come into play.
- Decision Trees: Think of these as “if-then” decision-makers. They classify behavior into categories like normal or suspicious.
- Random Forests: These are more advanced, combining multiple decision trees to make better predictions.
By using these algorithms, the system builds a baseline of normal behavior and identifies deviations that could signal threats, such as insider attacks or credential theft.
7. Real-Time Alerts: The System’s Siren
When an anomaly is detected, the system doesn’t sit quietly—it raises an alert. This is where Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) come into play.
For example, if the system notices unusual login times or massive file downloads from an unexpected location, it immediately notifies the security team. These alerts are actionable, enabling quick responses like:
- Locking the suspicious account
- Isolating a compromised device
- Launching an in-depth investigation
—
8. The Information Hub: Visualizing Insights
The information hub is where all the action gets visualized. It’s essentially a dashboard for your security team, displaying critical insights through graphs, trends, and reports.
This interface makes it easier to track anomalies and respond effectively. Think of it as your organization’s mission control, offering a real-time overview of what’s happening across the network.
9. Analysis and Reporting: Closing the Loop
Finally, the system consolidates its findings into detailed reports. These reports are invaluable for understanding incidents, improving threat models, and meeting compliance standards like GDPR or HIPAA.
By analyzing these reports, organizations can refine their UEBA systems, ensuring they stay ahead of evolving threats. It’s a continuous feedback loop that strengthens your cybersecurity posture over time.
Connecting It All Back to UEBA
The diagram perfectly illustrates the essence of UEBA—a layered system that collects data, analyzes it with advanced algorithms, and responds to threats in real time. Here’s how it aligns with the key principles of UEBA:
- Proactive Threat Detection: The system identifies anomalies before they escalate.
- Scalability: With decentralized servers and clusters, it adapts to organizations of any size.
- Behavior-Based Monitoring: By focusing on behavior rather than static rules, it detects threats traditional systems often miss.
In short, the framework combines technology, intelligence, and automation to deliver a powerful, future-ready cybersecurity strategy.
Final Thoughts
Understanding UEBA through this diagram provides a deeper appreciation of its potential. It’s not just a tool; it’s a comprehensive strategy for staying ahead of modern cyber threats. Whether you’re dealing with insider threats, credential theft, or abnormal network behavior, UEBA ensures you’re always one step ahead.
This hybrid approach of centralized and decentralized systems, powered by machine learning, is the key to building a resilient defense. So, the next time you think about fortifying your cybersecurity strategy, remember: UEBA isn’t just about detecting threats—it’s about preventing them before they even happen.