
Welcome back to our CTF Forensics series! In this second installment, we continue our deep dive into network forensics using Wireshark. If you’ve ever struggled with analyzing packet captures in CTF challenges, this guide will help you master essential techniques, from filtering traffic to extracting hidden data. Let’s sharpen our skills and uncover those elusive flags together!
Understanding PCAP Files
Most CTF challenges involving Wireshark provide a .pcap (packet capture) file, which contains recorded network traffic. Your task is to analyze this file and extract valuable information such as credentials, hidden messages, or files transferred over the network.
Common Wireshark Techniques for CTF
Following TCP and UDP Streams
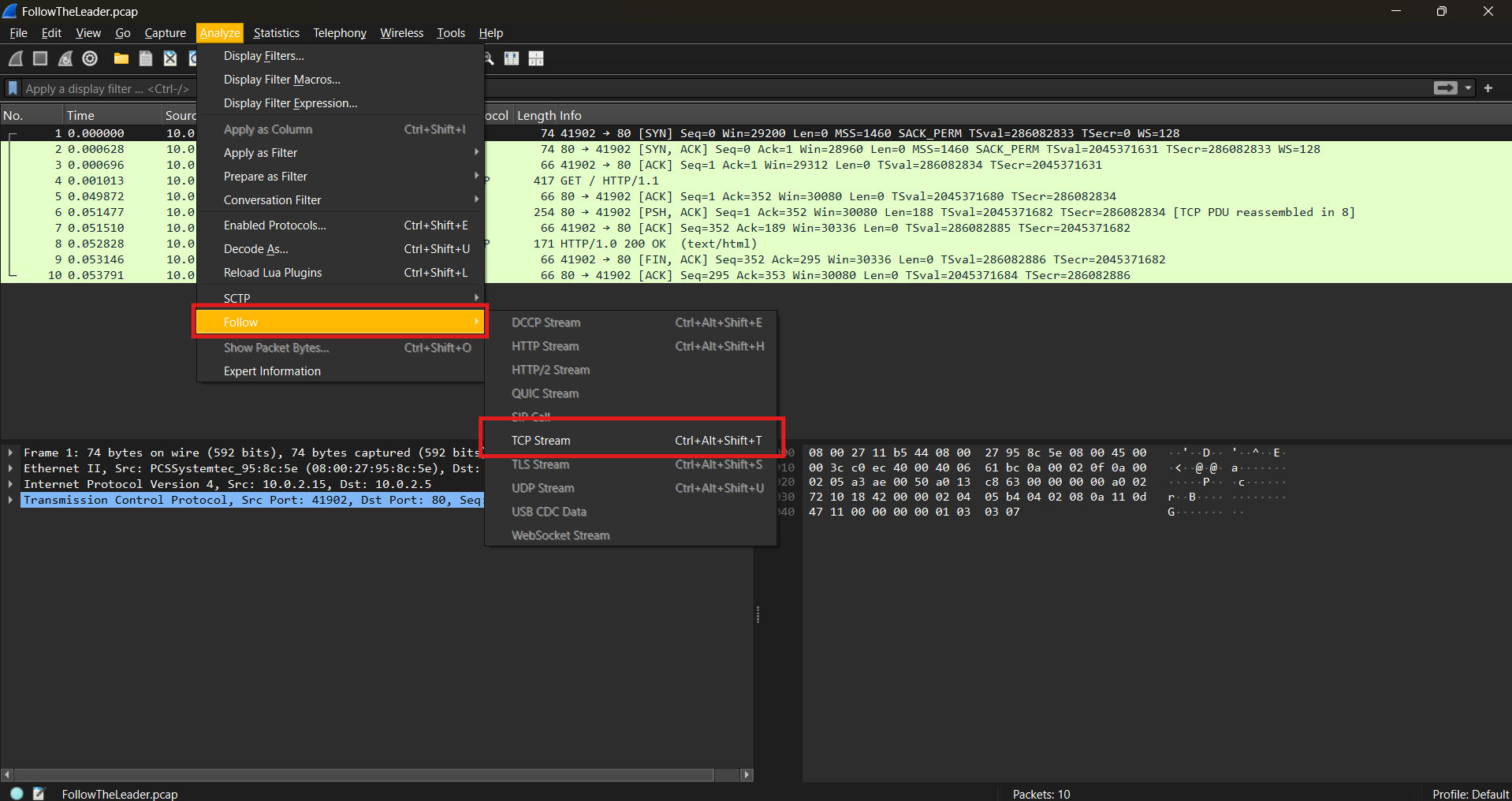
Reconstructing conversations between two parties is crucial in CTF challenges. To view the complete exchange of messages:
Right-click on a packet > Click "Follow" > Select "TCP Stream" or "UDP Stream"
- This allows you to see plaintext communication, credentials, and other useful information.
Extracting Files from PCAP
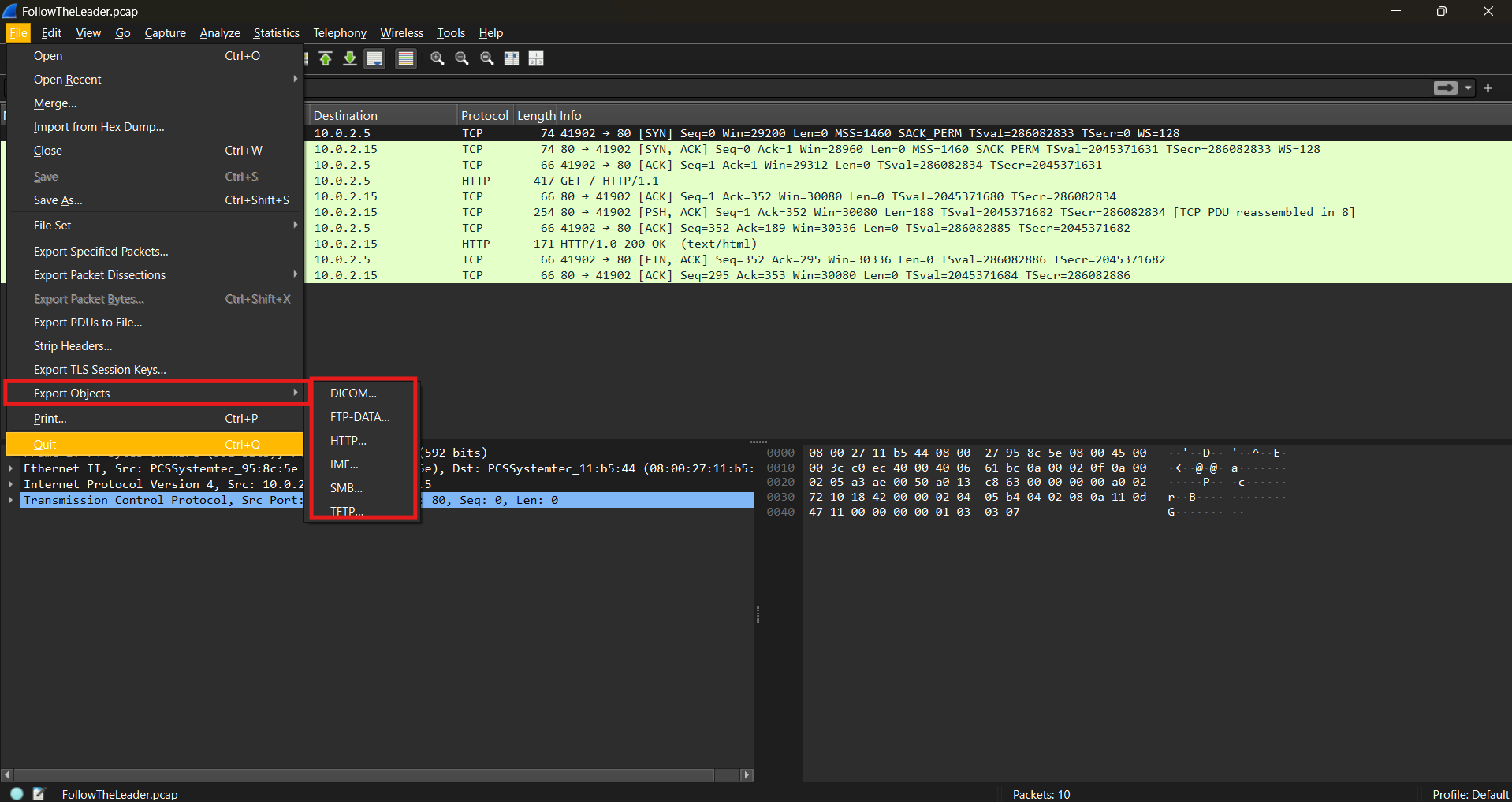
Sometimes, the challenge involves reconstructing transferred files. Wireshark can extract files from network traffic:
**File** > **Export Objects** > Select the protocol
Checking for Hidden Data in Protocols
Steganography techniques can hide data inside protocols like ICMP, DNS, or HTTP headers.
- Look for anomalies in packet payloads using
hex view.
- Use
tshark or scripts to extract and decode hidden messages.
Decrypting WPA or WEP Traffic
Filter the protocol:
eapol
If you plan to crack a WPA/WPA2 network, look for the 4-way handshake. This handshake occurs when a client connects to an access point. You can filter for EAPOL (Extensible Authentication Protocol over LAN) packets in Wireshark using the filter.
Wifi Cracking Tool
Use aircrack-ng to attempt cracking the WPA/WPA2 handshake:
aircrack-ng -w [wordlist.txt] -b [BSSID] [handshake.pcap]
Protocol Hierarchy in Wireshark
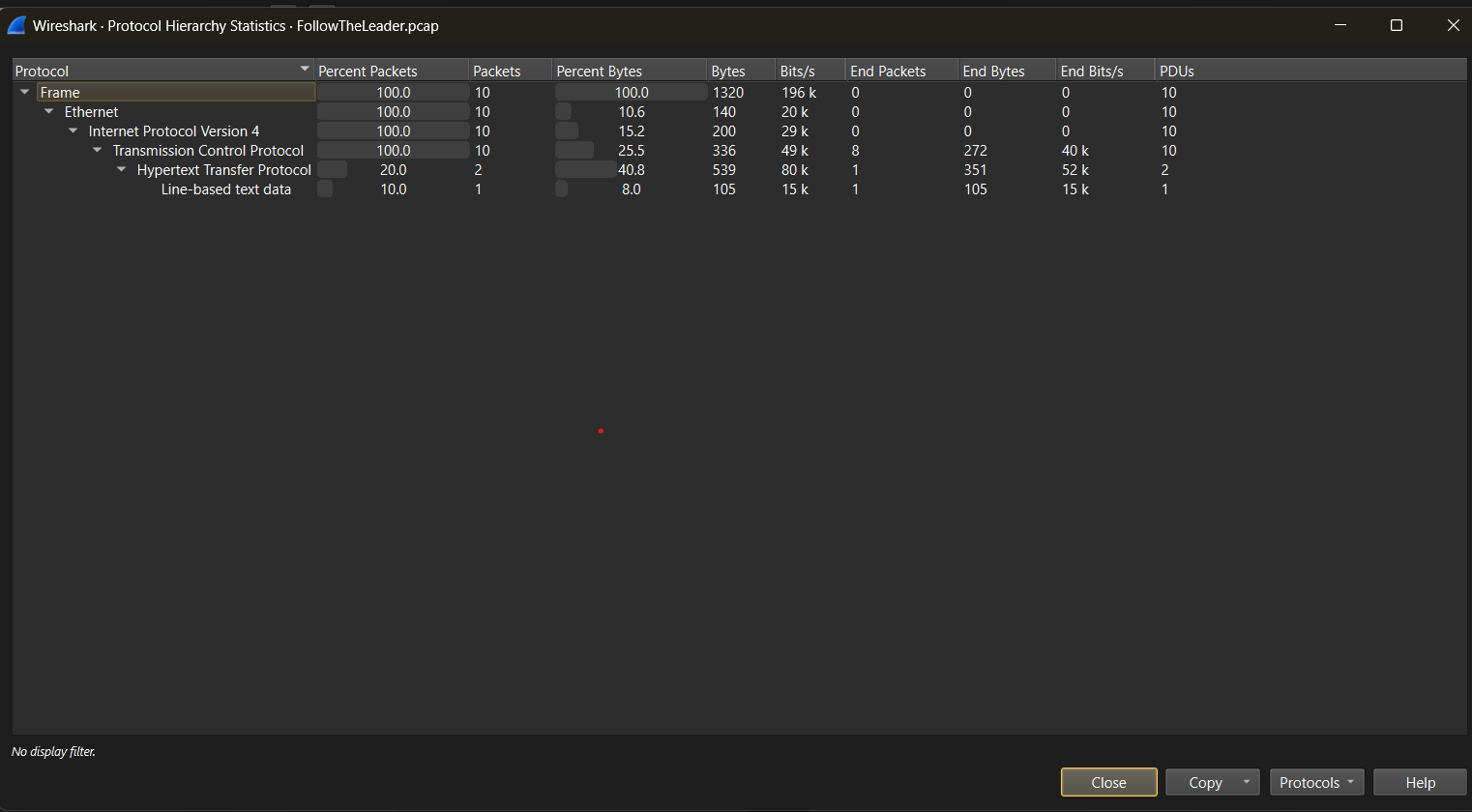
Wireshark’s Protocol Hierarchy feature provides a structured breakdown of all protocols present in a packet capture file, helping analysts understand the composition of network traffic. This tool categorizes traffic into different protocol layers, such as Ethernet, IP, TCP, HTTP, and more, making it easier to detect anomalies, filter relevant data, and identify suspicious activity. In CTF challenges, this feature is useful for quickly spotting uncommon or hidden protocols that might contain valuable clues or even the flag itself. By analyzing protocol distribution, you can determine whether a capture contains encrypted traffic, tunneling, or unexpected services.
Statstic > Protocol Hierarchy
Key Points on Protocol Hierarchy
- Provides a percentage breakdown of network protocols used in a capture.
- Helps in detecting unusual or hidden protocols used for covert communication.
- Assists in refining filtering techniques for faster packet analysis.
- Useful for spotting encrypted traffic, tunneling, or rare services.
NetworkMiner
NetworkMiner is a powerful network forensic analysis tool (NFAT) designed to extract useful artifacts from packet capture (PCAP) files. Unlike Wireshark, which focuses on packet-level analysis, NetworkMiner simplifies forensic investigations by automatically extracting files, images, credentials, and other useful metadata from captured traffic. This makes it a valuable tool for CTF challenges, especially when dealing with network-based challenges that involve reconstructing communication or retrieving transferred files.
- File Extraction– Extracts transferred files (images, docs, executables) from PCAPs.
- Credential Recovery– Automatically finds usernames and passwords from plaintext protocols (HTTP, FTP, Telnet).
- Host Analysis– Identifies IP addresses, MAC addresses, and communication details.
- Image & Data Recovery– Recovers images and possible steganographic content.
- DNS Analysis– Reveals queried domains, useful for tracking exfiltration or hidden messages.
- Passive Forensics– Works without actively interacting with the traffic.
- Quick Artifact Discovery– Saves time by categorizing extracted data into easy-to-navigate tabs.
Installation for Windows and Linux
Windows
Download Link - https://www.netresec.com/?page=NetworkMiner
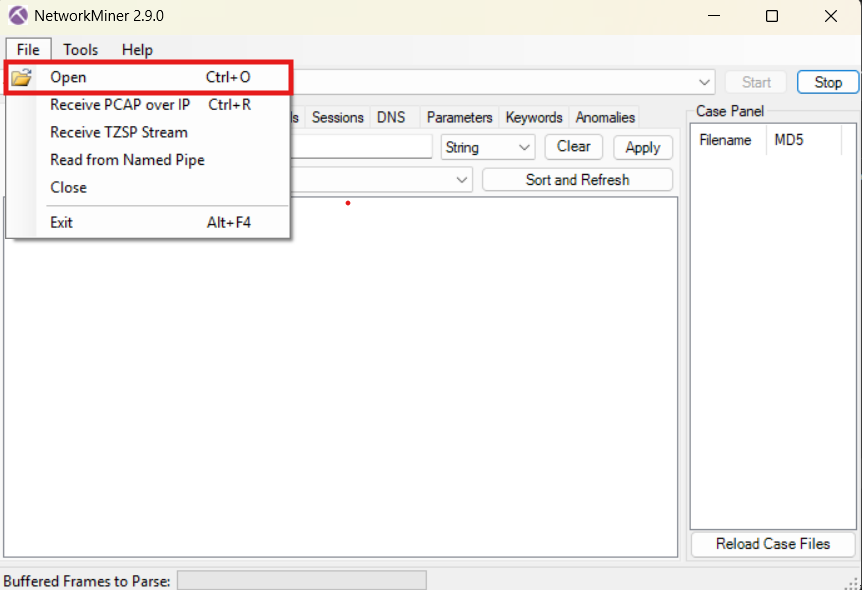
From the above download link u can download and unzip the file .
Its Portable version .
Linux
Same download link can be used to download here . Here the .exe file will be used with mono for installation .
sudo apt update && sudo apt install mono-complete -y
- Now Download NetworkMiner from the link -Network Miner
- Extract the Files and move the folder to
/opt/
unzip <file name> -mv /opt/
cd /opt/NetworkMiner
- Make the executable permission for the
NetworkMiner.exe file
sudo chmod +x NetworkMiner.exe
- Now run the file using
mono
mono /opt/NetworkMiner_1-2/NetworkMiner.exe
Check Out the old blog on Steganography
Stay tuned for next Part !!!…