
🐧Introduction to Network Scanning and Enumeration
⭕ Understanding the Importance of Network Scanning and Enumeration
Network scanning and enumeration are essential in hacking and cybersecurity because of the following reasons :
- They help identify potential vulnerabilities and assess the security posture of a network.
- Actively probing the network allows for the discovery of open ports, services, and configurations that may be susceptible to exploitation.
- The knowledge gained through scanning and enumeration enables patching or mitigation of vulnerabilities before they can be exploited by malicious actors.
- By mapping out the network, security professionals can better understand the network’s structure and identify potential points of entry.
- By prioritizing security measures based on the results of scanning and enumeration, organizations can effectively protect their assets and mitigate risks.'
⭕Differentiating Between Network Scanning and Enumeration
| Network Scanning | Network Enumeration |
|---|
| Purpose: Actively probing a network to identify live hosts, open ports, and running services. | Purpose: Extracting detailed information about network resources, such as user accounts, shared directories, and network protocols. |
| Focuses on Identifying vulnerabilities, availability, and configuration of the network. | Focuses on: Providing specific insights into the network’s internal components. |
| Techniques Used: Sending network packets, analyzing responses to identify open ports and services. | Techniques Used: Extracting information through techniques like LDAP queries, SNMP enumeration, and DNS enumeration. |
| Examples: Port scanning, service identification, and OS detection using tools like Nmap. | Examples: Enumerating user accounts, identifying network shares, and extracting information using tools like enum4linux and smbclient. |
| Importance: Helps in identifying potential vulnerabilities and strengthening network security measures. | Importance: Assists in discovering critical network components and enhancing overall network understanding. |
🐧Passive Network Reconnaissance
Network passive reconnaissance refers to the process of gathering information about a target network without directly interacting with it or causing any noticeable activity that could trigger security alerts.
🐾 1. Passive Network Monitoring:
Passive network monitoring is a technique used in passive network reconnaissance to capture and analyze network traffic without actively engaging with the target network.
Linux provides several powerful tools for passive network monitoring.
1. Tcpdump
Tcpdump is a command-line packet analyzer that captures and analyzes network traffic. It works by listening to network interfaces or reading packet capture (PCAP) files.
Installation
sudo apt-get install tcpdump
Switches
i : Specifies the network interface to capture packets from. Example :
sudo tcpdump -i eth1
-D : To list all the available interfaces
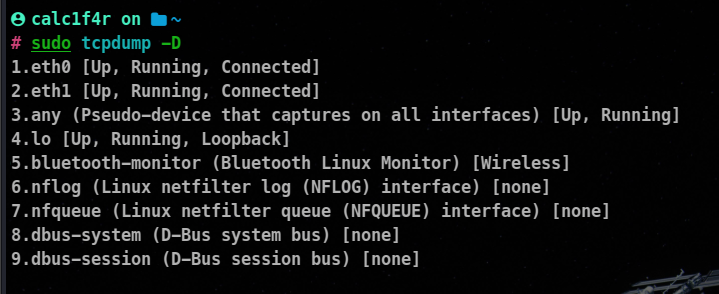
-n : Displays IP addresses instead of resolving them to hostnames. This can help in reducing the output latency. Be default Tcpdump resolves the names to undo that option we do this !
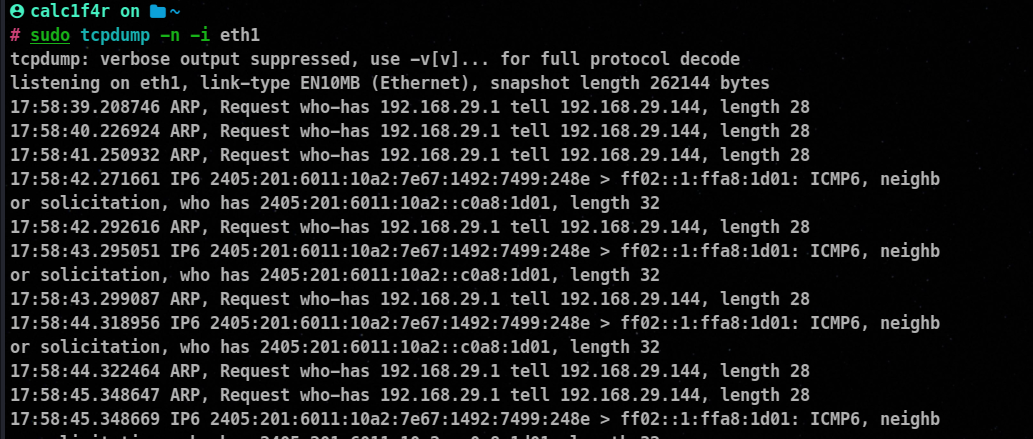
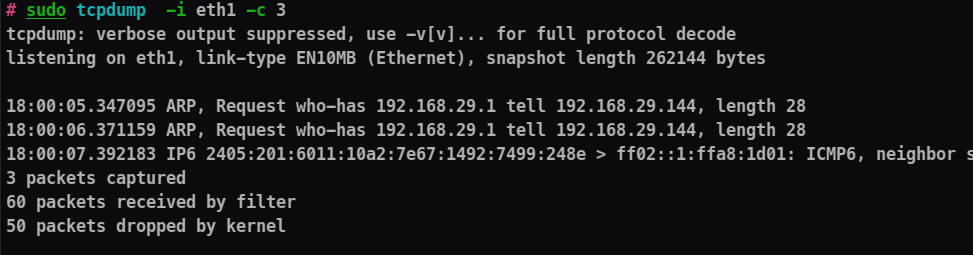
-c : Specifies the number of packets to capture before tcpdump exits.
-s : Sets the snapshot length of each captured packet. It defines the maximum number of bytes to capture for each packet.
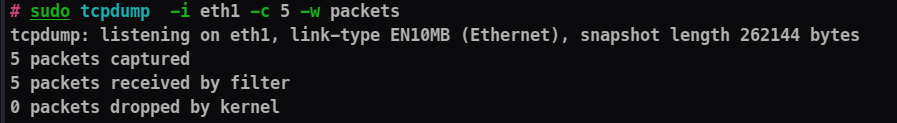
-w : Writes the captured packets to a file rather than displaying them on the console. For example, -w capture.pcap writes the packets to a file named “capture.pcap”.
-r : Reads Packets from a saved file rather than capturing them alive.
-A : Displays the packet contents in ASCII format, making it easier to read application later protocols such as HTTP
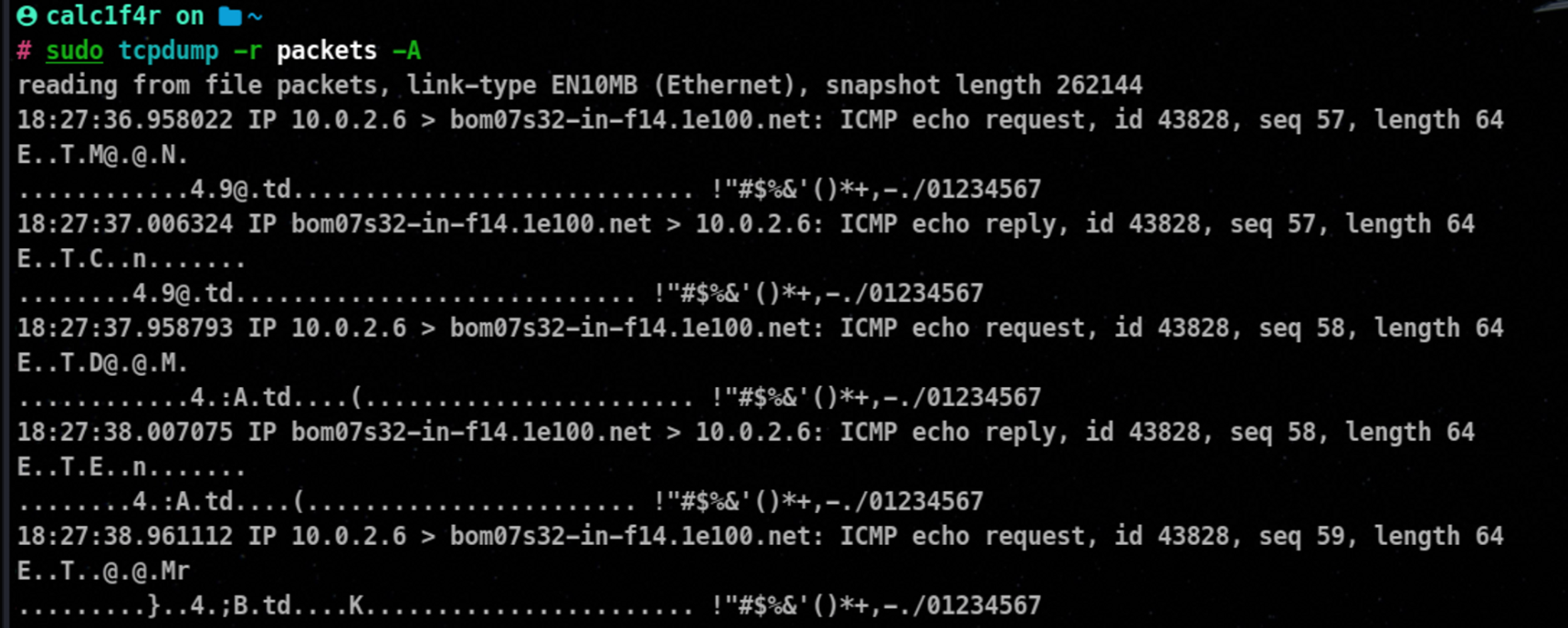
-v : Increase Verbosity, providing more detailed output.
-x : Displays the packet contents in both hex and ascii format
-F : Specifies a BPF filter to capture only specific types of packets to filter, manipulate. Example : -F "tcp port 80".
Packet Filtering
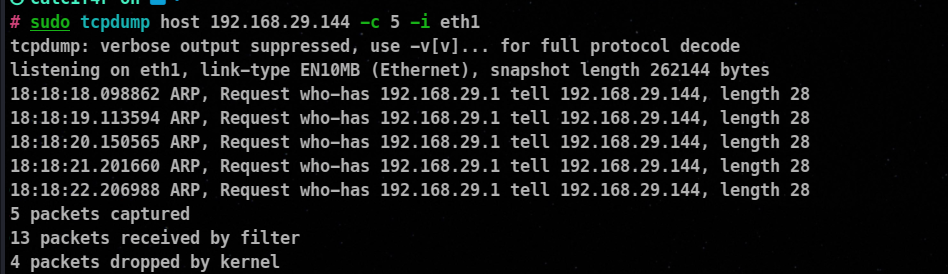
Filtering based on Host
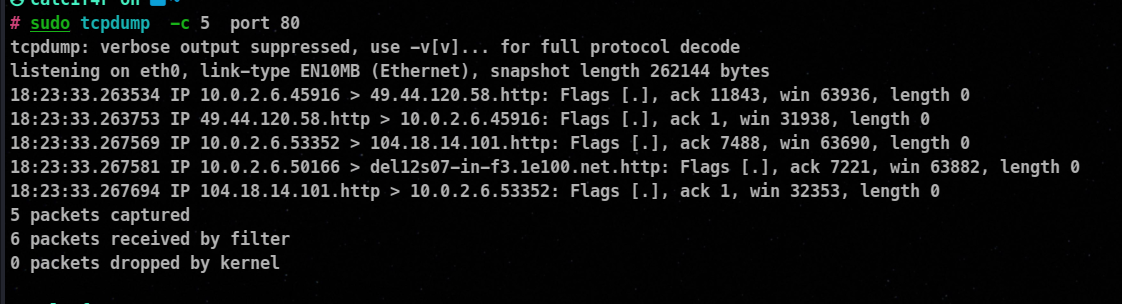
Filtering based on port
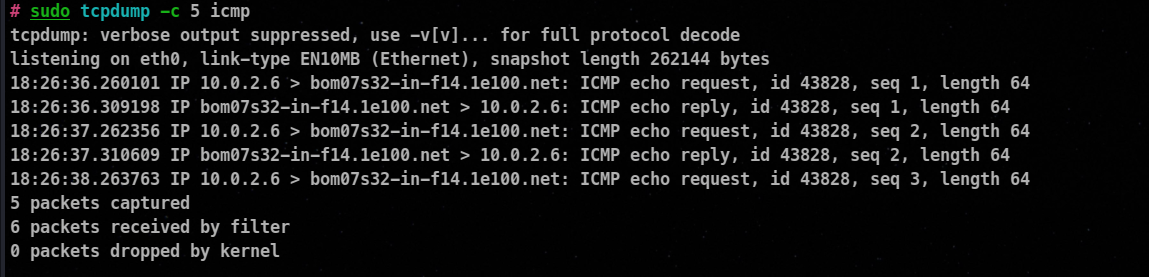
Filtering based on protocol
You can also use and or or operator to craft more complex filters
2. Tshark
Tshark is a command-line tool provided by Wireshark, a popular network protocol analyzer. It offers similar capabilities to tcpdump but provides more advanced filtering and analysis options.
Installation
sudo apt-get install tshark
Capturing Packets
tshark -i <interface_name>S
Saving Captured Packets
Reading Packets from Files
Specifying the number of packets to capture
tshark -i <interface> -c <packet_count>

Filtering Packets
tshark -Y "<filter>"
Some filters on which you can filter packets
ip.src == <source_ip>
ip.dst == <destination_ip>
tcp.port == <port_number>
udp.port == <port_number>
Filtering packets using a combination of source IP, destination IP and port Number
ip.src == <source_ip> and ip.dst == <destination_ip> and tcp.port == <port_number>
Filter packets by packet length:
frame.len == <length>
Filtering packets by protocol
<protocol>
🐾 Wireless Network Reconnaissance
Wireless network reconnaissance involves the passive gathering of information about wireless networks, including their SSIDs, MAC addresses, encryption methods, and potential vulnerabilities. This subtopic focuses on the tools available in Linux for hackers to conduct wireless network reconnaissance.
1. Airodump-ng
Airodump-ng is a powerful command-line tool used for capturing and analyzing wireless network traffic. It is part of the Aircrack-ng suite of tools, which are primarily used for wireless security auditing.
🔴 using Airodump-ng and its features for any unauthorized or malicious activities is strictly illegal and unethical.
Capturing and Displaying Networks
By default, Airodump-ng captures and displays information about available wireless networks. It continuously updates the list with real-time information, including network names (ESSIDs), MAC addresses, channels, signal strengths, encryption types, and more
airodump-ng wlan0
Capturing Specific Channel and BSSID
You can specify a specific channel and BSSID (MAC address of an access point) to capture data from a particular network. This can be useful for targeted monitoring or troubleshooting:
airodump-ng --channel 6 --bssid 00:11:22:33:44:55 wlan0
Saving Captured Data to a file
Airodump-ng allows you to save captured packets to a file for offline analysis. Specify the file name with the -w option:
airodump-ng -w capture_output wlan0
Filter Captured Data by ESSID
airodump-ng --essid MyNetwork wlan0
Display Connected Clients
airodump-ng --bssid 00:11:22:33:44:55 --output-format pcap --write clients_output wlan0
2. Kismet
Kismet is a popular wireless network analysis tool that allows you to monitor and analyze Wi-Fi networks. It provides a wide range of features for network discovery, packet capturing, and analysis. Here’s an overview of how to use Kismet and some example commands for different purposes:
Starting Kismet
kismet -c wlan0
Discover Networks
kismet -c wlan0
Saving Packets and Save to a File
kismet -c wlan0 -w capture_output.pcap
Filter Networks by ESSID:
You can filter the displayed networks based on their ESSID (network name) to focus on specific networks:
kismet -c wlan0 --filter-essid MyNetwork
🐸 Gps Integration
This is a unique feature with Kismat and a great one as well.
Kismet can integrate with a GPS device to associate captured Wi-Fi networks with their geographic coordinates. This enables you to map the networks and view their locations:
kismet -c wlan0 --gpsd
🦀 Remote Capture
Kismet supports capturing Wi-Fi packets from remote devices. You can specify the IP address and port of the remote Kismet server to capture packets from that server:
kismet -c remote:192.168.0.100:2501
🐾Passive DNS analysis
Passive DNS analysis is a technique used in passive network reconnaissance to gather information about domain names, subdomains, DNS misconfigurations, and potential spoofing attempts without actively engaging with the DNS infrastructure.
Using Dnsrecon
Dnsrecon is a command-line DNS reconnaissance tool used for information gathering and enumeration of DNS records. It helps in discovering subdomains, performing zone transfers, and conducting other DNS-related tasks. Here’s a guide on how to use Dnsrecon with examples and codes:
Installation
pip install dnsrecon
Usage
dnsrecon <options> <target>
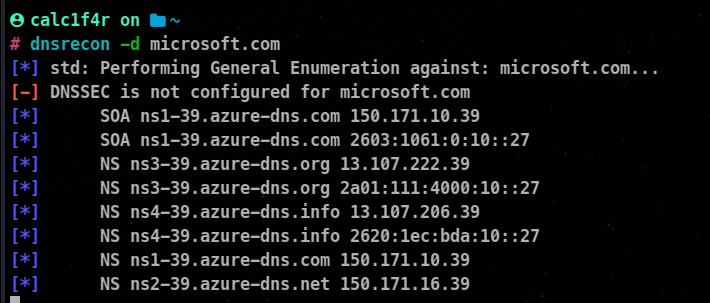
Various Available Options
-d <domain>: Specify the target domain.-t <type>: Specify the DNS record type to search for (e.g., A, AAAA, MX, NS, SOA).-r <resolver>: Specify a specific DNS resolver to use.-z: Perform a zone transfer.-D <file>: Provide a list of subdomains to test.-w <file>: Provide a wordlist file for subdomain bruteforcing.-c <file>: Specify a configuration file.
To search for specific DNS record types, use the -t option. For example, to find all MX records for a domain, use the following command:
dnsrecon -t mx -d example.com
To perform a zone transfer, use the -z option. Zone transfers allow you to retrieve all DNS records for a domain. For example:
dnsrecon -z -d example.com
To perform subdomain enumeration, you can use either a wordlist or a file containing a list of subdomains. For example, using a wordlist:
dnsrecon -d example.com -w subdomains.txt
🐧Active Network Reconnaissance
Active network scanning refers to the process of actively probing and interrogating a network or its devices to gather information, identify vulnerabilities, and assess the overall security posture. It involves sending deliberate network traffic or requests to target hosts and analyzing their responses to extract valuable insights about the network’s configuration, available services, open ports, and potential security weaknesses.
🐾 Finding Active Hosts
Finding active hosts is a critical aspect of active network scanning techniques as it helps identify live systems within a network.
There are various tools provided by linux to find active hosts in a network.
1. Ping Sweeping
Ping sweeping involves sending ICMP Echo Requests (ping) to a range of IP addresses to determine live hosts.
🔴 Note : windows machine won’t respond to these messages as their firewalls are instructed to ignore Icmp messages.
ping -c
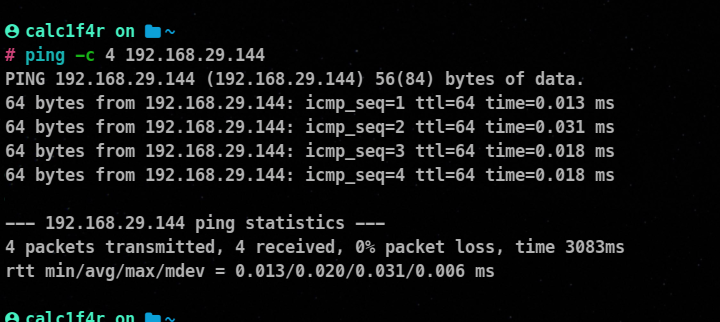
You can only check one host at a time using this.
But you can use this one line code to Run ping to your needs
for i in {1..255}; do ping -c 1 -W 1 192.168.1.$i; done
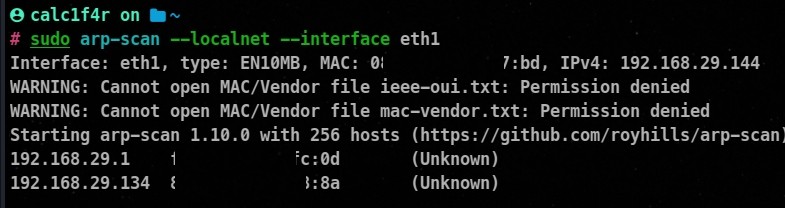
2. ARP Scanning
Address Resolution Protocol (ARP) scanning involves sending ARP requests to determine live hosts within a local network.
arp-scan --localnet
--localnet: Specifies to scan for the local network
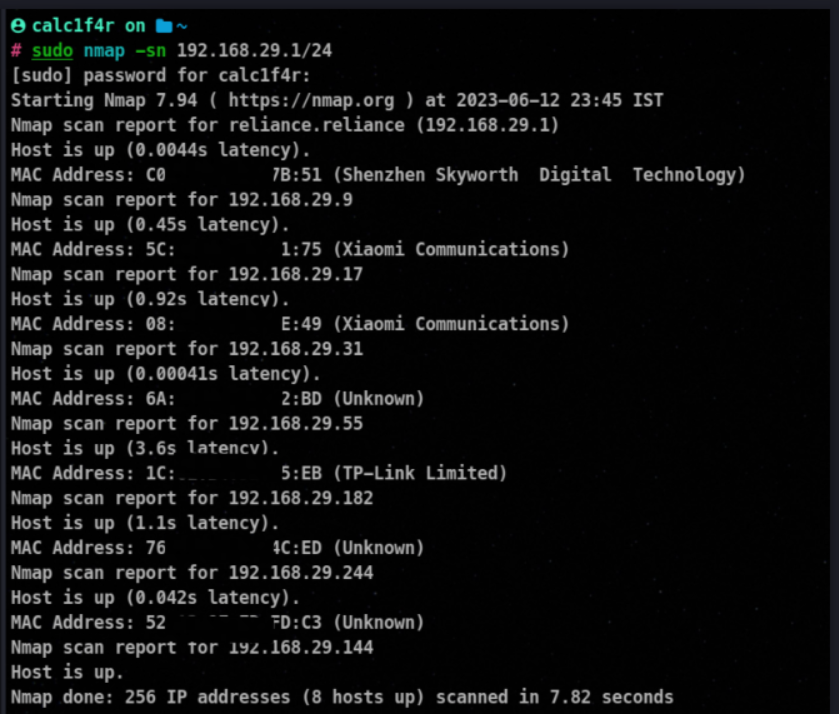
3. Nmap Discovery Scan
Nmap Offers various Types of Host Discovery Scans. To study about all you can checkout my previous blog On Nmap | Link
To do a basic Nmap host discovery scan you can try this !
nmap -sn <IP address range>
🐾 Finding Active Ports
After Finding the active hosts on a network for next step , we should always find the open ports on that machine because it helps in understanding the network’s services, identifying potential entry points for attacks, and assessing the security posture of the target network.
A port is a numbered communication endpoint in a computer’s network interface. It allows different applications and services to send and receive data over a network. Think of ports as channels through which data flows between your computer and the outside world.
Conditions of a port
| Port Condition | Meaning |
|---|
| Open | The port is actively accepting incoming connections. |
| Closed | The port is reachable but not currently in use. |
| Filtered | The port is likely being filtered by a firewall or IDS. |
| Unfiltered | The port is accessible, and its state cannot be determined. |
| Open | Filtered |
| Closed | Filtered |
Port scanning Using Tools
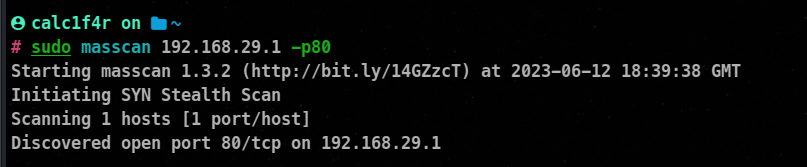
1. Using masscan
Masscan is a high-speed TCP port scanner designed for scanning large networks quickly. It is known for its speed and efficiency.
masscan <target> -p <port range> --rate <packets per second> -oX <output file>
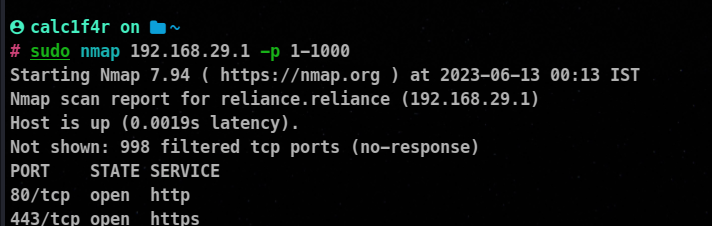
2. Using Nmap
As usual there are various type of port scans options available while using you can check out this blog
The basic one is this :
nmap <target> -p <port range>
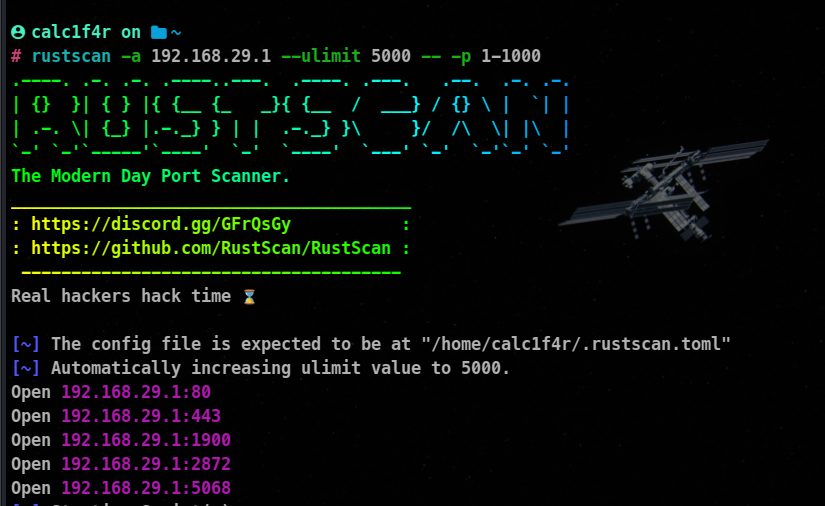
3. Using Rustscan
RustScan is a fast and efficient port scanner written in Rust programming language.
rustscan -a <target> --ulimit 5000 -- -p <port range>
The --ulimit 5000 option increases the maximum number of open file descriptors to allow RustScan to handle more simultaneous connections. You can adjust the value based on your system’s capabilities.
🐾 Service Enumeration
Service enumeration is a crucial step in the active network scanning process, where the goal is to identify the specific services or applications running on the target system or network.
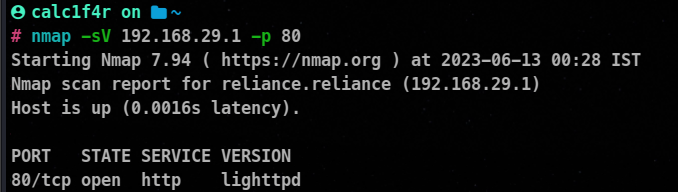
1. Using Nmap
Nmap is a powerful and widely used network scanning tool that can perform service enumeration.
nmap -sV <target IP>
or
nmap -p <port> -sV <target IP>
2. Using Netcat
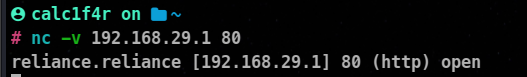
Netcat is a versatile tool for network communication and can also be used for service enumeration.
nc -v <target_ip> <port>
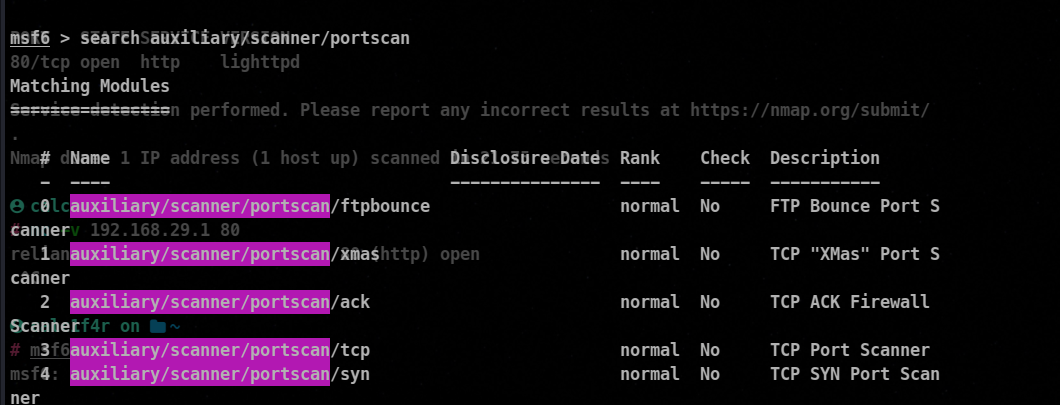
3. Metasploit Framework
Metasploit Framework is a comprehensive penetration testing tool that includes modules for service enumeration.
ms6> search auxiliary/scanner/portscan<module_name>
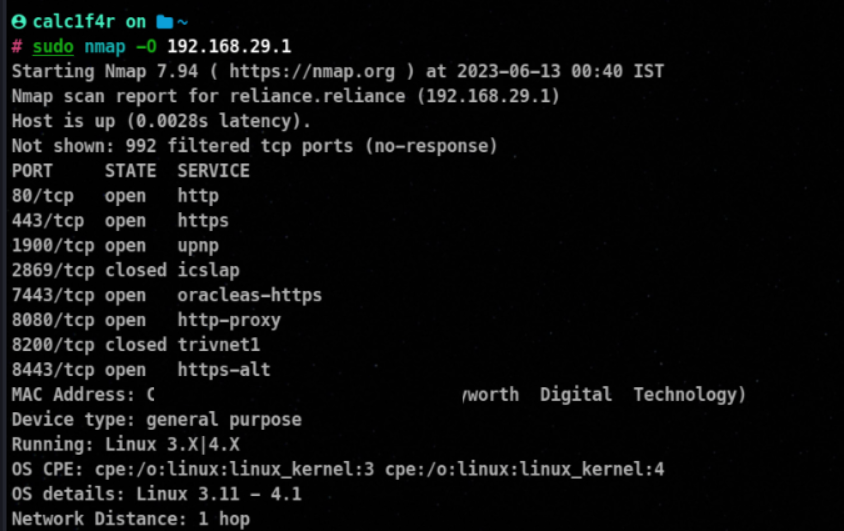
🐾 Operating System Fingerprinting
Operating System (OS) fingerprinting is a technique used in network scanning to identify the operating system running on a remote host. It involves analyzing various network attributes, behaviors, and responses to determine the OS type and version.
Using nmap
nmap -O <target IP>
Using Xprobe2
Xprobe2 is an active OS fingerprinting tool that sends crafted packets to the target host.
xprobe2 -T <target IP>
🐾 Active Enumeration Considerations
When performing active enumeration as part of network scanning techniques, it is important to consider the following factors:
- Legal and Ethical Considerations:
- Ensure that you have proper authorization to conduct active enumeration on the target network.
- Adhere to applicable laws, regulations, and ethical guidelines regarding network scanning activities
- Impact on Network Performance:
- Active enumeration techniques can generate significant network traffic and system load.
- Use scanning tools and techniques that minimize network congestion and do not disrupt the normal operation of the network.
- Intrusion Detection Systems (IDS) and Firewalls:
- Be aware that active enumeration activities might trigger alerts in intrusion detection systems or be blocked by firewalls.
- Coordinate with the network administrator to avoid any unintended consequences or disruptions.
🎡 Ending
Finally, Linux has powerful tools and techniques that can be used to enhance network security through network scanning and enumeration. Linux-based tools such as Nmap, Netcat, and Metasploit Framework provide valuable information about network architectures, identify vulnerabilities, and fortify systems. Responsible and ethical use is crucial to proactively defending against potential threats and ensuring the security of our networks. Stay curious, keep learning, and let Linux help you on your cybersecurity journey. Happy hacking and secure computing! ♥