Description :
We are going to learn about network mapping with Nmap from beginner to advance in multiple articles. Today we are going to cover Basic Scanning and understand how it actually Nmap works behind the scenes.

Before you start, You can join our discord server to engage with like minded people and share everything that you can share with people to help them and get your queries answered by people.
Understanding the basics
Hand Shaking
Before starting with Nmap and scanning it is important to know how really a network works in real. When we visit any website or access any service on the internet our browser goes to the website and asks, “Can I connect with you ?” and if the website or service is available then it will say, “ Yes, please you can.” and then our browser will say, “Thank you.” and it will load the website. In technical terms, a “handshaking” process happens behind the scenes.
What is TCP Header?
A TCP header holds information about the connection and the current data being sent over a connection including Source port, destination port, flags, data, and many more. The important part here is flags are being set while scanning the hosts.
What is TCP Header?
A TCP header holds information about the connection and the current data being sent over a connection including Source port, destination port, flags, data, and many more. The important part here is flags are being set while scanning the hosts.
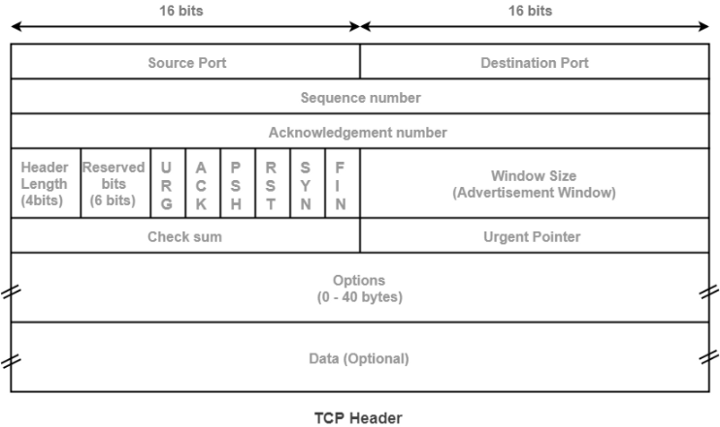
A handshaking process is done by setting the flags in the packet header. The response given by the service or host can be identified by flags set by them and by understanding that process one can understand the network scanning process very easy.
What is a port ?
A port is a logical or physical interface between computers or computer peripheral devices to communicate and connect for transferring information and data. There are 65,535 possible port numbers in a computer or computer peripheral devices.
Basic Scanning
Now we are aware of how a connection process and handshaking process work. Now we can go ahead and see how Nmap works behind the scenes.
1. TCP Connect Scan
A TCP connect scan is a connection-oriented scan that follows a 3-Way handshake process to determine whether the given port is open or not.
nmap -ST <ip>
-ST : TCP connect scan
When we use the above command, Nmap sends SYN (Synchronization) Packet to specified IP on several ports. If a port is open then it will respond with SYN/ACK (Synchronization/Acknowledgement) Packet that indicates the service or port is ready to connect and open. Then Nmap sends ACK Packet to acknowledge the connection.
If the port is not open then we will receive a response with RST (Reset) Packet instead of SYN/ACK Packet and that indicates the port is closed. This is how a TCP Connect Scan works. But this type of scan leaves a fingerprint on the target host.
2. TCP SYN (Stealth) Scan
A TCP SYN Scan does not follow the 3-Way handshake process. This decreases the chances of the scan being logged.
nmap -sS <ip>
-sS : TCP SYN stealth sca
When the above command is used, Nmap sends SYN (Synchronization) Packet to specified IP on several ports. If a port is open then it will respond with a SYN/ACK (Synchronization/Acknowledgement) Packet that indicates the service or port is ready to connect and open but instead of sending an ACK packet Nmap sends RST (Reset) flag and resets the connection. This is how a TCP SYN Scan works.
3. UDP Scan
Unlike TCP , UDP is a connectionless protocol. As being a connectionless protocol it does not follow handshaking while establishing a connection to a target.
nmap -sU <ip>
-sU : UDP scan
No guarantee that a service listening on UDP port would respond to our packets. If the packet received is ICMP Port Unreachable then the port is closed and if no response then we might consider it an open or filtered port.
This is it for today’s article. If you found it interesting and informative then share it with your friends. Thank you for reading till here. Let me know your query or topic on which you wanted to read an article in the response section.
You can follow on social media here: